Advent of Cyber 2022 – Day 6 Walkthrough

Advent of Cyber 2022 Day 6 is all about learning how to analyze suspicious emails.
TryHackMe gives us an email file to analyze. We need to parse through its’ headers, decode an encoded Message ID, extract the email attachment, calculate its’ sha256 hash sum, and use the hash to analyze whether or not the file is malicious.
It may seem like these tasks are difficult, but they’re actually easier than they sound. Let’s get hacking!
Question 1
What is the email address of the sender?
To solve the Day 6 challenges, we’ll need to start up an instance of the virtual machine (VM) provided by THM. This can be done using the green ‘Start Machine’ button at the top of the Day 6 writeup.
The answer to the first few questions can be found in the Urgent:.eml file on the Desktop of the VM.
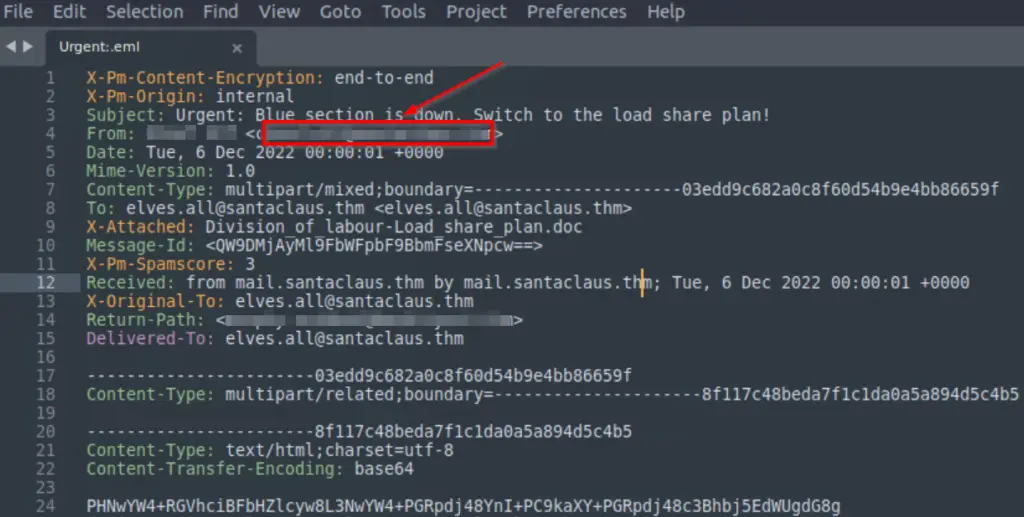
Answer (Highlight Below):
Question 2
What is the return address?
The return address can also be found in the Urgent:.eml file.
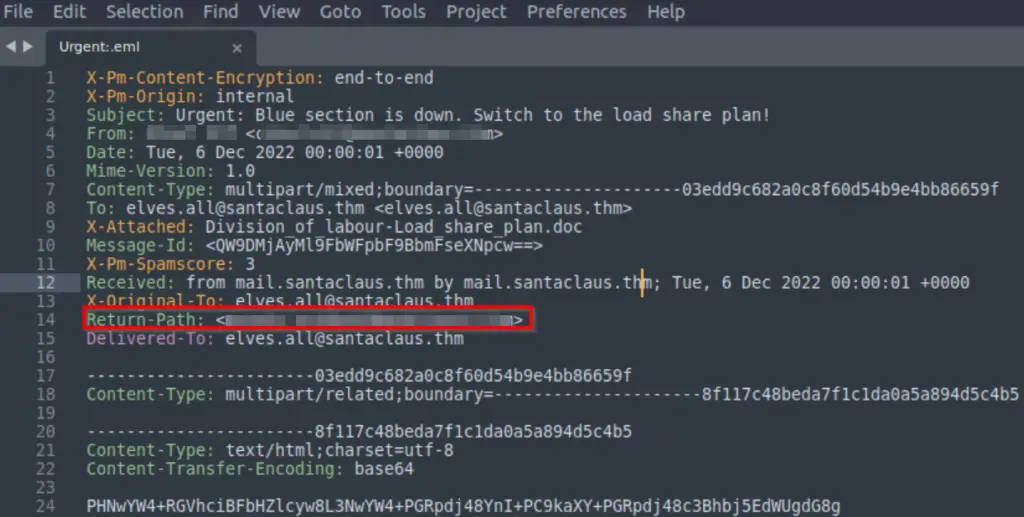
Answer (Highlight Below):
Question 3
On whose behalf was the email sent?
