TryHackMe – Introductory Networking – Walkthrough
This is my walkthrough and notes for the Introductory Networking room on TryHackMe.
This room tries to do two things. First, it introduces us to the two quintessential models of networking: the OSI model, and the TCP/IP model. These models are ubiquitous in IT and networking and help us understand and model the internet. Second, we get an introduction to and practice with some useful commands designed to help learn networking fundamentals.
About This Walkthrough:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
This room can be found at: https://tryhackme.com/room/introtonetworking
Walkthrough
Task 2 – The OSI Model: An Overview
The Open Systems Interconnect model is a representation of the internet that uses 7 layers in order to describe everything from the physical wires carrying the electric signals (Level 1), to the application interface we use to interact with the computer (Layer 7).
There are much better resources available to learn about the OSI Model, so I’m not going to attempt to cover it all here. I will try to cover the information needed to answer each question.
Question 1
Which layer would choose to send data over TCP or UDP?
Both TCP (Transmission Control Protocol) and UDP (User Datagram Protocol), function on the transport layer. In the OSI Model, TCP sits on top of IP, which works on the network layer.
So let’s count the layers from the bottom up – (1) Physical, (2) Data Link, (3) Network, (4) Transport. If we remember that IP functions on the Network layer, it should help us remember that TCP sits on the layer just above.
Answer:
(Highlight below to see answer):
4
Question 2
Which layer checks received packets to make sure that they haven’t been corrupted?
The concept of encapsulation is fundamental to the OSI Model, and will be covered in greater detail. Basically, each layer of the OSI Model becomes a payload that is contained by the layer below it. For example, the Application Layer (Layer 7) data is encapsulated by the Presentation Layer (Layer 6). The outermost layer is Data Link (Layer 2), which contains the data for all of the layers above it. When the data gets to its destination, it is basically unwrapped layer by layer, with each layer corresponding to a different protocol that dictates how to process the data.
It’s important to check for corruption, so this happens at the outermost layer of data encapsulation, Data Link (Layer 2). The Data Link layer relies on the Ethernet protocol, which uses Ethernet frames as the standard data package type. The Ethernet frame encapsulates the data needed for higher layers; an Ethernet frame contains an IP packet, which contains a TCP segment.
Answer:
2
Question 3
In which layer would data be formatted in preparation for transmission?
When data is being prepared for transmission, it goes down the layers of the OSI Model; the data is encapsulated in the payload of a TCP segment, which is then encapsulated by an IP packet, which itself is encapsulated in an Ethernet frame.
The Ethernet frame is the last step in preparing the data for transmission.
Answer:
2
Question 4
Which layer transmits and receives data?
Once the data has been formatted in preparation for transmission, it is then passed down to the Physical layer, which does the actual transmitting and receiving.
Answer:
1
Question 5
Which layer encrypts, compresses, or otherwise transforms the initial data to give it a standardised format?
When data comes from the application layer, it may need to be formatted in order to be understood by the application layer on the receiving computer before it can be transmitted. This is the job of the Presentation layer, which sits just below the Application layer and performs encryption and decryption as well as compression and decompression.
Long before the data is transmitted anywhere, it first needs to be formatted so that it can be passed down the OSI Networking stack. There has to be something that gets the data from the application layer and prepares it for the transport layer. This is the job of the Presentation layer.
Answer:
6
Question 6
Which layer tracks communications between the host and receiving computers?
Known as the session layer, this layer is responsible for maintaining communications.
Answer:
5
Question 7
Which layer accepts communication requests from applications?
This has to happen at the application layer.
Answer:
7
Question 8
Which layer handles logical addressing?
The term ‘logical addressing’ refers to IP addresses, so this layer must be operating on the same layer as the Internet Protocol (IP).
Answer:
3
Question 9
When sending data over TCP, what would you call the “bite-sized” pieces of data?
For the most part, each protocol uses a different adjective to describe chunks of data: packets, frames, datagrams, and segments are all ways of distinguishing similar things. Which of these corresponds with TCP?
Answer:
Segments
Question 10
[Research] Which layer would the FTP protocol communicate with?
I googled ‘FTP OSI Layer’, and found the answer at the top of the search engine results page.
HINT: FTP works on the Application layer. It actually uses TCP.
