TryHackMe – Linux Fundamentals Part 2 – Complete Walkthrough
This Room is the second in the three part Linux Fundamentals series on TryHackMe.
It covers using SSH to log in to a remote machine, flags/switches, more filesystem commands, permissions, and some common root directories.
About This Walkthrough:
In this walkthrough (like all of my walkthroughs), I will not only cover what you need to get through the room, but I will also dive into the topics covered by the room itself. Instead of repeating the same information as the TryHackMe room, I try to cover the same topics using my own voice and perspective. My hope is that having an additional source of information and perspective will help support learning and retention of the same topics covered in the room. Sometimes I will also cover a topic that isn’t covered in the TryHackMe room because I feel that it may be a useful supplement at that point in the lesson. Feel free to use this room as a supplement rather than a walkthrough.
I also try to prevent spoilers by making finding the solutions a manual action, similar to how you might watch a video of a walkthrough (i.e. the answers are given, but they still require an intentional act to obtain). My recommendation is always to work as hard as you can through every problem and only use the solutions as a last resort.
I personally love TryHackMe and really appreciate everything that they do to make the field of cybersecurity more accessible and fun.
This room can be found at: https://tryhackme.com/room
- TryHackMe – Linux Fundamentals Part 2 – Complete Walkthrough
Walkthrough
Task 1 – Introduction
This room is the second in the three part ‘Linux Fundamentals’ series. The first part is considered a prerequisite, so go back and complete that one if you haven’t yet – it goes through a bunch of the most important commands and operators.
In this room, we’ll see flags and operators, learn permissions, and increase our aptitude with Linux filesystem management.
Question 1
Let’s proceed!
Answer:
No answer needed
Task 2 – Accessing Your Linux Machine Using SSH
This Task is super exciting, as we’ll be using a remote computer securely using a popular protocol known as SSH.
SSH, or secure shell, allows us to login and access a command line on a remote computer. It uses cryptography to secure the connection; this means that if our data is intercepted, it would still be protected by encryption. Data is encrypted before it is sent and then decrypted by the remote machine.
To complete this task, we need to deploy two machines at the same time:
(1) The ‘linuxfundpt2’ machine is deployed using the green ‘Start Machine’ button at the top of Task 2.
(2) The AttackBox is deployed using the blue ‘Start Attackbox’ button at the top of the page.
You will need to wait a minute for each one to load.
AttackBox is a fully featured Ubuntu Linux virtual machine (VM), which we’ll use in almost every Room involving Linux going forward. Once the AttackBox is loaded, use the icon on the desktop to access the terminal.
Next, we’ll use SSH to log in to our ‘linuxfundpt2’ machine. In the AttackBox terminal, type:
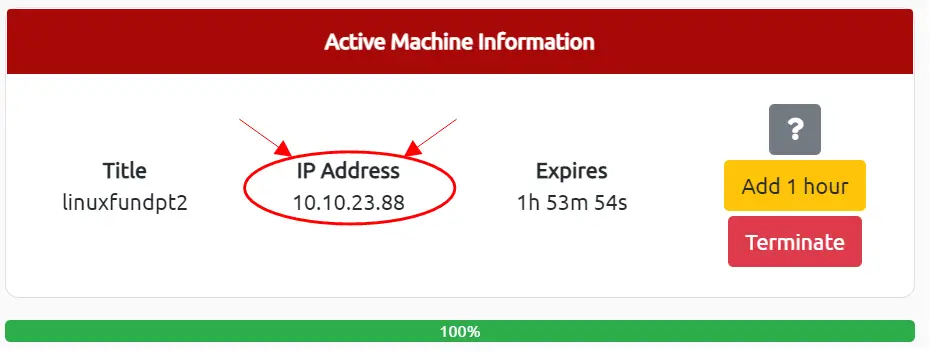
ssh tryhackme@<IP address>
The IP address can be found on the card for the ‘linuxfundpt2’ machine, which should be at the top of the page:
In this example, the exact command we would use is:
Note that ‘tryhackme’ here is a user; for this command to work, the ‘linuxfundpt2’ must already have a user named ‘tryhackme’.
You will see the following message, which basically just tells us that we haven’t used SSH to log into this computer before:
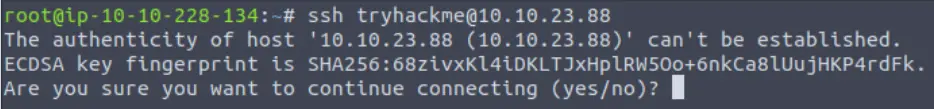
Type in ‘yes’ and you will be prompted for the password (this would be the password for user ‘tryhackme’). We are given the password ‘tryhackme’ so type that in and you should see a welcome message for the ‘linuxfundpt2’ machine.
Question 1
I’ve logged into the Linux Fundamentals Part 2 machine using SSH!
