TryHackMe – Advent of Cyber 2023 Day 17

Day 17 of the Advent of Cyber 2023 event is a blue team challenge focused on the use of the SiLK suite to identify and study a C2 server.
Rather than focusing at the packet level, the SiLK suite contains a number of helpful tools for analyzing network traffic at a higher level. SiLK makes it easy to extract important information from a larger dataset, as well as to get statistics about the extracted data. This means that if we have a sizeable source of network data, we can efficiently look at things like Source IPs, ports, and protocols to quickly piece together a high-level survey of what is going on in the network.
Advent of Cyber 2023 can be found at: https://tryhackme.com/room/adventofcyber2023
About This Walkthrough/Disclaimer:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by requiring a manual action (highlighting) to obtain all solutions. This way you can follow along without being handed the solution if you don’t want it. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
Walkthrough for TryHackMe Advent of Cyber 2023 Day 17
Question 1
Which version of SiLK is installed on the VM?
We can run ‘silk_config -v’ to get the version:
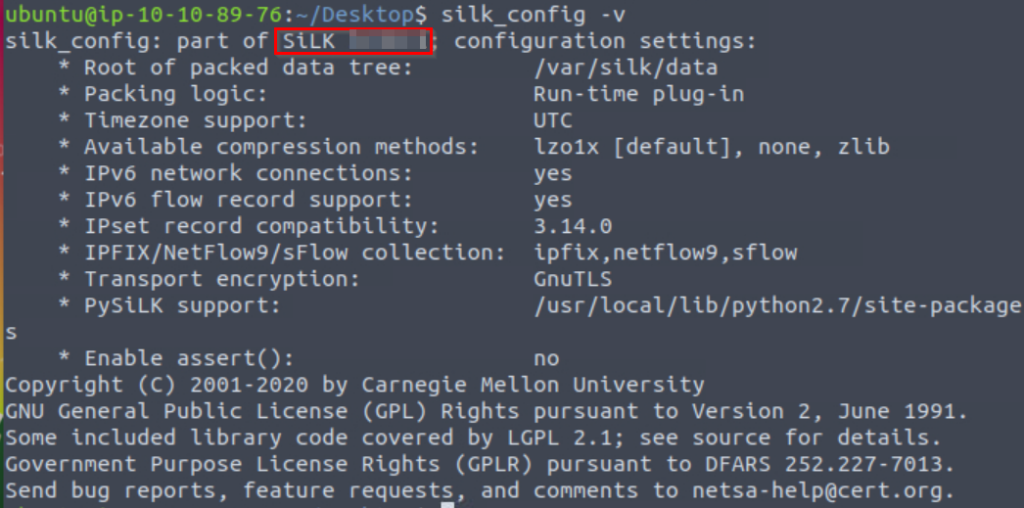
Answer (Highlight Below):
3.19.1
Question 2
What is the size of the flows in the count records?
First I listed the contents of the Desktop:
The file suspicious-flows.silk is the binary flow file that we want to target.
Now we can run rwfileinfo to get more information about the file:
rwfileinfo suspicious-flows.silkTo answer the question, we are looking for the value of ‘count-records’:
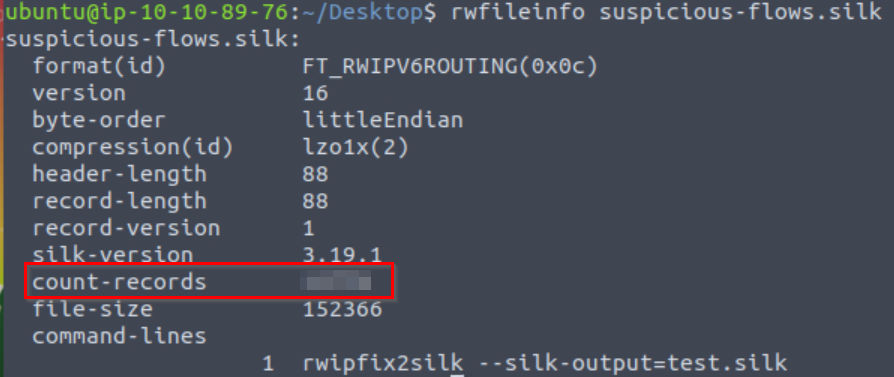
Answer (Highlight Below):
11774
Question 3
What is the start time (sTime) of the sixth record in the file?
