TryHackMe – Advent of Cyber 2023 Day 13

Day 13’s adventures are focused on two pillars of defensive cybersecurity: firewalls and honeypots. These are two important topics from both offensive and defensive perspectives. In order to get the flag, we will need to modify a script containing firewall rules to enable us to connect to a hidden web server.
The Advent of Cyber 2023 challenge can be found at: https://tryhackme.com/room/adventofcyber2023
About This Walkthrough/Disclaimer:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by requiring a manual action (highlighting) to obtain all solutions. This way you can follow along without being handed the solution if you don’t want it. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
Walkthrough for TryHackMe Advent of Cyber 2023 Day 13
Question 1
Which security model is being used to analyse the breach and defence strategies?
This is the framework that we were introduced to in the description, and it is used to model both offensive and defensive capabilities.
Answer (Highlight Below):
Diamond Model
Question 2
Which defence capability is used to actively search for signs of malicious activity?
This capability is a process in which defenders actively search for malicious actors, activities, or weaknesses within their own systems.
Answer (Highlight Below):
Threat hunting
Question 3
What are our main two infrastructure focuses? (Answer format: answer1 and answer2)
The first is used as a primary line of defense, and utilizes a rule-based system for controlling network traffic.
The second is a decoy that is used to trap and gather intelligence on attackers.
Answer (Highlight Below):
Firewall and Honeypot
Question 4
Which firewall command is used to block traffic?
This is a verb that describes the act of preventing network traffic.
As a quick reference, the following is the command to allow all outgoing traffic:
sudo ufw default allow outgoingAnd this is the command the deny all incoming traffic:
sudo ufw default deny incomingAnswer (Highlight Below):
deny
Question 5
There is a flag in one of the stories. Can you find it?
Now we get into the actual activity. To begin, we need to have both our AttackBox and target system booted up. Using an AttackBox (or your own VM with VPN), SSH into the target machine using the credentials provided:
vantwinkle:TwinkleStar
ssh vantwinkle@<target IP>
The working directory contains a bash shell script, ‘Van_Twinkle_rules.sh’ and the ‘pentbox’ directory:
This is a good opportunity to go through all of the steps described in the description. However in order to proceed, all that we will need to do is to modify the rules in ‘Van_Twinkle_rules.sh’ so that we can access a web server from our AttackBox.
Let’s take a look at the shell script. Note that we will need to use sudo permissions:
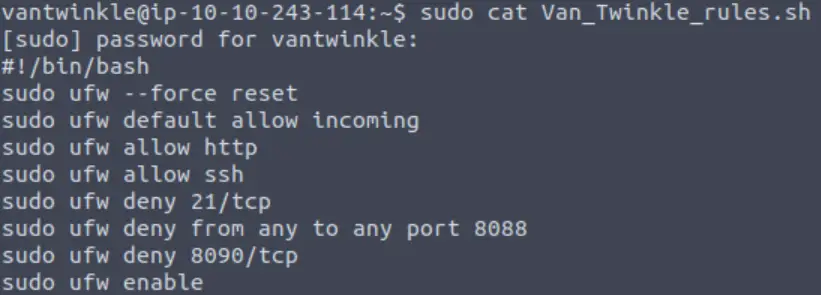
It looks like the rules are allowing http, but are denying connections to certain ports. Specifically port 8090 and 8088 are called out.
