What is a Malicious URL? How to Check URLs for Malware
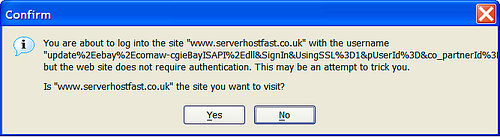
As our reliance on computers and the internet grows, the threat of cybercrime grows with it. Malicious actors employ various tactics to compromise our online security, and one of the most common tactics is the use of malicious URLs.
A malicious URL is a web address that can be used to deliver malware, perform phishing attacks, or accomplish other harmful activities. Malicious URLs can be used to compromise our systems, data, personal information (PII) and identities. Understanding what a malicious URL is and how to identify and check URLs for potential threats has become increasingly important for safeguarding our online experiences.
In this article, we will cover the topic of malicious URLs in detail. We’ll cover exactly what they are, how they can be used to achieve a variety of harmful goals, and how you can protect against this prevalent cybersecurity threat. By the end of this article, you will understand why malicious URLs are one of the most threatening online security issues, and how to defend against them.
What is a Malicious URL?
A malicious URL is a web address that has been created or modified to deceive users and initiate harmful activities. The URL by itself is not necessarily dangerous, but many different types of cyber attacks can be executed when the victim clicks on a link to the URL.

Malicious URLs are often used by scammers, fraudsters, and black-hat (i.e. malicious) hackers. Ethical hackers may also use similar techniques when providing testing services for companies, such as internal penetration tests or red team assessments.
Malicious URLs often resemble legitimate websites, and can be highly sophisticated and convincing. A well-designed malicious website looks real, but behind the scenes there may be a variety of nefarious activities occurring. These may include phishing, downloading of malware, gathering sensitive information, or establishing a direct connection (e.g. a ‘shell’) between your machine and a hacker’s. Clicking on a malicious URL can compromise a user’s security, privacy, and sensitive data and may result in a total compromise of the machine. Skilled hackers may then be able use the compromised machine as a foothold to gain further access to other machines on an internal network (called pivoting) or other services on the network, such as file shares or databases.
It’s important for us to avoid malicious URLs because no amount of defense is adequate to protect against them. Firewalls and antivirus software are essential, but they can’t protect you from all potential attacks if you click on the wrong link. Clicking on a malicious link is akin to letting a Trojan horse through the gates of your castle; what good are the castle walls if you let the enemy in through the front door?
The Anatomy of a URL
Let’s start by learning what a URL is.
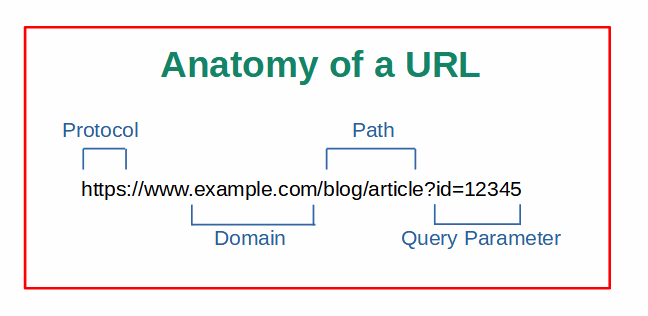
A URL, or Uniform Resource Locator, is a string of characters that functions as the address of a resource on the internet. It is a fundamental component of web browsing and is used to identify and locate webpages, files, images, videos, and other online resources. A typical URL consists of several components:
- Protocol: The beginning of a URL specifies the protocol to be used for accessing the resource. This includes “http://” or “https://” for webpages, “ftp://” for file transfers, or “mailto://” for email addresses.
- Domain Name: The next part of the URL represents the unique name of the website or server hosting the resource. For example, electronicsreference.com is the domain name of this site. Websites can also have subdomains, including the common ‘www’ subdomain.
- Path: Unless you are on the homepage of a website, chances are that the webpage you are on has a path following the domain name. For example, this article has a path of ‘what-is-a-malicious-url’. The path indicates the specific location of the resource within the website’s directory structure, and it generally corresponds to an actual object (i.e. a directory or a file) on the web server.
- Query Parameters: These are optional parameters that provide additional information to the server and can modify the behavior or content of the resource.
Let’s take the URL “https://www.example.com/blog/article?id=12345,” as an example. The protocol is https, the domain name is “example.com,” the path is “/blog/article,” and the query parameter is “id=12345.”
When you click on a link, the site’s URL is what tells your web browser where to go. It’s important that the sites we visit are trustworthy because when we visit a website, we are really creating a connection between our computer and another computer somewhere else in the world. Even though this type of connection is somewhat limited by itself, it can be exploited in various ways by bad actors. Malicious URLs are one of the most frequent and important tactics used by malicious actors.
What Makes a URL Malicious?
A malicious URL poses as a regular one, but is secretly being used to initiate a harmful activity via malicious code. If you visit the web page with a browser, you may or may not notice something strange.
Malicious sites are designed to deceive users by mimicking legitimate websites, often leading unsuspecting individuals to click on them and unknowingly expose themselves to a wide range of attacks. Examples of malicious URLs include phishing URLs, malware URLs,
It’s important to realize that malicious URLs have little or no power to perform harmful activities unless they are actually clicked on. Once clicked, these harmful links may direct users to fraudulent websites, phishing sites, or initiate the download of malicious software onto their devices, compromising their security and privacy.
