Advent of Cyber 2022 – Day 4 Walkthrough
Question 1
What is the name of the HTTP server running on the remote host?
Before performing any scanning, I like to start an engagement by pinging the target:
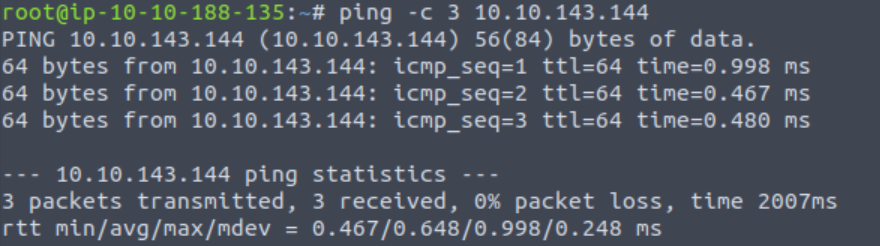
This confirms that I can connect to the target and also gives us potential information about the OS: a TTL of 64 indicates that the target is most likely running Linux.
TryHackMe is looking for the name of the server (software), which can be found using many types of scan including nikto:
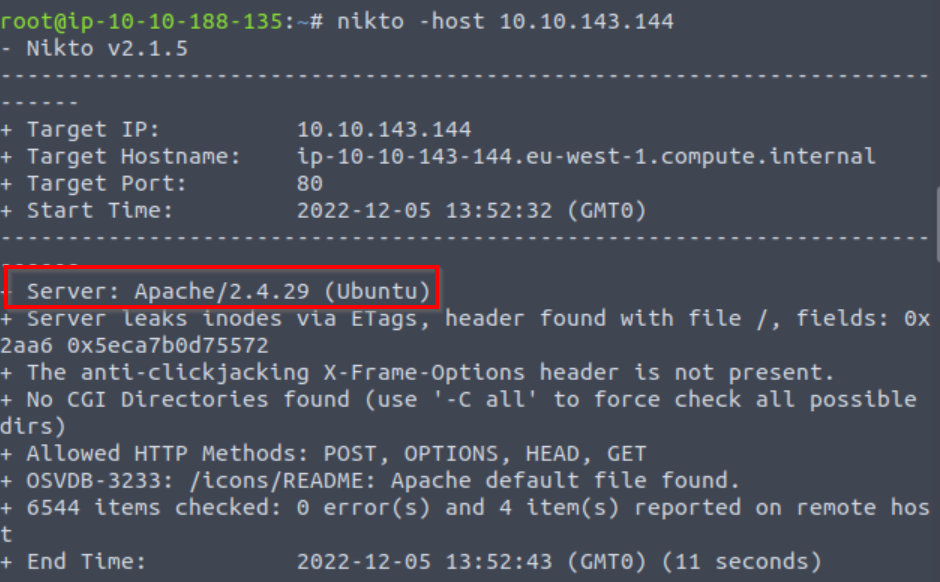
Answer (Highlight Below):
Apache
Question 2
What is the name of the service running on port 22 on the QA server?
This is the standard service that runs on port 22, and is identified by an nmap scan.
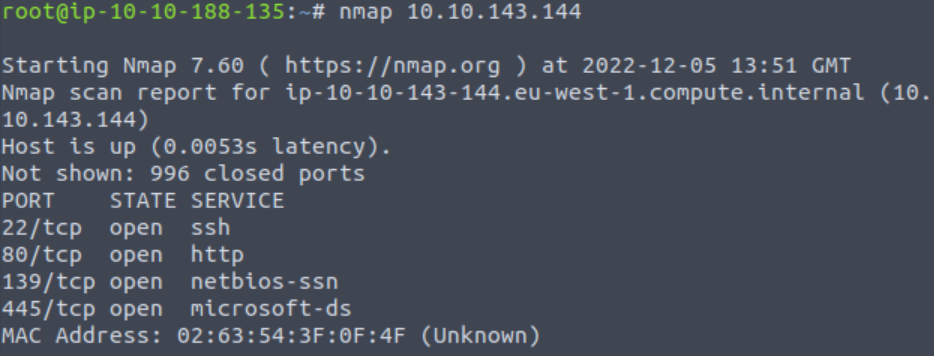
Answer (Highlight Below):
SSH
Question 3
What flag can you find after successfully accessing the Samba service?
Samba is a file share service that can sometimes be exploited for sensitive information.
