TryHackMe – Learning Cyber Security – Complete Walkthrough
Introduction
Learning Cyber Security is the first room in TryHackMe‘s Pre Security Learning Path.
It can be found at: https://tryhackme.com/room/beginnerpathintro
Summary
This room introduces some basic concepts that are important in the field of infosec. The information is basic but important. This room presents an easy first introduction to the security field.
Walkthrough
Task 1 – Web Application Security
Why understanding how the web works is important
To attack web applications, you need to understand how they work. Hacking websites isn’t some magical process but does come down to knowing how a part of a website functions and being able to identify weaknesses to take advantage of. Once you have a good understanding of the fundamentals, you’ll learn about the techniques and tools used in hacking sites.
If something is vulnerable, it means there is the possibility of it being attacked or harmed. If an application or system has a vulnerability, there is something that can be attacked or taken advantage of (a weakness).
Question 1
Read the above and learn how to hack BookFace, TryHackMe’s vulnerable social media site.
Walkthrough:
Click the green ‘View Site’ button at the top right side of Task 1.
This will open up a page with instructions at the top and a simulated web browser beneath it.
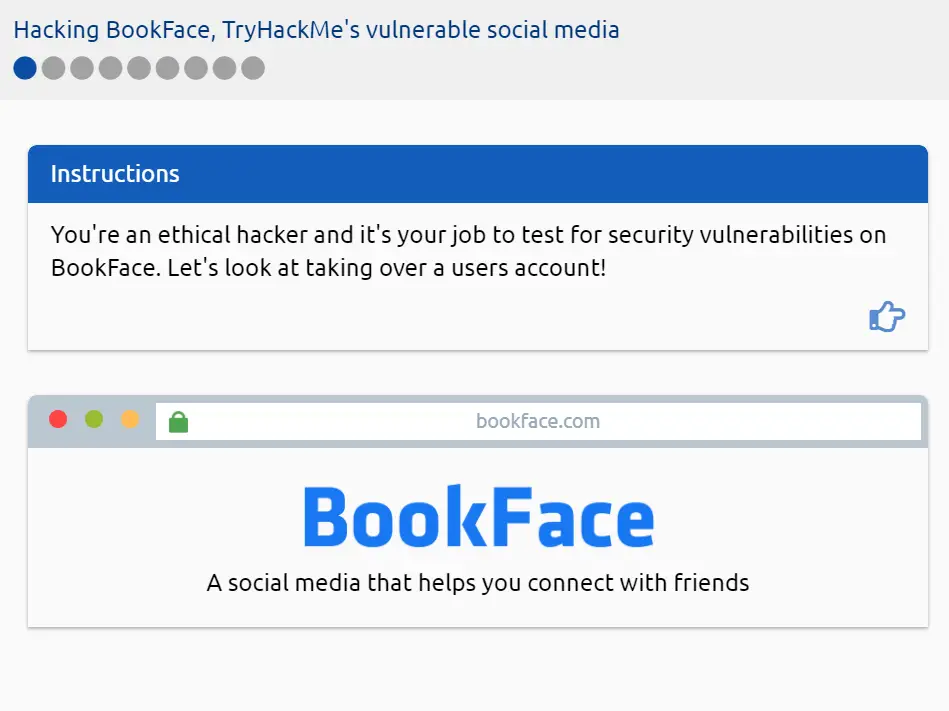
Navigate through each set of instructions and web pages.
Answer:
No answer needed
Question 2
What is the username of the BookFace account you will be taking over?
