Advent of Cyber 2022 – Day 8 Walkthrough

Advent of Cyber 2022 Day 8 covers an essential but often ignored topic within the cybersecurity community: blockchain technologies.
Blockchain is an interesting technological ecosystem, and it remains to be seen what the long term impact of it will be. It can be hard to sort our what is ‘real’ and what is hype when it comes to these technologies. However, getting a handle on how the basic technology works isn’t actually that difficult.
I spent about a month and a half earlier this year diving into solidity and smart contract writing and security. Over that time, I developed a sense of the space, although eventually I decided to refocus my efforts on established technologies. However one thing that is clear is that security is incredibly important in the blockchain space because contracts are immutable. This means that any security flaws in a smart contract are very difficult to correct after the fact. In turn, this led to the development of smart contract auditing – currently, a well paying niche within the world of cybersecurity.
Note: In my walkthrough for Question 1, I will cover how to import, compile, deploy, and interact with smart contracts using Remix. In Question 2, I cover only the steps required to get the flag. I’m hoping this will help add clarity to the walkthrough as a whole.
Question 1
If not already completed, download the zip folder attached to this task, and open Remix in your preferred browser.
Remix is a great IDE for quickly interacting with contracts on a blockchain or building out small projects in Solidity. For larger projects, we would probably work with something like Hardhat.
To get started, we’ll need to download and extract the solidity files from TryHackMe.
Next, import the files into Remix:
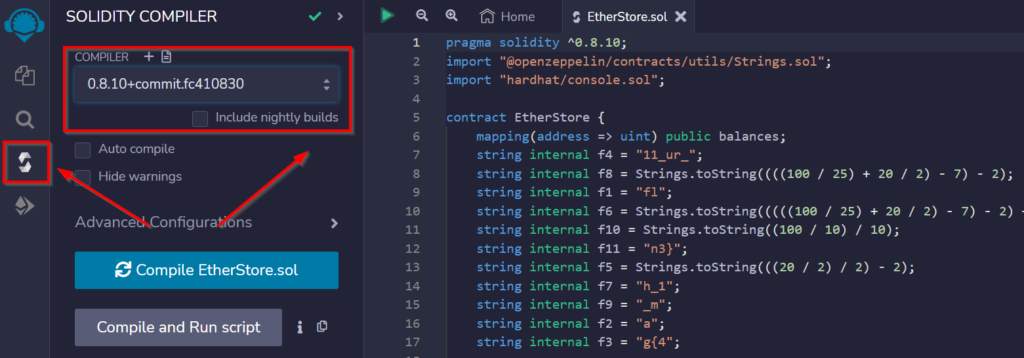
Next, compile both files using the ‘0.8.10+commit…’ standard per the instructions from TryHackMe:
Now if you scroll down, you should see the following options under ‘Deployed Contracts’:
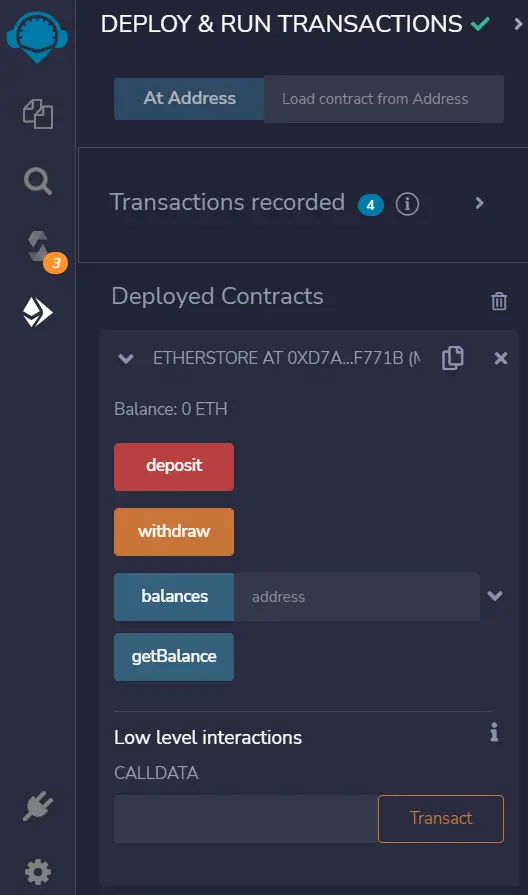
If we click the ‘getBalance’ button, we should find that this contract has a current balance of 0 ETH:
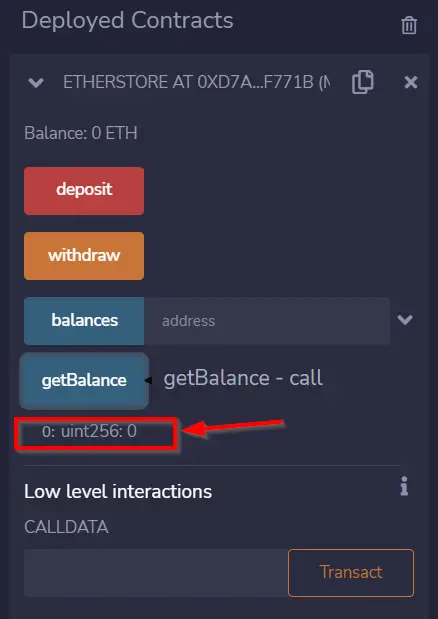
Let’s interact with this contract by depositing some ETH.
