TryHackMe – What is Networking? – Complete Walkthrough
This room provides an excellent introduction into fundamental networking concepts. It is part of TryHackMe’s Pre Security Learning Path.
The ‘What is Networking?’ room can be found at: https://tryhackme.com/room/whatisnetworking
Summary
Summary of what is covered
Walkthrough
Task 1 – What is Networking?
Networks are simply things connected. For example, your friendship circle: you are all connected because of similar interests, hobbies, skills and sorts.
Networks can be found in all walks of life:
- A city’s public transportation system
- Infrastructure such as the national power grid for electricity
- Meeting and greeting your neighbours
- Postal systems for sending letters and parcels
But more specifically, in computing, networking is the same idea, just dispersed to technological devices. Take your phone as an example; the reason that you have it is to access things. We’ll cover how these devices communicate with each other and the rules that follow.
In computing, a network can be formed by anywhere from 2 devices to billions. These devices include everything from your laptop and phone to security cameras, traffic lights and even farming!
Networks are integrated into our everyday life. Be it gathering data for the weather, delivering electricity to homes or even determining who has the right of way at a road. Because networks are so embedded in the modern-day, networking is an essential concept to grasp in cybersecurity.
Take the diagram below as an example, Alice, Bob and Jim have formed their network! We’ll come onto this a bit later on.
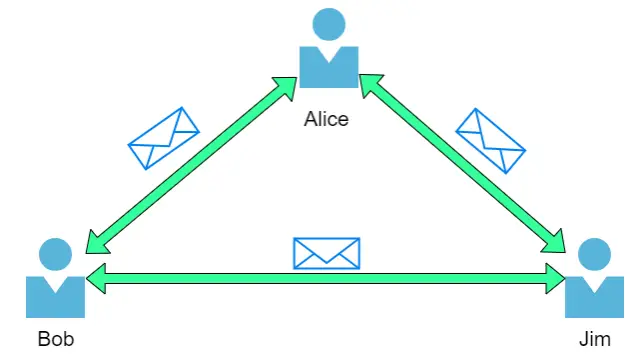
Networks come in all shapes and sizes, which is something that we will also come on to discuss throughout this module.
Question 1
What is the key term for devices that are connected together?
Walkthrough:
This question is basically a freebie – if you don’t know it by now, just re-read the description of networks provided above by THM.
Answer:
(Highlight below to find the answer):
Network
Task 2 – What is the Internet?
Now that we’ve learnt what a network is and how one is defined in computing (just devices connected), let’s explore the Internet.
The Internet is one giant network that consists of many, many small networks within itself. Using our example from the previous task, let’s now imagine that Alice made some new friends named Zayn and Toby that she wants to introduce to Bob and Jim. The problem is that Alice is the only person who speaks the same language as Zayn and Toby. So Alice will have to be the messenger!
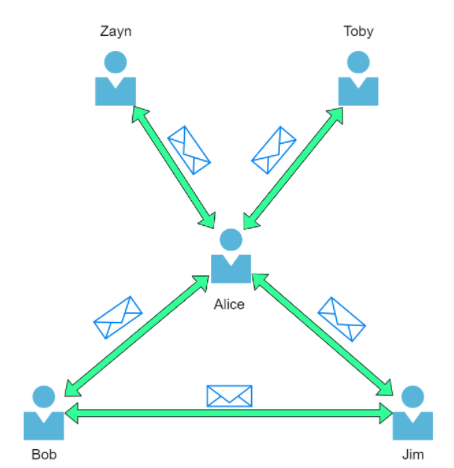
Because Alice can speak both languages, they can communicate to one another through Alice — forming a new network.
The first iteration of the Internet was within the ARPANET project in the late 1960s. This project was funded by the United States Defence Department and was the first documented network in action. However, it wasn’t until 1989 when the Internet as we know it was invented by Tim Berners-Lee by the creation of the World Wide Web (WWW). It wasn’t until this point that the Internet wasn’t used as a repository for storing and sharing information (like it is today).
