Day 10 – Offensive is the Best Defense
Today’s task is an introduction to nmap. nmap is an incredibly popular port scanning tool used in networking. It is an industry standard and is used in penetration testing, bounty hunting, red and blue team operations. TryHackMe has several rooms dedicated to help you master nmap.
Nmap is a command line tool, and the syntax is relatively simple. The most basic example would be:
nmap <IP>
Which would perform a standard TCP scan of the top 1000 ports of a target machine.
There are many options that are baked into nmap, such as scanning all ports or specific ports, other scan types, vulnerability scans, and service detection scans. We’ll cover some of these options as we answer the questions for Day 10.
Question 1
Help McSkidy and run nmap -sT <IP>. How many ports are open between 1 and 100?
Launch both the AttackBox and the Day 10 target machine.
Open a terminal window and type in ‘nmap -sT 10.10.10.10’, substituting in your target machine’s IP address. Count the number of open ports from the response:
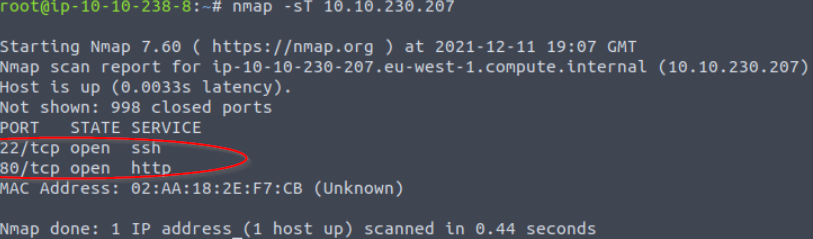
Answer:
(Highlight below to see answer):
2
Question 2
What is the smallest port number that is open?
This is the lower number of the two open ports we just found, which is running the SSH (Secure Shell) service.
Answer:
(Highlight below to see answer):
22
Question 3
What is the service related to the highest port number you found in the first question?
This is the service running on port 80.
Answer:
(Highlight below to see answer):
http
Question 4
Now run nmap -sS 10.10.230.207. Did you get the same results? (Y/N)
Run nmap again, this time using the ‘-sS’ flag. Unlike the TCP Connect scan (using the -sT flag), this will initiate a TCP SYN scan, which sends a SYN packet and waits for a SYN/ACK response. If this response is received, nmap will register the port as open but will not attempt a full 3-way handshake. In other words, it will not send the final ‘ACK’ packet that results in a TCP session. This makes the SYN scan a stealthier option than using the Connect Scan.
Run the TCP SYN scan as described. You should obtain the following response:
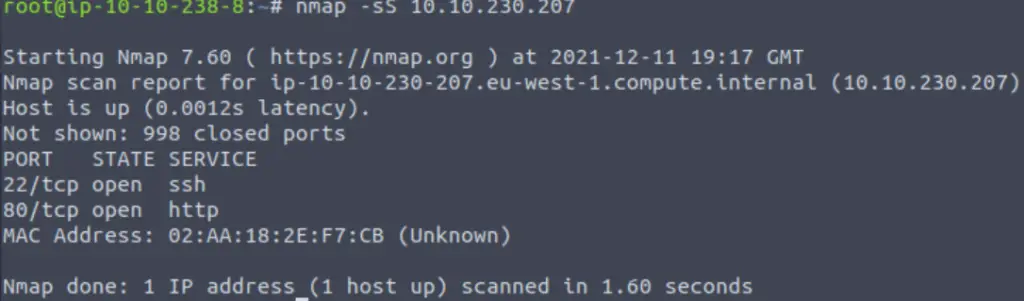
Answer:
(Highlight below to see answer):
Y
Question 5
If you want Nmap to detect the version info of the services installed, you can use nmap -sV 10.10.230.207. What is the version number of the web server?
This scan will take a bit longer than the previous scans. Look for the service running on port 80:
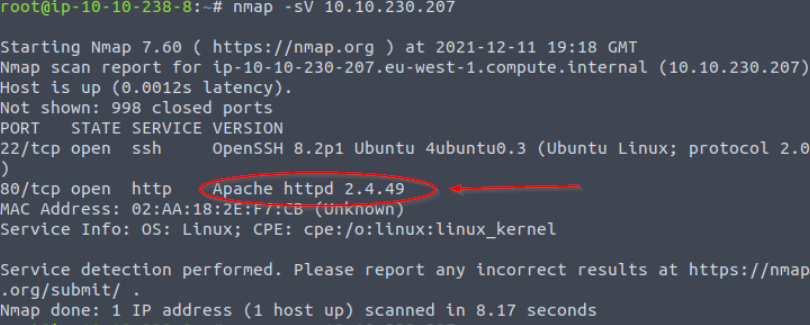
Answer:
(Highlight below to see answer):
Apache httpd 2.4.49
Question 6
By checking the vulnerabilities related to the installed web server, you learn that there is a critical vulnerability that allows path traversal and remote code execution. Now you can tell McSkidy that Grinch Enterprises used this vulnerability. What is the CVE number of the vulnerability that was solved in version 2.4.51?
