TryHackMe – Pickle Rick – Walkthrough and Notes

Pickle Rick is a beginner friendly, Rick and Morty themed CTF on TryHackMe. It covers port and directory enumeration, web app testing, source code analysis and basic Linux commands.
If you’ve been learning hacking via TryHackMe’s platform, you’ve probably worked through some Linux and Windows boxes (likely via SMB/Samba exploitation). Pickle Rick might be the first web-app CTF you encounter (or one of the first), and it is an excellent place to start.
Pickle Rick can be found at: https://tryhackme.com/room/picklerick
About This Walkthrough
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by making finding the solutions a manual action, similar to how you might watch a video of a walkthrough; they can be found in the walkthrough but require an intentional action to obtain. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
Walkthrough for TryHackMe Pickle Rick
Task 1 – Pickle Rick
Question 1
What is the first ingredient Rick needs?
As in any challenge, it’s always a good idea to start enumerating via port scanning. I like to start with a top-1000 (default) nmap scan with T4 timing to speed it up:
nmap -T4 <IP>
It looks like there are two ports open: port 22, which is the default SSH port and port 80, which is the default http port. This two-port combination of 22 and 80 is one of the most common in CTFs.
But nmap guesses these services and doesn’t give us any version information. At this point, it is often useful to continue our enumeration by running a version or -A (all) scan on the open ports we’ve found. Alternatively, many people just run a version or ‘all’ scan on the top 1000 ports, combining the two scans I’m running here. That can just take a bit longer for the scan to run.
nmap -T4 -A -p22,80 <IP>

Looks like we have an Ubuntu Linux machine running an Apache webserver on port 80 and OpenSSH on port 22. We also have version information for OpenSSH on port 22.
Good practice is to run a vulnerability to scan (such as nmap –script=vuln) and also manually enumerate these services to see if there are any known vulnerabilities for these service versions. In this case, I did not find anything of value.
SSH is rarely a direct path through a CTF although sometimes we can brute-force SSH credentials. In general when we see a combination of SSH and another service like http, it is the other service that will contain the path forward.
A great place to start enumerating http is by navigating to the IP address using a web browser. We want to carefully look at both the landing page and its’ source code.

The home/landing page contains a cool image and an interesting little description.
Looking at the source code, we find a username that probably should not have been left in the comments.

At this point, we don’t know what this username corresponds to. It could be SSH, or maybe a web login of some kind. A good next step is to enumerate the web server using dirb, dirbuster, or gobuster.
We also find links to an /asset directory that contains a number of Rick and Morty images and other files, but nothing that seems likely to help our progress in finding our flags.
I decided to use dirb because I’m most comfortable with it, and used the ‘big’ wordlist:
dirb http://<IP>/ /usr/share/wordlists/dirb/big.txt
The dirb scan uncovers two files to follow up on; server-status has a 403 code and is rarely a path forward, but robots.txt looks interesting. The robots.txt file typically contains information intended for web crawlers but it could contain other information as well.
Using the browser to navigate to <IP>/robots.txt:
There’s an interesting text string here…could this be a password? We found a potential username earlier in the source code of the home page, but we don’t know where these possible credentials might work.
We do know that SSH is running on the default port, so I decided to try our potential credentials to establish an SSH connection:
It looks like our attempt to connect via SSH was rejected by the server. It could be the case that we need to wrangle an SSH connection but this seems unlikely.
Instead I decided to enumerate a bit more. Starting with a more comprehensive dirb scan using the common extensions file:
dirb http://<IP> /usr/share/wordlists/dirb/big.txt -x /usr/share/wordlists/dirb/extensions_common.txt

Wow; dirb found a lot more with these extensions enabled. It’s a good idea to navigate to each of these and get a sense of what they contain.
Portal.php redirects to login.php, which contains a login form. Could this be where our credentials work?
Using the credentials that we found earlier:
Username: R1ckRul3s
Password: Wubbalubbadubdub
We gain access to a Command Panel:
Some experimentation shows that we can use standard Linux commands. Using ls to list the contents of the working directory:
We can see some of the contents that we had already seen earlier, like the assets directory, login.php, portal.php and robots.php. More interesting is the Sup3rS3cretPickl3Ingred.txt.
I tried using cat to print the file contents but received an error that this command had been disabled. We have other options like less, more, head, tail, etc. to try.
Using the less command, I obtained the first ingredient Rick needs:

Answer (Highlight Below):
mr. meeseek hair
Question 2
Whats the second ingredient Rick needs?
There is a clue.txt in the directory that tells us that the next flag is somewhere in the file system.
Knowing that the file name might contain the string ‘ingredient’, I used the find command to search the entire file system:
find / ingredient
Then I was able to use the browser page search feature to jump to a file that seemed highly likely to contain the second ingredient:
Using the less command to grab the contents of the second ingredients file:
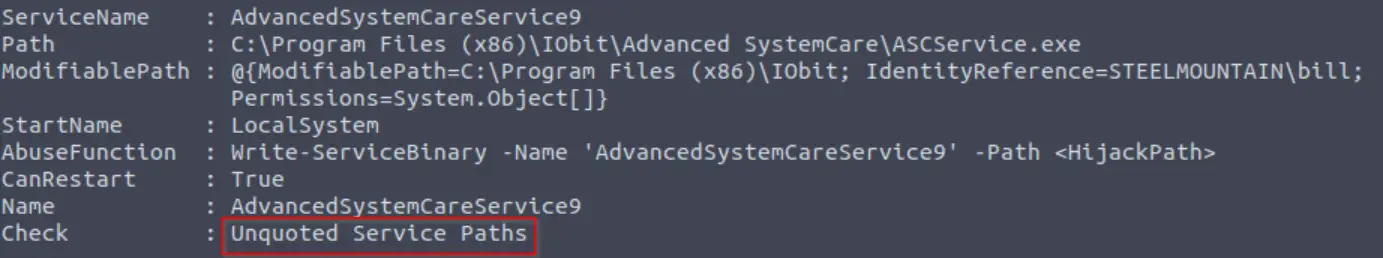
Note that we need to use quotes since ‘second ingredients’ contains two words.
Answer (Highlight Below):
1 jerry tear
Question 3
Whats the final ingredient Rick needs?
I noticed that below the file contents, was a long commented string. Could this be the final ingredient?

Using CyberChef, I found that decoding from Base64 three times resulted in successfully decoding this string:
Rabbit hole! Damn it. Honestly I enjoyed this one. It turned out to indeed be a ‘rabbit hole’, but was fun to pursue without wasting any more time.
So if that wasn’t the way to the third ingredient, what could be?
Well we always want to gain root access and/or access to the /root directory. But attempting to view the contents of /root results in no response. That’s probably because accessing /root typically requires root privileges.
Luckily, there is a command that allows us to elevate privileges to root and enable us to read and access the contents of the /root directory.
That command is sudo (superuser do). In cases like this, it’s always good to try escalating privileges using sudo to access files or directories that our user doesn’t have access to by default.
I used sudo ls to list the contents of root, finding the 3rd.txt file.
Again using sudo, this time combined with less to read the txt file:

Answer (Highlight Below):
fleeb juice
Conclusion
Overall, I really enjoyed this room. Unlike many other beginner rooms on TryHackMe, Pickle Rick offers minimal guidance while still keeping the difficulty level low. The many Rick and Morty elements also added to the style of the CTF as a whole, making it more enjoyable. A huge thanks to tryhackme for putting this room together!