Advent of Cyber 2022 – Day 7 Walkthrough

Advent of Cyber 2022 Day 7 is all about CyberChef. Today’s tasks involve using CyberChef to perform multiple functions used to decode and clean up encoded text.
CyberChef is an incredible useful tool for this, and Day 7 gives us a lot of great practice.
Question 1
What is the version of CyberChef found in the attached VM?
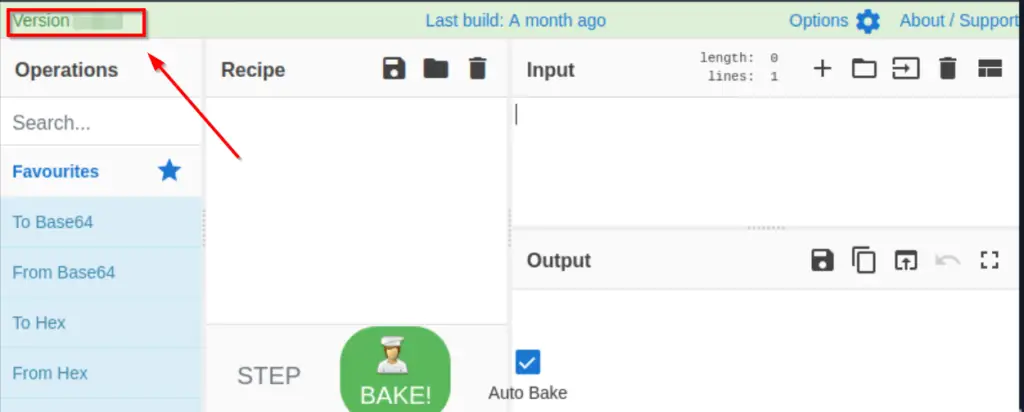
Open Mozilla and click the CyberChef bookmark. The version number is on the top left side of the app UI.
Answer (Highlight Below):
9.49.0
Question 2
How many recipes were used to extract URLs from the malicious doc?
There are several steps that we need to take in order to extract the URLs.
After dragging the file into the Input field, we need to go through the following:
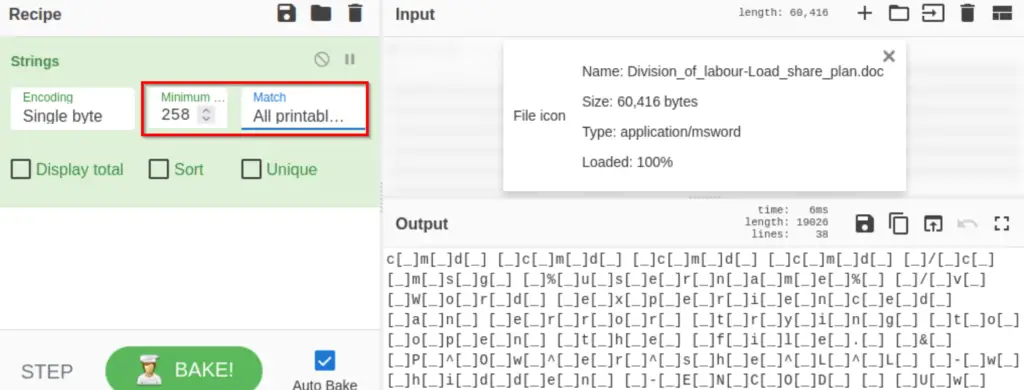
Search for and select the ‘Strings‘ function, and add it the Recipe field by dragging it over. Change Match to ‘All printable chars’, and increase the Minimum field until the noise is eliminated. The output should look like the following; this should occur at a Minimum string length of 258.
