TryHackMe – Advent of Cyber 2023 Day 5

Day 5 of the TryHackMe Advent of Cyber 2023 challenge is focused on the DOS operating system.
DOS is a legacy operating system that is uncommon today, but the commands that are covered in the Day 5 activities are mostly still useful on the Windows command line.
In addition to the joys of playing around with DOS, we also get to compile a simple “Hello, World” program in C. And we also get to learn about magic bytes, hex and ASCII.
The Advent of Cyber 2023 room can be found at: https://tryhackme.com/room/adventofcyber2023
About This Walkthrough/Disclaimer:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by requiring a manual action (highlighting) to obtain all solutions. This way you can follow along without being handed the solution if you don’t want it. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
Day 5 – Reverse Engineering
A Christmas DOScovery: Tapes of Yule-tide Past
Question 1
How large (in bytes) is the AC2023.BAK file?
Use the green ‘Start Machine’ button at the top of Day 5’s tasks to start the VM. You should see an application called ‘DOSBox-X’ on the Desktop:
The rest of the day’s activities will be performed from inside this application. After starting it up, you should see the following:
We can immediately start using the DOS terminal. Let’s try out a few commands. We can list the contents of the working directory with dir:
dir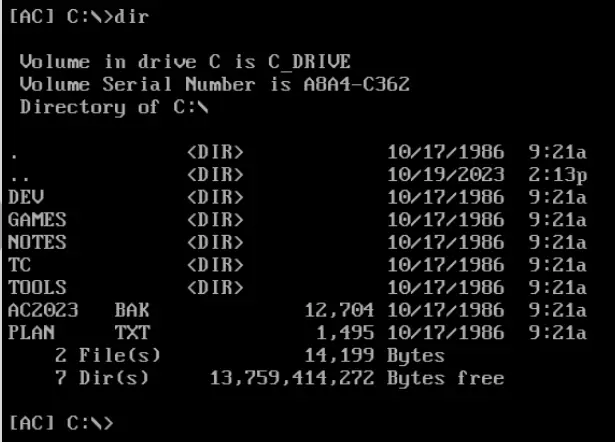
This directory contains the AC2023.bak file, and the directory listing returns its size. We can already answer the first question!
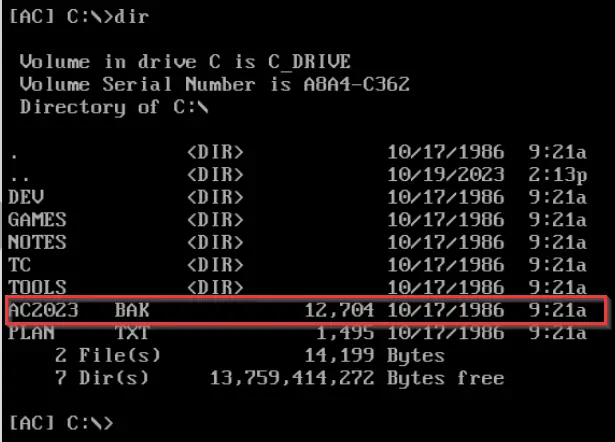
Answer (Highlight Below):
12,704
Question 2
What is the name of the backup program?
Next, let’s change directories to C:\Tools\Backup and list its contents:
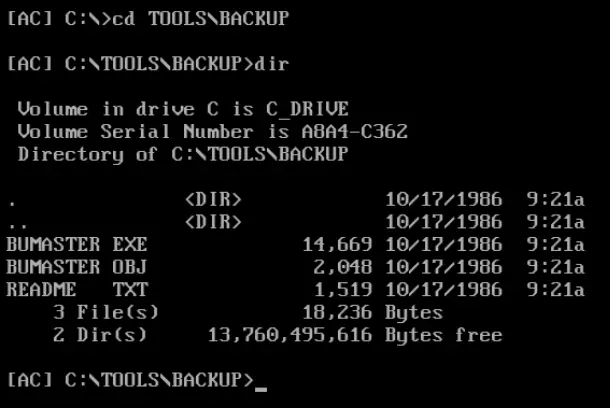
We can edit README.TXT, which gives us a nice format for reading its contents:
edit README.TXT
You should see the following text, which includes the name of the backup program.