Answer:
(Highlight below to see answer):
7
Question 11
Which transport layer protocol would be best suited to transmit a live video?
There are two transport layer protocols, TCP and UDP.
TCP – Slow and reliable. Used when you don’t need a massive amount of data (or can stand slower transmission) but don’t want any errors in the data. Example: visiting a web page (like this one!)
UDP – Fast but unreliable. Used when you need speed and don’t mind some dropped packets. Example: streaming a video.
Answer:
UDP
Task 3 – Encapsulation
In each layer of the OSI Model (and the TCP/IP model, as we’ll see), data in encapsulated by the layer below it.
In other words, an Ethernet frame contains an IP packet (also called a datagram), which contains a TCP segment. The layers encapsulate each other like a Russian nesting doll.
The following image shows how data is encapsulated in preparation for transmission:
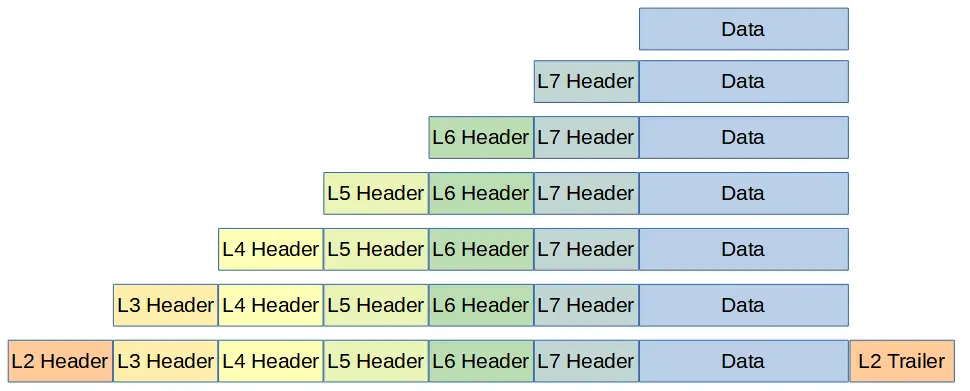
The Layer 2 data, called an Ethernet Frame, therefore contains inside of itself the data for all of the Layers above it.
When the data is received, it is unpacked one layer at a time in a process that reverses the encapsulation, i.e. de-encapsulation.
Question 1
How would you refer to data at layer 2 of the encapsulation process (with the OSI model)?
Layer 2, also called the Data Link Layer, uses the Ethernet protocol. Ethernet sends and receives data in Ethernet Frames.
Answer:
Frames
Question 2
How would you refer to data at layer 4 of the encapsulation process (with the OSI model), if the UDP protocol has been selected?
Layer 4 is the Transport layer, which has two protocols associated with it – TCP and UDP. Data that is formatted for TCP is called a segment, while data formatted for UDP is called a datagram.
Answer:
Datagrams
Question 3
What process would a computer perform on a received message?
The process of wrapping each layer into the layer below it is called encapsulation, while the opposite process is called de-encapsulation.
Answer:
De-encapsulation
Question 4
Which is the only layer of the OSI model to add a trailer during encapsulation?
Check the image above. A trailer is added at Layer 2 (Ethernet protocol).
Answer:
Data link
Question 5
Does encapsulation provide an extra layer of security (Aye/Nay)?
Answer:
Aye
Task 4 – The TCP/IP Model
The OSI Model is great for learning networking, but it isn’t actually how the internet works.
There is a simpler model called the TCP/IP model that is actually more accurate than the OSI Model. The main reason that the OSI Model is still used is because it enhances learning the conceptual basis of networking. The best part about this is that because the TCP/IP model is simpler than the OSI model, it’s very easy to learn once you understand the OSI Model.
The TCP/IP Model is a four Layer networking model. The two lowest layers of the OSI Model (1 -Physical and 2 – Data Link) are combined into the Network Interface layer. The three highest layers of the OSI Model (5 – Session, 6 – Presentation, and 7 – Application) are combined into the Application layer.
Hybrid models that combine the OSI and TCP/IP Models are also very common.
Question 1
Which model was introduced first, OSI or TCP/IP?
The TCP/IP model predates OSI by a few years.
TCP/IP
Question 2
Which layer of the TCP/IP model covers the functionality of the Transport layer of the OSI model (Full Name)?
There is no difference between the OSI and TCP/IP models regarding the functionality of the Transport layer.