Notice that the above output contains a lot of the repeated pattern ‘[_]’. To remove these characters, we can add a ‘Find/Replace‘ function to the Recipe field, and enter the Regex [\[\]\n_]
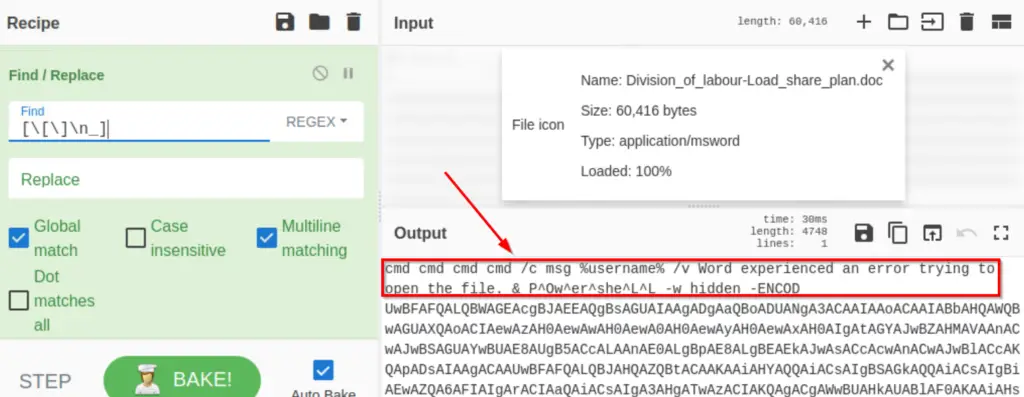
The beginning of the Output looks like it is part of a PowerShell script. We need to remove this text to isolate the base64 string below. Add a ‘Drop bytes‘ function and select a Length of 124.
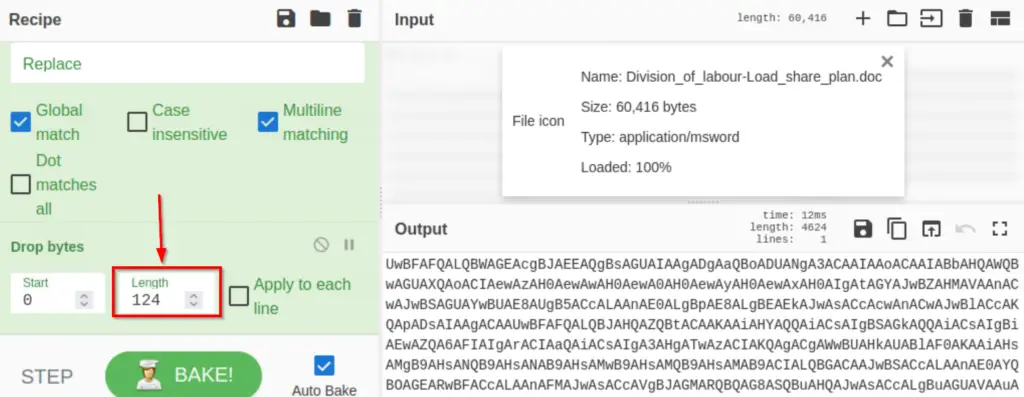
Next, let’s decode the base64 string using the ‘From Base64‘ function.
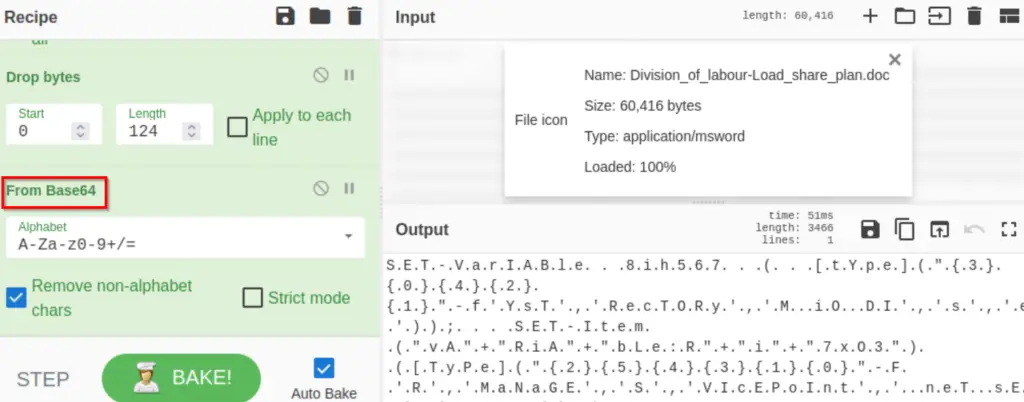