Walkthrough:
The answer can be found on the second page of the website simulation we accessed during Question 1. Look at the end of URL for Ben Spring’s BookFace page, bookface.com/Ben.Spring
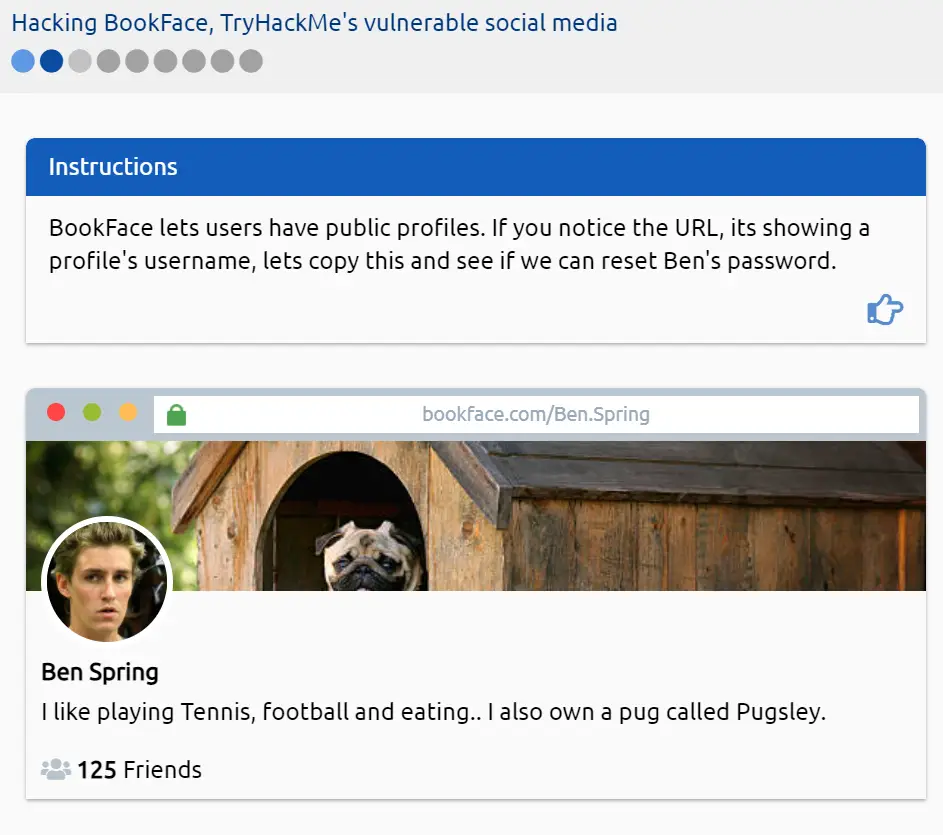
The point here is that social media sites often use the URL as an identifier for the username. This gives us a critical piece of information (the username itself) that can be used to exploit a weakness. Finding a username or list of users is a common step in hacking.
Answer:
(Highlight below to find the answer):
Ben.Spring
Question 3
Hack the BookFace account to reveal this task’s answer!
Walkthrough:
