Advent of Cyber 2022 – Day 3 Walkthrough

Day 3 is all about open source intelligence (OSINT) and GitHub. OSINT is a huge subject, and there are several (surprisingly large) books on this topic alone.
GitHub is a version control service that many developers and hackers use every single day. For example it is common to find cybersecurity tools or even exploit code on GitHub. As Day 3 will cover, GitHub can also be used as a valuable source of OSINT when developers accidentally expose sensitive information.
One topic that is also covered, albeit subtly, is WordPress. The GitHub repo that we explore contains files for a WordPress installation. WordPress is the most common content management system (CMS) system used on websites today, and a significant percentage of websites are built using WordPress.
Question 1
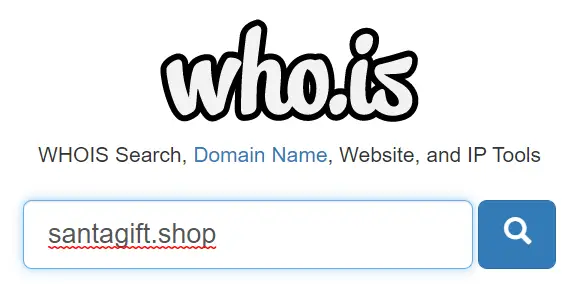
What is the name of the Registrar for the domain santagift.shop?
Registrar information can be found with a whois lookup. We can use a free site like https://who.is/
Answer (Highlight Below):
NAMECHEAP INC
Question 2
Find the website’s source code (repository) on github.com and open the file containing sensitive credentials. Can you find the flag?
We need to find the santagift.shop repository on GitHub. Go to github.com and search for ‘santagift.shop’. You should see something like the following:
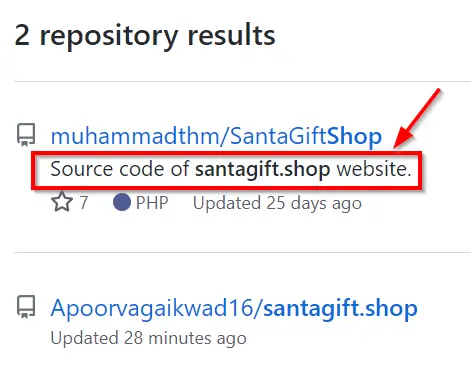
Note that the top results says that it is the “Source code of santagift.shop website”.
Next, let’s look through the repository to find the file containing the flag.
It looks like this repository contains the files for a WordPress installation. WordPress is one of the most common platforms (called a content management system, or CMS) for creating websites.
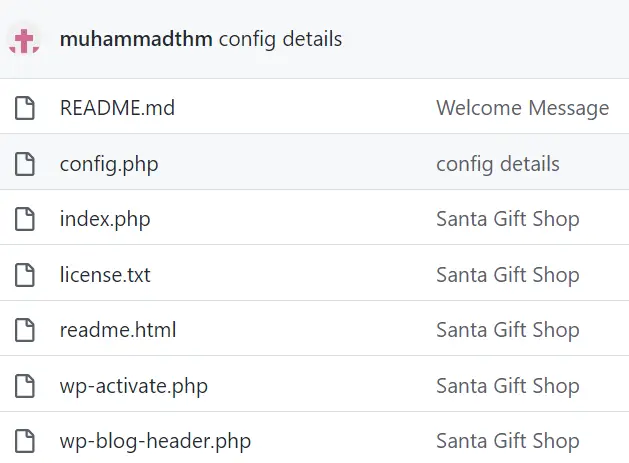
Credentials are often stored in files that contain user information, database information, and configuration files.
If you’re struggling to find the right file, continue on with the next question for now (as the answer to the next question if the file that you need).
Answer (Highlight Below):
{THM_OSINT_WORKS}
Question 3
What is the name of the file containing passwords?
HINT: It’s a configuration file.
Answer (Highlight Below):
config.php
Question 4
What is the name of the QA server associated with the website?
This can be found in README.md:
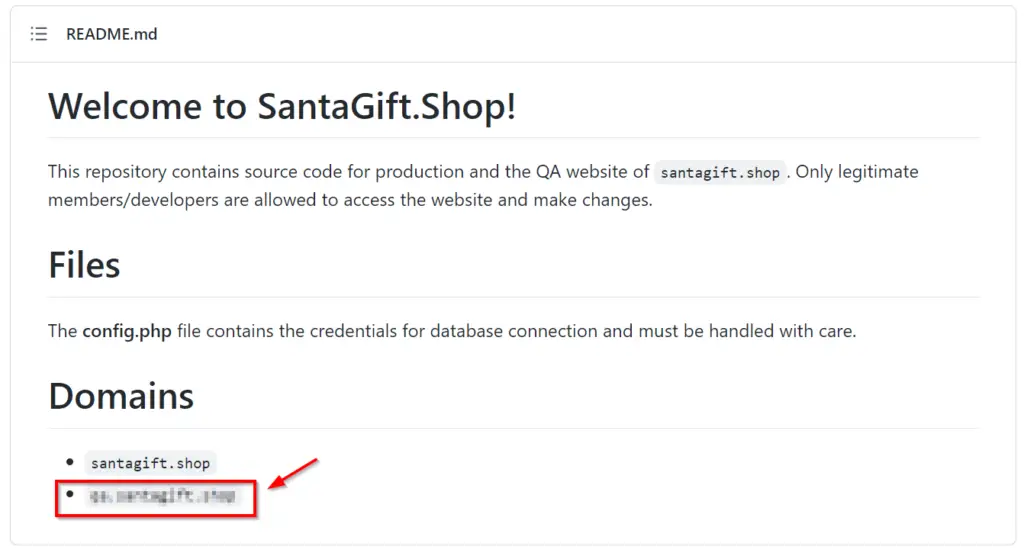
If you look closely, you might notice that README.md tells us where to find database credentials.
Reading through readme’s and code is the best way to learn about a project. GitHub repositories are often meant to be collaborative. This means that developers often include good written descriptions about a project as well as comments in the code.
Answer (Highlight Below):
qa.santagift.shop
Question 5
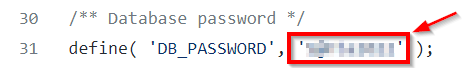
What is the DB_PASSWORD that is being reused between the QA and PROD environments?
This can be found in the same config file that we found the flag in.
A Note regarding CREDENTIALS:
Credentials are one of the things we are after as hackers. They are the keys to the kingdom. Anytime we can exfiltrate data during a CTF, we should.
However this is not the case in bug bounty. In general, we should avoid any kind of data exfiltration unless it is part of the testing scope. Bug bounty program scope normally does not allow this and hunters are wise to avoid any actions that could potentially lead to legal troubles.
Answer (Highlight Below):
S@nta2022
Conclusion for Advent of Cyber 2022 Day 3
This room covered a brief overview of open source intelligence (OSINT) and GitHub. A subtle but brilliant detail was the use of the GitHub repo containing files for a WordPress installation. WordPress is one of the most common platforms used for developing websites so I thought this was a nice touch.