TryHackMe – Introductory Researching – Walkthrough and Notes
This page contains a walkthrough and notes for the Introductory Researching room at TryHackMe.
Brief introduction to the room
About This Walkthrough:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by making finding the solutions a manual action, similar to how you might watch a video of a walkthrough; they can be found in the walkthrough but require an intentional action to obtain. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
<— Insert table of contents here —>
Walkthrough
Task 1 – Introduction
While it’s true that hacking requires IT knowledge and skills, the ability to research, learn, tinker, and try repeatedly is just as (or arguably more) important.
It’s impossible to know everything about every computer system, so hackers must learn how to do their own research. Much of the time, success in research depends on how a term is searched, so learning how to search is also an essential skill.
Question 1
Read the Introduction
Answer:
No answer needed
Task 2 – Example Research Question
In this task, the writeup guides us through an example of using research to figure out how to extract a message from a JPEG image file.
With a few simple google searches, we learn that data can be hidden in image files and is called steganography. We learn about a tool called steghide that can extract data from a JPEG, and we learn how to install and use steghide.
This type of rapid learning and shifting to achieve a specific goal is common in CTF competitions as well as in penetration testing.
The following questions provide some practice doing this type of research:
Question 1
In the Burp Suite Program that ships with Kali Linux, what mode would you use to manually send a request (often repeating a captured request numerous times)?
Walkthrough:
When putting together an effective search, try to identify the most important key words. These are non-fluff words that provide an active description of what it is we need. Looking at the question, we see the following key words:
Burp Suite, Kali Linux, mode, manual, send, request, repeat
Now let’s use these keywords in combination to perform a useful search. We know that we are asking specifically about a feature (mode) in Burp Suite, so we definitely want to include this term. Then we can combine it with other keywords to come up with potentially useful combinations:
Burp Suite manual send request mode
Burp Suite repeat request
Burp Suite send request manual
They seem repetitive but sometimes removing or adding a single keyword can change the search engine results significantly. In this case, all of these combinations resulted in my finding the answer on the very first entry in the search engine results page.
Answer:
Repeater
Question 2
What hash format are modern Windows login passwords stored in?
Walkthrough:
Using the same method as above, we identify the keywords:
Hash, format, modern, Windows, login, passwords, stored
hash format Windows login passwords
Windows hash format login password storage
Login password storage hash format Windows
Using any of these word combinations results in similar results. I quickly learn that there are two common Windows hash formats; LM and NTLM. NTLM is the newer format.
Answer:
NTLM
Question 3
What are automated tasks called in Linux?
Walkthrough:
Once again, we start by identifying the keywords in the question:
automated, tasks, Linux
There are only a few ways to combine these and they should all yield similar results in the search engine.
Answer:
Cron Jobs
Question 4
What number base could you use as a shorthand for base 2 (binary)?
Walkthrough:
Identifying the keywords:
number base shorthand base 2 binary
Again, we can use some combination of these to find what we’re looking for.
Answer:
Base 16
Question 5
If a password hash starts with $6$, what format is it (Unix variant)?
Walkthrough:
This one was a little trickier. I started with the keywords I could find in the question:
password hash $6$ format Unix
I quickly found that the $6$ indicated the SHA-512 algorithm, but this didn’t fit the format that TryHackMe wanted the answer in.
I performed another search, this time using SHA512 to narrow down the field.
Answer:
sha512crypt
Task 3 – Vulnerability Searching
In order to effectively hack a system, we need to find out what software and services are running on it. As we find out about different types of software on a target, we need to check for existing/known vulnerabilities for that software.
Lucky for hackers, there are existing websites that contain searchable databases of vulnerabilities. Some of most common are ExploitDB and NVD (National Vulnerability Database).
In addition, Kali Linux also comes with the ‘searchsploit’ tool pre-installed, which allows us to use the command line to search ExploitDB.
Question 1
What is the CVE for the 2020 Cross-Site Scripting (XSS) vulnerability found in WPForms?
Walkthrough:
Navigate to ExploitDB and search for ‘WPForms’. There are two results, both of which involve cross-site scripting but only one of which has a CVE.
Answer:
CVE-2020-10385
Question 2
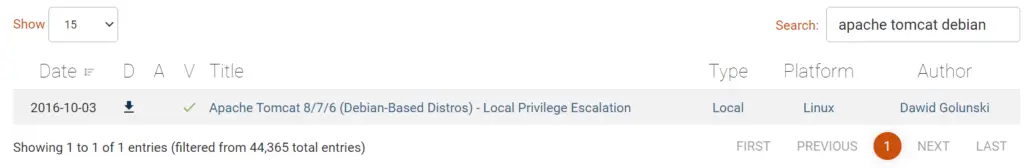
There was a Local Privilege Escalation vulnerability found in the Debian version of Apache Tomcat, back in 2016. What’s the CVE for this vulnerability?
Walkthrough:
I performed an exploit-db search for ‘apache tomcat’ and got about 60 results so I ran another search, this time using the phrase ‘apache tomcat debian’. I found only one result, which turned out to be our target.