Transport
Question 3
Which layer of the TCP/IP model covers the functionality of the Session layer of the OSI model (Full Name)?
The Session, Presentation, and Application layers of the OSI model are accounted for by the Application layer of the TCP/IP model.
Answer:
(Highlight below to see answer):
Application
Question 4
The Network Interface layer of the TCP/IP model covers the functionality of two layers in the OSI model. These layers are Data Link, and?.. (Full Name)?
The Physical and Data Link layers of the OSI model are accounted for by the Network Interface layer of the TCP/IP model.
Many of the popular hybrid models combining OSI and TCP/IP keep these layers separate.
Answer:
(Highlight below to see answer):
Physical
Question 5
Which layer of the TCP/IP model handles the functionality of the OSI network layer?
There is really just a name shift here. The Internet layer of the TCP/IP model covers the functionality of the Network layer in the OSI model.
Answer:
(Highlight below to see answer):
Internet
Question 6
What kind of protocol is TCP?
TCP is a connection-based (also called connection-oriented) protocol. This means that it establishes a session that requires consistent communication.
In general, connection-based protocols are designed to ensure high data quality, but this comes at a cost; they are also slower than a connectionless protocol.
Answer:
(Highlight below to see answer):
Connection-based
Question 7
What is SYN short for?
TCP packets use flags to indicate a connection state or to provide information. Flags are just single bits that are set in the TCP header. The most common flags are SYN, ACK, FIN, and RST:
SYN – Short for synchronize. This is the first step in establishing a TCP session via a three-way handshake.
ACK – Short for acknowledgement. This flag is commonly set to indicate that data or a request has been correctly received. The second step of the three way handshake is when the server sends the client a packet with both the SYN and ACK flags set (bits equal to ‘1’). This is called SYN/ACK.
FIN – Short for finish, this flag is set to request termination of the session.
RST – The reset flag is used to indicate that something has gone wrong and termination is requested as a result. This is often because the service is down or is not accepting requests.
Answer:
(Highlight below to see answer):
Synchronise
Question 8
What is the second step of the three way handshake?
The three way handshake involves three steps:
(1) A SYN packet is sent by the client to request a session.
(2) The server replies with a SYN/ACK packet, indicating that it has received the request and is ready to establish a session.
(3) The client replies to the server with an ACK packet, indicating that has received the SYN/ACK packet from the server. The session has now been established.
Answer:
(Highlight below to see answer):
SYN/ACK
Question 9
What is the short name for the “Acknowledgement” segment in the three-way handshake?
This is also the third packet sent during a three-way handshake.
Answer:
(Highlight below to see answer):
ACK
Task 5 – Networking Tools – Ping
Ping is so well known that it’s become colloquial in the US. It’s common to hear things like “I’ll ping you about that later” and similar usages. But what is ping?
In essence, ping is a utility that is designed to test reachability. It’s a way of asking if a given host is reachable and available, and also measures the round trip time of messages sent between the originating host and destination computer.
The syntax of ping is simple:
ping <target>
If you just run ping this way will send packets continuously until you kill the command using CTRL-C.
A popular option is to use the ‘-c’ (count) flag, which allows you to specify the number of packets you want to send. If we want ping a host three times for example, we can use the command:
ping -c 3 <target>
Question 1
What command would you use to ping the bbc.co.uk website?
We saw that the basic syntax for ping is as follows:
ping <target>
The target can be an IP address or a domain. You can also use ping to determine the IP address of a website. In this case, we’ll be using the URL provided (bbc.co.uk)
Answer (Highlight Below):
ping bbc.co.uk
Question 2
Ping muirlandoracle.co.uk
What is the IPv4 address?
You can use the TryHackMe AttackBox to perform the ping using the terminal, or you can use your own machine.