Before we change these rules, let’s use an nmap scan so that we can get a quick view of the target machine’s ports:
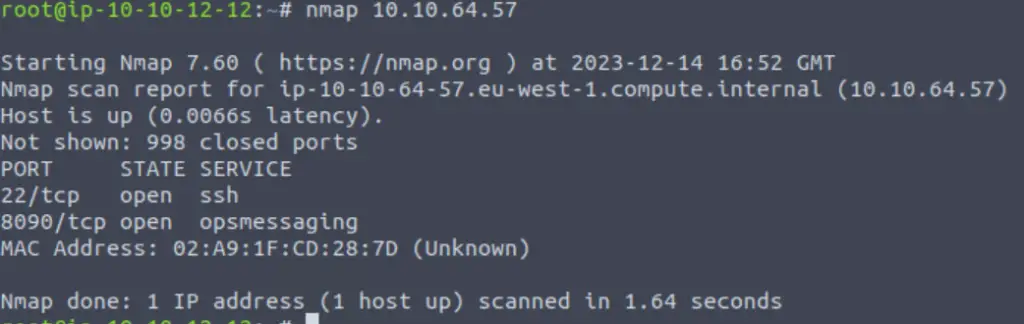
It looks like port 8090 is open! What’s going on here?
Well you may have discovered this earlier if you had run through the commands from TryHackMe’s description, but UFW (Uncomplicated FireWall) is not yet running!
We can see this by checking the status:
sudo ufw status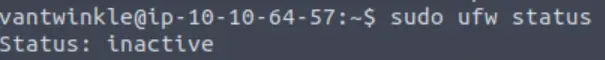
Let’s see if we can further enumerate the open port (8090) to see what’s running on it.
We can use an nmap service version (-sV) scan on this port to see if we can get further information:
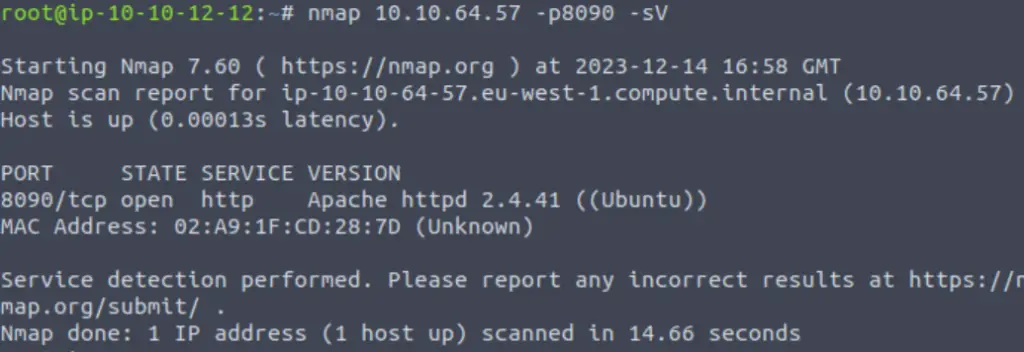
It looks like there is an Apache server running on this port! Let’s see if we can access the server using Firefox:

Okay, so it looks like we can actually access the webserver (and the flag) without actually interacting with the firewall at all. Of course, this isn’t the intended the route, so we’re just going to ignore this for now.
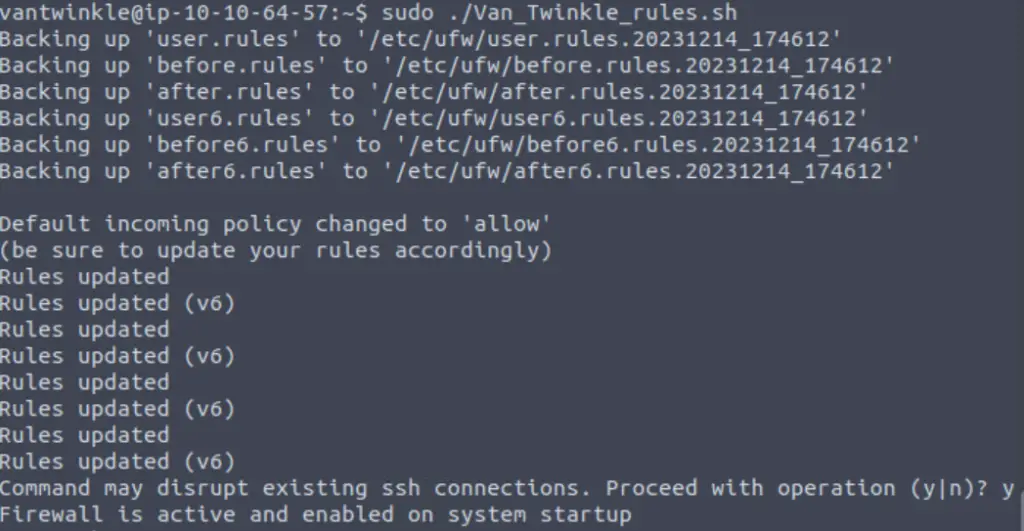
Instead, let’s run the ‘Van_Twinkle_rules.sh’ script, which should activate the firewall:
sudo ./Van_Twinkle_rules.sh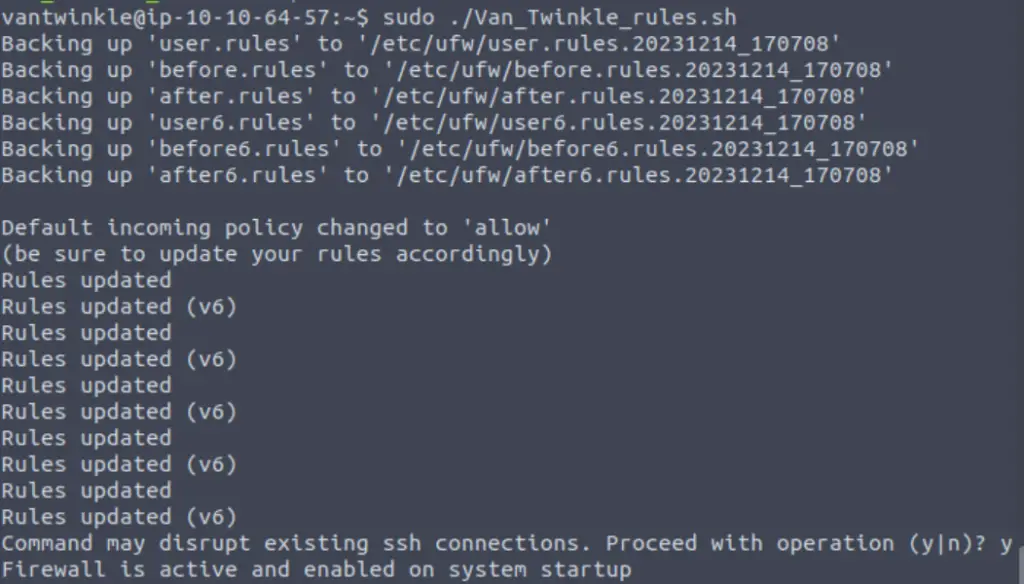
Now if we try to visit the web page, our connection attempt will time out:
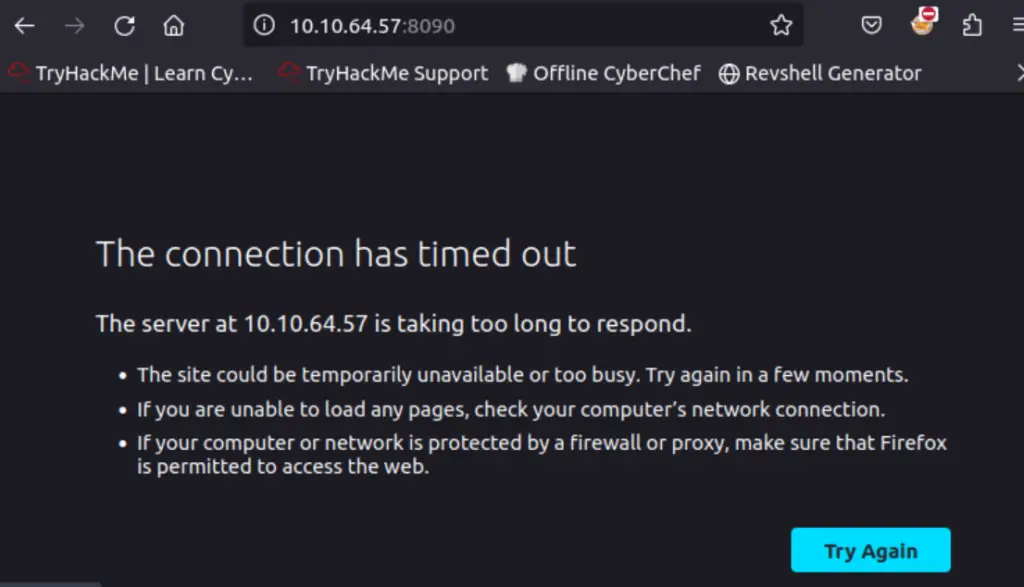
And if we scan the port again with nmap, we will see that it’s now in a filtered state. ‘Filtered’ means that the port is likely open but our connection attempt is being blocked by a firewall.