Let’s relate Alice’s network of friends to computing devices. The Internet looks like a much larger version of this sort of diagram:
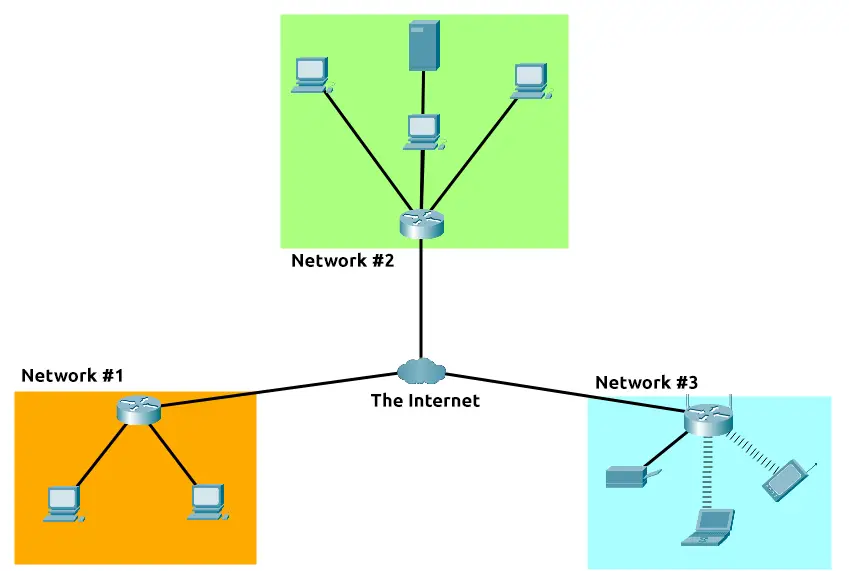
As previously stated, the Internet is made up of many small networks all joined together. These small networks are called private networks, where networks connecting these small networks are called public networks — or the Internet! So, to recap, a network can be one of two types:
- A private network
- A public network
Devices will use a set of labels to identify themselves on a network, which we will come onto in the task below.
Question 1
Who invented the World Wide Web?
Walkthrough:
The answer can be found in the above description of the internet, or you can easily Google it.
Answer:
(Highlight below to find the answer):
Tim Berners-Lee
Task 3 – Identifying Devices on a Network
To communicate and maintain order, devices must be both identifying and identifiable on a network. What use is it if you don’t know whom you’re talking to at the end of the day?
Devices on a network are very similar to humans in the fact that we have two ways of being identified:
- Our Name
- Our Fingerprints
Now we can change our name through deed poll, but we can’t, however, change our fingerprints. Every human has an individual set of fingerprints which means that even if they change their name, there is still an identity behind it. Devices have the same thing: two means of identification, with one being permeable. These are:
- An IP Address
- A Media Access Control (MAC) Address — think of this as being similar to a serial number.
IP Addresses
Briefly, an IP address (or Internet Protocol) address can be used as a way of identifying a host on a network for a period of time, where that IP address can then be associated with another device without the IP address changing. First, let’s split up precisely what an IP address is in the diagram below:
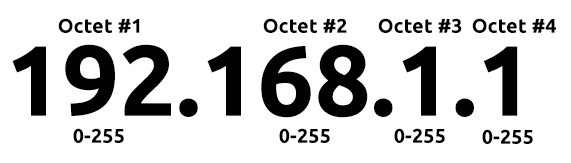
An IP address is a set of numbers that are divided into four octets. The value of each octet will summarise to be the IP address of the device on the network. This number is calculated through a technique known as IP addressing & subnetting, but that is for another day. What’s important to understand here is that IP addresses can change from device to device but cannot be active simultaneously more than once within the same network.
IP Addresses follow a set of standards known as protocols. These protocols are the backbone of networking and force many devices to communicate in the same language, which is something that we’ll come onto another time. However, we should recall that devices can be on both a private and public network. Depending on where they are will determine what type of IP address they have: a public or private IP address.
A public address is used to identify the device on the Internet, whereas a private address is used to identify a device amongst other devices. Take the table & screenshot below as an example. Here we have two devices on a private network:
| Device Name | IP Address | IP Address Type |
| DESKTOP-KJE57FD | 192.168.1.77 | Private |
| DESKTOP-KJE57FD | 86.157.52.21 | Public |
| CMNatic-PC | 192.168.1.74 | Private |
| CMNatic-PC | 86.157.52.21 | Public |
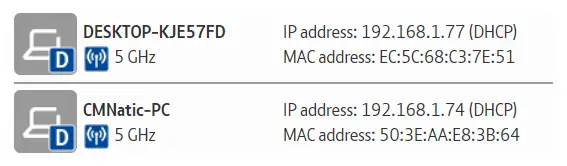
These two devices will be able to use their private IP addresses to communicate with each other. However, any data sent to the Internet from either of these devices will be identified by the same public IP address. Public IP addresses are given by your Internet Service Provider (or ISP) at a monthly fee (your bill!)