The email was sent on behalf of the person identified in the ‘From:’ field.
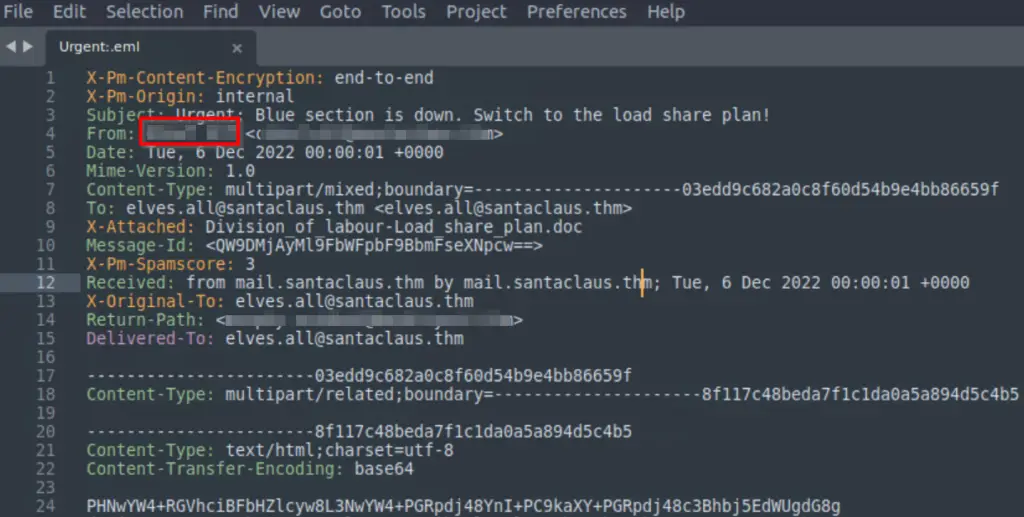
Answer (Highlight Below):
Chief Elf
Question 4
What is the X-spam score?
Look for the X-Pm-Spamscore field in the Urgent:.eml file.
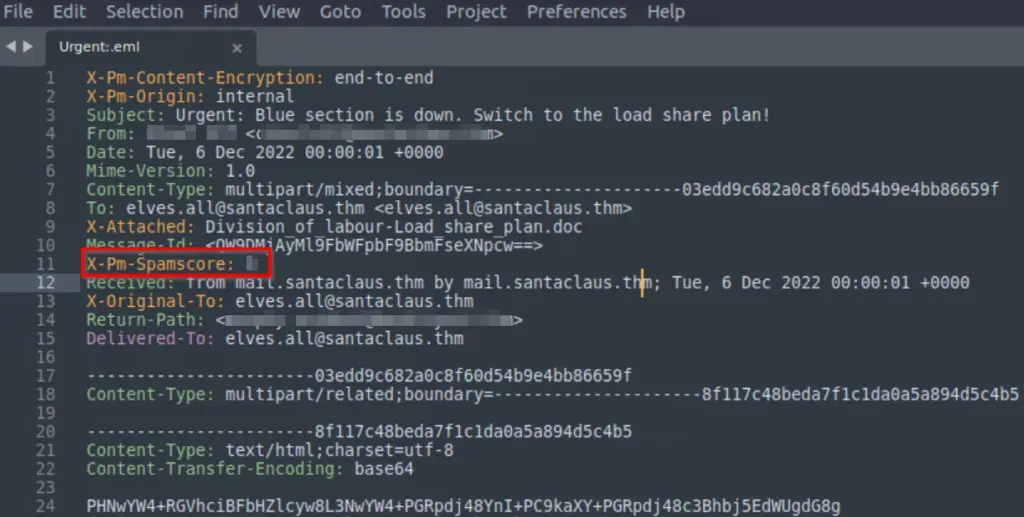
Answer (Highlight Below):
3
Question 5
What is hidden in the value of the Message-ID field?
