Advent of Cyber 2022 – Day 2 Walkthrough

This page contains a walkthrough for the Advent of Cyber 2022, Day 2 challenges on TryHackMe.
Day 2 is all about logs, and we are introduced to a two crucial Linux commands along the way: ls and grep. These are both extremely common and important.
The most difficult part of Day 2’s challenge is probably learning how to read a log file and search it using grep.
In the walkthrough below, I cover how to solve the challenges and also some quick tips to make the most of the lessons contained within Day 2.
Question 1
Ensure you are connected to the deployable machine in this task.
To deploy the machine, click the green ‘Start Machine’ button:
It will take a couple of minutes for the machine to spin up. I got an error at first, but this was resolved by refreshing the page.
Answer:
No answer needed
Question 2
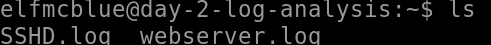
Use the ls command to list the files present in the current directory. How many log files are present?
The ls command is one of the most commonly used and will quickly become second nature. It can be used alone (without any flags).
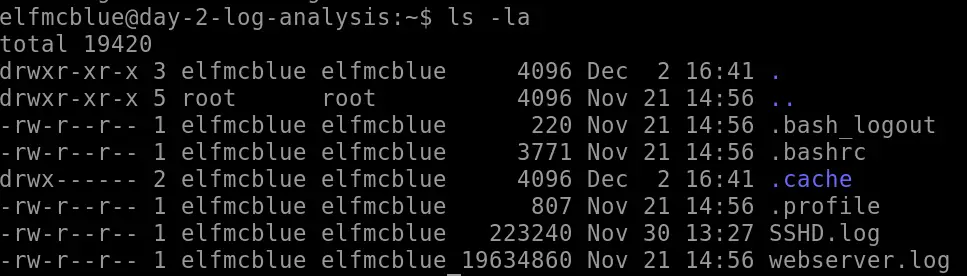
The -la flags are very common as well; this gives us lots of helpful details about the files and directories in the directory.
Another tip: we aren’t limited to the present working directory. We can use the ls command to list the contents of other directories, such as the root directory:
ls /root
Answer (Highlight Below):
2
Question 3
Elf McSkidy managed to capture the logs generated by the web server. What is the name of this log file?
We used the ls command to list the logs:

Which of these seems likely to be the web server log?
Answer (Highlight Below):
webserver.log
Question 4
Begin investigating the log file from question #3 to answer the following questions.
We will be using the grep command to investigate the log file in the next few questions.
Answer (Highlight Below):
No answer needed
Question 5
On what day was Santa’s naughty and nice list stolen?
We have to find a good way to parse through the log file. I started by doing a simple grep search and looking at the output.
Since we are looking for Santa’s list, I decided that a good first search might be for the term “Santa”:
grep -i "santa" webserver.log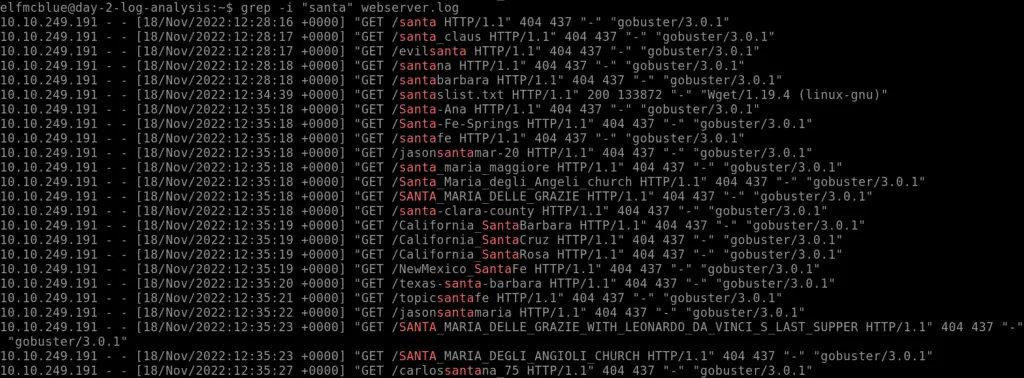
There’s actually a lot here to unpack. If we start with the column on the left, we’ll notice that every single GET request came from the same IP. This may or may not be normal, but there seems to be a lot of activity from a single actor which can often indicate malicious activity.
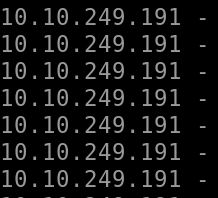
Next, I noticed from the timestamp that this all occurred on the same day, and within a short period of time.