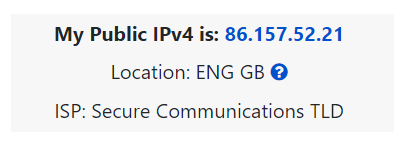
As more and more devices become connected, it is becoming increasingly harder to get a public address that isn’t already in use. For example, Cisco, an industry giant in the world of networking, estimated that there would be approximately 50 billion devices connected on the Internet by the end of 2021. (Cisco., 2021). Enter IP address versions. So far, we have only discussed one version of the Internet Protocol addressing scheme known as IPv4, which uses a numbering system of 2^32 IP addresses (4.29 billion) — so you can see why there is such a shortage!
IPv6 is a new iteration of the Internet Protocol addressing scheme to help tackle this issue. Although it is seemingly more daunting, it boasts a few benefits:
- Supports up to 2^128 of IP addresses (340 trillion-plus), resolving the issues faced with IPv4
- More efficient due to new methodologies
The screenshot below compares both an IPv6 and IPv4 address.
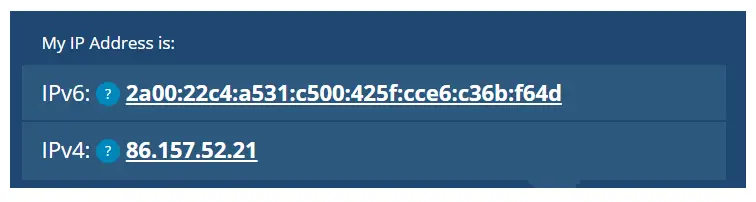
MAC Addresses
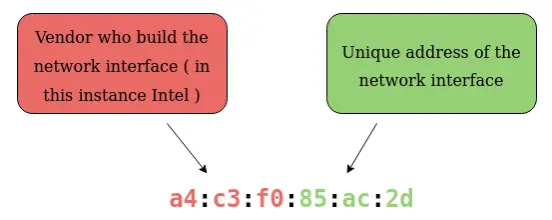
Devices on a network will all have a physical network interface, which is a microchip board found on the device’s motherboard. This network interface is assigned a unique address at the factory it was built at, called a MAC (Media Access Control ) address. The MAC address is a twelve-character hexadecimal number (a base sixteen numbering system used in computing to represent numbers) split into two’s and separated by a colon. These colons are considered separators. For example, a4:c3:f0:85:ac:2d. The first six characters represent the company that made the network interface, and the last six is a unique number.
However, an interesting thing with MAC addresses is that they can be faked or “spoofed” in a process known as spoofing. This spoofing occurs when a networked device pretends to identify as another using its MAC address. When this occurs, it can often break poorly implemented security designs that assume that devices talking on a network are trustworthy. Take the following scenario: A firewall is configured to allow any communication going to and from the MAC address of the administrator. If a device were to pretend or “spoof” this MAC address, the firewall would now think that it is receiving communication from the administrator when it isn’t.
Places such as cafes, coffee shops, and hotels alike often use MAC address control when using their “Guest “or “Public” Wi-Fi. This configuration could offer better services, i.e. a faster connection for a price if you are willing to pay the fee per device. The interactive lab attached to this task has been made to replicate this scenario!
Practical
The interactive labs simulate a hotel Wi-Fi network where you have to pay for the service. You’ll note that the router is not allowing Bob’s packets ( blue) to the TryHackMe website and is placing them in the bin, but Alice’s packets (green) are going through fine because she has paid for Wi-Fi. Try changing Bob’s MAC address to the same as Alice’s to see what happens.
Deploy the interactive lab and proceed to answer the following questions below.
Question 1
What does the term “IP” stand for?
Walkthrough:
This answer can be obtained from the write-up above or a quick Google search. IP is one of the most common acronyms in the world of IT. IP is often closely associated with TCP (i.e. TCP/IP) but they are different protocols that work on different layers of the OSI and TCP/IP networking models (the two most common models of computer networks).
Answer:
(Highlight below to find the answer):
Internet Protocol
Question 2
What is each section of an IP address called?
Walkthrough:
IP addresses are divided into four sections, each with eight bits. For review, a ‘bit’ is a single binary digit.
Since each bit can represent one of two values (0 or one), the total number of values of eight bits is 28 = 256. In base-10 (decimal) we would represent these values as 0 through 255. In eight bit binary, these are represented by 00000000 (0 in base-10) and 11111111 (255 in base-10).