First, enter a value to be deposited into the ‘value’ field:
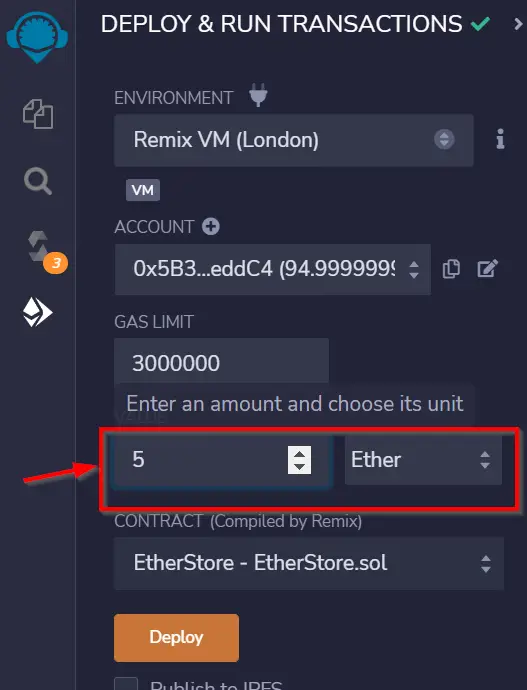
Next, scroll down and press the ‘Deposit’ button. Now if we check the balance again, we will find that we have a large amount of currency. This is because if you followed the instructions above, you will have deposited several ETH, but Remix is giving us our balance in Wei, which is a much smaller unit.
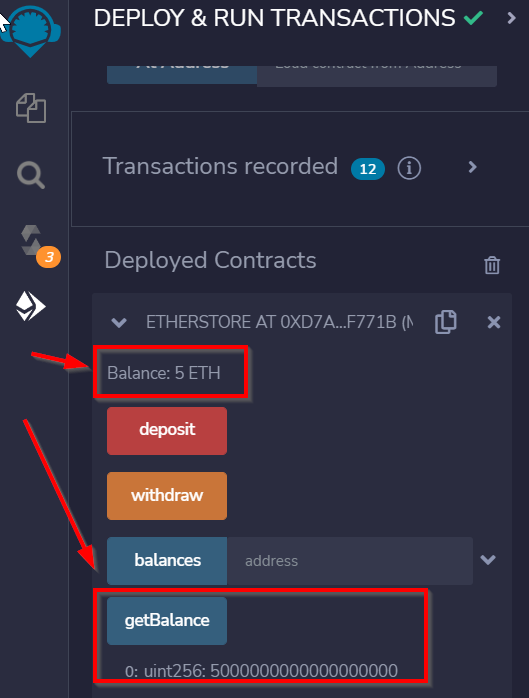
Answer:
No answer needed
Question 2
What flag is found after attacking the provided EtherStore Contract?
Now that we know how to interact with a contract, we can move on to using one contract to attack another. You can think of this similarly to how we use one machine (e.g. the TryHackMe AttackBox) to attack another machine.
In this case, we will be using Attack.sol to attack EtherStore.sol.
- Select a new account.
2. Deploy the EtherStore.sol contract.
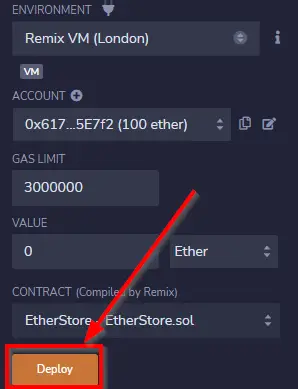
3. Deploy the Attack.sol contract, pasting in the address of the EtherStore.sol contract:
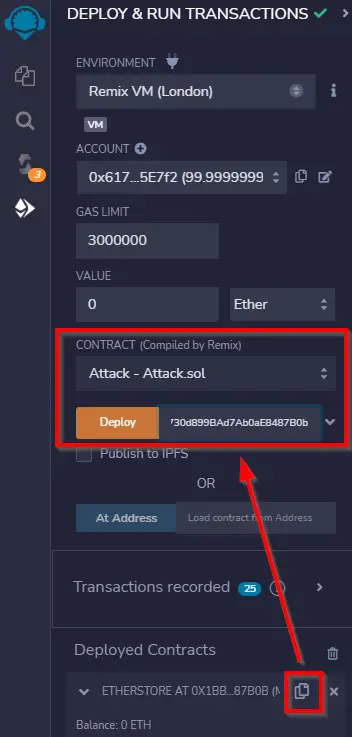
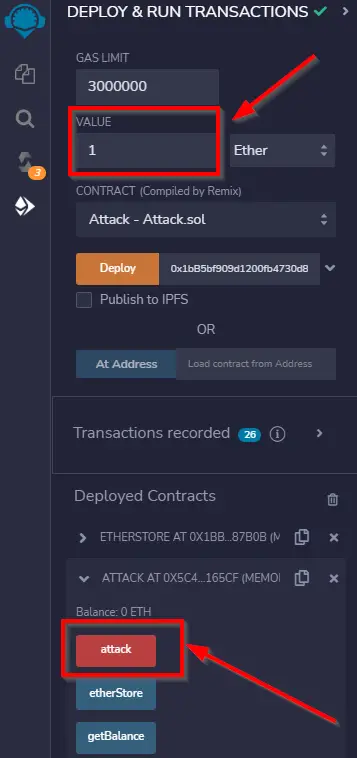
4. Enter a value of ‘1’, and scroll down to Deployed Contracts. Use the red ‘attack’ button to launch the attack:
You should see a confirmation of the transaction and the flag printed in the console.log:
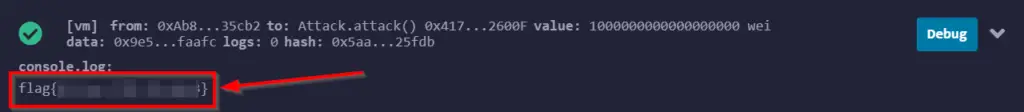
Answer (Highlight Below):
flag{411_ur_37h_15_m1n3}