Day 18 – Playing With Containers
Advent of Cyber 3, Day 18 is all about using and hacking Docker. In this walkthrough, I’ll cover every step needed to complete today’s tasks, and more importantly, understand what we’re doing.
Docker is a virtualization software designed to help developers build and deploy applications quickly.
Let’s break this down to help you understand Docker quickly and intuitively. First, what is virtualization?
Virtualization is the process of creating a simulated environment that abstracts away essential underlying components of a computer, such as the hardware. For example, the AttackBox on TryHackMe allows us to interact with a computer environment without the computer physically being in front of us. The AttackBox is a virtual machine (VM). VMs allows a single physical computer to ‘carve up’ its resources into multiple virtualized computers.
So what’s the difference between Docker and a VM like the AttackBox?
Well, every VM requires its own OS as well as virtual copies of the hardware needed for the OS to function. This means that VMs are resource intensive.
This is where Docker comes in. Instead of virtualizing the entire computer like a VM, Docker only virtualizes the OS.
Docker containers sit on top of the OS of the host machine and share the OS kernel, binaries, and libraries. This does introduce one limitation – containers must share the OS of their host machine. So a container running Windows will need to be on a Windows machine, and a container running Linux requires a Linux machine.
The advantage is that containers are extremely lightweight, requiring less storage, memory, and even time to complete basic functions like starting up.
Question 1
What command will list container images stored in your local container registry?
Let’s start our journey into Docker by starting the AttackBox or accessing a Docker-ready machine as described in the TryHackMe writeup.
The writeup also gives us the command we need expressly, but let’s say we didn’t’; what could we do to figure it out?
One command combination I like is a –help flag piped into grep with the search term in question. In this case, I am looking for a command that will list container images, so I’d use something like:
docker –help | grep “images”
This gives me the following result:
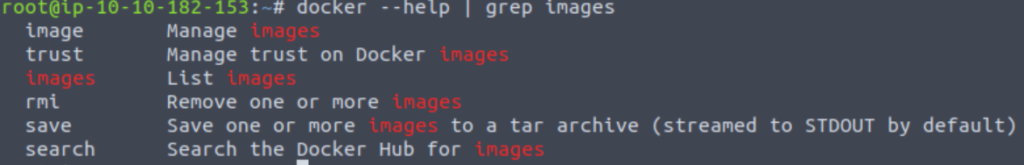
A short list, and I quickly identify the ‘images’ option as a prime candidate.
Answer:
(Highlight below to see answer):
docker images
Question 2
What command will allow you to save a docker image as a tar archive?
We can answer this question using the same technique of piping the docker –help results into grep, this time looking for the string “save”:
docker –help | grep “save”