The ‘rwcut’ command will read records from the binary. We can grab the first six records using the argument ‘–num-recs=6’:
rwcut suspicious-flows.silk --num-recs=6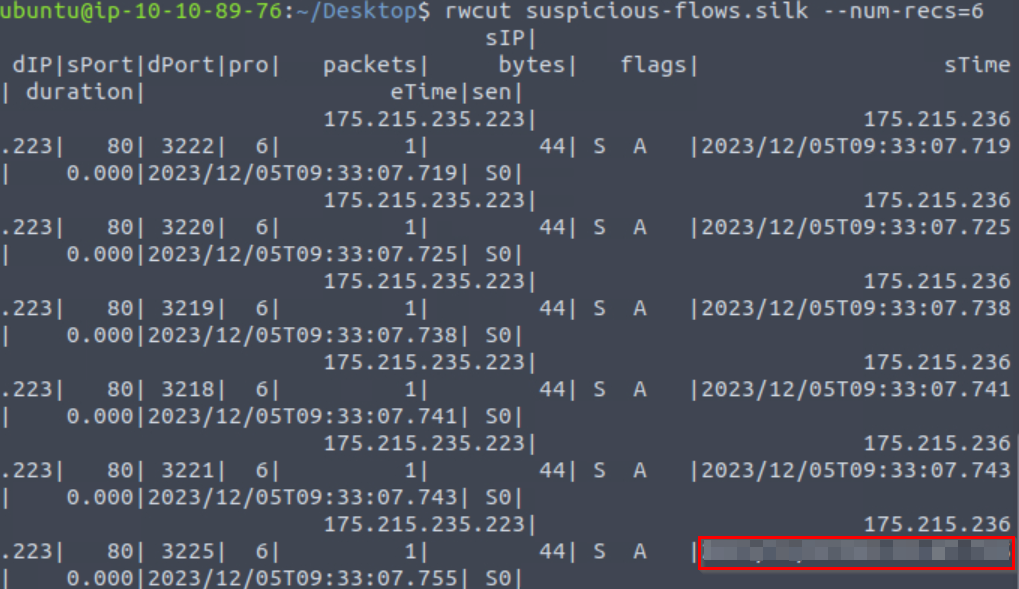
Grab the sTime value to answer Question # 3.
Answer (Highlight Below):
2023/12/05T09:33:07.755
Question 4
What is the destination port of the sixth UDP record?
There are a few different ways to do this, but it is best to use rwfilter to filter based on protocol (17 is UDP). I then passed the output to rwcut and simplified the output specifying the fields.
Here’s the command I used:
rwfilter suspicious-flows.silk --proto=17 --pass=stdout | rwcut --fields=protocol,sIP,dIP,dPort --num-recs=6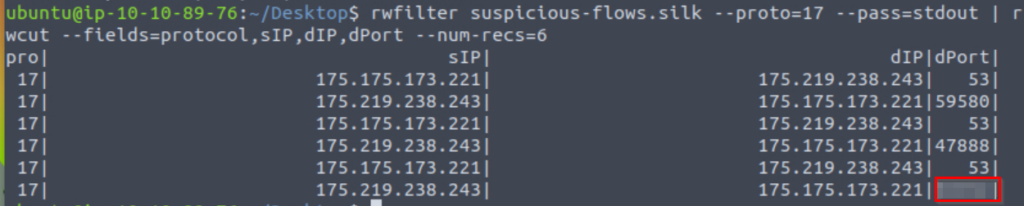
Answer (Highlight Below):
49950
Question 5
What is the record value (%) of the dport 53?