I performed a Google search for ‘CVE Apache httpd 2.4.49’. The first result was a this page on cve.mitre.org, which gave me the following information:
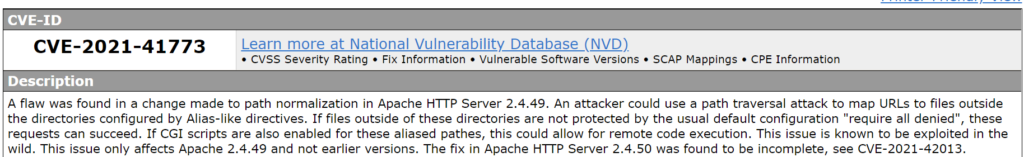
Note at the end of the description: “The fix in Apache HTTP Server 2.4.60 was found to be incomplete, see CVE-2021-42013”.
Answer:
(Highlight below to see answer):
CVE-2021-42013
Question 7
You are putting the pieces together and have a good idea of how your web server was exploited. McSkidy is suspicious that the attacker might have installed a backdoor. She asks you to check if there is some service listening on an uncommon port, i.e. outside the 1000 common ports that Nmap scans by default. She explains that adding -p1-65535 or -p- will scan all 65,535 TCP ports instead of only scanning the 1000 most common ports. What is the port number that appeared in the results now?
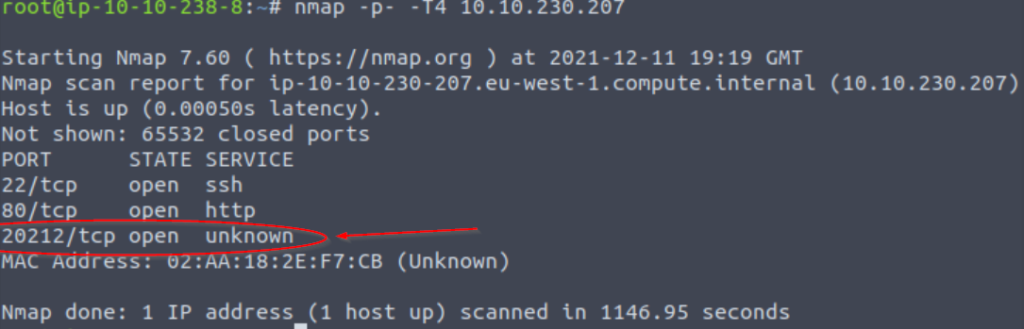
Perform a scan using the -p- flag, which scans all 65535 ports rather than just the top 1000 ports. This scan takes a while; personally I will often initiate this scan first during a CTF and then background the scan, perform a normal ‘top 1000 port’ scan and later verify that I didn’t miss any ports. If I’m not crunched for time, I will sometimes also run the ‘-p-‘ scan first thing and then grab a coffee or do something else while the scan is running so that I ensure I am capturing all open ports before proceeding.
I also recommend using the ‘-T4’ timing scan while using this option. This will dramatically reduce the amount of time that the scan takes, and I haven’t found it to be any less thorough as a result of the faster timing (I have found that a -T5 scan – the fastest possible- will occasionally miss ports so I stick to the -T4 option).
When the scan is complete, you should find a third port that wasn’t in our initial results:
Answer:
(Highlight below to see answer):
20212
Question 8
What is the name of the program listening on the newly discovered port?
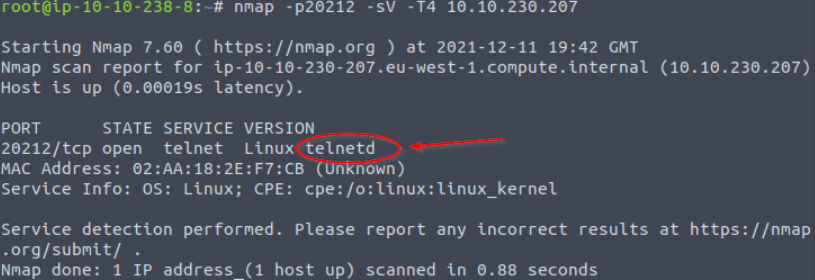
Note that with -p- scan we were able to find that TCP port 20212 is open, but the scan wasn’t able to tell us the service or version.
Let’s scan this port specifically using the ‘-p20212’ and ‘-sV’ flags. The first option tells nmap to only scan port 20212, and the second flag tells nmap to run the ‘version’ scan and attempt to find the service and version details:
Answer:
(Highlight below to see answer):
telnetd