Answer:
No answer needed
Task 3 – Introduction to Flags and Switches
Most Linux commands have options, and we use code called flags or switches to access those options.
For example, if we use the ls command, we will be given a list of files and folders in the current working directory. If we add the -a flag to the command, i.e.:
ls -a
We will now see the hidden files and folders as well as the non-hidden ones. Hidden files and folders are marked with a dot ‘.’ before their name.
It would be tough to memorize every option for every command, so Linux helps us out by allowing us to view help or manual pages for commands.
These can be accessed in two ways: the –help flag or the man command.
The man command
We can use the man command, followed by the command that we want to learn about, to access that command’s manual page.
The manual page typically includes a description of the command, the general syntax of using the command, and a comprehensive list of options and the flags for those options. All you have to do is type in ‘man <command>’. For example, to see the manual page for the ls command, we would type:
man ls
You can even access the manual page for the man command by typing in ‘man man’.
The –help flag
Many commands will allow you to access a help screen by using the ‘–help’ flag. This option tends to be less comprehensive than the man page, but should give you all of the flag options for that command.
To use the –help flag for the ls command, you would type:
ls –help
Question 1
Explore the manual page of the ls command
Walkthrough:
Type ‘man ls’ and start getting familiar with the layout of man pages.
Answer:
No answer needed
Question 2
What directional arrow key would we use to navigate down the manual page?
Walkthrough:
Try it out; there are only four directional arrows so only one will be correct. You can also scroll through manual pages. Extensive details for how to use manual pages can be found by using the ‘man man’ command.
Answer:
(Highlight below to find the answer):
down
Question 3
What flag would we use to display the output in a “human-readable” way?
Walkthrough:
This question assumes that we are still in the ls manual page (‘man ls’).
As we scroll down the manual page for ls, you’ll notice that a large part of the manual page is the DESCRIPTION section, which lists all of the available options by their flags, in alphabetical order.
Scroll down through the manual page until you find the flag that corresponds with human readable output. What is this flag?
Answer:
(Highlight below to find the answer):
-h
Task 4 – Filesystem Interaction Continued
In ‘Linux Fundamentals Part 1’, we saw a number of commands to help us interact with the Linux filesystem. These commands were: ls, cd, cat, pwd, find, and grep.
We’ll continue to build on this with a bunch of new commands: touch, mkdir, cp, mv, rm, and file.
touch – creates a blank file
mkdir – creates a directory
cp – copies a file or directory (use the flag -r to copy a directory)
mv – moves a file or directory
rm – deletes a file or directory
file – determines file type
Question 1
How would you create the file named “newnote”?
Walkthrough:
We use the command to create a new file, ‘touch’ combined with the name of the new file we want to create.
If we wanted to create a file called ‘mynewfile’, we could use the command:
touch mynewfile
Answer:
(Highlight below to find the answer):
touch newnote
Question 2
On the deployable machine, what is the file type of “unknown1” in “tryhackme’s” home directory?
Walkthrough:
To complete this question, we must be logged in to the ‘linuxfundpt2’ machine as ‘tryhackme’. If you’re no longer logged in, use the procedure from Task 2 to use ssh to log in.
Also if you’re logged in to the ‘linufundpt2’ machine but have navigated away from the home directory, use ‘cd ~‘ to return to it. Remember you can also use the pwd command to determine where you are in the filesystem.
First, use the ‘ls’ command to list the files in the home directory. You should see three files, one of which is ‘unknown1’.
Next, we can use the ‘file‘ command to determine the file type of unknown1. If we wanted to find the file type of our fictional file ‘mynewfile’, we would use the following command:
file mynewfile
Knowing this, how can we determine the file type of file ‘unknown1’?
Answer:
(Highlight below to find the answer):
file unknown1
Question 3
How would we move the file “myfile” to the directory “myfolder”
Walkthrough:
If we use the command ‘ls’, we should see both the file ‘myfile’ as well as the directory ‘myfolder’.
There are two ways to get ‘myfile’ into ‘myfolder’; we can either make a copy (using the ‘cp‘ command) or we move it (using the ‘mv‘ command).
Since our instructions are to move the file, we should use the ‘mv‘ command.
Let’s go back to our fictional example using ‘mynewfile’. If we wanted to move ‘mynewfile’ into ‘myfolder’, we would use the following command:
mv mynewfile myfolder
Now it’s up to you to re-write this for ‘myfile’.
Answer:
(Highlight below to find the answer):
mv myfile myfolder
Question 4
What are the contents of this file?
Walkthrough:
The contents of a file can be viewed using the ‘cat‘ command.
Because ‘myfile’ is in the directory ‘myfolder’, there are several ways to get its contents using ‘cat’.
You can either navigate into myfolder (using ‘cd’) or execute the command from the home directory by directing ‘cat’ to myfolder/myfile.