Enter the username we just found into the password reset page (the third page of the simulation) and click the ‘Reset Password’ button:
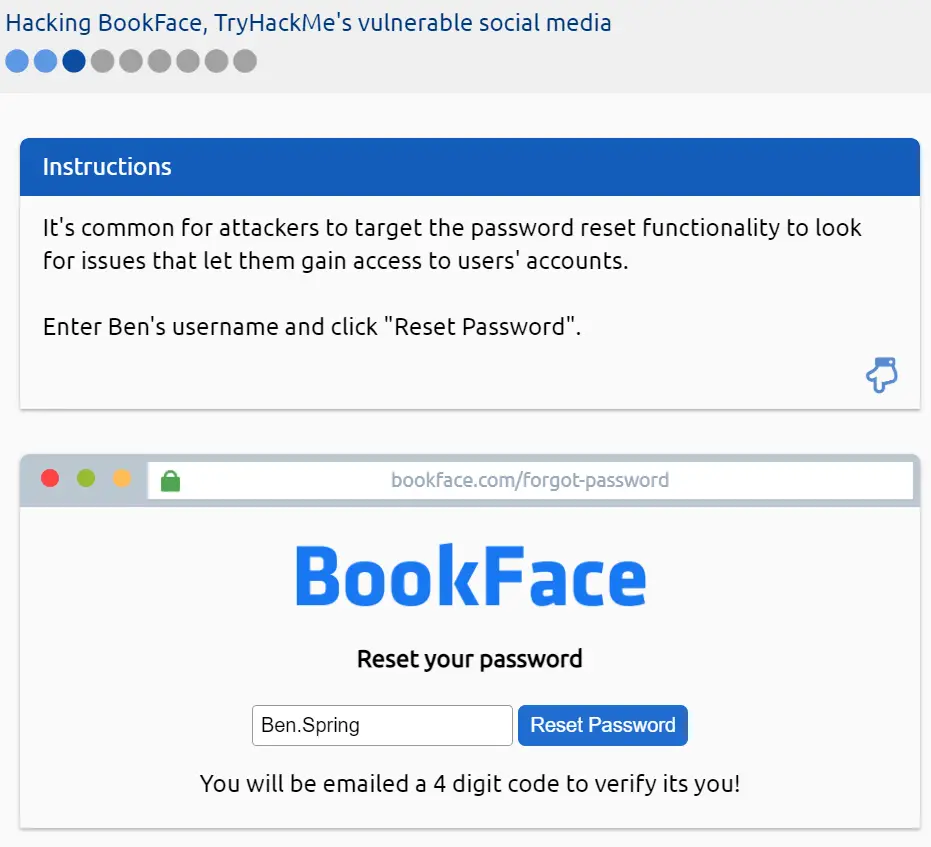
You will then be directed to guess the code, and your guess will probably be incorrect:
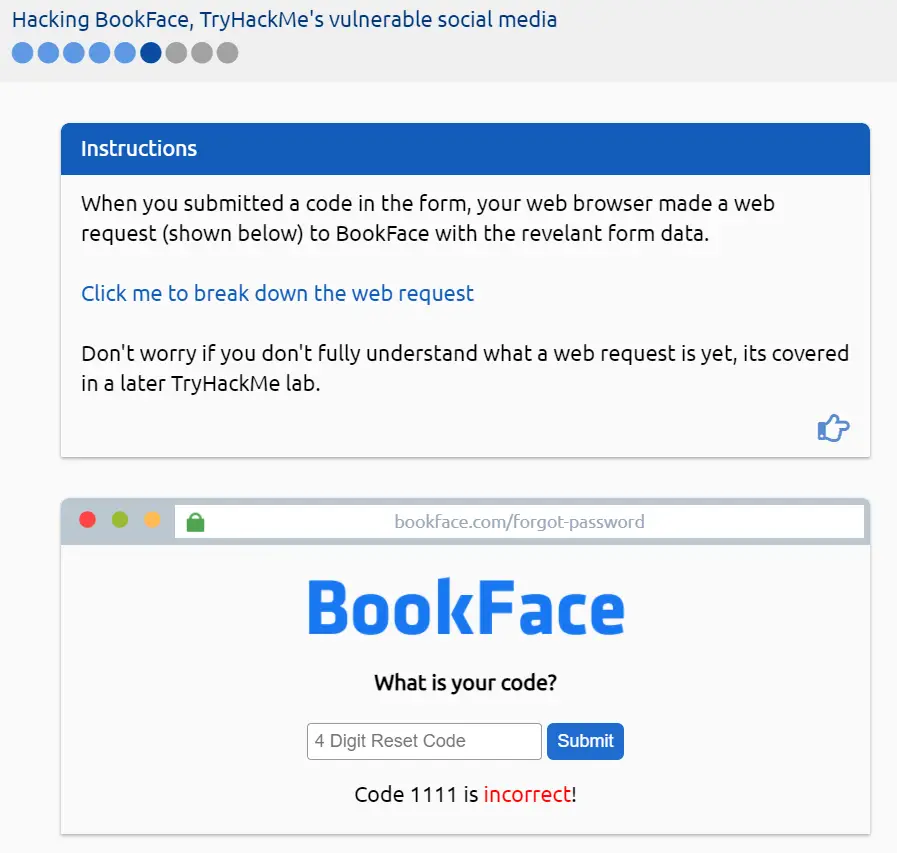
THM also lets us know that when we clicked the ‘Submit’ button, our browser submitted a Web Request to BookFace:
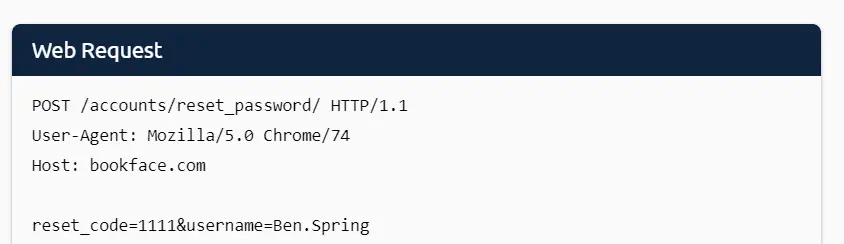
This type of Web Request is POST, which is covered in a later lesson.
A four digit code can be any number from 0000 to 9999, so there are a total of 10,000 possibilities. This is too much, so THM instructs us to use a tool called BruteForce to try every possibility.