An IP address consists of four of these sets of eight bits.
The question here is, what is the special name for a sequence of eight bits?
Hint: An octopus has eight arms, and an octagon has eight sides…
Answer:
(Highlight below to find the answer):
Octet
Question 3
How many sections (in digits) does an IP address have?
Walkthrough:
Take a look at the IP address from the above example:

Another (more specific) way of framing this question would be “How many octets are there in an IP (IPv4) address”?
Answer:
(Highlight below to find the answer):
4
Question 4
What does the term “MAC” stand for?
Walkthrough:
This answer is also given directly in the write-up or can easily be googled.
One thing to keep in mind is that even though MAC addresses are introduced here immediately following IP addresses, they actually use a totally different protocol (Ethernet vs. IP) and operate on a different network layer (data link vs. network).
MAC addresses are also used for identifying a specific machine within a network, while IP addresses are used to connect computers on different networks.
Answer:
(Highlight below to find the answer):
Media Access Control
Question 5
Deploy the interactive lab using the “View Site” button and spoof your MAC address to access the site. What is the flag?
Walkthrough:
Review the information under the ‘Practical’ section above.
Click the green ‘View Site’ button all the way at the top of the task:
A window will open and you will see a network simulation that looks like this:
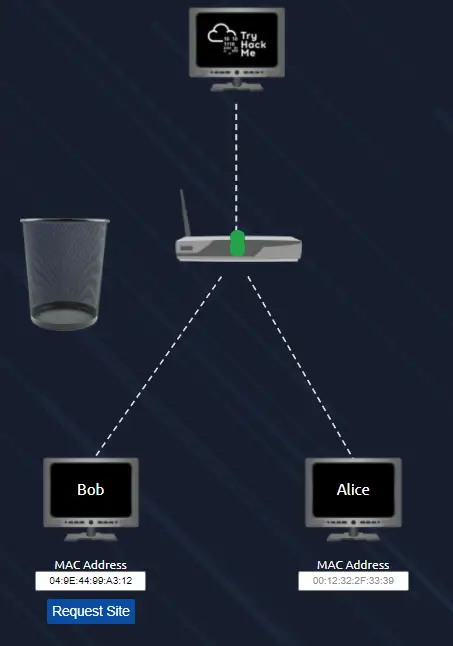
This simulation represents two users, Bob and Alice, who are attempting to access the TryHackMe website from a hotel network. Alice has paid for internet access but Bob is trying to save his hard earned money.
When we open the simulation, we see that there are green dots travelling from Alice to TryHackMe, representing Alice’s packets.
The device in the middle is a router, which controls the flow of information from Alice and Bob.
If Bob tries to send a packet to TryHackMe (by clicking the blue ‘Request Site’ button), the packet is rejected and is sent to the trash bin.
This is because the router is preventing Bob from accessing the internet. The router has been configured by the hotel to only allow packets through from users that have paid for internet access.
But Bob has a secret weapon! He knows that the router uses MAC addresses to identify computers. If he pretends to be Alice, the router will allow him to access to the website. All he needs to do is figure out Alice’s MAC address and spoof his own MAC address so that the router thinks that he is Alice.
Since we are given Alice’s MAC address, this task is made easy for us. All we need to do is copy Alice’s MAC address and use it to replace Bob’s current MAC address in the box. Note that in the image below, we have replaced Bob’s MAC address with Alice’s:
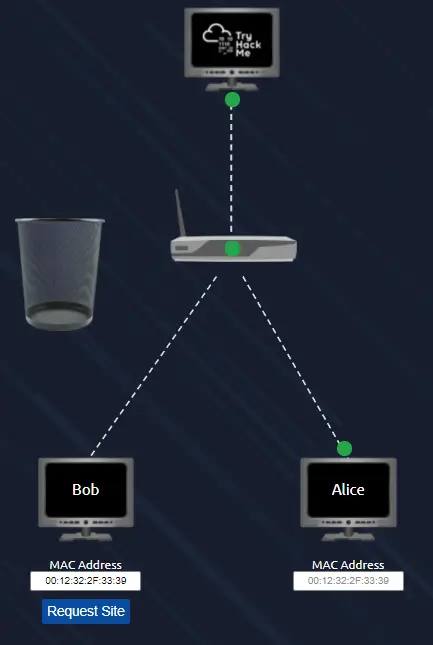
This time if we click the blue ‘Request Site’ button, Bob’s packet will be successfully forwarded by the router to TryHackMe, and we will be given the flag.