We can use rwstats to get the statistics for dPort 53 (which typically corresponds with DNS):
rwstats suspicious-flows.silk --fields=dPort --values=records --count=10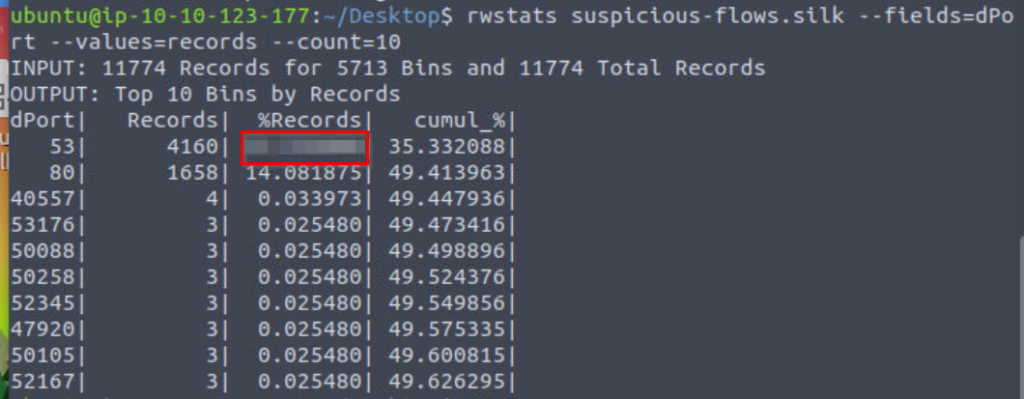
The value that we are looking for is the %Records entry that corresponds with port 53.
Answer (Highlight Below):
35.332088
Question 6
What is the number of bytes transmitted by the top talker on the network?
I used the rwstats command again, but this time sorted by the source IP (sIP). The top talker will then be at the top of the list:
rwstats suspicious-flows.silk --fields=sIP --values=bytes --count=10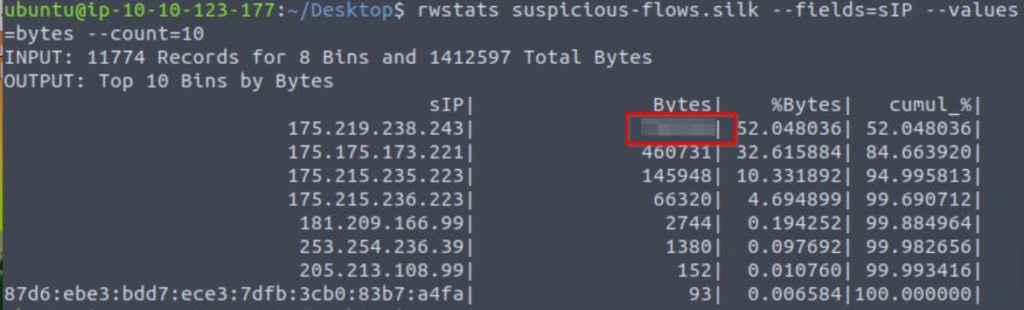
Answer (Highlight Below):
735229
Question 7
What is the sTime value of the first DNS record going to port 53?
For this, I used rwfilter to filter out anything that wasn’t going to port 53, then I used rwcut to get the sTime value for the first record (I also grabbed the source and destination IP addresses).
rwfilter suspicious-flows.silk --aport=53 --pass=stdout | rwcut --fields=sTime,sIP,dIP --num-recs=1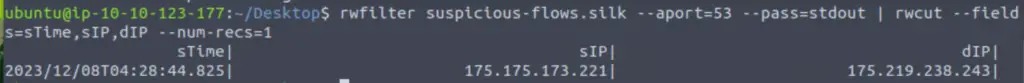
Answer (Highlight Below):
2023/12/08T04:28:44.825
Question 8
What is the IP address of the host that the C2 potentially controls? (In defanged format: 123[.]456[.]789[.]0 )
We can use rwfilter and rwstats to get a closer look at what’s going on:
rwfilter FILENAME --aport=53 --pass=stdout | rwstats --fields=sIP,dIP --values=records,bytes,packets --count=10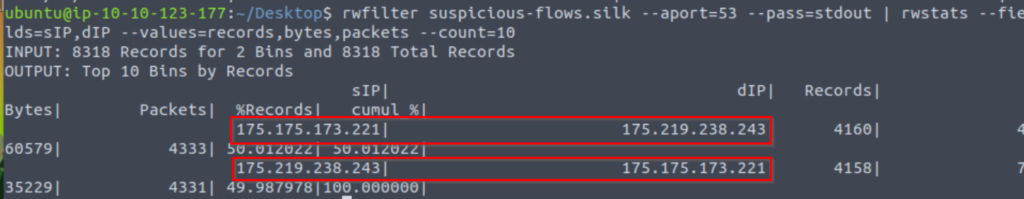
This is a lot of traffic, and it’s all going back and forth between two IP addresses. This points to malicious activity, but which one was the culprit?
