TryHackMe – Advent of Cyber 2023 Day 8

Day 8 of TryHackMe’s Advent of Cyber 2023 challenge is focused on disk forensics.
To complete the tasks for Day 8, we will need to step into the role of a forensics lab analyst and take a look at a USB drive loaded with malware and other interesting clues. To analyze the drive and its contents, we get hands-on with AccessData FTK Imager – a powerful forensics tool that can be used to preview recoverable data from disks of any kind.
TryHackMe Advent of Cyber 2023 can be found here.
About This Walkthrough/Disclaimer:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by requiring a manual action (highlighting) to obtain all solutions. This way you can follow along without being handed the solution if you don’t want it. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
Walkthrough for TryHackMe Advent of Cyber 2023 Day 8
Question 1
What is the malware C2 server?
Open FTK Imager and add the physical drive as instructed. We can explore the drive in the Evidence Tree pane (on the upper left side of the GUI).
Within the ‘DO_NOT_OPEN’ directory, we can see a number of files in the File List.
We can find the malware C2 server inside secretchat.txt:
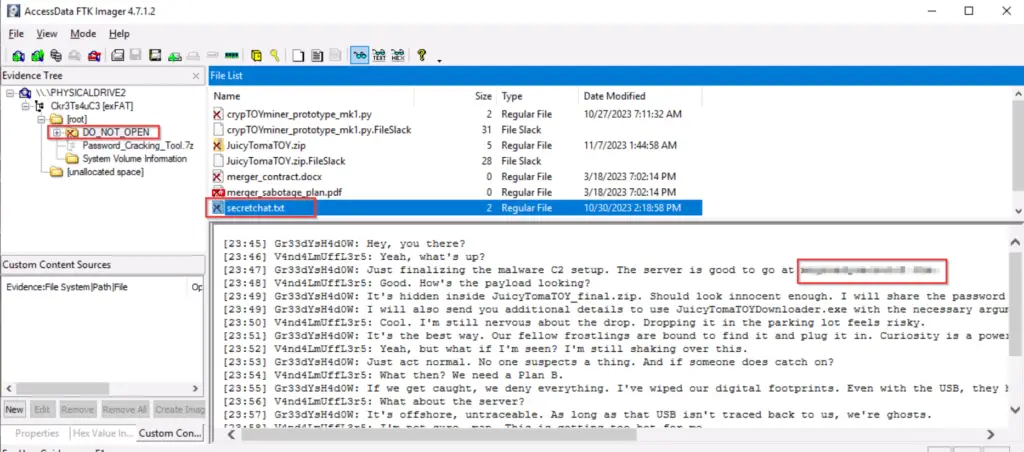
What is C2 software?
As an (extremely brief) overview, C2 stands for ‘Command and Control’. C2 software is used to remotely control sessions from hosts that have been compromised. They are extremely common in the world of red teaming as well as malware/ransomware/spyware etc. There are companies that develop, manage, and sell C2 software – sometimes to malicious actors or oppressive regimes. Once a victim’s machine is compromised by a piece of malware, it will attempt to connect back to a C2 server. From the perspective of the bad actor, they will then be able to send commands, run scripts, or open shells on the infected machine.
Answer (Highlight Below):
mcgreedysecretc2.thm
Question 2
What is the file inside the deleted zip archive?
Continuing to explore the drive, we can see a zip file called JuicyTomaTOY.zip. If you click on this zip file, you can see the contents below:
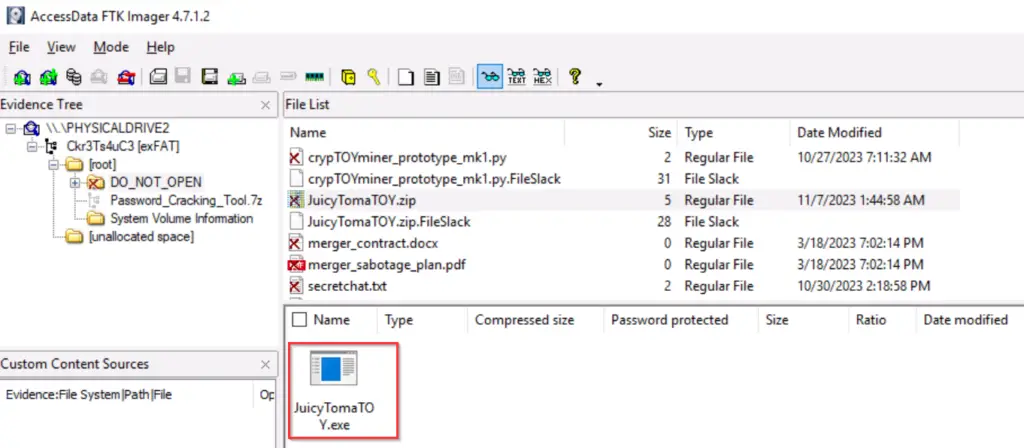
Answer (Highlight Below):
JuicyTomaTOY.exe
Question 3
What flag is hidden in one of the deleted PNG files?