Using the AttackBox:
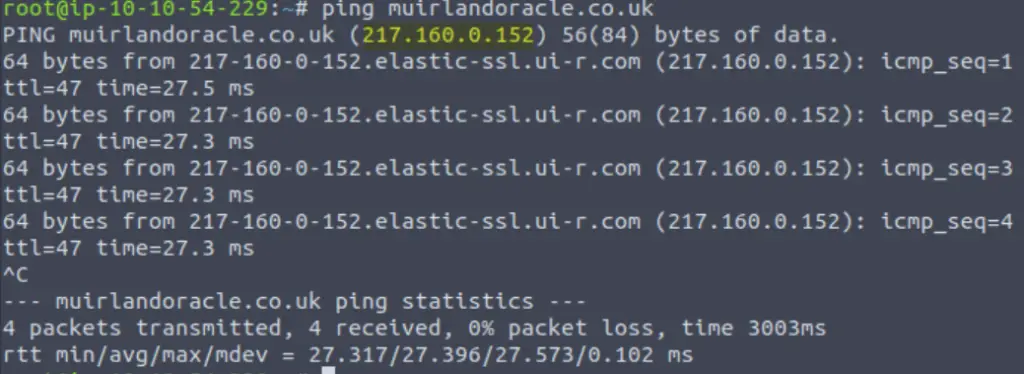
Answer (Highlight Below):
217.160.0.152
Question 3
What switch lets you change the interval of sent ping requests?
You can always use the man page or –help option to get more information about a command and the options available for it.
Whenever possible, I try to narrow down the search by piping the output into grep. In this case we are asked what switch allows us to change the interval of requests, so I decided to use the search term ‘interval’ in my grep command:
man ping | grep interval
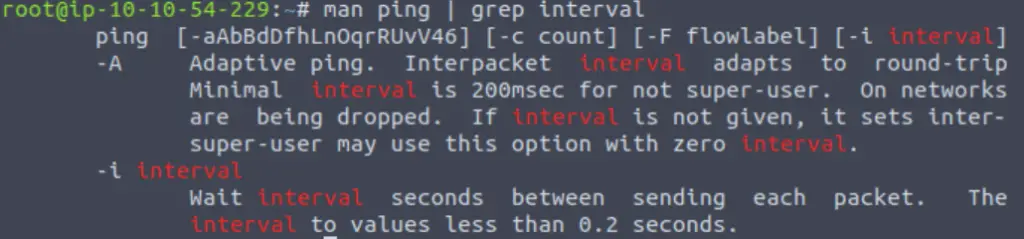
This produced two results, and it is fairly obvious which is the one we are looking for.
Answer (Highlight Below):
-i
Question 4
What switch would allow you to restrict requests to IPv4?
I used the same technique as for the last question, this time piping the ping man page into grep, this time searching for the string “IPv4”:
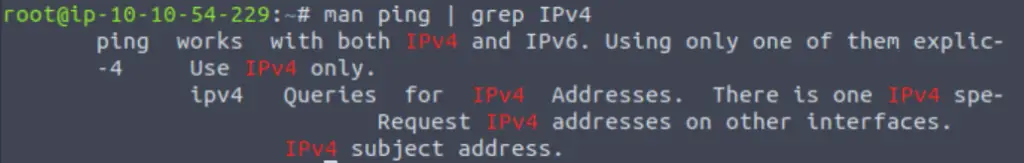
Note that grep is case-sensitive.
Answer (Highlight Below):
-4
Question 5
What switch would give you a more verbose output?
I used the same trick again, this time using grep to search for the string ‘Verbose’:
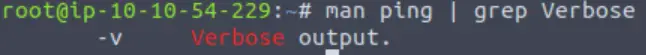
Answer (Highlight Below):
-v
Task 6 – Networking Tools – Traceroute
Traceroute is a great utility that is useful for seeing where a packet travels en route to its’ destination. It can give us an idea of what geographical locations and networks the packet travels through.
Traceroute is super useful for determining any points of failure, as well as any response delays or routing loops which could be impeding data transfer.
Question 1
Use traceroute on tryhackme.com
Can you see the path your request has taken?
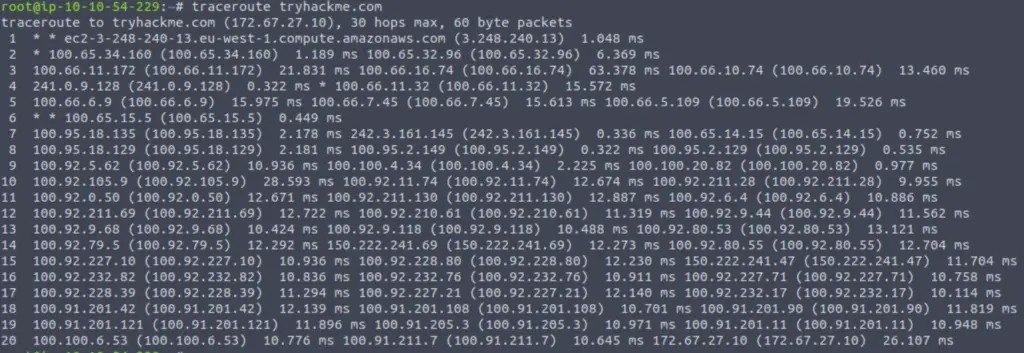
Answer:
(Highlight below to see answer):
No answer needed
Question 2
What switch would you use to specify an interface when using Traceroute?