BruteForce is a method of password cracking that involves trying every possible combination.
Enter the minimum and maximum possible numbers into the Web Request Repeater tool at the bottom of the page and click the ‘BruteForce’ button:
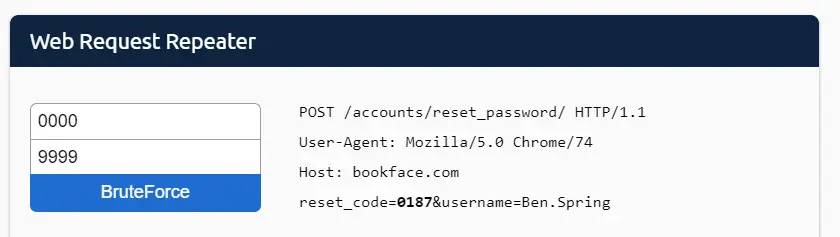
This tool will cycle through POST web requests using each possible number until the correct code is found:
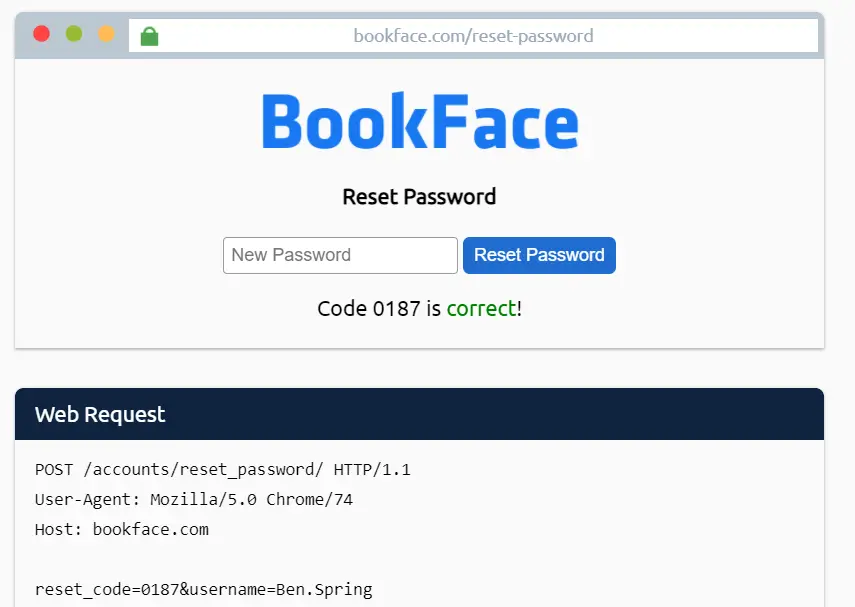
Now we can reset the password, allowing us full access to the account. Click the ‘Reset Password’ button.
We are informed that this was a real-life Instagram vulnerability, and that a hacker was rewarded with a check for $10k. Pretty awesome!
The answer is given on the last page of the simulation.
Answer:
(Highlight below to find the answer):
THM{BRUTEFORCING}
Task 2 – Network Security
Why networking is important
Networking is really important to understand in cyber security. From scanning and identifying who and what is on a network, to reviewing network logs to monitor and track what users have been up to will require you to have an understanding of how networks work.
TryHackMe’s Complete Beginner learning path will walk you through the networking concepts and give you enough knowledge to get started in your cyber security journey.
Question 1
Read the above, and see how Target was hacked on the right hand side.
Walkthrough:
This task follows the same recipe as Task 1.
Click the green ‘View Site’ button at the top right side of Task 2.

Note: If you don’t click the button inside Task 2, you will continue to see the site for Task 1.
We are walked through a series of pages that describe a Target hack. Target’s air conditioner units were vulnerable and directly connected to Target’s main store network. This allowed access to the main network via the air conditioners.
Go through the pages; no answer is needed for Question 1.
Answer:
No answer needed
Question 2
How much did the data breach cost Target?
Walkthrough:
The answer can be found on the third page.
