The Cyber Kill Chain Model
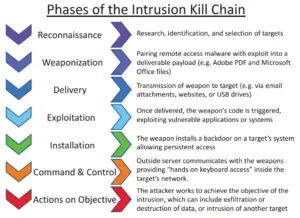
The cyber kill chain is a model that uses seven steps to describe the progression of a cyber attack.
The seven steps are: (1) reconnaissance, (2) weaponization, (3) delivery, (4) exploitation, (5) installation, (6) command and control, and (7) action on objective.
Developed by Lockheed Martin, the model of the cyber kill chain has been widely adopted in the cybersecurity industry.
It is a useful model for anyone involved in the field of cybersecurity, including both attackers and defenders.
Red teamers and penetration testers use the cyber kill chain model to improve their knowledge and tactics.
Defenders need to understand the cyber kill chain to protect their own systems.
What is a military “kill chain”?
The cyber kill chain is closely related to the general military concept of a ‘kill chain’. A kill chain generally describes the steps taken during an offensive attack.
The typical steps of a military kill chain include:
– Identifying the target
– Dispatching forces
– Initiating the attack
– Destroying the target
There are many different versions of kill chains. Some are much more detailed than this. What Lockheed Martin did was to take the basic concept of a kill chain and apply it to cyber attacks.
The 7 Steps of the Cyber Kill Chain
- Reconnaisance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and Control
- Action on objective
Reconnaissance
There are two types of reconnaissance: passive and active. These steps are often performed in sequence.
One of the primary goals of both types of recon is to maximize the attack surface. This means identifying every possible aspect of an organization that present a possible attack point.
Passive Reconnaissance
Passive reconnaissance is information gathering that is completely undetectable by the target. This most often includes public sources of information systems and employees.
Popular sources of passive reconnaissance include:
- Search engines
- Web archives
- Website contact details
- Job sites
- CV databases
The goal is to gather as much information as possible.
This includes mapping the organizational hierarchy, collecting contact information, and financial details. Computer systems, networks, and assets may also mapped during this step.
The type of information gathered may also be related to a specific type of attack or may be more general in nature. For example, attackers who want to phish may gather as many email addresses as possible and learn about employees to improve their chances of success. By combining information from different sources and techniques, an attacker can maximize their chance of success.
From these sources an attacker can identify individual email addresses, contact details, organizational hierarchy, financial records, computer systems, applications used (listed as employee skills), staff photos and third-party suppliers (advertising their customer base).
Active Reconnaissance
Active reconnaissance is any recon activity that could potentially be detected by the target. This includes visiting a website, as the server could log the IP address.
Other examples of active recon include:
- Port scanning
- Network scanning
- Service, version, or vulnerability scanning
- Testing a website for weakness or looking for information
- Directory enumeration
- Sending emails to gain information (such as obtaining the non-delivery report)
Weaponization
The second stage of the cyber kill chain is weaponization. Weaponization is the process of creating ‘cyber weapons’ that will be used to attack targets identified during reconnaissance. This may include preparing exploit payloads or malware. A common example that we see in CTFs (capture the flag exercises) is customizing an online exploit from Github or ExploitDB or using msfvenom to generate a payload.
In CTFs we will generally just attack the target outright as there is no consequence if we are detected or crash the target. On real infrastructure a blatant assault resulting in a system crash is often unacceptable. This is one area where penetration testing and red teaming diverge. Penetration tests may be intentionally loud to allow defenders to see what they can detect. Red teaming is closer to the actions performed by true malicious targets, as they will generally seek to be as stealthy as possible.
To test their cyber weapons, stealthy attackers may create clones of the target infrastructure to test on. These clones allow attackers to test their tools invisibly before actually attacking the system.
After the weapon has been created, it will be linked with some type of payload. The payload is the action, function or process that the attacker wants to be run upon delivery. For example, a reverse shell payload will cause the target to attempt to connect to the attacker’s machine on a specified port. This will generate a shell if the attacker is listening on that port.
Delivery
After creating their cyber weapons, attackers need to direct them against the target. The delivery step describes the methods used by attackers to direct an attack against a target.
There are several common methods that we will cover here: direct attack, phishing, website/watering hole, and malicious media.
Direct attack
If the attacker can gain a connection to the target then they may be able to directly deliver a payload. This is common in attacks on web applications, such as using an upload form to place a payload on the target machine. Other examples could include exploiting misconfiguration, default credentials, or weak passwords to obtain a direct connection that allows delivery of a payload.