We need to decode the value in the Message-Id field:
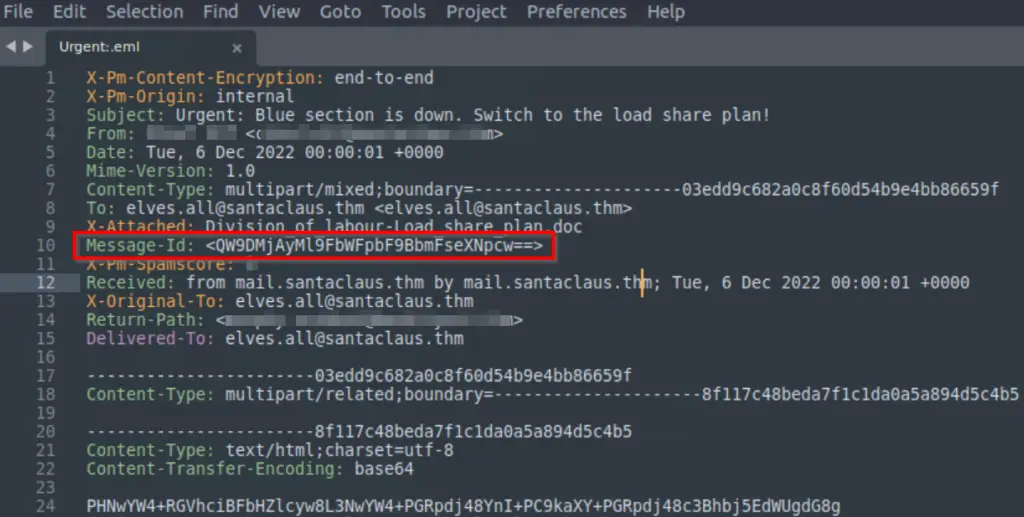
There is a fantastic tool called CyberChef that can be used to automatically decode this:
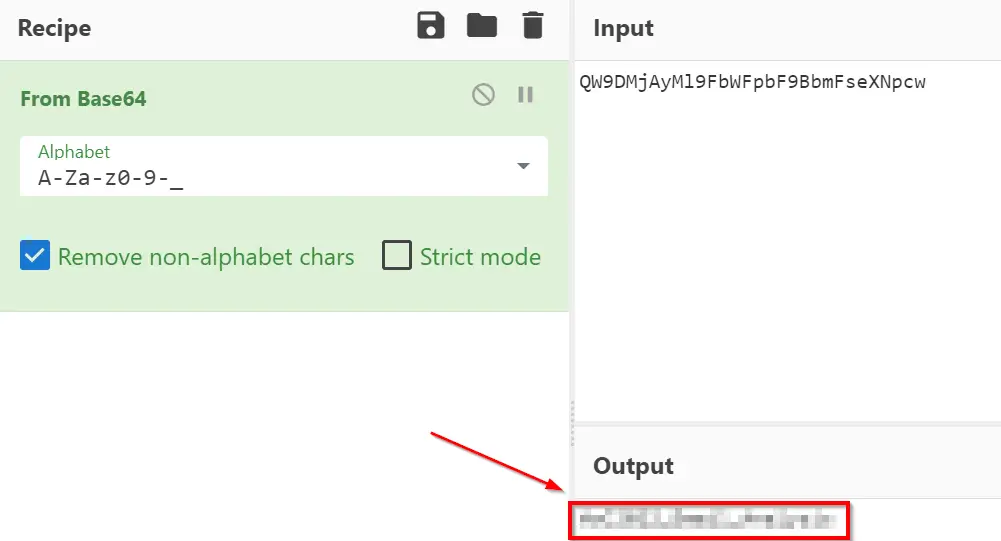
Answer (Highlight Below):
AoC2022_Email_Analysis
Question 6
Visit the email reputation check website provided in the task.
What is the reputation result of the sender’s email address?
Follow the link to https://emailrep.io/ and enter the email address ‘[email protected]’.
Answer (Highlight Below):
RISKY
Question 7
Check the attachments.
What is the filename of the attachment?
The filename of the attachment can be found in the Urgent:.eml file. Details can be found starting on line 38:
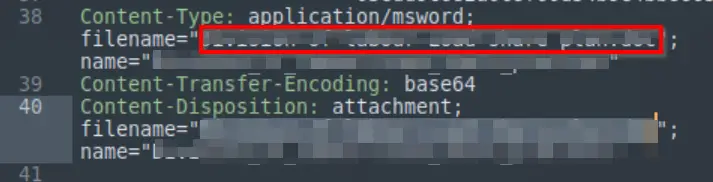
Answer (Highlight Below):
Division_of_labour-Load_share_plan.doc
Question 8
What is the hash value of the attachment?