At this point you may have realized that switches are often designated by letters that often correspond to the primary descriptor.
In this case, I used grep to search for ‘interface’:
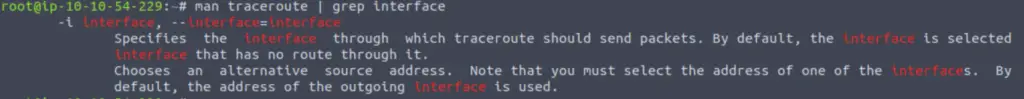
Answer:
(Highlight below to see answer):
-i
Question 3
What switch would you use if you wanted to use TCP SYN requests when tracing the route?
This time using grep to search for ‘tcp’:
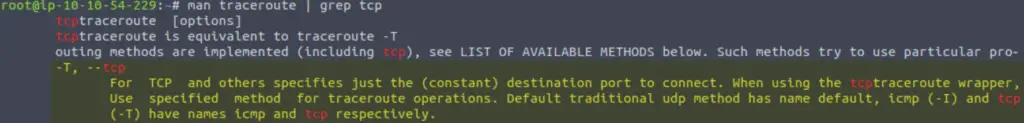
(Highlight below to see answer):
-T
Question 4
[Lateral Thinking] Which layer of the TCP/IP model will traceroute run on by default (Windows)?
I did a Google search for ‘traceroute tcp/ip layer’, where the first result returned an answer of ‘network layer’ or layer 3.

But ‘network’ layer is actually layer 3 from the OSI model. We have to convert this to the name of layer 3 in the TCP/IP model to get our answer.
Answer:
(Highlight below to see answer):
Internet
Task 7 – Networking Tools – WHOIS
WHOIS provides public information about domain registration. As such, it is often one of the first steps completed in performing recon against a target.
WHOIS queries can be performed using one of the many available webapps (including ICANN) or on the command line.
Question 1
Perform a whois search on facebook.com
No answer needed
Question 2
What is the registrant postal code for facebook.com?
The whois search produces a bunch of information. You have to scroll down a bit to find the ‘Registrant Postal Code’:
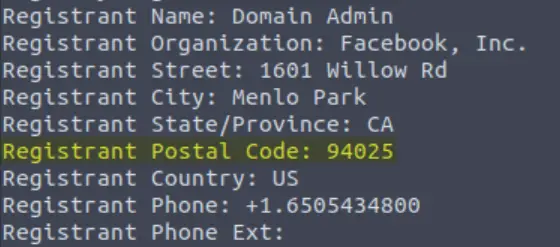
You can also grep for ‘Postal’ to find the answer:
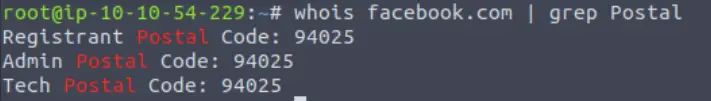
Answer:
(Highlight below to see answer):
94025
Question 3
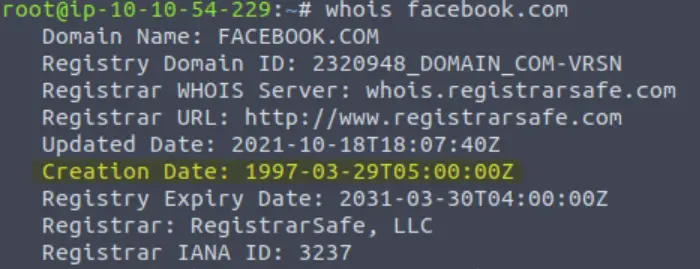
When was the facebook.com domain first registered?
