TryHackMe – Pwnkit: CVE-2021-4034 – Walkthrough

This room covers CVE-2021-4034, also known as pwnkit because it exploits a vulnerability found in the ‘Policy Toolkit’, or Polkit package.
Pwnkit is a local privilege escalation (LPE) vulnerability that can easily be exploited to obtain root access on Linux machines. What makes pwnkit so dangerous is that Polkit is installed by default on most Linux distributions; this means that this vulnerability is incredible widespread. The ubiquity of polkit coupled with how easy it is to exploit, makes pwnkit highly dangerous.
This room can be found at: https://tryhackme.com/room/pwnkit
Walkthrough
Task 1 – Info – Introduction and Deploy
Question 1
Deploy the machine by clicking on the green “Deploy” button at the top of this task!
Unlike most rooms on TryHackMe, Pwnkit: CVE-2021-4034 uses a single virtual machine. You don’t need to start the AttackBox or use OpenVPN to access the machine.
Launch the VM (named Pwnkit v1.5.1) using the green ‘Start Machine’ button at the top of Task 1. The terminal interface will open automatically.
Answer:
No answer needed
Task 2 – Tutorial – Background
Pwnkit was discovered by Qualsys; you can read more about it on the Qualsys blog here and/or checkout the technical security advisory here.
According the security advisory:
"This vulnerability is an attacker's dream come true: - pkexec is installed by default on all major Linux distributions (we exploited Ubuntu, Debian, Fedora, CentOS, and other distributions are probably also exploitable); - pkexec is vulnerable since its creation, in May 2009 (commit c8c3d83, "Add a pkexec(1) command"); - any unprivileged local user can exploit this vulnerability to obtain full root privileges; - although this vulnerability is technically a memory corruption, it is exploitable instantly, reliably, in an architecture-independent way; - and it is exploitable even if the polkit daemon itself is not running."
Polkit and pkexec
In order to understand Pwnkit, we need to dig into Polkit and pkexec.
Polkit is a type of privilege authorization software that is used to control system-wide privileges in Unix-like systems. Polkit can be used to determine if a user has the required permissions to perform actions requiring higher-level privileges. This is important because it allows non-privileged processes to communicate with privileged processes.
Since May 2009, polkit has contained a program called pkexec that makes it possible to execute commands with elevated privileges, similar to sudo. Polkit allows for much more granularity than sudo, one of the reasons it is installed by default on most Linux distributions. The pkexec utility is essentially the front-end for polkit, providing an easy way to control privileges.
Normally when we use the pkexec command, we are required to provide a password confirming root access. Without the root password, we cannot use pkexec:
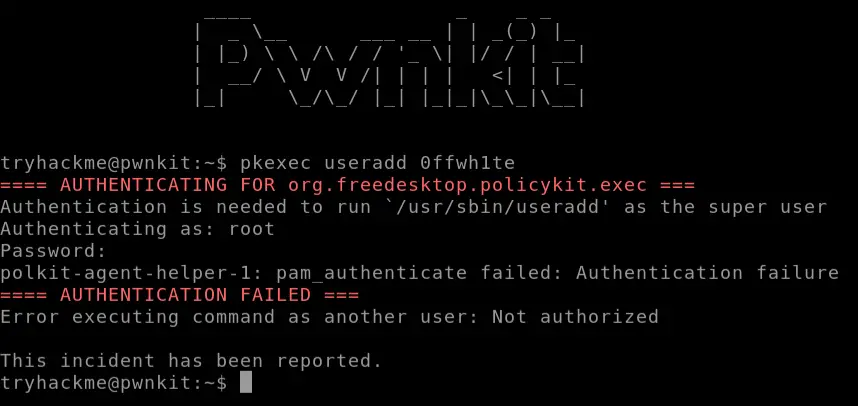
If we fail to provide the correct password, authentication fails and the attempt is logged.
The basis for pwnkit is an ‘out-of-bounds write‘ vulnerability. Line 534 of pkexec contains a for-loop that requires an argument to run. If no argument is given, then the for-loop is bypassed.
Then when pkexec tries to write to the value of the (nonexistent) argument, it instead overwrites the next thing in memory. When the program is called using a C function named execve(), the next thing in memory is the first value in a list of environment variables.
This means that if we pass pkexec a null list of arguments, we can get it to overwrite an environment variable.
Question 1
Is Pwnkit exploitable remotely (Aye/Nay)?
Pwnkit is a local privilege escalation (LPE) vulnerability.
Answer (Highlight Below):
Nay
Question 2
In which Polkit utility does the Pwnkit vulnerability reside?
This utility is the front-end for polkit.
Answer (Highlight Below):
pkexec
Task 3 – Practical – Exploitation
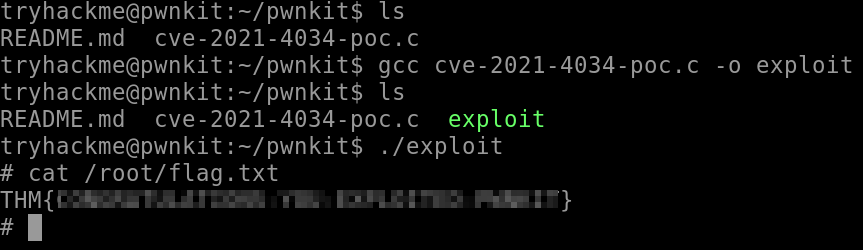
In the VM, navigate into the pwnkit directory. This directory contains an exploit written in C called cve-2021-4034-poc.c. You can check out the GitHub repository here.
We need to compile the exploit using gcc:
gcc cve-2021-4034-poc.c -o exploit
It’s important that we output to a file called exploit or the code won’t work properly.
Then we can run the exploit:
./exploit
Question 1
Read through the cve-2021-4034-poc.c file and try to understand how it works. See if you can match this up with the Qualys security advisory and the explanation given in the previous task!
Answer:
No answer needed
Question 2
Exploit the vulnerability!
What is the flag located at /root/flag.txt?
Answer (Highlight Below):
THM{CONGRATULATIONS-YOU-EXPLOITED-PWNKIT}
Task 4 – Tutorial – Remediations
Qualsys first discovered the vulnerability in November 2021, and quickly coordinated with vendor and open source distributions. There’s a good chance that the Linux distributions on machines that you manage already have a patch available.
Canonical has already released a patch for Ubuntu systems, which can be applied via the apt package manager:
sudo apt update && sudo apt upgrade
For systems without an available patch, the recommended hotfix is to remove the SUID bit from the pkexec binary:
sudo chmod 0755 `which pkexec`
Question 1
Read the remediations task
Answer:
No answer needed
Question 2
Patch the vulnerability on any Linux devices that you manage!
Patch or use the hotfix.
Answer:
No answer needed
Conclusion
This room does a great job of introducing pwnkit (CVE-2021-4034). It gives us a great overview and provides a machine that we can use to exploit this important vulnerability. It’s truly amazing (and kind of scary) just how easy this one is to exploit and gain root!
Overall, I really enjoyed this room. A huge thanks to tryhackme and MuirlandOracle for putting this room together!