To get the hash value, first we need to extract the attachment from the Urgent:.eml file. We can use the emlAnalyzer tool to do this.
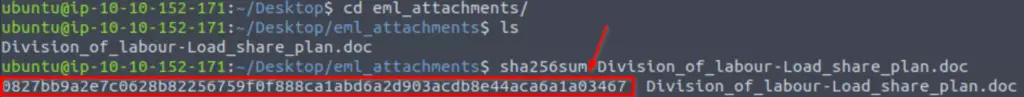
Navigate to the Desktop directory and enter the command:
emlAnalyzer –extract-all -i ./Urgent\:.eml
You should see a new directory on the Desktop called ’eml_attachments’:
Answer (Highlight Below):
0827bb9a2e7c0628b82256759f0f888ca1abd6a2d903acdb8e44aca6a1a03467
Question 9
Visit the Virus Total website and use the hash value to search.
Navigate to the behaviour section.
What is the second tactic marked in the Mitre ATT&CK section?
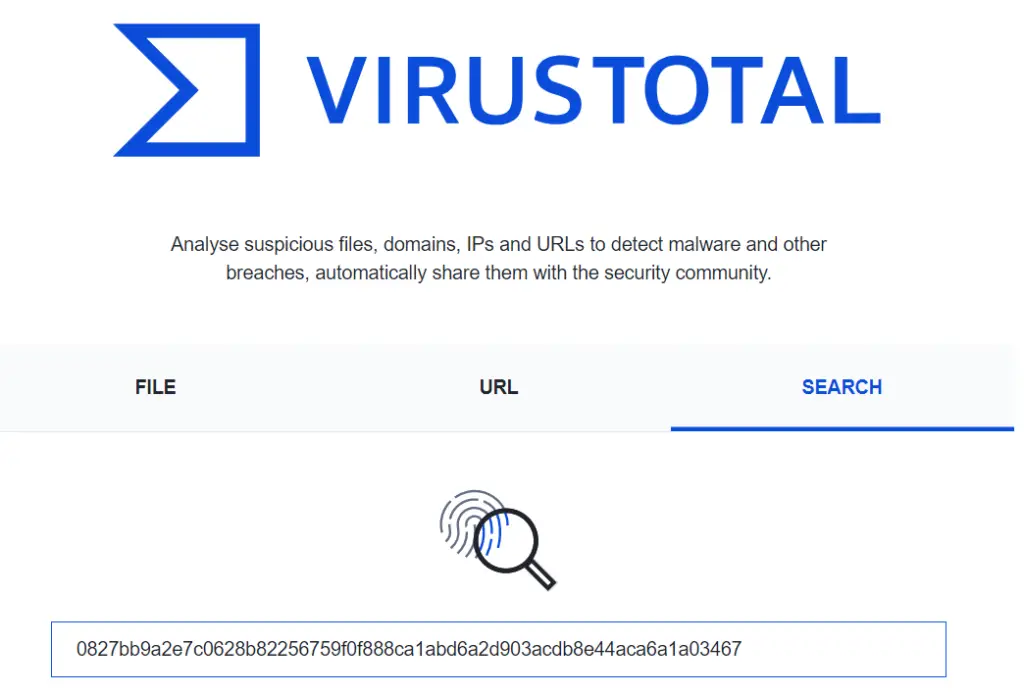
Navigate to https://www.virustotal.com/gui/home/search and enter the hash value in the search bar:
Go to the ‘Behavior’ tab and scroll down to the ‘Mitre ATT&CK Tactics And Techniques’ section:
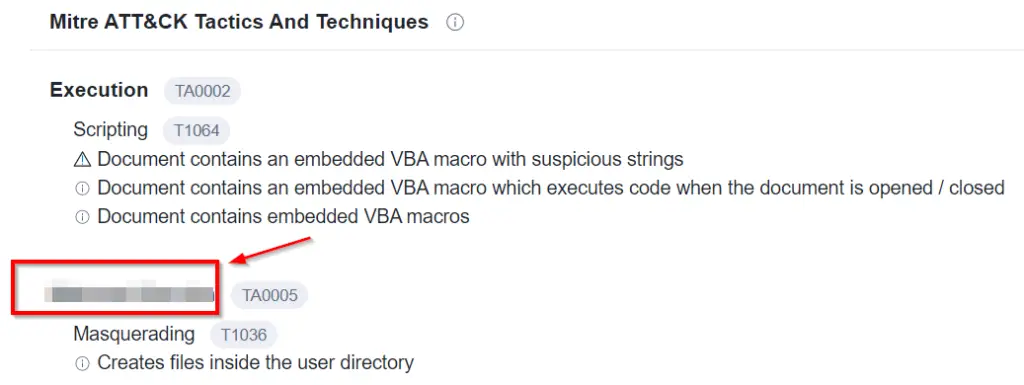
Answer (Highlight Below):
Defense Evasion
Question 10
Visit the InQuest website and use the hash value to search.