Once again, you can either look through the whois result manually or use a tool like grep.
If you search manually, you will find the answer under ‘Creation Date’ near the top:
You can also use the grep command. Now that we’ve gotten comfortable piping a command into grep, let’s add the ‘-i’ flag which tells grep to ignore case. This means that if we search for a term like ‘date’, grep will return all results for both ‘date’ and ‘Date’. We can now search for ‘date’ as such:
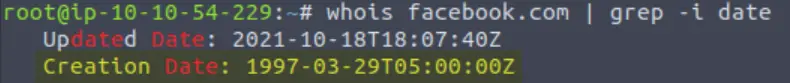
Answer:
(Highlight below to see answer):
29/03/1997
Question 4
Perform a whois search on microsoft.com
This is easy enough:
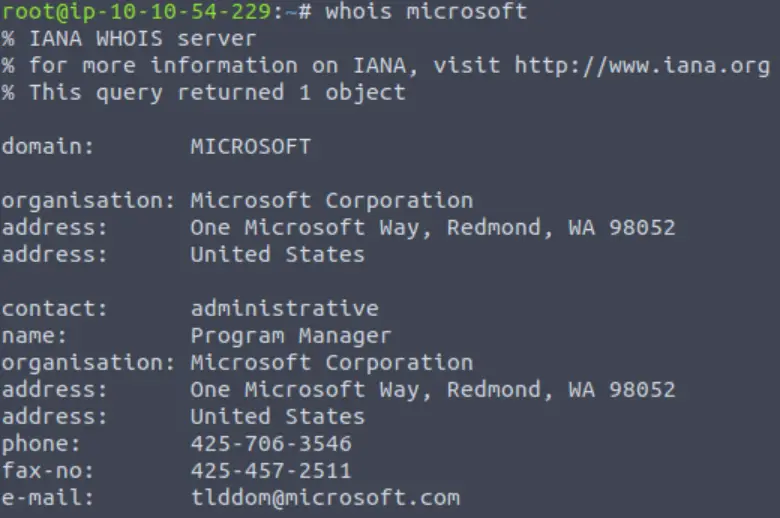
Answer:
(Highlight below to see answer):
No answer needed
Question 5
Which city is the registrant based in?
The address is pretty close to the top of the results:
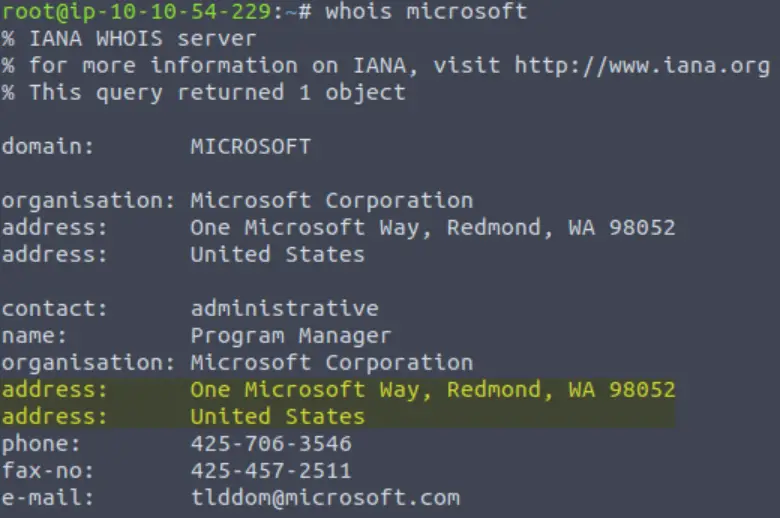
Answer:
(Highlight below to see answer):
Redmond
Question 6
[OSINT] What is the name of the golf course that is near the registrant address for microsoft.com?