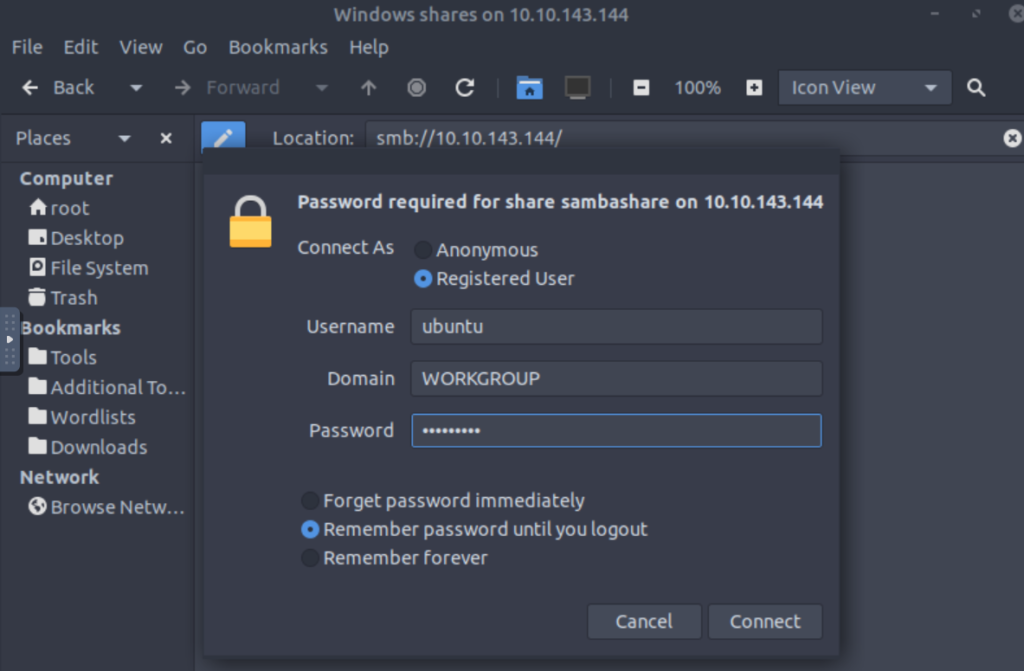
TryHackMe gives us good information telling us how to connect to Samba:
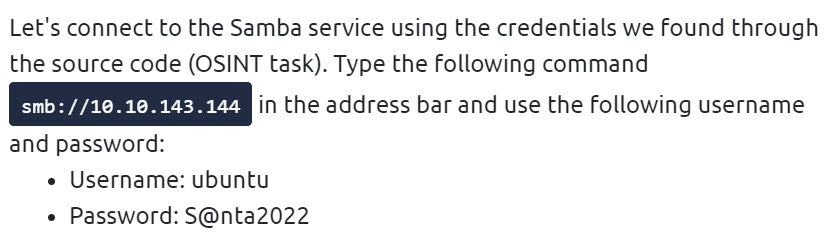
Use the IP for your target machine (mine will be different) and make sure to use the credentials supplied:
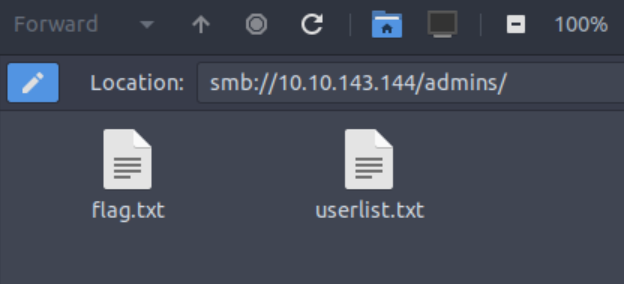
The flag is in the admin directory:
Answer (Highlight Below):
{THM_SANTA_SMB_SERVER}
Question 4
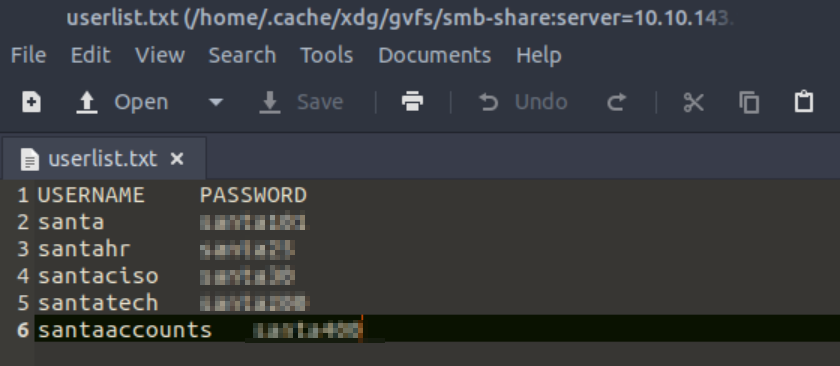
What is the password for the username santahr?
This can be found in userlist.txt (also in the admin folder on the Samba share).
Answer (Highlight Below):
santa25