To answer this question, we can adjust the previous command a bit to filter based on ‘destination’ port (–dport=53) rather than ‘any port’ (–aport=53).
Let’s try the first IP address:
rwfilter suspicious-flows.silk --saddress=175.175.173.221 --dport=53 --pass=stdout | rwcut --fields=sIP,dIP,stime | head -10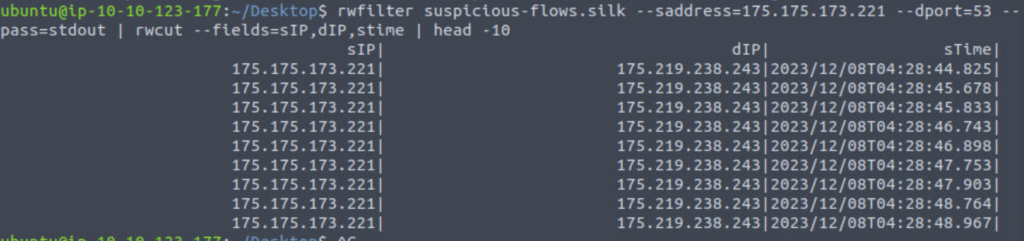
Now let’s try the second IP address:
rwfilter suspicious-flows.silk --saddress=175.219.238.243 --dport=53 --pass=stdout | rwcut --fields=sIP,dIP,stime | head -10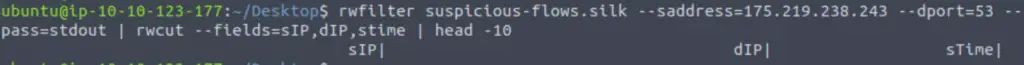
This time we don’t get any results! This points to the first one being the culprit.
Answer (Highlight Below):
175[.]175[.]173[.]221
Question 9
Which IP address is suspected to be the flood attacker? (In defanged format: 123[.]456[.]789[.]0 )
In the beginning of our investigation, we noticed a lot of traffic on port 80, so this is likely a good place to continue:
rwfilter suspicious-flows.silk --aport=80 --pass=stdout | rwstats --fields=sIP,dIP,dPort --count=10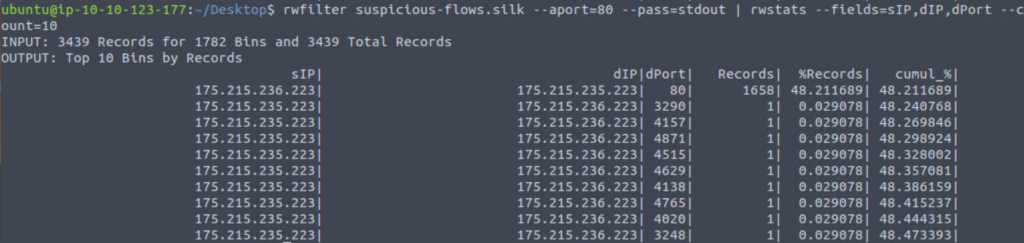
It looks like there’s one IP responsible for all of this http traffic!
Answer (Highlight Below):
175[.]215[.]236[.]223
Question 10
What is the sent SYN packet’s number of records?
For this last question, all we need to do is use rwstats to get the number of packets sent by the IP address that we just identified:
rwstats suspicious-flows.silk --fields=sIP,dIP --values=records,packets --count=10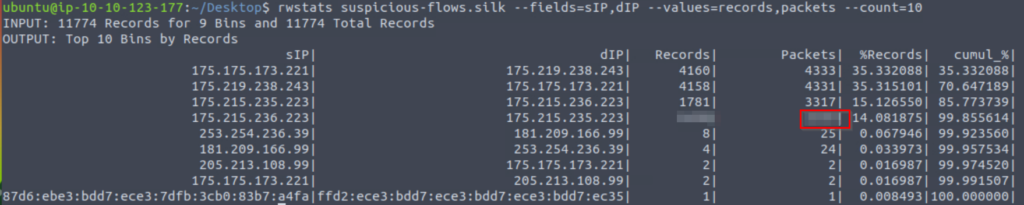
Answer (Highlight Below):
1658