Under the root directory, we see a number of .png files:
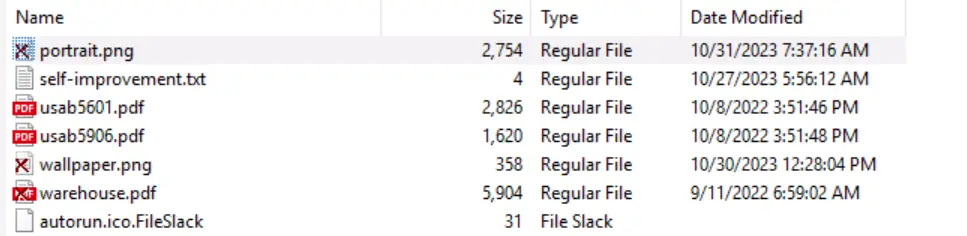
Let’s go through these files. We can use the ‘find’ feature – either by pressing ‘ctrl+f’ or right-clicking inside the viewer pane and selecting ‘find’:
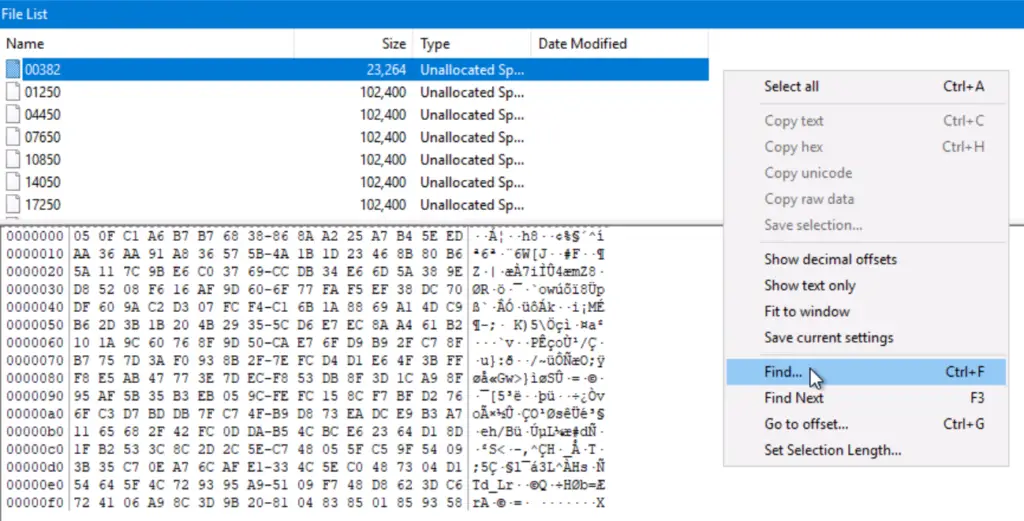
If we search through the .png files in the root directory, we will find that portrait.png contains the flag:
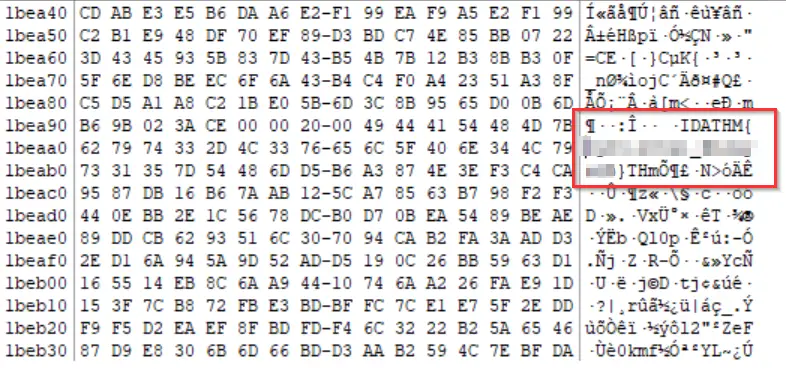
Answer (Highlight Below):
THM{byt3-L3vel_@n4Lys15}
Question 4
What is the SHA1 hash of the physical drive and forensic image?
To get the SHA1 hash, we can use the ‘File > Verify Drive/Image’ option.
First, select ‘PHYSICALDRIVE2’ from the Evidence Tree:
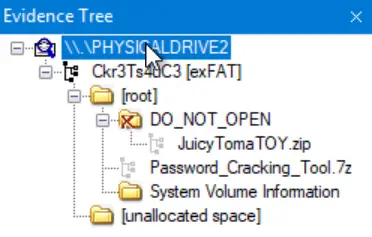
Select ‘File > Verify Drive/Image’ and allow it to complete. You will then be provided with the MD5 and SHA1 hashes:
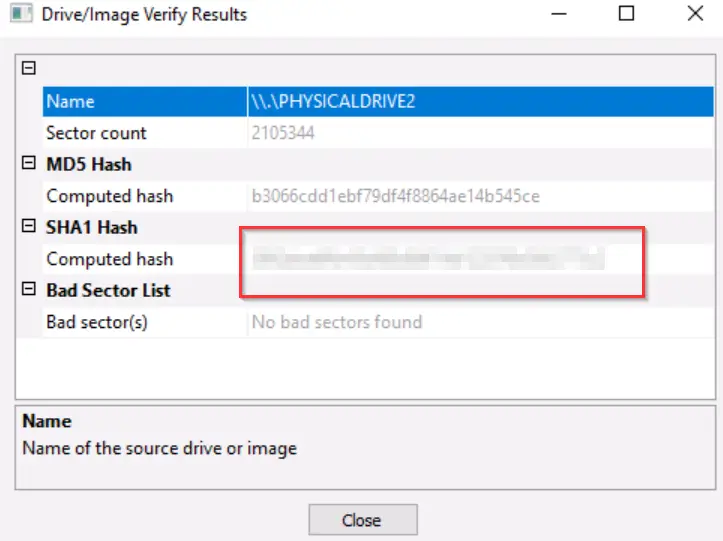
Answer (Highlight Below):
39f2dea6ffb43bf80d80f19d122076b3682773c2
Conclusion
I really liked the backstory and supporting elements of today’s activities. USB-based attacks are still a thing (although many security teams have learned to defend against this approach), and I couldn’t help but imagine this Christmas-meets-Mr. Robot scenario.
I also enjoyed the C2 element that was included. This definitely increased the element of realism of the challenges.