Intrusion Detection System
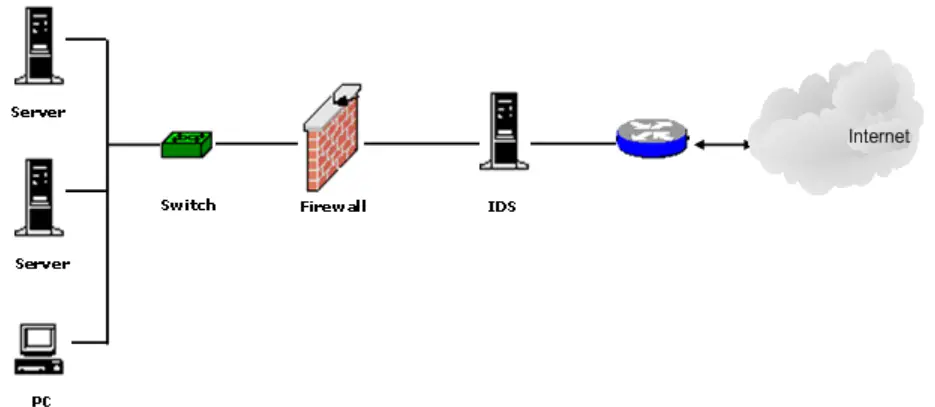
An intrusion detection system (IDS) is a passive monitoring device that detects potential threats on a computer system. The IDS will generate alerts when threats are detected. This enables security operations center (SOC) analysts and incident responders to respond to the threat.
Intrusion detection systems are designed to be deployed in different environments. As with many other cybersecurity tools, an IDS can either be host-based or network-based. IDSs are often combined with or integrated into firewalls to add an additional layer of protection.
What is an Intrusion Detection System (IDS)?
An intrusion detection system (IDS) is a software application or hardware device that automates intrusion detection on a host or network.
An IDS receives copies of network traffic or system logs, analyzes the information, and generate alerts when a possible intrusion is identified. They do this using either (a) malware signature detection or (b) anomaly detection.
Alerts generated by an IDS contain information such as the source and destination IP addresses, port numbers, and protocol. They also provide details like the broken rule that caused the alert and the incident class (bad traffic, network trojan).
This information allows the SOC to take appropriate action in order to defend the network or host.
Types of Intrusion Detection Systems
The two primary types of IDS are host-based (HIDS) and network based (NIDS).
| Type of IDS | Coverage | Advantages | Disadvantages |
| Host-based (HIDS) | Single host | Greater visibility (depth) | Requires more resources and memory |
| Network-based (NIDS) | Entire network | Monitors all network traffic | Less visibility (depth) into specific hosts |
Host-Based IDS (HIDS)
A host-based IDS lives on a particular endpoint and protects it against both internal and external threats. HIDS often have the ability to monitor the system logs, observe running processes, and monitor traffic to and from the machine.
HIDS create a database of checksums and file attributes for system files on the device. They detect changes by periodically comparing the historical values with the current ones. Using a checksum ensures 100% data integrity. The HIDS will alert when critical files have been altered. HIDS are particularly useful on machines that don’t often change their configurations.
HIDSs consume a lot of disk space and resources. Although they have deep visibility into the host machine, they do not operate on the network level.
This is where the network-based detection system (NIDS) comes into play.
Network-Based IDS (NIDS)
A network-based detection system (NIDS) monitors an entire network. It has visibility into all traffic flowing through the network.
NIDS make decisions based on packet metadata and contents. This wider viewpoint provides more context and the ability to detect widespread threats; however, these systems lack visibility into the internals of the endpoints that they protect.
NIDS are frequently paired with firewalls. They can sit either in front of or behind the firewall and monitor all inbound and outbound network traffic.
NIDS can also detect and alert users about changes in conditions such as traffic load. This allows for detection of denial of service (DoS) attacks.
However, many NIDS struggle with encrypted data as well as fragmented packets. For best security, deploy NIDS which are capable of re-assembling packet streams to avoid missing more elusive attacks.
The advantage of placing a NIDS in front of a firewall is that it gets to see traffic that would otherwise be blocked. This can provide an early indication of an impending attack.
NIDS vs. Firewall
NIDS are often compared with firewalls but the two function in different ways.
The difference between NIDSs and firewalls is that NIDS are passive, while firewalls are active.
NIDS monitor traffic and report suspicious findings, but firewalls are capable of actively blocking traffic. Firewalls block traffic based on rules and are therefore capable of preventing intrusion. To prevent these intrusions from occurring, we need to use an intrusion prevention system (IPS).
Next-generation firewalls integrate NIDS functionality into a firewall, offering a product that combines both layers of security.
HIDS vs. NIDS
Due to the different levels of visibility, deploying a HIDS or NIDS in isolation provides incomplete protection to an organization’s system. A unified threat management solution, which integrates multiple technologies in one system, can provide more comprehensive security.
IDS Detection Methods
There are three common intrusion detection methods used by IDSs: signature detection, anomaly detection, and hybrid detection.
Signature Detection
The most common method of intrusion detection method is signature-based.
For signature-based detection to work, a unique identifier is established for a known threat. This identifier may be a unique patch of code or the hash of a known malicious file, and is called a signature.
The IDS then monitors traffic for the signature of that threat (as well as many others) in order to flag possible attacks.
One of the advantages of signature-based detection is that it can achieve a high detection rate with no false positives.
On the other hand, signature-based IDS is limited to detecting known threats.
Anomaly Detection
Anomaly-based IDS solutions compare the data against a model of “normal” behavior.
All behavior is compared to this model, and any anomalies are labeled as potential threats.
While this approach can detect many threats that signature-based detection cannot, there arises the difficulty of building an accurate model of “normal” behavior. This means that anomaly-based detection systems must balance false positives with false negatives.
Hybrid Detection
A hybrid IDS uses both signature-based and anomaly-based detection.
This enables the hybrid system to detect more potential attacks with a lower error rate than using either system in isolation. In general, a hybrid system is favored over an anomaly-based system alone as the addition of signature-based detection should not result in an increase of false positives.
Intrusion Prevention Systems (IPS)
Closely related to the intrusion detection system is the intrusion prevention system (IPS). An IPS adds active functionality to an IDS, enabling it to stop possible attacks.
An IPS is usually used in place of a NIDS, adding a second active layer of network defense to an existing firewall.
When used correctly, IPS can be a powerful addition to an organization’s security systems. They can prevent unauthorized access to the network without human intervention.
On the other hand, IPSs have the risk of flagging false positives and thereby blocking legitimate traffic. It is therefore important to configure the IPS properly so that it performs its intended function.
How to Use an IDS
An IDS is a valuable component of an organization’s cyber defense.
Firewalls provide a starting point for network security, but more advanced attacks can get through them.
IDSs provide additional lines of defense, making it more difficult for an attacker to gain access to an organization’s network or systems undetected. Host-based IDSs can also add another layer of protection for specific, critical machines.
When choosing an IDS or a related product, the most important thing to consider is the relationship between security and cost.
Additional Resources
For additional reading or resources intrusion detection systems I recommend starting with the NIST Guide to Intrusion and Prevention Systems.