TryHackMe – Advent of Cyber 3 – Day 2
On day 2 we get to hack a real website by manipulating cookies.
THM’s writeup for Day 2 is excellent so I won’t attempt to recreate it here. The important thing we need to know is that cookies are a way of storing data. They are the solution to the problem that HTTP is a stateless protocol. In contrast, TCP and FTP are stateful protocols.
This means that the server doesn’t store information about who is making requests; cookies can be freely manipulated, allowing us to do things like pretending to be another user.
Question 1
Open the static site in a new tab, here.
Click on the link to open up the site and open up developer tools in your browser. Navigate to the tab corresponding to cookies (‘Storage’ in Firefox, ‘Application’ in Edge/Chrome).
You’ll see a login screen with a link to register for a new account. Click on the link and register with a fake name and email address. For this example, I will be using the name ‘Bob’, password of ‘Burger’ and email address [email protected]:
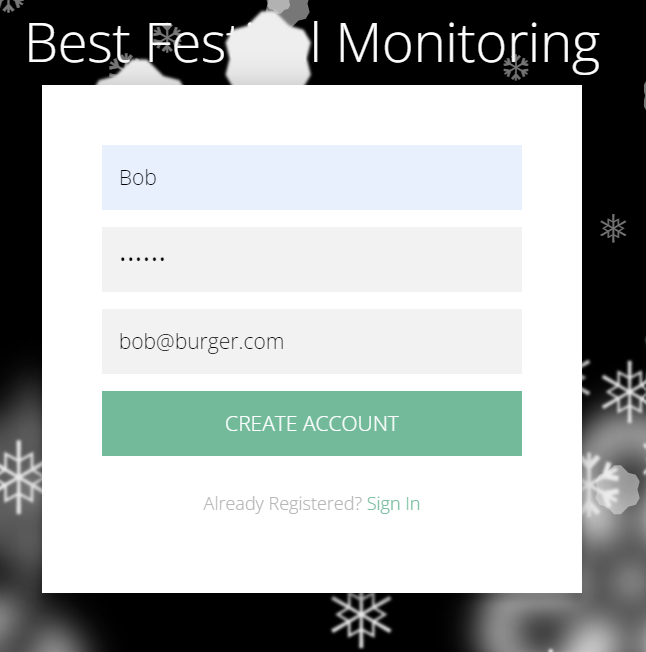
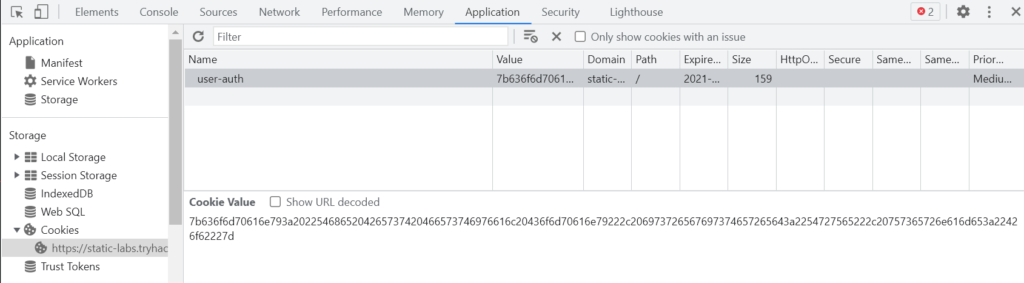
Click on ‘Create Account’, and you should see a cookie appear in the Developer console. This is how it looks in Chrome:
It looks similar in Firefox:
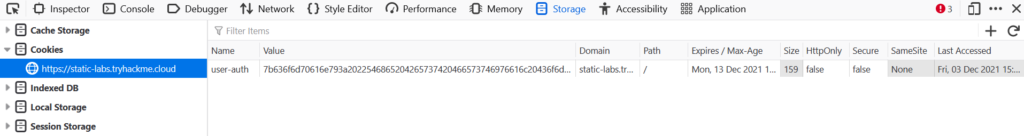
In both cases, we can see the name of the cookie, its’ value, and other information such as expiration information.
Answer:
No answer needed
Question 2
What is the name of the new cookie that was created for your account?
Follow the instructions above to get the name of the cookie.
Answer:
(Highlight below to see answer):
user-auth
Question 3
What encoding type was used for the cookie value?
We can see that the cookie value is a long string of characters:
7b636f6d70616e793a2022546865204265737420466573746976616c20436f6d70616e79222c206973726567697374657265643a2254727565222c20757365726e616d653a22426f62227d
Clearly this cookie has been encoded. In its’ current state it doesn’t mean much to us, but maybe we can figure out how to decode it.
