TryHackMe – Advent of Cyber 3 – Day 3 – Walkthrough
Enumeration is key. This is one of the most important lessons to learn when starting out in offensive cybersecurity.
Enumeration is the process of discovering as much about potential attack vectors as possible. It’s part of information gathering, and typically involves trying to make an active connection with the target.
The type of enumeration depends on the target itself. For web applications, one of the primary forms of enumeration is content discovery. This means discovering as much about the web application as possible. We want to identify all of the directories and files, if possible. Every piece of information can potentially be used offensively. We might find documents and pages that we weren’t supposed to see, and can sometimes use them to gain access to an internal system.
The most common way of performing content discovery is using tools that rely on brute-force techniques to find content. It all starts with a wordlist. A wordlist is a list of words that are used, one by one, to find directories and files. Each word is appended to the end of the web app’s URL and the tool tries to determine if the specific combination is valid, which will happen if a Status Code of OK is returned. Wordlists are typically generated using the most statistically common names for directories and files, making discovery of a given page or file to be likely. The longer the wordlist, the higher the chances of successful discovery but the longer the scan will take.
One of the most common tools is dirb. Kali Linux (the OS installed on the AttackBox machine) comes with dirb and a good selection of wordlists.
To proceed, we’ll need to launch both the target machine for the task, as well as the THM AttackBox (unless you’re using an OpenVPN client).
Launch the target machine by clicking the green ‘Start Machine’ button at the top of the task:
Launch the AttackBox by using the blue ‘Launch AttackBox’ button at the top of the page.
Question 1
Using a common wordlist for discovering content, enumerate http://<IP> to find the location of the administrator dashboard. What is the name of the folder?
Open a terminal and use dirb to enumerate the target. The syntax for using dirb is:
dirb http://<IP> <wordlist>
For example, if we have an IP address of 10.10.10.10 and want to use the ‘big.txt’ dirb wordlist, we would use:
dirb http://10.10.10.10 /usr/share/wordlists/dirb/big.txt
Try experimenting with different lists to see the results and how fast they are.
Using the ‘big.txt’ wordlist, I was able to find the answer to this question in just a few seconds.
Answer:
(Highlight below to see answer):
admin
Question 2
In your web browser, try some default credentials on the newly discovered login form for the “administrator” user. What is the password?
Open a web browser and navigate to the admin page we just found. Using the earlier example of IP address 10.10.10.10, this would correspond with navigating to:
http://10.10.10.10/admin/
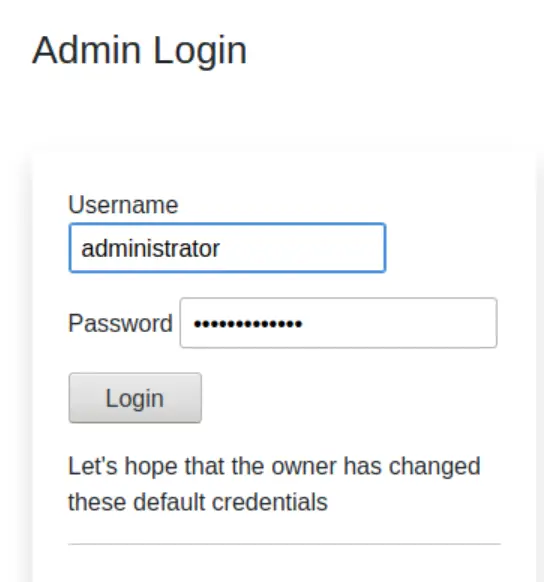
The page contains a login form as well as a statement indicating that default credentials were initially used.
Let’s try some common default credentials and see if we can gain access. The writeup on THM shows a few examples of common default credentials:
| Count | Username | Password |
| 1 | administrator | administrator |
| 2 | administrator | password123 |
| 3 | administrator | letmein |
Try these combinations to see what works!
Answer:
(Highlight below to see answer):
administrator
Question 3
Access the admin panel. What is the value of the flag?
Once you find the right combination, you will be taken to the admin panel. Scroll to the bottom of the page to find the flag.
Answer:
(Highlight below to see answer):
THM{ADM1N_AC3SS}