Now that we have the address, we can use it to find the nearby golf course:
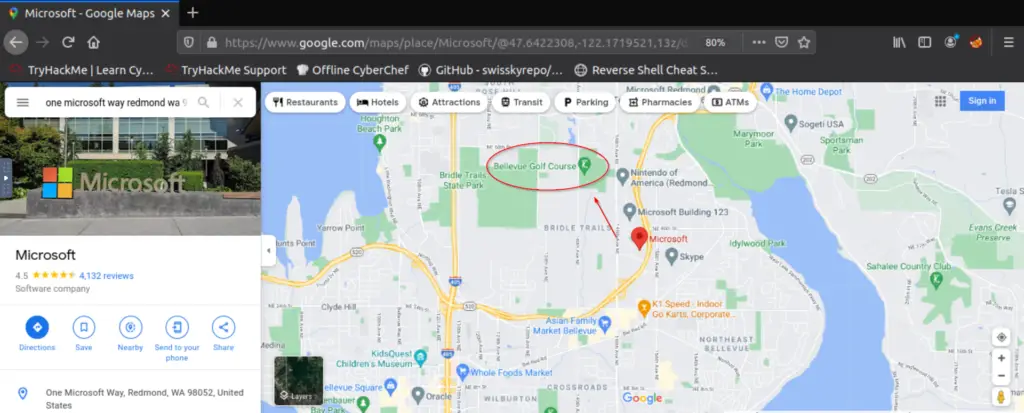
Answer:
(Highlight below to see answer):
Bellevue Golf Course
Question 7
What is the registered Tech Email for microsoft.com?
Again, we can either do this manually or we can use grep to search for us:

Answer:
(Highlight below to see answer):
Task 8 – Networking Tools – Dig
Question 1
What is DNS short for?
Here’s an easy way to remember it: DNS is the system that links domain names to IP addresses.
Answer:
(Highlight below to see answer):
Domain Name System
Question 2
What is the first type of DNS server your computer would query when you search for a domain?
It it doesn’t have an entry for a domain name in its’ local cache, your computer will then query a recursive DNS server. Then if the recursive DNS server doesn’t find an entry, the request will be passed to a root name server, which sends it to the appropriate top-level domain (TLD) server which should have the answer.
Answer:
(Highlight below to see answer):
Recursive
Question 3
What type of DNS server contains records specific to domain extensions (i.e. .com, .co.uk*, etc)*? Use the long version of the name.
If the recursive DNS server doesn’t have the record, it will then forward the request to a root name server. But the root name server itself doesn’t contain records for specific domains – instead, they just pass the request to the right TLD server.
Answer:
(Highlight below to see answer):
Top-Level Domain
Question 4
Where is the very first place your computer would look to find the IP address of a domain?
Your computer will first check its’ own local cache to see if has the requested IP address.
Answer:
(Highlight below to see answer):
Local Cache
Question 5
[Research] Google runs two public DNS servers. One of them can be queried with the IP 8.8.8.8, what is the IP address of the other one?
Just Google it!
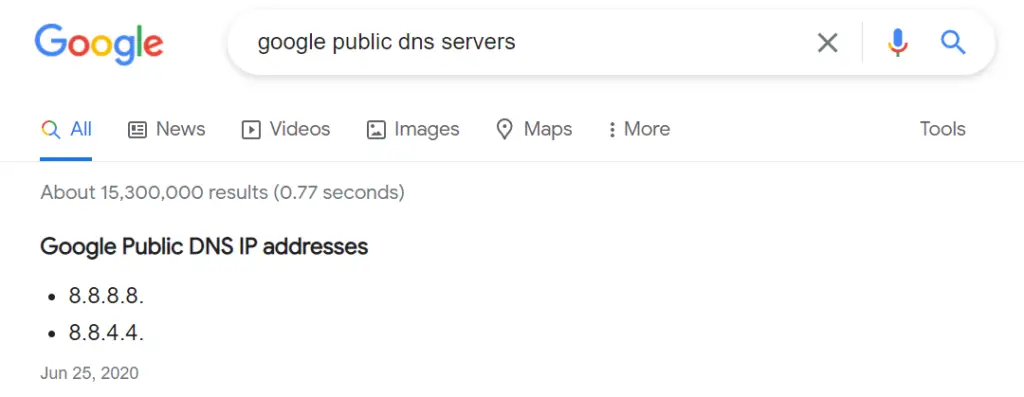
Answer:
(Highlight below to see answer):
8.8.4.4
Question 6
If a DNS query has a TTL of 24 hours, what number would the dig query show?
This is the number of seconds in 24 hours.
Answer:
(Highlight below to see answer):
86400
Conclusion
Overall, I thought that this room provided a decent intro to networking and some important commands. It does a great job of subtly giving exposure to a wide variety of topics in networking. A huge thanks to MuirlandOracle for putting this room together!