Day 16 – OSINT Ransomware Madness
OSINT is the process of gathering and analyzing as much useful information about a target as possible, using publicly available resources.
Question 1
!!! ВАЖНЫЙ !!! Ваши файлы были зашифрованы Гринчем. Мы используем самые современные технологии шифрования. Чтобы получить доступ к своим файлам, обратитесь к оператору Grinch Enterprises. Ваш личный идентификационный идентификатор: «b288b97e-665d-4105-a3b2-666da90db14b». С оператором, назначенным для вашего дела, можно связаться как “GrinchWho31” на всех платформах. !!! ВАЖНЫЙ !!!
I loved the fact that this challenge starts with this Cyrillic looking text!
First things first, I translated the text into English using Google translate:
!!! IMPORTANT !!! Your files were encrypted by the Grinch. We use the most advanced encryption technology. Contact your Grinch Enterprises operator to access your files. Your personal ID is “b288b97e-665d-4105-a3b2-666da90db14b”. The operator assigned to your case can be contacted as "GrinchWho31" on all platforms. !!! IMPORTANT !!!
No answer needed
Question 2
What is the operator’s username?
This can be found in the translated text (above).
Answer:
(Highlight below to see answer):
GrinchWho31
Question 3
What social media platform is the username associated with?
I performed a Google search of ‘GrinchWho31’ and found results on Reddit but that wasn’t the answer TryHackMe was looking for, so I continued down the search engine results page:
Answer:
(Highlight below to see answer):
Question 4
What is the cryptographic identifier associated with the operator?
Navigating to GrinchWho31’s page on Twitter, I found the following recent tweet:
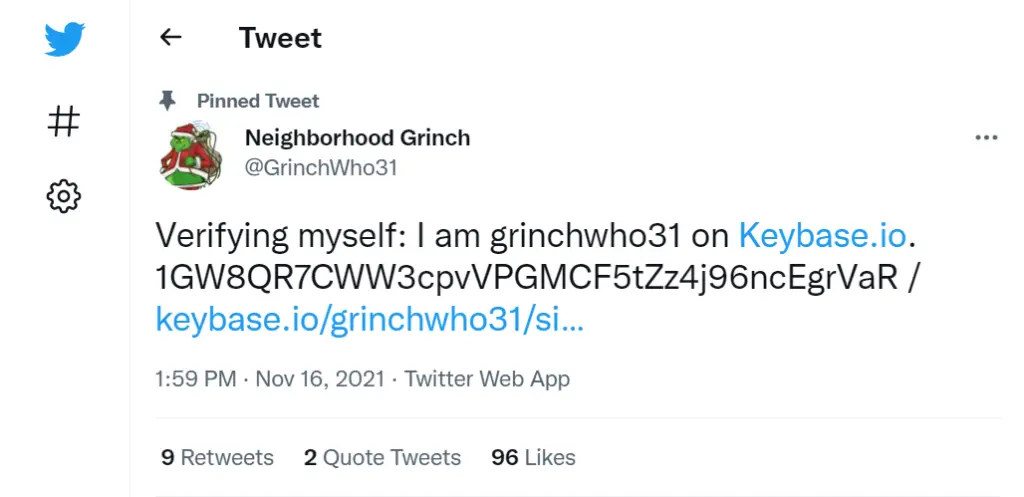
There’s a weird number/letter combination that looks like it could be the cryptographic identifier we’re looking for.
Answer:
(Highlight below to see answer):
1GW8QR7CWW3cpvVPGMCF5tZz4j96ncEgrVaR
Question 5
What platform is the cryptographic identifier associated with?
There’s a link to the platform immediately following the identifier.
Answer:
(Highlight below to see answer):
keybase.io
Question 6
What is the bitcoin address of the operator?