We can make this much more readable by decoding the text. The default Powershell encoding is UTF-16LE. We can use the ‘Decode text‘ function to do this:
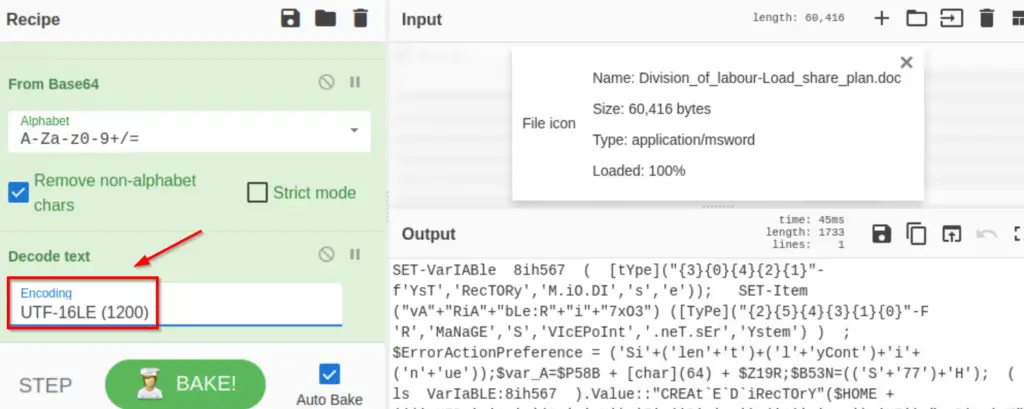
This is looking better but there’s still a lot of extra characters that we can remove. Use a ‘Find/Replace’ function and enter the regex [‘()+'”`] into the Find field:
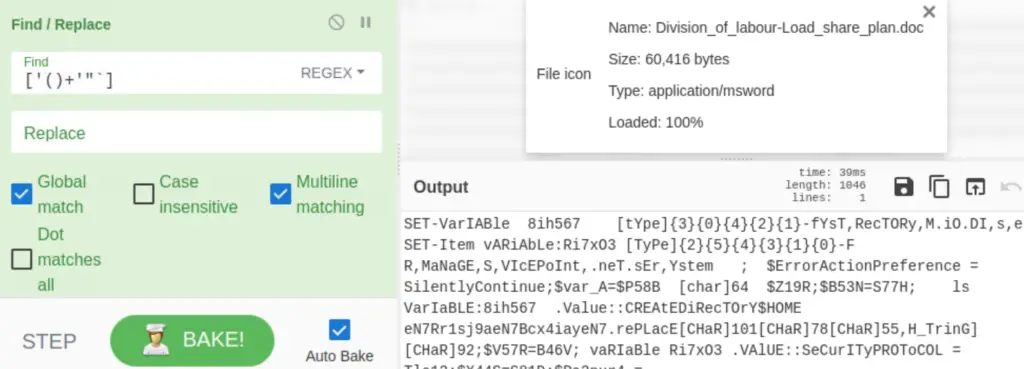
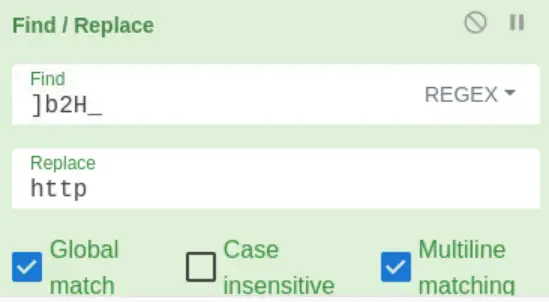
If we analyze the output, we can see that there appears to be a string ‘]b2H_’ in front of each domain reference. Using a ‘find/replace‘ function, enter the regex ]b2H_ into the Find field, and http as the string for it to be replaced with.