From myfolder:
cat myfile
From the home directory:
cat myfolder/myfile
A third option is to use the && operator to combine ‘cd’ with ‘cat’ from the home directory, i.e.:
cd myfolder && cat myfile
Any of these methods should give you the flag you need to answer the question.
Answer:
(Highlight below to find the answer):
THM{FILESYSTEM}
Question 5
Continue to apply your knowledge and practice the commands from this task.
Walkthrough:
This question is a freebie. My recommendation is to combine the commands with the operators covered in Linux Fundamentals Pt. 1.
Answer:
No answer needed
Task 5 – Permissions 101
Different users and groups can have different permissions for files and folders. An analogy might be protecting a child from accessing adult-only files. A common example is preventing guests from accessing system files that could cause a major error if accidentally modified or deleted.
There are three permissions that can be set in Linux: read, write, and execute.
Read (abbreviated ‘r’) is the permission to read a file.
Write (abbreviated ‘w’) is the permission to edit a file.
Execute (abbreviated ‘x’) is the permission to run a file.
Luckily, it is very easy to see the permissions of any file or folder in Linux by using the ‘ls’ command with the ‘-l’ flag, which means ‘long’:
ls -l
If we do this, we’ll find a listing of files and their permissions. This will look like this:
root@ip-10-10-248-165:~# ls -l
total 28
drwxr-xr-x 3 root root 4096 Dec 29 2020 Desktop
drwxr-xr-x 2 root root 4096 Sep 10 2020 Downloads
drwxr-xr-x 2 root root 4096 Oct 30 2020 Instructions
drwxr-xr-x 2 root root 4096 Mar 18 19:35 Pictures
drwxr-xr-x 3 root root 4096 Aug 16 2020 Postman
drwxr-xr-x 2 root root 4096 Sep 3 12:22 Scripts
drwxr-xr-t 2 root root 4096 Aug 13 2020 thinclient_drives
lrwxrwxrwx 1 root root 19 Mar 18 17:52 Tools -> /root/Desktop/Tools
root@ip-10-10-248-165:~#
The permissions are on in the first column on the left, represented by ‘drwxrwxrwx’.
Here, the first letter ‘d’ stands for ‘directory’. A dash ‘-‘ signifies a file, and an ‘l’ represents a link file.
The next nine entries are three sets of a repeating pattern ‘rwx’, which stands for the ‘read, write, execute’ permissions of a specific party.
The three sets are:
(1) The file owner
(2) The group that the file is associated with
(3) All other users
A dash ‘-‘ means that no permission has been assigned, and a letter (r, w, or x) means that the owner, group, or other users have permission to complete that function.
For example:
drwxr-xr–
Means that it is a directory; the owner has permission to read,write, and execute, the group has permission to read and execute (but not to write), and all other users have permission to read but not write or execute.
Second column: how many links there are to the file.
Third column: the owner of the file.
Fourth column: the group owner of the file.
Fifth column: the size of the file, in bytes.
Sixth column: the last data and time that the file was modified.
Seventh column: filename or directory name.
Groups and Users
We’ve mentioned groups, but what are they? The idea of a group is creating a set of users that have shared permissions.
It gives us one more way to control permissions for files and directories.
Switching Between Users
Linux has a special command that enables switching between users: su.
The su command has different options. A common one uses the ‘-l’ flag, which allows you to inherit more of the permissions of the users you are using su to switch to.
Question 1
On the deployable machine, who is the owner of “important”?
Walkthrough:
To complete this question, we need to be connected to the ‘linuxfundpt2’ machine via SSH (Task 2, above).
Next, we run the ‘ls -l’ command to give us a list of files and folders in the working directory:
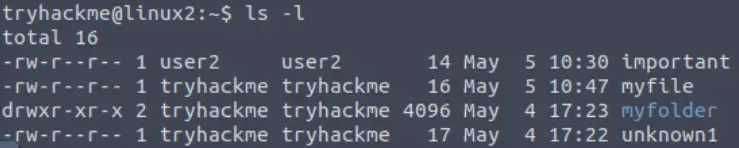
We can see that the top line corresponds with the file ‘important’ (the names of the files and folders are in the rightmost column).
The third column contains the entry for the file’s owner.
Answer:
(Highlight below to find the answer):
user2
Question 2
What would the command be to switch to the user “user2”?
Walkthrough:
We use the ‘su‘ command to switch users, using the following syntax:
su <username>
For example, if we want to switch to a user named ‘greg’, we would use the command:
su greg
Take this example and apply it to user ‘user2’.