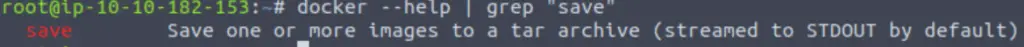
Answer:
(Highlight below to see answer):
docker save
Question 3
What is the name of the file (including file extension) for the configuration, repository tags, and layer hash values stored in a container image?
If you haven’t yet, run the ‘docker images’ command. This will list the container images that are currently stored in the local container registry.
Use the ‘docker pull’ command to retrieve the latest image from GrinchEnterprises’ publicly available Elastic Container Registry (ECR):
docker pull public.ecr.aws/h0w1j9u3/grinch-aoc:latest
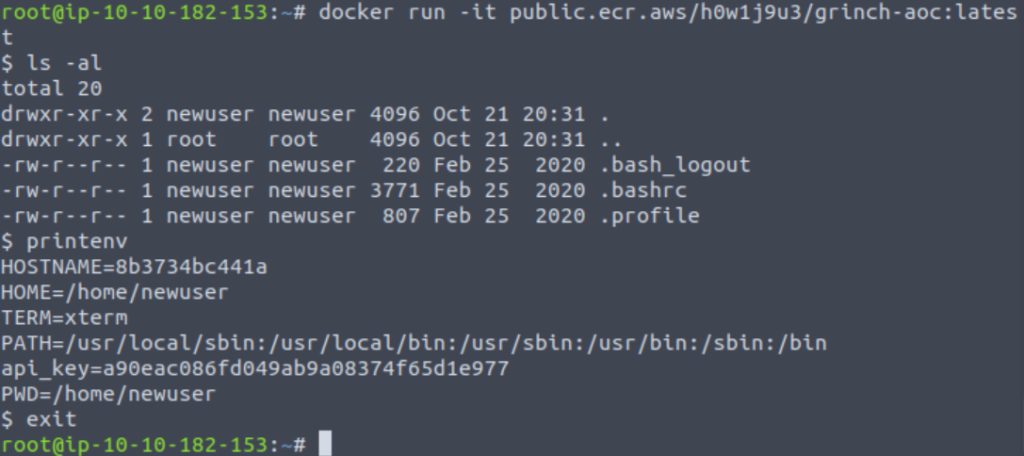
Next, we can start a shell allowing us to interact with the container using the ‘docker run’ command:
docker run -it public.ecr.aws/h0w1j9u3/grinch-aoc:latest
This will open a command prompt indicated by a dollar sign ($). We can do some recon here using Linux commands like ‘ls’ and ‘printenv’, but our challenge requires that we exit the shell:
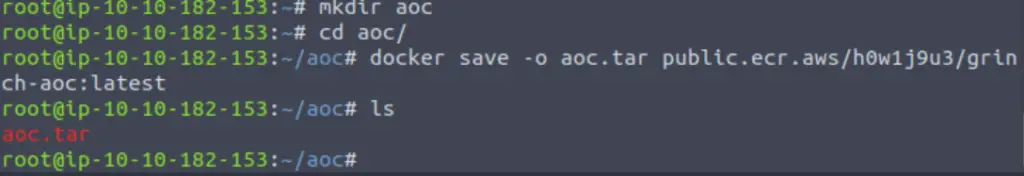
Create a directory ‘aoc’:
mkdir aoc
Then change to the new directory:
cd aoc
Save the docker image as a .tar (tape archive) file called ‘aoc.tar’:
docker save -o aoc.tar public.ecr.aws/h0w1j9u3/grinch-aoc:latest
Unpack aoc.tar using the ‘tar’ command:
tar -xvf aoc.tar
Now we’ll use the jq tool to pretty-print output to improve readability; jq comes pre-installed on the AttackBox.
Let’s read manifest.json using cat and jq:
cat manifest.json | jq
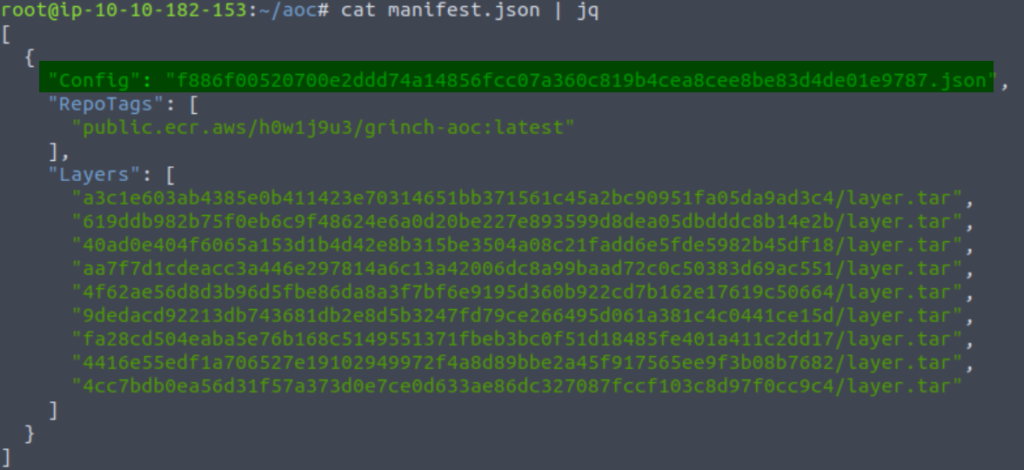
Note the .json file that is flagged as “Config” (highlighted above).
Going back to the original question, we were asked to find a file containing configuration data, repository tags, and layer hash values. Could this be the one?
Following this thread, we can also see what’s inside the config file using:
cat f886f00520700e2ddd74a14856fcc07a360c819b4cea8cee8be83d4de01e9787.json | jq
Answer:
(Highlight below to see answer):
manifest.json
Question 4
What is the token value you found for the bonus challenge?
The rest of this challenge would normally require spending time going through the different layers and trying to find things of interest, but we are guided to find the answer to the last question.
First, change directories (use the ‘Tab’ key autocomplete so you don’t have to copy or type the full directory name):
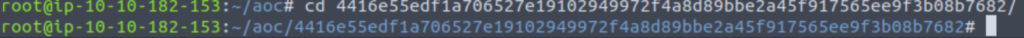
Unpack layer.tar:
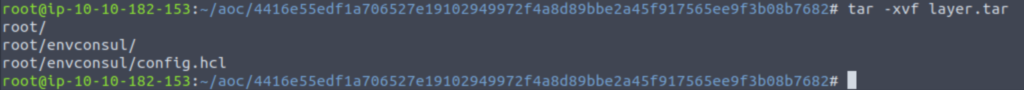
Now let’s read root/envconsul/config.hcl using cat:

We can look through the file manually, or we can grep for the string “token” since this is what we are asked to find in the question.
cat root/envconsul/config.hcl | grep “token”
Answer:
(Highlight below to see answer):
7095b3e9300542edadbc2dd558ac11fa