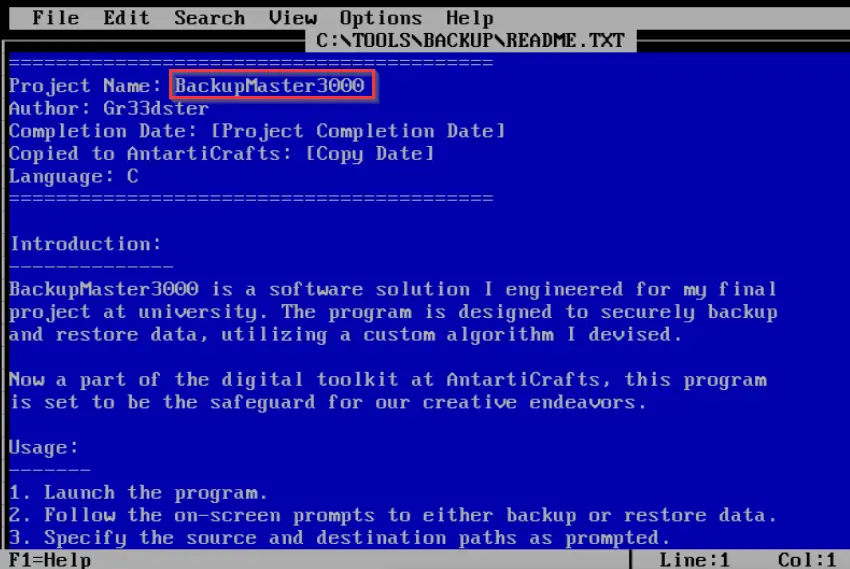
Answer (Highlight Below):
BACKUPMASTER3000
Question 3
What should the correct bytes be in the backup’s file signature to restore the backup properly?
Scrolling down through README.TXT, we find the following information:
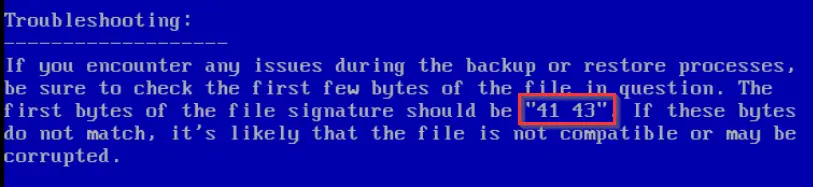
It looks like we may need to change the magic bytes of the file to get it to work.
Answer (Highlight Below):
41 43
Question 4
What is the flag after restoring the backup successfully?
We can get some practice by navigating to C:\DEV\HELLO:
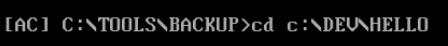
If we list the contents of this directory, we should see a file called HELLO.C:
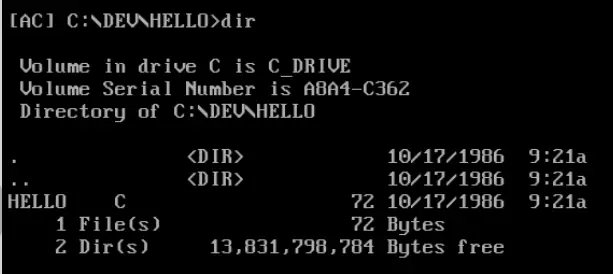
We can open this file with the Borland Turbo C Compiler using the tc command:
tc HELLO.C