Answer:
CVE-2016-1240
Question 3
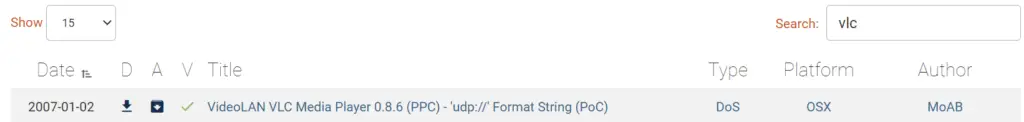
What is the very first CVE found in the VLC media player?
Walkthrough:
This time, I performed a search on exploit-db using the term ‘vlc’, and then sorted by date to find the first CVE.
Answer:
CVE-2007-0017
Question 4
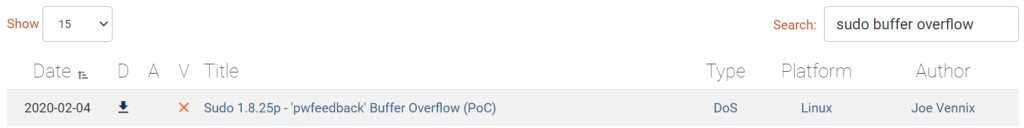
If you wanted to exploit a 2020 buffer overflow in the sudo program, which CVE would you use?
Walkthrough:
I used exploit-db to search for ‘sudo buffer overflow’. Once again, the first result is our target:
Answer:
CVE-2019-18634
Task 4 – Manual Pages
Manual (‘man’) pages are great for finding help on many Linux commands. Since there are so many commands with different syntax and so many options available to use, it isn’t possible to memorize all of them. This is often where the man pages come in; they often provide a good overview of the syntax and options for that command.
To access the man page for a command, just type ‘man <command>‘ into the command line.
Question 1
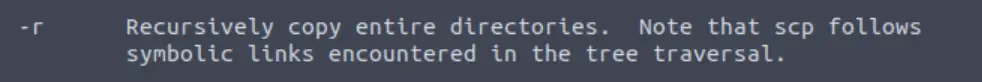
SCP is a tool used to copy files from one computer to another.
What switch would you use to copy an entire directory?
Walkthrough:
Access the man page for scp by typing ‘man scp’ in the command line.
Scan the man page for entries related to directories. I found the following entry:
Answer:
-r
Question 2
fdisk is a command used to view and alter the partitioning scheme used on your hard drive.
What switch would you use to list the current partitions?
Walkthrough:
Pull up the man page for fdisk and start scanning it for anything that would correspond to listing the current partitions. This was very easy to find.
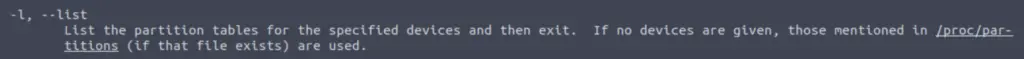
Answer:
-l
Question 3
nano is an easy-to-use text editor for Linux. There are arguably better editors (Vim, being the obvious choice); however, nano is a great one to start with.
What switch would you use to make a backup when opening a file with nano?
Walkthrough:
This time I tried to narrow down my results by piping the man page into the grep command, searching for the term ‘backup’:
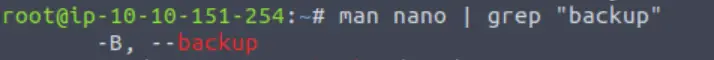
This might be the answer but I decided to pull up the actual man page and read the corresponding entry:
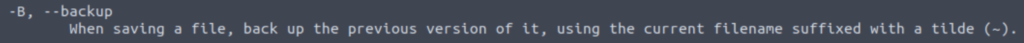
This sounds reasonable.
Answer:
-B
Question 4
Netcat is a basic tool used to manually send and receive network requests.
What command would you use to start netcat in listen mode, using port 12345?
Walkthrough:
This time we need to use the netcat man page, looking for two pieces of information:
(1) how to start in listen mode
(2) how to specify the port number (12345)
We can again pull up the man page for netcat using ‘man netcat’.
(1) The option that lets you start in listen mode:
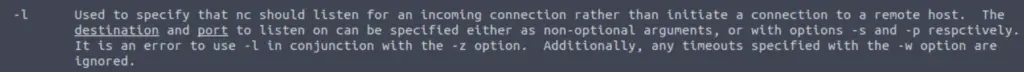
(2) The option that allows you to specify the port number:
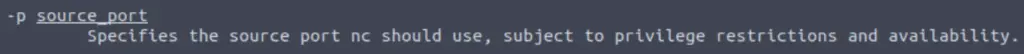
Now combine these into the command.
Answer:
nc -l -p 12345
Task 5 – Final Thoughts
There are lots of skills that are needed for hacking, but one of the most important is the ability to do research. Being able to search for different things and be flexible is an incredibly useful attribute.
Question 1
Research Complete!
Answer:
No answer needed
Conclusion
This room is interesting in that it is trying to pursue a tough goal; teaching the importance of research. In the field of cyber in general, there are going to be times when you don’t know what to do or how to proceed. You need to be able to search for things, scan for related materials, and quickly assess information to figure out what is actionable.
We are also introduced to exploit-db and a few really important linux commands. This is great for passive learning.
A huge thanks to MuirlandOracle for putting this room together!