Next, we can extract the URLs using an ‘Extract URLs’ function. What remains is a few URLs:
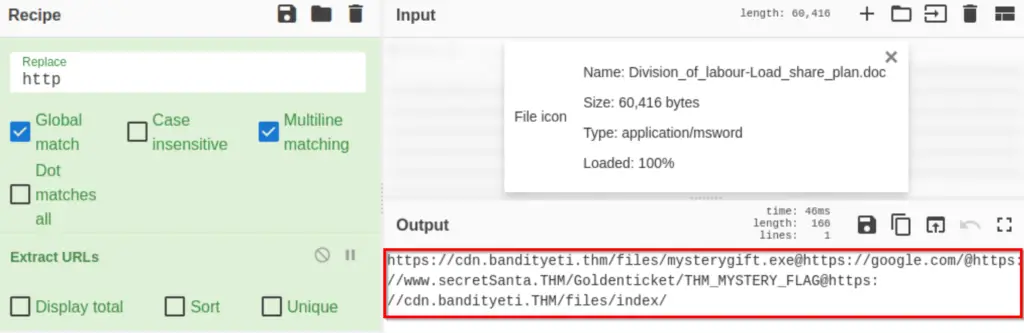
Note that the above output is a list of URLs separated by an ‘@’ character. We can use the ‘Split’ function to remove the @ characters and separate each URL with a new line:
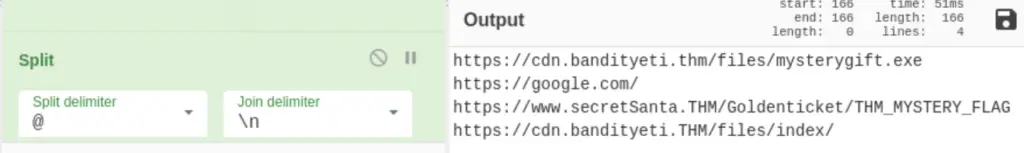
Next, we can render the URLs harmless using the ‘Defang URL‘ function:
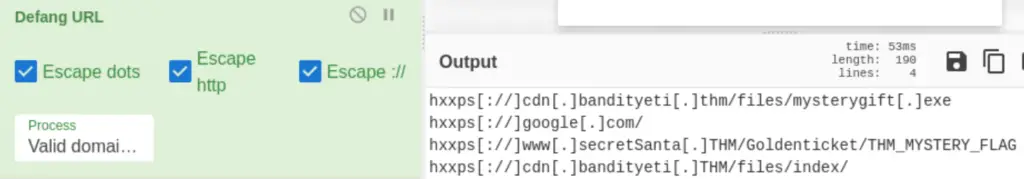
Answer (Highlight Below):
10
Question 3
We found a URL that was downloading a suspicious file; what is the name of that malware?
Look for the suspicious executable:
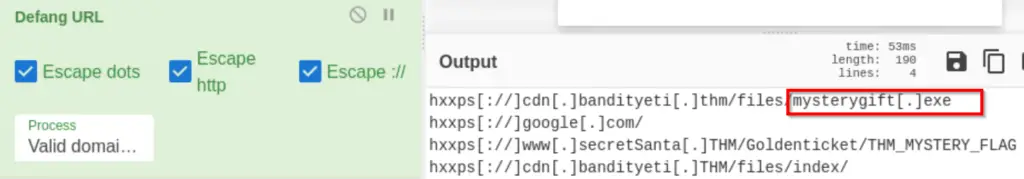
Answer (Highlight Below):
mysterygift.exe
Question 4
What is the last defanged URL of the bandityeti domain found in the last step?
Copy and paste the last of the defanged URLs in the output:
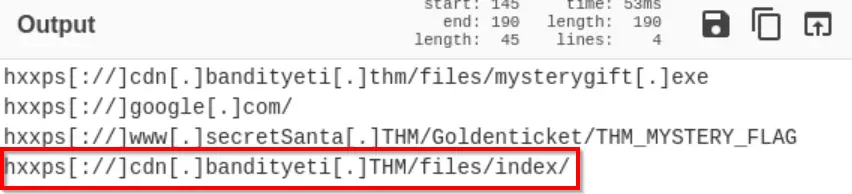
Answer (Highlight Below):
hxxps[://]cdn[.]bandityeti[.]THM/files/index/
Question 5
What is the ticket found in one of the domains? (Format: Domain/<GOLDEN_FLAG>)
The Output also contains the flag:
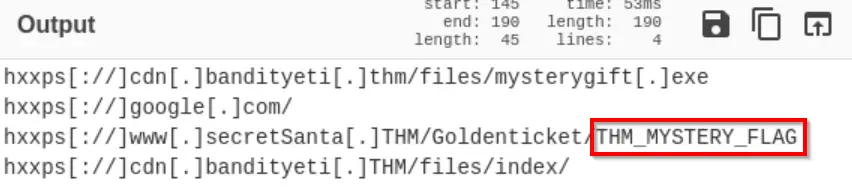
Answer (Highlight Below):
THM_MYSTERY_FLAG