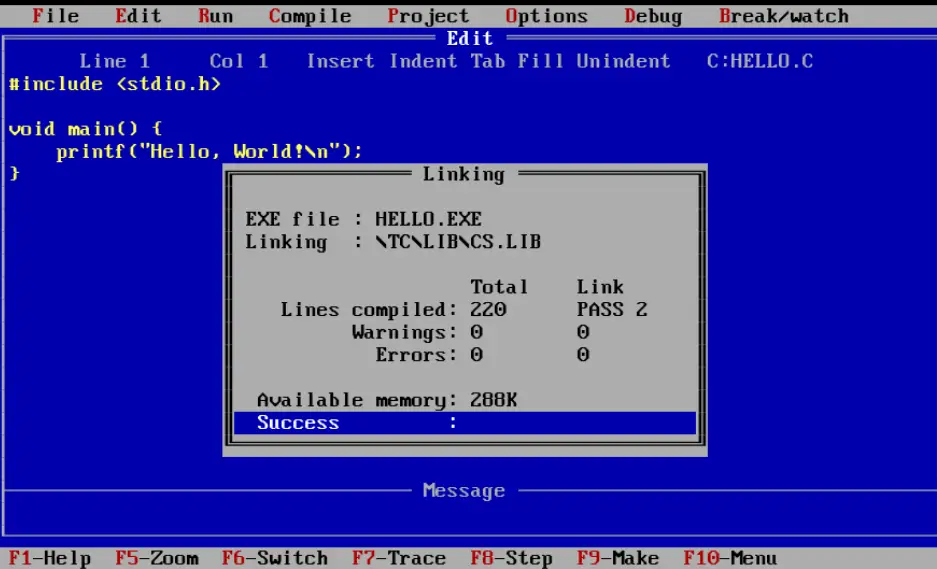
We need to compile this file (COMPILE > BUILD ALL). When compilation completes, you should see a ‘Success’ message:
If we check the contents of the working directory, we can see that there is a new file: HELLO.EXE
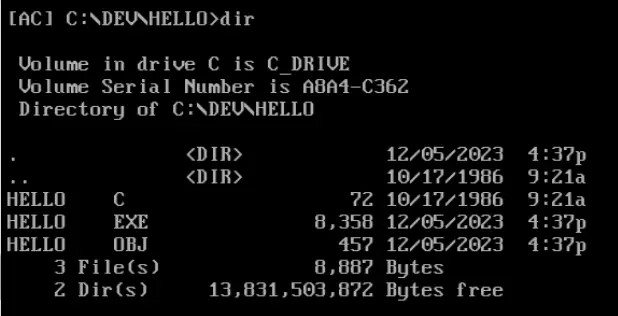
If you open this file with ‘edit’, then you should see that the first two characters are ‘MZ’. These are the magic bytes for the file, which help identify the file type.
Let’s go back to the C:. We want to change the magic bytes of the backup file AC2023.bak:
From the readme file, we learned that the magic bytes correspond to hex ’41 43′. We need to convert these bytes to ASCII in order to change them using the DOS editor (because the DOS editor displays the contents in ASCII format).
