TryHackMe Web Application Security – Walkthrough and Notes
Web Application Security is an introductory room on TryHackMe. It contains a short introduction to the topic of web app security, and an exercise in identifying an IDOR in a practice web application.
About This Walkthrough/Disclaimer:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by requiring a manual action (highlighting) to obtain all solutions. This way you can follow along without being handed the solution if you don’t want it. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
This room can be found at: https://tryhackme.com/room/introwebapplicationsecurity
Walkthrough for TryHackMe Web Application Security
Task 3 – Practical Application of Web Application Security
This section introduces the concept of an IDOR. IDOR stands for ‘Insecure Direct Object Reference’, which sounds complex. But finding IDORs can be easy, and (despite their complex name), they are recommended learning for new hackers and bug-bounty hunters.
In the lab example, take some time to look through the different pages available on the web application. There’s a main page, and pages for shipments, inventory, and ‘Your Activity’.
One of the most important things web pentesters and bug bounty hunters look for, are any potential inputs to the web application. This includes search bars, upload forms, and even links that cause some action on the website back end.
The URI of a web page can often be manipulated; basically, any time we visit a URI what we are really doing is sending an http request (most often GET but POST is also common) to the web server. The response depends on how the server has been programmed.
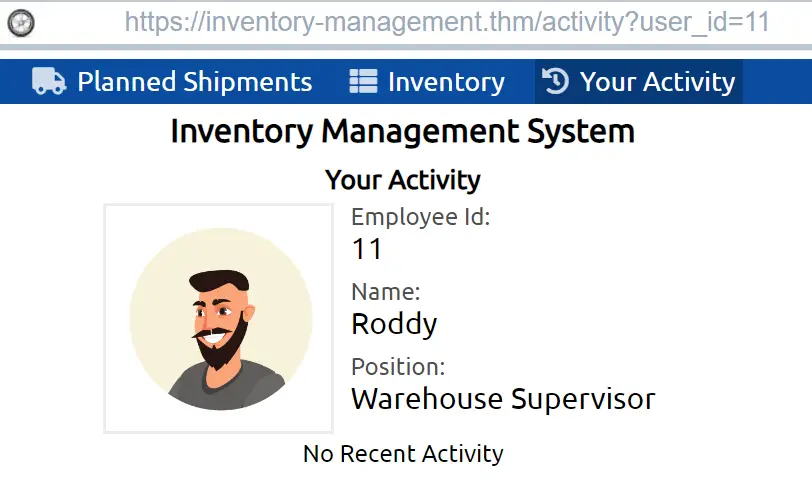
While looking at the web application, you may have noticed that when we go to the ‘Your Activity’ page, we are visiting a the following URL:
https://inventory-management.thm/activity?user_id=11
This tells us that we are passing the user_id of ’11’ to the web server, which then serves the page that we see:
What if we change the user_id number? We can try entering other numbers. Let’s see what happens if we enter a user_id of 1:
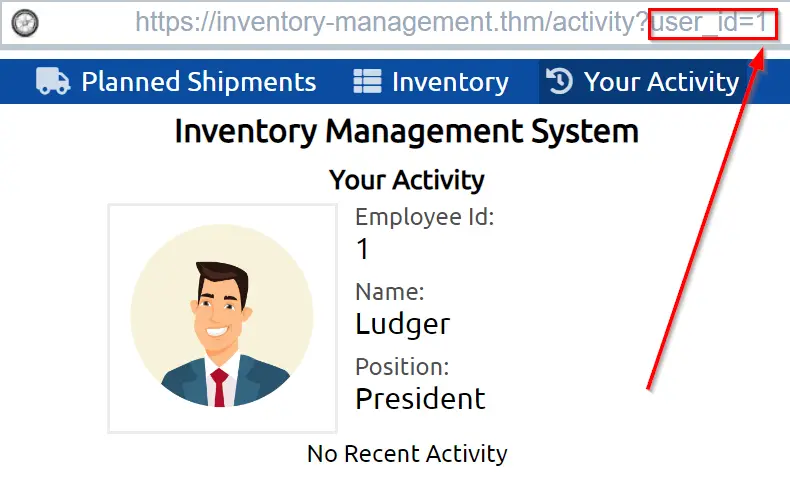
In this case, we are able to pull up the User Activity page for the President of the company. Obviously this is already a major finding. We can similarly view the User Activity pages for other users as well.
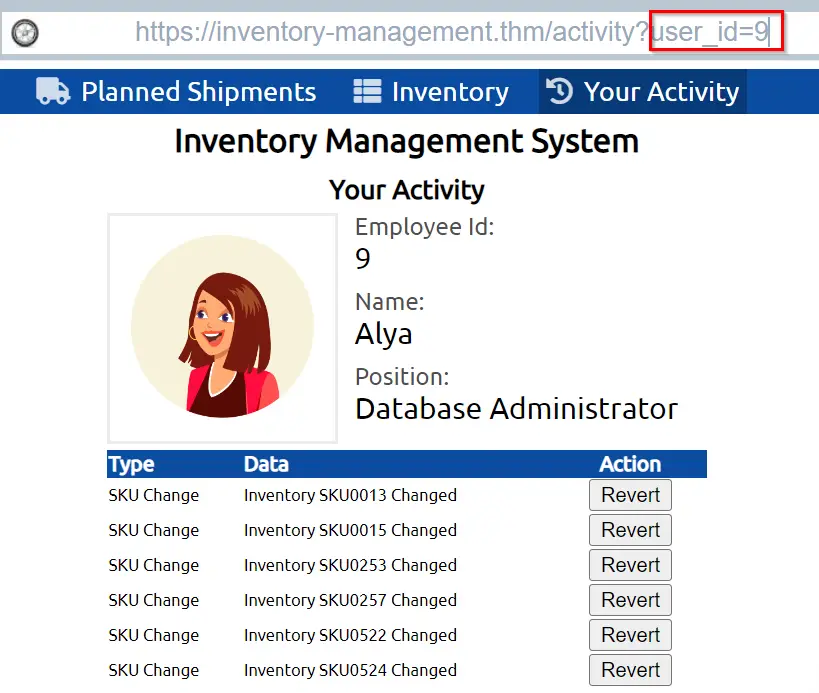
If we go to user_id=9, we can see the activity of Alya, a Database Administrator. It looks like she’s been busy making changes to the inventory system!
Luckily, we can easily revert her changes using a convenient button.
After reverting each of the changes, you should see the following screen that includes the flag needed to finish the room!

Question 1
Check the other users to discover which user account was used to make the malicious changes and revert them. After reverting the changes, what is the flag that you have received?
Answer (Highlight Below):
THM{IDOR_EXPLORED}
Conclusion
This is the type of room that is useful for absolute beginners. It’s the kind of room that I might show to someone who has no experience, to try to get them interested in hacking. It’s easy enough for someone who has zero experience, and it does cover some topics that are very important in the field of web application security.
I enjoyed this room. Thanks to tryhackme, and strategos for putting it together!