Phishing
Phishing, also known as spear phishing, is the act of sending an email that contains a malicious file or website link to potential victims in the target organization.
If the user opens the attachment or clicks the link to the malicious website, their own computer will then run code that results in payload delivery.
Attackers can dramatically increase their odds of success by spoofing the ‘from’ (origin) email address. They generate large lists of valid target emails and perform recon allowing them to customize the email for each recipient.
While many people are familiar with poor phishing attacks, fewer are aware that they can actually be surprisingly well-executed and effective.
An example of a well-executed phishing attack could be:
- Selecting an employee to target
- Using Facebook and LinkedIn to gain information about the employee including their interests, their boss, and/or their employees
- Spoofing an email from a boss or an employee, using the publicly available information
For example, if the victim is interested in kayaking, the attacker could potentially spoof an email from a colleague that is kayaking themed, with a link “what do you think about this kayaking blog?” With just a bit of work, even the blog could easily appear legitimate.
Website or watering hole
Another strategy for gaining payload delivery is by hosting malicious code on a website. This can be interrelated with phishing but can also be an independent strategy.
For example, an attacker could gain control of a website and install malicious code. When victims then visit the website (that they ordinarily trust), the code will execute. This can result in the attacker gaining a connection or control over multiple other systems.
Malicious Media
Another common delivery method is the use of malicious media. Delivery using malicious media involves using some type of storage device to run an attacker’s code.
One example could be sending CDs or USB sticks containing malicious code to potential victims. This could be more or less sophisticated. Like phishing, reconnaissance is crucial to increasing the odds of success.
An example of a well-executed malicious media attack could be:
- Identify a target based on role. For this example, let’s use the Maintenance Manager at a facility.
- Using recon to gain important information about the target. In this example, we could call the facility, pretending to be the supplier of equipment or services used by Maintenance Managers in the same industry.
- Sending the victim a well typed letter and USB thumb drive containing ’20 Helpful Tools for Maintenance Managers’.
While this level of sophistication is rare, it is certainly possible and IT departments need to protect against these types of attacks. More common examples might include leaving USB sticks around the business or home of the victim in the hopes that they will be inserted into a computer.
One common type of malicious media is called a ‘Rubber Ducky’. A Rubber Ducky is a USB stick that actually mimics a computer keyboard. After insertion, it waits for a time and then begins to send commands corresponding to typing on a keyboard. For example, the Rubber Ducky could execute START > RUN > CMD, which would start a command line interface. USB Rubber Duckies can be purchased or made, and can be programmed to run many different commands.
Exploitation
The fourth step of the cyber kill chain is exploitation. Exploitation is the act of executing code in such a way as to take advantage of a weakness that has been identified. After delivering the payload, exploitation will result in the attacker gaining a foothold on the target system.
As with the other steps in the cyber kill chain, there are different ways of exploiting security flaws.
Direct Attack Exploitation
A direct attack exploitation occurs during a direct attack (see delivery methods above). This occurs when the attacker is able to exploit a security flaw that allows for a successful direct attack. After the payload is delivered directly, the attacker can run the code, resulting in exploitation. At this point, the attacker may have gained enough of a foothold to begin escalating their privileges or perform another desired action.
Installation
The next step in the cyber kill chain is installation. The installation step involves using the foothold gained during a successful exploit to install code that furthers the attackers objectives.
After gaining a foothold on the target, attackers will seek to achieve persistence. Persistence means that the attacker can continue to access the target system for some period of time (ideally indefinitely). This is achieved during the installation phase because it involves ‘installing’ some type of code that allows for a backdoor or repeated access.
If the system is not well maintained, the attacker could even create a new, legitimate user for themselves that allows them to directly access the system indefinitely.
Command and Control
The command and control step of the cyber kill chain describes the attacker’s ability to execute commands as if they were an authorized user.
Attackers have access to command and control (called ‘C2’) software that may allow them to remotely monitor and execute code on many computers at the same time.
One of the most common examples is a botnet, which is a network of devices that have been infected with bot malware. The attacker can then control a large number of bots that may enable them to perform a number of activities. These include spamming as well as launching Denial of Service (DoS) attacks. Botnets may also be rented out to other malicious parties.
Action on Objectives
In the cyber kill chain, action on objectives is the step during which the attacker performs actions to achieve their own objectives. This could include copying and/or destroying important data, defacing a website, transferring funds, or even encrypting for ransom.
The Cyber Kill Chain, Revisited
The cyber kill chain is an excellent model for cyber attacks, and can be a useful tool in the hands of both blue and red teamers.