Day 12 – Sharing Without Caring
Question 1
Scan the target server with the IP 10.10.52.77. Remember that MS Windows hosts block pings by default, so we need to add -Pn, for example, nmap -Pn 10.10.52.77 for the scan to work correctly. How many TCP ports are open?
In addition to the -Pn flag, I also used the -T4 flag to speed up the scan:
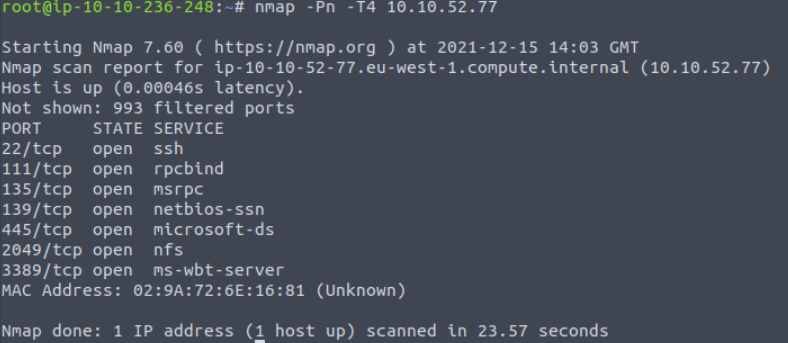
Answer:
(Highlight below to see answer):
7
Question 2
In the scan results you received earlier, you should be able to spot NFS or mountd, depending on whether you used the -sV option with Nmap or not. Which port is detected by Nmap as NFS or using the mountd service?
We actually found this answer in the previous scan but for completion’s sake I performed the scan again using the -sV flag. I limit the scan to the known open ports using the -p flag to keep the scan fast, also scanning port 1 so that we are scanning one closed port in addition to the open ports, which can help nmap with version detection:
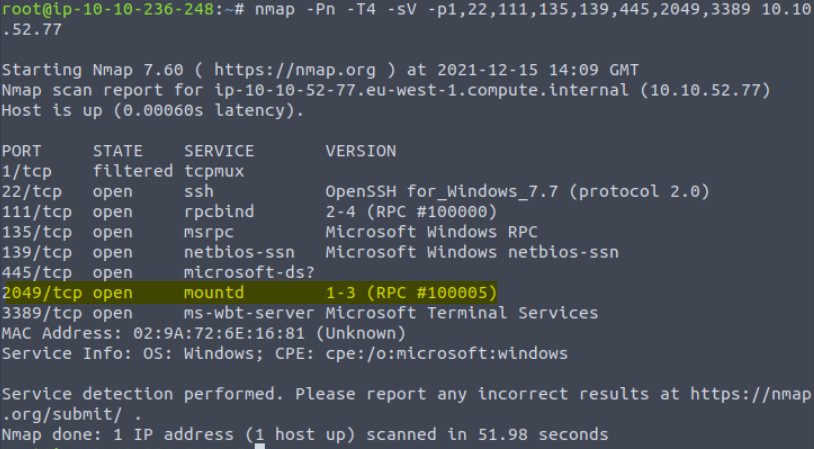
In the first scan, TCP port 2049 was identified as using nfs in the original scan, and mountd with a version of 1-3 (RPC #100005) in the second scan using -sV version detection.
Answer:
(Highlight below to see answer):
2049
Question 3
Now that we have discovered an NFS service is listening, let’s check what files are being shared. We can do this using the command showmount. In the terminal below, we run showmount -e 10.10.52.77. The -e or --exports show the NFS server’s export list.
As we can see in the terminal output above, we have two shares, /share and /my-notes. After you have started the attached machine, use the AttackBox terminal to discover the shares on 10.10.52.77.
How many shares did you find?
Using the showmount command to print the export list on the NFS server:
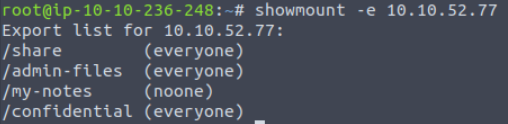
How many total shares are there?
Answer:
(Highlight below to see answer):
4
Question 4
How many shares show “everyone”?