Answer:
(Highlight below to find the answer):
su user2
Question 3
Now switch to this user “user2” using the password “user2”
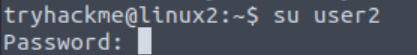
Walkthrough:
Use the command from the last question to switch users. You will be prompted to enter the password for user2 (which is also user2):
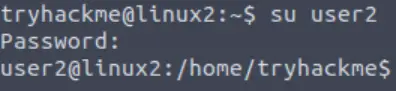
If successful, you should see username ‘user2’ reflected in the command prompt:
Answer:
No answer needed
Question 4
Output the contents of “important”, what is the flag?
Walkthrough:
Let’s use the cat command to read the file named ‘important’, using the following syntax:
cat <filename>
Answer:
(Highlight below to find the answer):
THM{SU_USER2}
Note that we didn’t actually need to login as user2 in order to read ‘important’. When we performed the ‘ls -l’ command earlier, we saw that all users have permission to read ‘important’.
Task 6 – Common Directories
This Task covers some of the most important and common directories in Linux.
Before we look at these directories, it’s important to note that we can always get to the root directory with the command:
cd /
Contrast this with the command that we can use to travel to our user’s home directory:
cd ~
The directories that we are covering in this Task can be found in the root directory, so feel free to use the ‘cd /’ command to travel to the root directory and investigate them for yourself:
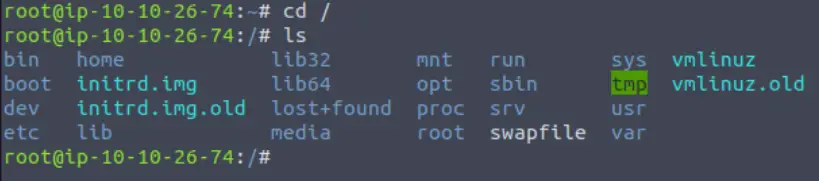
We’ll be covering the following directories: /etc, /var, /root, and /tmp.
Directory /etc
The /etc directory contains system configuration files that are used by the operating system.
Examples include the sudoer file, which contains a list of users having ‘sudo’ (super user do) permissions, as well as user password files.
Directory /var
The /var directory contains variable data such as logs or databases. The idea is that the /var folder contains information that is frequently accessed or edited.
Directory /root
The /root folder is the home directory for the root user.
Directory /tmp
You may have guessed this: the /tmp directory is used to store temporary files. The contents of the /tmp folder are deleted when the computer is restarted, similar to a computer’s memory (RAM).
Question 1
Read me!
Answer:
No answer needed
Question 2
What is the directory path that would we expect logs to be stored in?
Walkthrough:
Based on the description, we should expect logs to be stored somewhere in the /var directory.
If we list the contents of the directory, we can take a good guess:
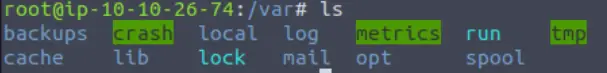
Take a look at each option. Which of these would be most likely to contain logs?
Answer:
(Highlight below to find the answer):
/var/log
Question 3
What root directory is similar to how RAM on a computer works?
Walkthrough:
This is mentioned in the write-up. As a tip, which directory is used to temporarily store data and clears out the data during restart?
Answer:
(Highlight below to find the answer):
/tmp
Question 4
Name the home directory of the root user
Walkthrough:
This is one of the common directories mentioned in the write-up.
Answer:
(Highlight below to find the answer):
/root
Question 5
Now apply your learning and navigate through these directories on the deployed Linux machine.
Walkthrough:
Try to navigate into each one, perform ‘ls’ commands, and guess what the different files and folders do. This is a great way to strengthen your command line skills; don’t forget to use ‘cd /’ to navigate to the root directory and ‘cd ~’ to go to the home directory.
Answer:
Paste and hide answer
Task 7 – Conclusions and Summaries
If you’re new to Linux, this room is definitely worth going through again. I’d also recommend continuing through the third room in the series and then doing the whole series again. Some of this material may have seemed difficult the first time through but it will quickly become easier.
Question 1
Proceed to the next task to continue your learning
Answer:
No answer needed
Task 8 – Linux Fundamentals Pt. 3
Let’s continue our Linux journey with the third (and final) part of the Linux Fundamentals series!
Here’s the link: https://tryhackme.com/room/linuxfundamentalspart3
Question 1
Terminate the machine from task 2!
Answer:
No answer needed
Question 2
Join Linux Fundamentals Part 3!
Answer:
No answer needed
Conclusion
This room is packed with useful information and exercises. I enjoy the fact that we are introduced to the idea of spinning up two virtual machines, one of which we access using SSH. This allows us to get familiar with this concept, which will later be expanded to actually attacking and gaining access to machines.
I also felt that this room did a great job of encouraging development of the same commands learned in Part 1. One suggestion might be to also have a few exercises requiring use of the Linux operators previously learned as well.
Overall, I really enjoyed this room. A huge thanks to tryhackme and cmnatic for putting this room together!