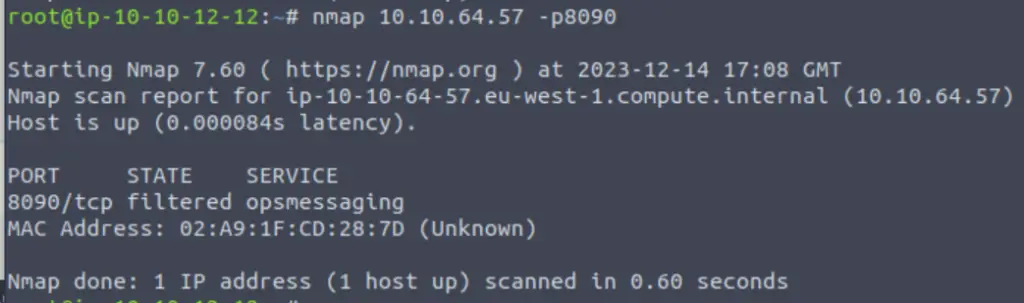
Our job is to modify the firewall rules to enable us to connect to the web server. Let’s look at the firewall rules again (this time, I used nano in order to be able to edit them):
sudo nano Van_Twinkle_rules.sh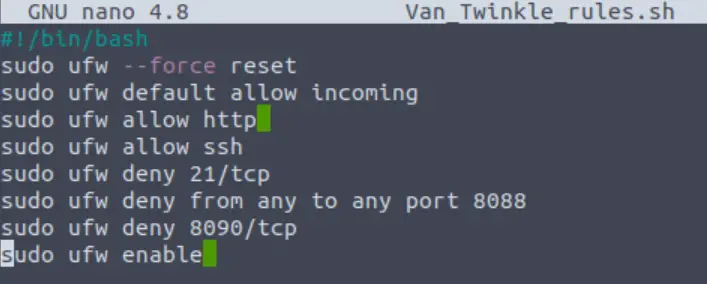
Note the line that prevents us from connecting to the server is ‘sudo ufw deny 8090/tcp’.
In this case, we can simple delete this line:
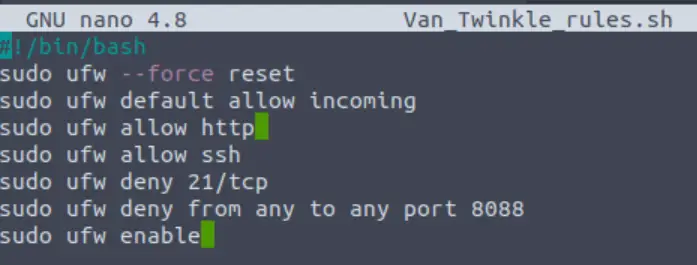
Run the script again:
And now we can access the server using our browser:

The flag can be found lower down on this page. You can always search for the string ‘THM{‘ instead of looking for it manually.
Answer (Highlight Below):
THM{P0T$_W@11S_4_S@N7@}