Using an online hex to ASCII converter (you can just Google it), we can find out the actual ASCII text that we will need to use:
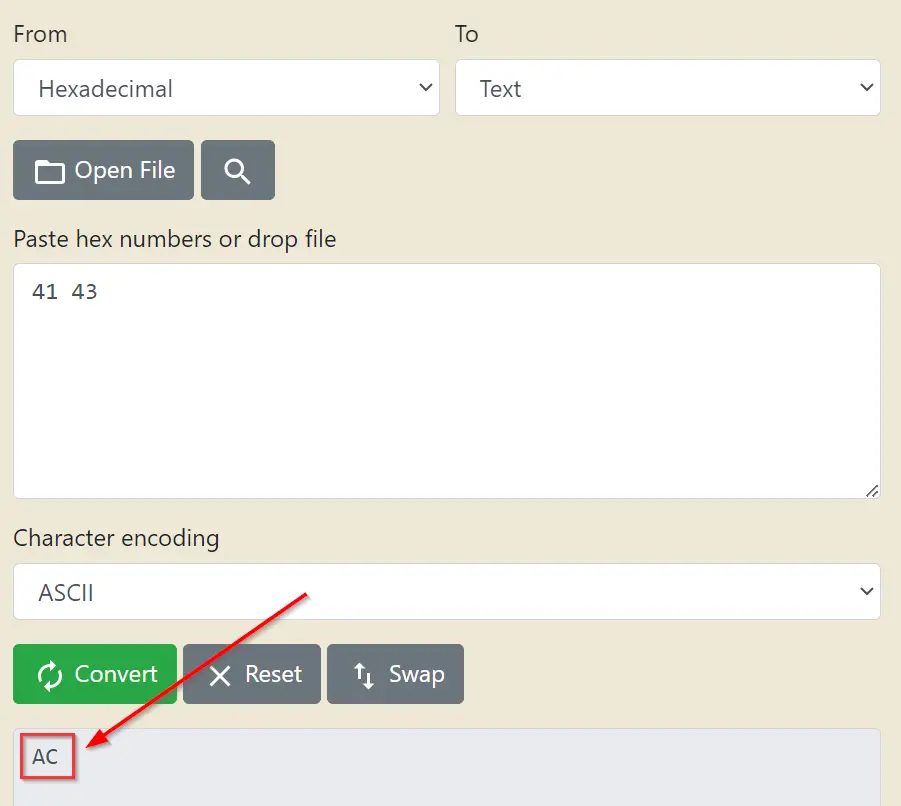
Now we can use the DOS editor to open AC2023.BAK:
edit AC2023.BAK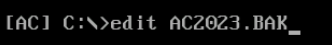
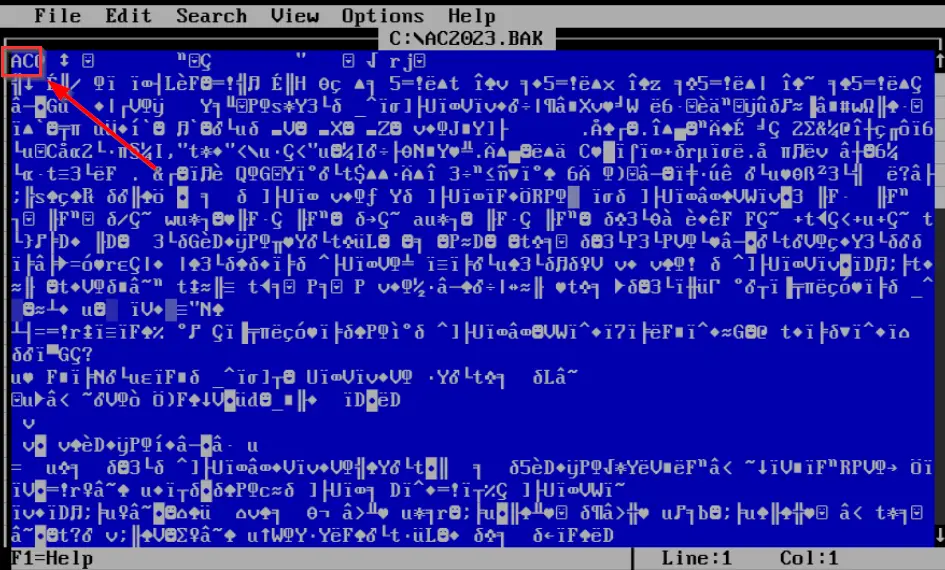
Save this and exit.
Now let’s run BackupMaster3000 on this file to retrieve the flag!
C:\TOOLS\BACKUP\BUMASTER.EXE AC2023.EXE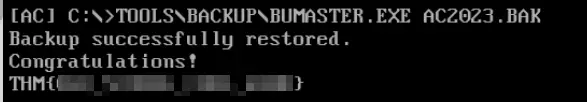
Answer (Highlight Below):
THM{0LD_5CH00L_C00L_d00D}
Conclusion
Day 5 of the TryHackMe Advent of Cyber 2023 challenge was all about the joy of exploring legacy systems like DOS. In addition to playing around with DOS, we were also introduced to important concepts in IT and security like backups, compiling a C program, and magic bytes.