Inspect the previous result:
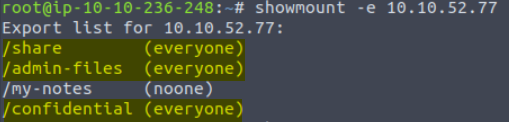
Answer:
(Highlight below to see answer):
3
Question 5
What is the title of file 2680-0.txt?
Observe the set of shares that we just found. Three are accessible to everyone (/share, /admin-files, /confidential), and one is not (/my-notes).
We want to mount these shares to our local drive so that we can access them; we can do so using the mount command with syntax:
mount 10.10.10.10:</share> <mount point>
The <share> is the name of the share we want to mount, and the <mount point> is a directory that we will mount into.
In the example on THM, we are told create a directory named tmp1 using the mkdir command, and then attempt to mount the /my-notes share:
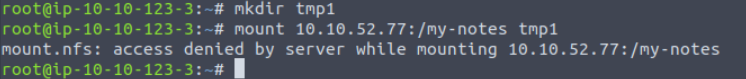
This doesn’t work because /my-notes is the one share that is accessible to ‘noone’.
Instead we mount the /share directory:
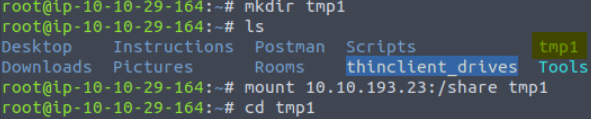
Now that we’ve entered our mount point, we can list the files and read them using nano:
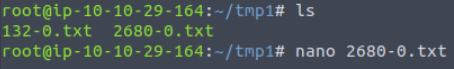
You should enter the nano editor, where we can see the title:
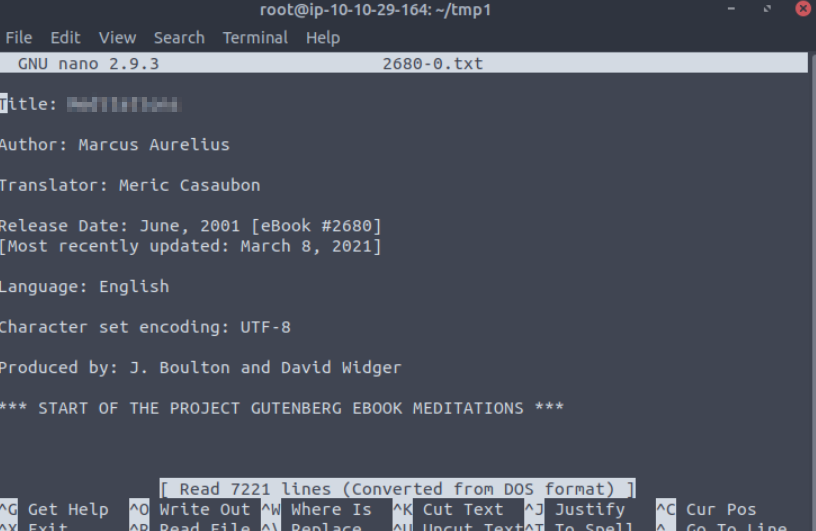
Answer:
(Highlight below to see answer):
Meditations
Question 6
It seems that Grinch Enterprises has forgotten their SSH keys on our system. One of the shares contains a private key used for SSH authentication (id_rsa). What is the name of the share?
I used nano to check out the other file in this share, which turned out to be Sun Tzu’s The Art of War.
There’s nothing useful here, so let’s check out the other shares.
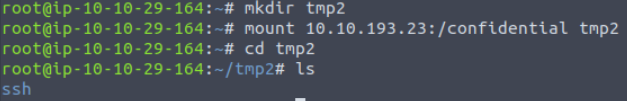
Looks like this might be the one.
Answer:
(Highlight below to see answer):
/confidential
Question 7
We can calculate the MD5 sum of a file using md5sum FILENAME. What is the MD5 sum of id_rsa?
Navigating into the directory we just found and using ls we find two files:
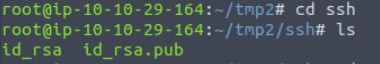
The first, id_rsa is the private key whereas id_rsa.pub is the public key.
We want to calculate the md5sum, which is used to verify file integrity.
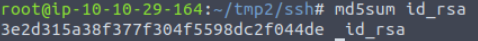
Answer:
(Highlight below to see answer):
3e2d315a38f377f304f5598dc2f044de