Luckily there are existing applications that can do the heavy lifting for us. One popular application is CyberChef, we can be accessed here.
Start by pasting the value of the cookie into the ‘Input’ field in CyberChef. An icon of a magic wand should appear next to the ‘Output’ field title. Click on the magic wand:
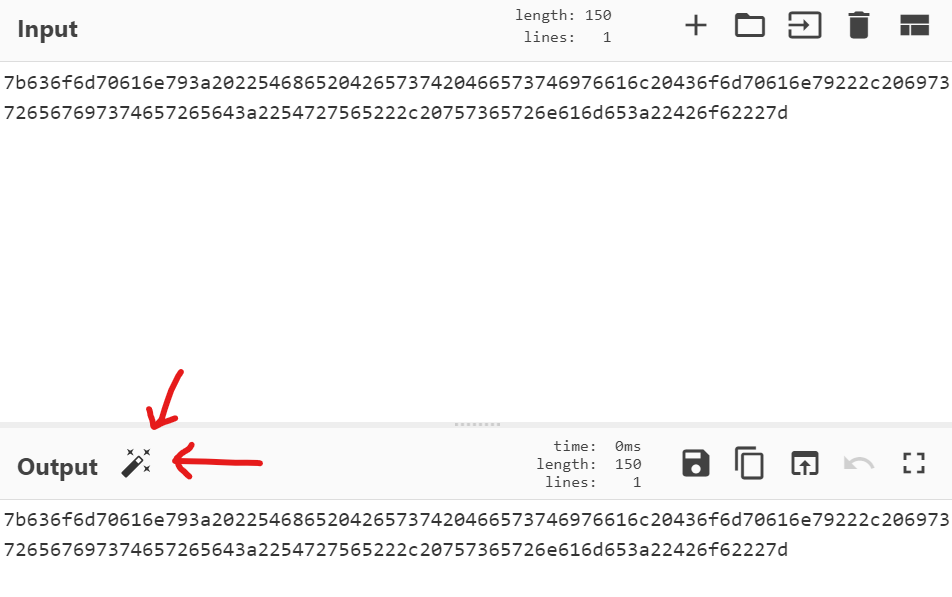
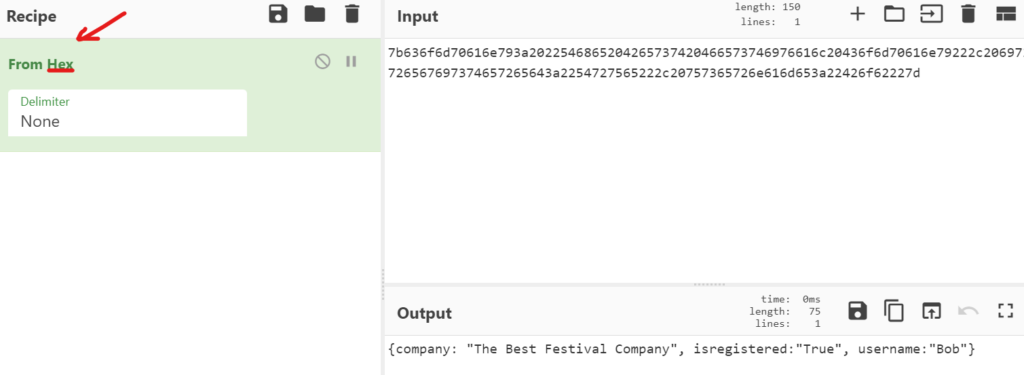
CyberChef can automatically detect the type of encoding that is used, and should output something that is much more readable.
The ‘Recipe’ field will show us what type of encoding was used:
Answer:
(Highlight below to see answer):
hexadecimal
Question 4
What object format is the data of the cookie stored in?
CyberChef has given us the decoded cookie, which looks like this:
{company: “The Best Festival Company”, isregistered:”True”, username:”Bob”}
This type of object notation is mentioned in THM’s writeup for this Task (Day 2). As a further hint, this type of object notation was derived from the JavaScript programming language.
Answer:
(Highlight below to see answer):
JSON
Question 5
Manipulate the cookie and bypass the login portal. What is the value of the administrator cookie? (username = admin)
OK. So we’ve decoded the cookie into JSON (JavaScript Object Notation), which is readable to us.
Now we need to manipulate the cookie so that we can trick the server into thinking that we’re the administrator!
Let’s look again at the decoded cookie:
{company: “The Best Festival Company”, isregistered:”True”, username:”Bob”}
The whole cookie consists of three attribute/value pairs. Since we want to fool the server into thinking that we are the administrator, let’s go ahead and change the value of the username attribute to ‘admin’:
{company: “The Best Festival Company”, isregistered:”True”, username:”admin”}
The server is expecting hexadecimal, not JSON so we need to re-encode our manipulated cookie in order for our attack to work. Luckily we can use CyberChef to do this for us.