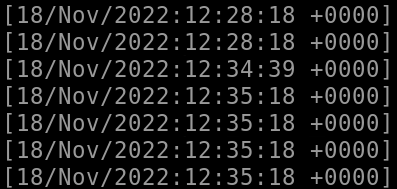
The next column shows us that these were all GET requests, which is a common type of http request. It’s what we use to fetch web pages. In this case, I also noticed that many of these requests had similar names, and there were a bunch containing the term ‘Santa’. This would be strange behavior, and I am immediately thinking that we are looking at the logs from a brute force attack.
Finally, I noticed that nearly all of them contained the term ‘gobuster’. I happen to know that gobuster is a brute force directory enumeration tool, but a quick Google search would also turn this up.
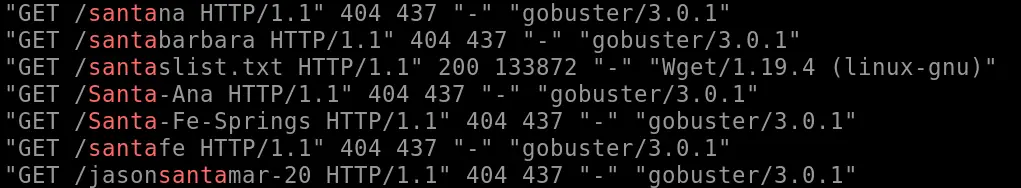
We can piece together these details to confirm with a high degree of certainty, that a malicious actor at the IP address that we found, attacked our webserver using gobuster.
Now that we know this occurred, we can just look up to see what day of the week the attack took place was in order to answer the question.
Answer (Highlight Below):
friday
Question 6
What is the IP address of the attacker?
See the results of the grep search (from the last question).
Answer (Highlight Below):
10.10.249.191
Question 7
What is the name of the important list that the attacker stole from Santa?
The previous search (using the term ‘Santa’) actually worked, but there is another clever way to solve this problem.
If you look closely at the results, you might notice that the string ‘404’ was included on (almost) every line. This is the infamous HTTP 404 error, indicating that a page was not found at that location.
Since we are looking for a document that The Bandit Yeti was able to attack, we can do a search to find the lines that don’t contain the 404 code. I did try searching for 200 type codes, but I found that there was way too much data returned to effectively parse.
Instead, I performed a grep search that would exclude resources that returned a 404 during the gobuster attack:
grep -i -v 404 webserver.logIn this command, the ‘-v’ option tells grep to perform an invert-match search. Check out the man page for more details!
Warning: Spoiler in the image below
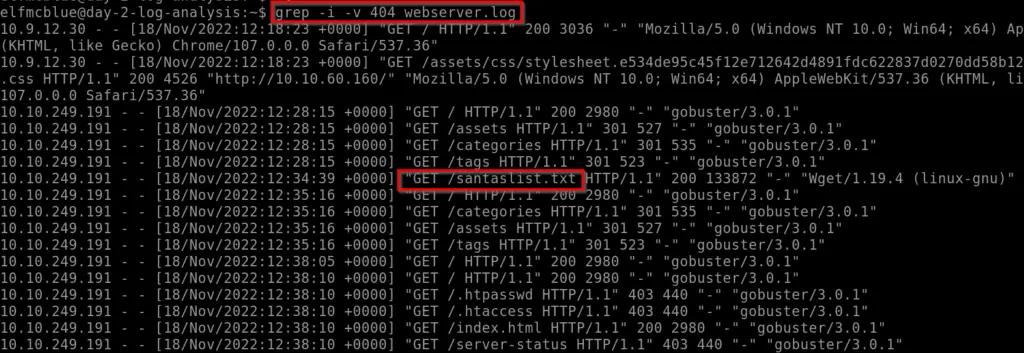
Answer (Highlight Below):
santaslist.txt
Question 8
Look through the log files for the flag. The format of the flag is: THM{}
To do this, we can grep for the term ‘THM{‘
grep "THM{" SSHD.logI used this to search both log files.
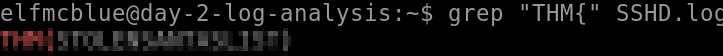
Answer (Highlight Below):
THM{STOLENSANTASLIST}
Conclusion for Advent of Cyber 2022 Day 2
We are definitely heating up in this challenge. While many newbs (myself included) love offensive content, it is incredibly useful to see things from the blue team’s side as well. Logs are critical not only for the blue team, but also for pentesters and red teamers to be aware of.
It’s important to realize that when we attempt to hack a system, there may be a huge amount of log data generated. The more noisy an attack is, the more logs it will create and the easier it will be to detect.