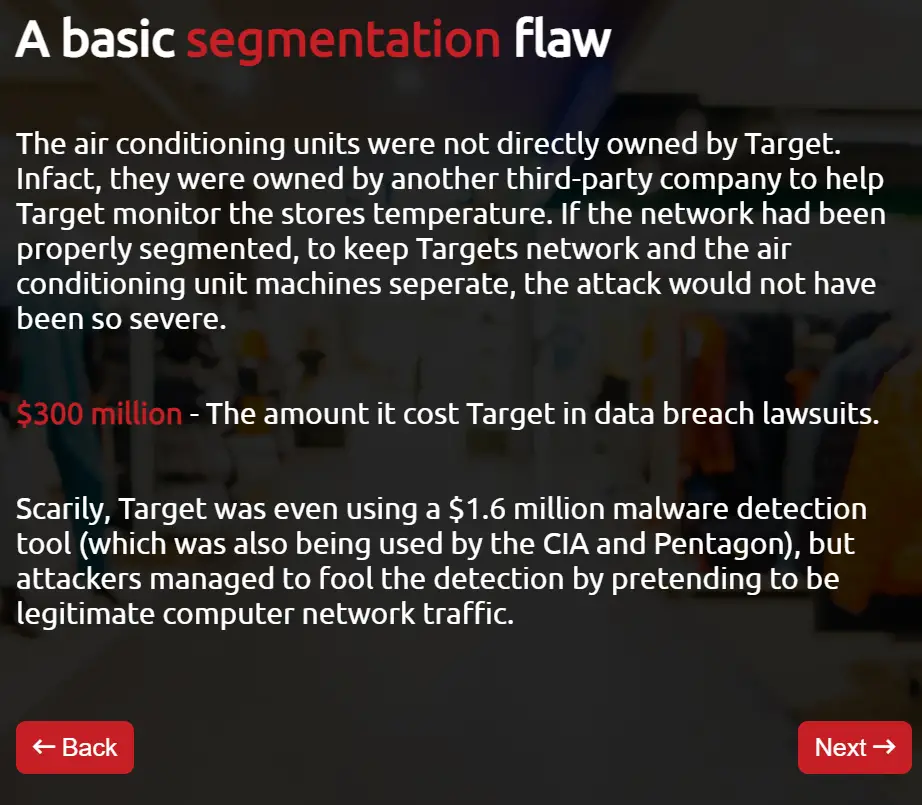
Answer:
(Highlight below to find the answer):
$300 million
Task 3 – Learning Roadmap
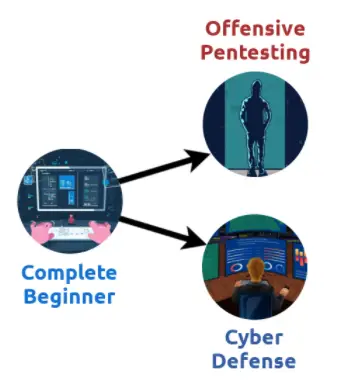
Above is a learning path roadmap. The Complete Beginner path will teach you the computing basics and introduce you to some security techniques. Once you have the security basics, enroll in either the Offensive Pentesting or the Cyber Defense path.
The skills you acquire from the learning paths will prepare you for a career as an ethical hacker, penetration tester or cyber security analyst.
Walkthrough:
The image refers to the Complete Beginner Learning Path, but this lesson is currently part of the Pre Security path.
I recommend completing the Pre Security path first, then going through the Complete Beginner path. The only problem is that the Pre Security path is informational and uses simulations rather than actual machines; in other words, you don’t actually learn any hacking. However it does introduce many important concepts.
If you’re itching to start hacking, you can alternately go through both the Pre Security and Complete Beginner paths at the same time. You may find the Complete Beginner path to be difficult, but you can always reference topics from Pre Security at any time. In a way, these paths reflect the informational and practical sides of hacking; both are necessary. It’s just that one can be more fun than the other!
Question 1
Read the above
Answer:
No answer needed
Conclusion
Congratulations! We have just completed our first step in our journey of learning how to hack.
We learned about the importance of understanding the web and networks. We were even introduced to an important type of attack, brute-force.
At this point, you may be thinking about an amazing career in infosec or becoming a professional penetration tester.
But hacking can be hard work and stressful!
Try to temper your expectations and train yourself to have fun. Hacking is one of the few legitimate career paths where you can be rewarded for thinking deviantly, which can be a lot of fun for the right person. But it’s also difficult and complex, and we’ve only taken one step on a journey of many, many steps.
On the other hand, taking the first step is the most important. Allow yourself to be proud of your accomplishment. Acknowledging and rewarding even the smallest step is key to staying motivated.
Nice job!