Following the link through to keybase.io, I found this page:
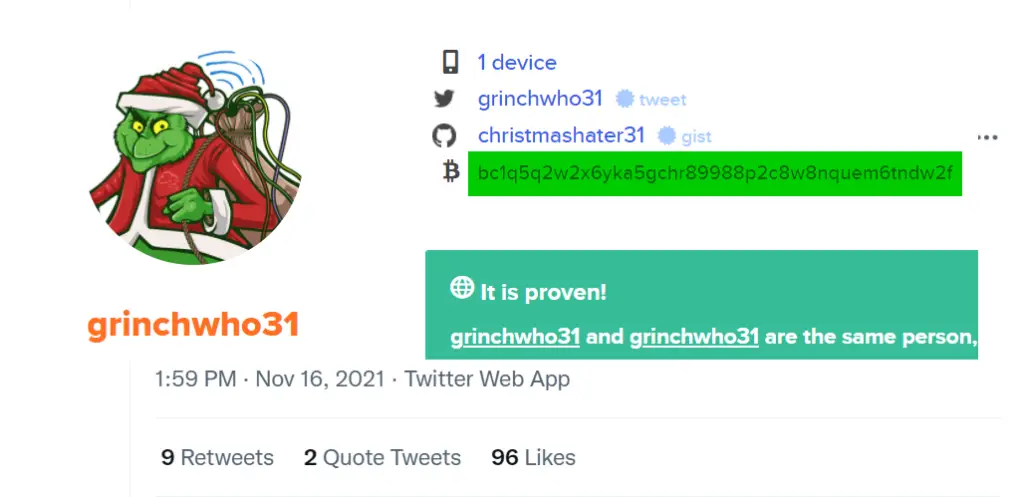
GrinchWho31 has an account here. It looks like he has connected a twitter and a github account as well as a bitcoin address.
Answer:
(Highlight below to see answer):
bc1q5q2w2x6yka5gchr89988p2c8w8nquem6tndw2f
Question 7
What platform does the operator leak the bitcoin address on?
We’ve been to the GrinchWho31’s Twitter and keybase.io pages. There’s another account on a third platform that is linked to.
Answer:
(Highlight below to see answer):
GitHub
Question 8
What is the operator’s personal email?
Follow the link to ChristmasHater31’s github page. We see two repositories, ChristBASHTree and Christmas-Stealer.
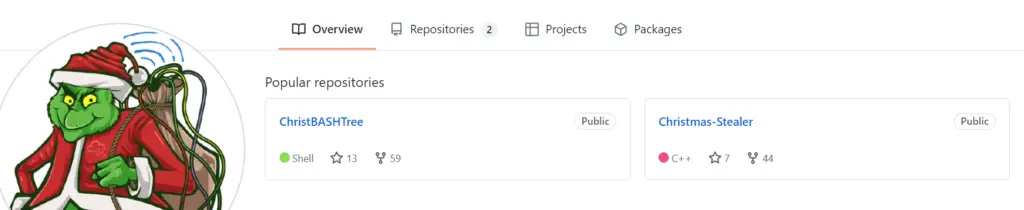
Christmas-Stealer sounded interesting so I looked around but didn’t see anything related to a personal email address. There’s only 1 commit, so I checked out ChristBASHTree.
The code didn’t have anything that jumped out but there was another commit. Clicking on the ‘Update tree.sh’ commit, I was able to see what was changed; at the very end there was originally a name and email address:
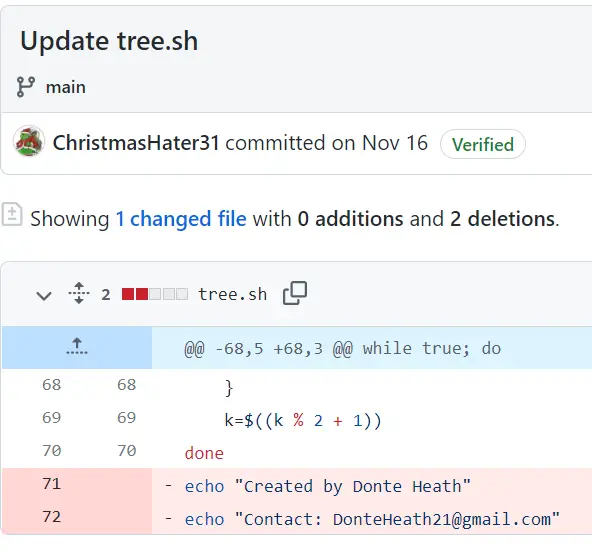
Answer:
(Highlight below to see answer):
Question 9
What is the operator’s real name?
Answer:
Donte Heath