What is the subcategory of the file?
Navigate to https://labs.inquest.net/ and click on the ‘INDICATOR LOOKUP’ button to search by a hash, then enter the hash into the Lookup field:
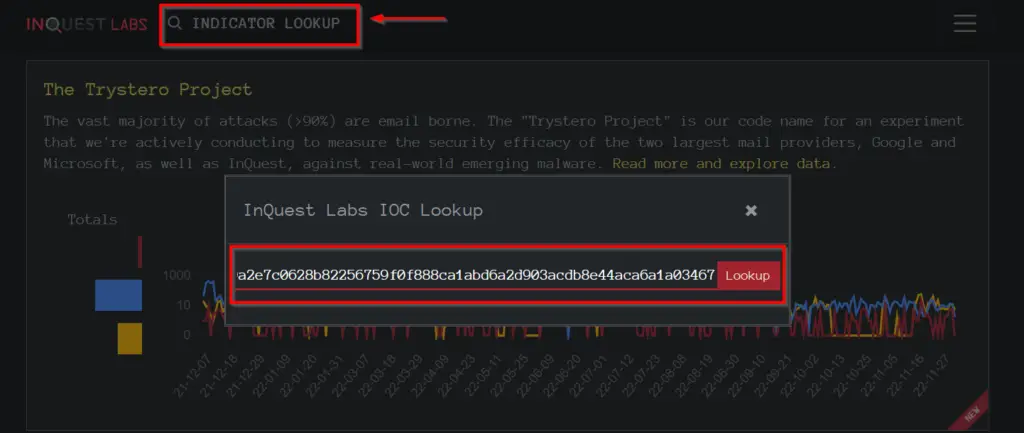
I only had one result returned. Select the returned result and look for the ‘Subcategory’ field:
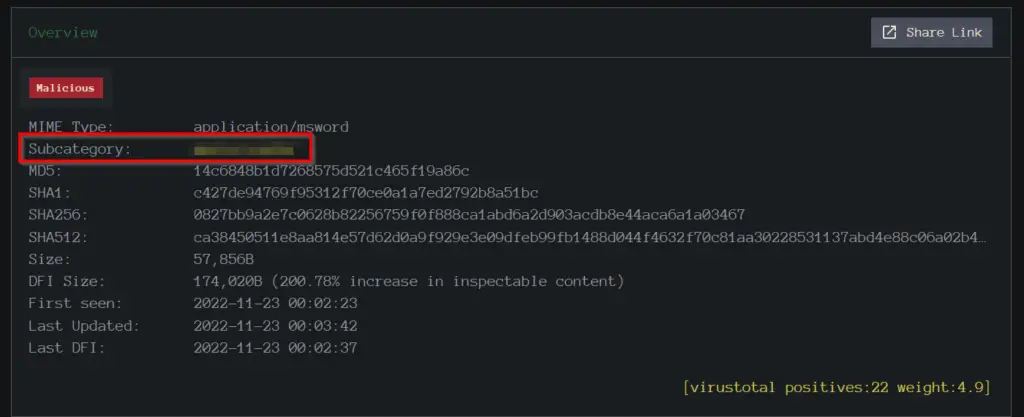
Answer (Highlight Below):
macro_hunter
Conclusion – TryHackMe Advent of Cyber Day 6 Walkthrough
This is my favorite room so far. I thought that the challenges did a great job of exposing a variety of important topics in a super interesting and fun way.
As always, a hearty thanks to TryHackMe and everyone involved.