Well-designed malicious websites and web applications often look identical to regular ones, and may even be clones or imitations of the legitimate website that you though you were visiting. In fact, one of the keys to a successful malicious website is that it looks just like a regular one. For example, scammers create phishing websites in order to execute phishing scams. A fake website can be used to steal credit card or other personal data and may be set up with a fake login designed to look like the real thing.
Bad actors have various methods of convincing us to click on malicious links. These include phishing emails, text messages, and even advertisements. Like the malicious URLs themselves, the success of these methods depends on how convincing they are. Skilled cyber criminals do their research on potential targets and craft custom emails or messages using resources like social media to improve their odds of success. Although this may seem frightening, it’s also easy to protect yourself and your assets by following simple rules that we will cover in this article.
It’s crucial to understand the red flags and indicators that can help identify potentially dangerous links. By scrutinizing the URL structure, looking for misspellings or inconsistencies, and assessing the website’s credibility, we can make informed decisions about whether or not to proceed.
Fortunately, there are effective methods to check URLs for malware and protect ourselves from falling victim to these malicious traps. Implementing robust security measures, such as using reliable antivirus software and keeping it up to date, is essential. Additionally, employing browser extensions or plugins that analyze URLs for potential threats and block access to suspicious websites can further enhance our protection. We’ll cover the most important steps for protecting yourself against malicious URLs in the following section.
Protecting Against Malicious URLs
Protecting yourself from malicious URLs is crucial in safeguarding your online security and privacy. By following a few essential practices, you can dramatically reduce the risk of falling victim to harmful web addresses. Here are some best practices to protect yourself from malicious URLs:
1. Always be skeptical: Exercise caution when clicking on links, especially those you find in emails or messages, on social media platforms, or on unfamiliar websites. Examine the URL before clicking. Look for misspellings, unusual characters, IP addresses, unique URLs or inconsistencies that might indicate malicious intent.
2. Hover before you click: Always hover your mouse cursor over a link before clicking it. This action will reveal the actual URL destination in a tooltip or status bar at the bottom of the browser. Verify that the URL matches the expected website or resource before proceeding. The beginning of the URL is typically the most important; if you don’t recognize then the domain then you shouldn’t click on the link. You can also copy and paste the link into a text file for further analysis, but be careful not to accidentally click it.
3. Use a malicious URL checker: There are multiple free URL checkers available online, such as https://www.virustotal.com/gui/home/url, or https://www.ipqualityscore.com/threat-feeds/malicious-url-scanner. Virustotal.com is a well-known highly vetted site for analyzing potentially malicious files and URLs. But keep in mind that these tools won’t catch everything; skepticism is always the best defensive tool.
3. Keep your software updated: Outdated software is one of the most common reasons for all kinds of cybersecurity attacks and breaches. Stay o)n top of updates for your operating system, web browser, and security software to ensure that you have the latest security patches and protections against known vulnerabilities.
4. Use reputable security software: Install and maintain reliable antivirus and anti-malware software on your devices. For Windows devices, just make sure that Defender is running and that the defaults are all turned on. This includes real-time protection, which uses behavioral and heuristic detections to detect malicious activity. These programs help detect and block malicious URLs and other threats, and form an important layer of defense that should always be used.
5. Use browser and application security features: Take advantage of built-in security features in your web browser. Enabling options like phishing and malware protection can help by warning you or blocking access to potentially harmful websites. Choosing a secure browser is also an important factor; there has been a lot of debate around ‘which browser is the most secure’, but many cybersecurity professionals recommend Firefox. In addition, use two-factor authentication wherever possible to add another layer of security around your application logins.
6. Use strong password policies: Passwords are rarely stored in ‘clear-text’, so even if an attacker gains access to your system, they typically still have to crack your passwords. Make them hard or impossible to crack, and limit the risk if they are cracked by using the following practices:
a. Use long, randomized passwords – a reputable password manager is crucial for this. Many cybersecurity professionals use and recommend random passwords with 30 characters or more if possible.
b. Don’t reuse passwords – again, use a password manager to help with this.
c. Don’t store passwords in cleartext on your machine – keep your most important passwords written down in a secure location or in an offline file (i.e. a file on a system or hard drive that is never exposed to the internet).
7. Educate yourself: Stay informed about the latest threats, phishing techniques, and common indicators of malicious URLs. Educate yourself and your family members or colleagues about safe browsing practices to enhance overall awareness.
Prevention is key when it comes to protecting yourself from malicious URLs. By adopting these proactive measures and maintaining a cautious approach, you can minimize the risk of falling victim to online scams, malware infections, and other cyber threats.
In Summary: Defending Against Malicious URLs
Understanding the nature of malicious URLs and implementing effective strategies to check URLs is essential in today’s digital world.
We’ve discovered that a malicious URL is a web address deliberately designed to initiate harmful activities, such as phishing attacks, malware downloads, and fraudulent redirections. These URLs often mimic legitimate websites, making it crucial to exercise caution and employ robust defense mechanisms.
We have also discussed some of the most important proactive measures to defend ourselves against malicious URLs. These include staying vigilant and skeptical, hovering before clicking, keeping software updated, using reputable security software, using strong passwords, enabling browser security features, and continuously educating ourselves about the latest cyber threats.
By implementing these best practices, we can dramatically reduce the risk of falling victim to online scams, malware infections, and other cybercrimes. We can navigate the digital landscape with confidence and protect our sensitive information and digital identities.
It’s important to remember that online security is an ongoing effort, and staying informed about emerging threats and evolving defense mechanisms is crucial. It isn’t difficult, but it does take some effort. By prioritizing digital safety, we can all enjoy a safer online experience and protect ourselves from the ever-present dangers of malicious URLs.