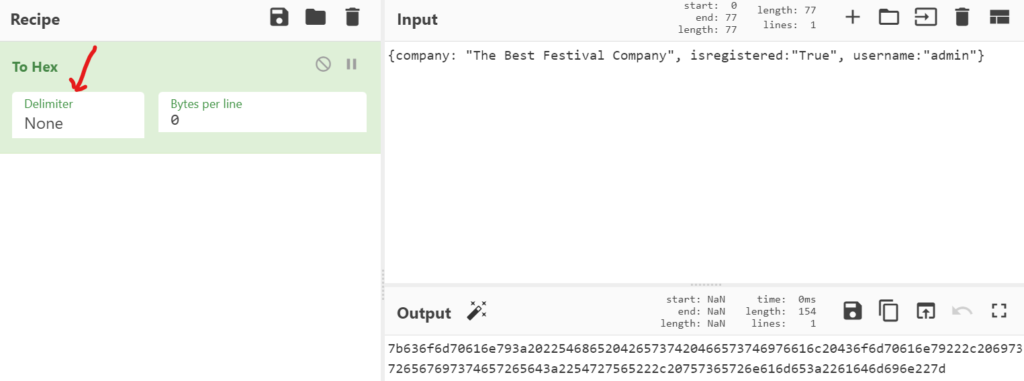
Copy the manipulated cookie into the ‘Input’ field. CyberChef doesn’t know what we want it to do with it, so double click the ‘To Hex’ button on the left side of the screen. By default, CyberChef will use a delimiter of space so our re-encoded cookie will contain spaces that we didn’t see in the original cookie. Select a delimiter of ‘none’ to remove the spaces:
Answer:
(Highlight below to see answer):
7b636f6d70616e793a2022546865204265737420466573746976616c20436f6d70616e79222c206973726567697374657265643a2254727565222c20757365726e616d653a2261646d696e227d
Question 6
What team environment is not responding?
Return to the Developer tools console and replace the original value of the cookie with the new one.
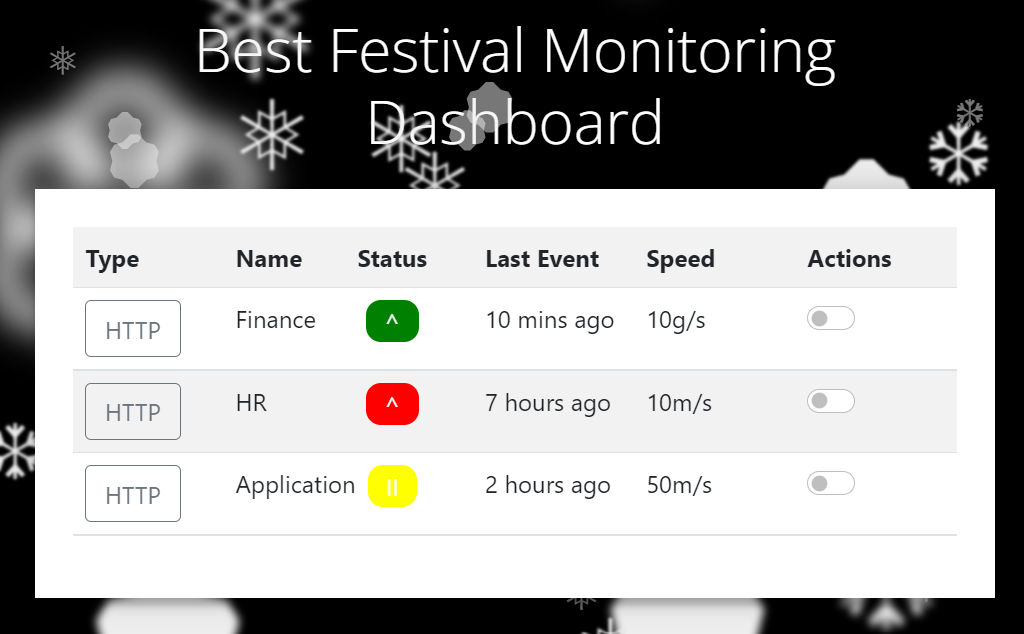
Refresh the page and you should see the ‘Best Festival Monitoring Dashboard’ page. Our attack worked!
There are three teams shown on the dashboard, each with information including a green/yellow/red status indicator.
The red status indicator shows us that one team environment is not responding.
Answer:
(Highlight below to see answer):
HR
Question 7
What team environment has a network warning?
This is the team environment with a yellow status indicator.
Answer:
(Highlight below to see answer):
Application