Answer:
(Highlight below to find the answer):
THM{YOU_GOT_ON_TRYHACKME}
Task 4 – Ping (ICMP)
Ping is one of the most fundamental network tools available to us. Ping uses ICMP (Internet Control Message Protocol) packets to determine the performance of a connection between devices, for example, if the connection exists or is reliable.
The time taken for ICMP packets travelling between devices is measured by ping, such as in the screenshot below. This measuring is done using ICMP’s echo packet and then ICMP’s echo reply from the target device.
Pings can be performed against devices on a network, such as your home network or resources like websites. This tool can be easily used and comes installed on Operating Systems (OSs) such as Linux and Windows. The syntax to do a simple ping is ping IP address or website URL. Let’s see this in action in the screenshot below.
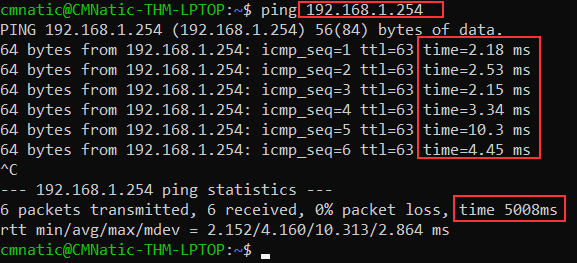
Here we are pinging a device that has the private address of 192.168.1.254. Ping informs us that we have sent six ICMP packets, all of which were received with an average time of 5.3 seconds.
Now you are going to do the same thing to ping the address of “8.8.8.8” on the deployable website in this task. Pinging the correct address will reveal a flag to answer the following question below.
Question 1
What protocol does ping use?
Walkthrough:
The answer is given in the first paragraph of the write up. This question is looking for the answer in the form of an acronym.
Answer:
(Highlight below to find the answer):
ICMP
Question 2
What is the syntax to ping 10.10.10.10?
Walkthrough:
Recall that the correct syntax using an IP address is as follows:
ping <IP address>
Answer:
(Highlight below to find the answer):
ping 10.10.10.10
Question 3
What flag do you get when you ping 8.8.8.8?
Walkthrough:
To complete this question, you have to launch the simulation by clicking the green ‘View Site’ button at the top right side of the task.

A window will open, showing a simulated command line interface.
Unlike a real command line, we’ll need to interact by using the text field and blue ‘Send Ping Request’ button at the top of the page.
As we enter data into the text field, we’ll notice that our command on the simulated command line will change.
Enter the supplied IP address (8.8.8.8) into the text field and click the blue ‘Send Ping Request’ button.
Note that the entire command is now:
ping -c 4 8.8.8.8
There is an additional option here that hasn’t been covered.
The flag ‘-c’ has been entered. This allows us to specify the total number of times that we want to ping the IP address. The number ‘4’ following the flag tells the computer that we want it to ping the designated IP address a total of 4 times. If this option is not selected, the computer will ping the IP address indefinitely, repeating the ping over and over until cancelled by the user.
If you forget to include this option in the command, you can always use ‘ctrl-c’ to interrupt the endless ping cycle.
After pinging the IP address a total of 4 times, the terminal will output a summary with the answer flag at the end.
Answer:
(Highlight below to find the answer):
THM{I_PINGED_THE_SERVER}
Task 5 – Continue Your Learning – Intro to LAN
Continue your learning by joining the “Intro to LAN” room.
Question 1
Join the “Intro to LAN” room.
Walkthrough:
This task is a freebie. Join the “Intro to LAN” room and click the green ‘Question Done’ button.
Answer:
(Highlight below to find the answer):
No answer needed
Conclusion
This room covers some of the most fundamental topics when it comes to computer networks.
We are given a general definition of networks and the internet is defined as a large network that contains many other networks.
The significance of the internet is that it allows different networks to communicate with each other.
A solid introduction to both IP addresses and MAC addresses follows, and we are introduced to the ping command.
While each of these topics deserve study on their own, this lesson does a good job in exposing the newbie to them.
I found the introduction to ping to be a bit random but I think that the point here is to get the new hacker a little more familiar with IP addresses by providing practical experience. In reality, ping can be a very useful tool for network troubleshooting as it can tell us whether or not we can communicate with a specific machine. We can use ping in a step by step manner to determine where we might be having an issue on a network or between networks.