TryHackMe – Hashing – Crypto 101 – Walkthrough and Notes
Hashing – Crypto 101 is a TryHackMe room that introduces the concepts of hashes and cracking. Hashing is used for a variety of different things, like protecting passwords and ensuring data integrity. This means that it’s important for security folk to understand how hashing works, what the different popular hashing formats are, and how a hashed password can still be cracked.
The ‘Hashing – Crypto 101’ room on TryHackMe does a good job of introducing these important concepts. It can be found at: https://tryhackme.com/room/hashingcrypto101
About This Walkthrough/Disclaimer:
In this walkthrough I try to provide a unique perspective into the topics covered by the room. Sometimes I will also review a topic that isn’t covered in the TryHackMe room because I feel it may be a useful supplement.
I try to prevent spoilers by requiring a manual action (highlighting) to obtain all solutions. This way you can follow along without being handed the solution if you don’t want it. Always try to work as hard as you can through every problem and only use the solutions as a last resort.
Walkthrough for TryHackMe Hashing – Crypto 101
Task 1 – Key Terms
Question 1
Read the words, and understand the meanings!
Is base64 encryption or encoding?
Answer (Highlight Below):
encoding
Task 2 – What is a hash function?
Question 1
What is the output size in bytes of the MD5 hash function?
Answer (Highlight Below):
16
Question 2
Can you avoid hash collisions? (Yea/Nay)
Answer (Highlight Below):
Nay
Question 3
If you have an 8 bit hash output, how many possible hashes are there?
8 bits => 28 possibilities
Answer (Highlight Below):
256
Task 3 – Uses for hashing
Question 1
Crack the hash “d0199f51d2728db6011945145a1b607a” using the rainbow table manually.
The rainbow table in the description has a matching entry:
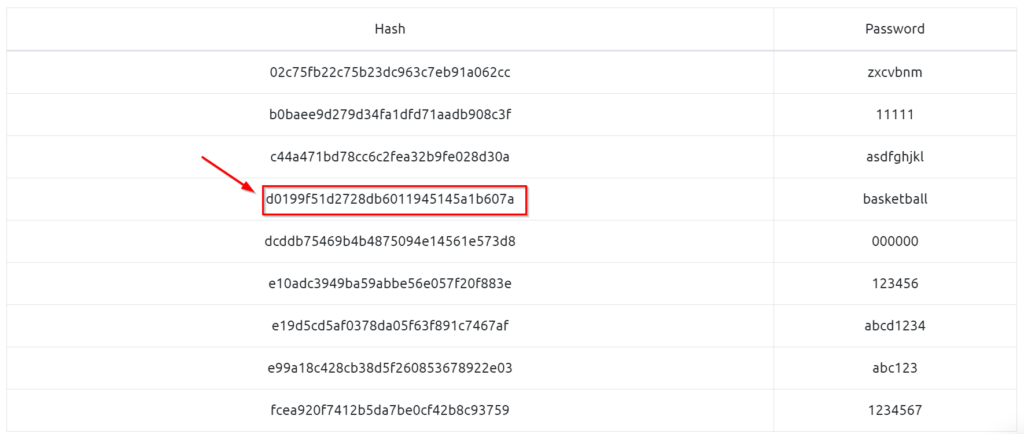
Answer (Highlight Below):
basketball
Question 2
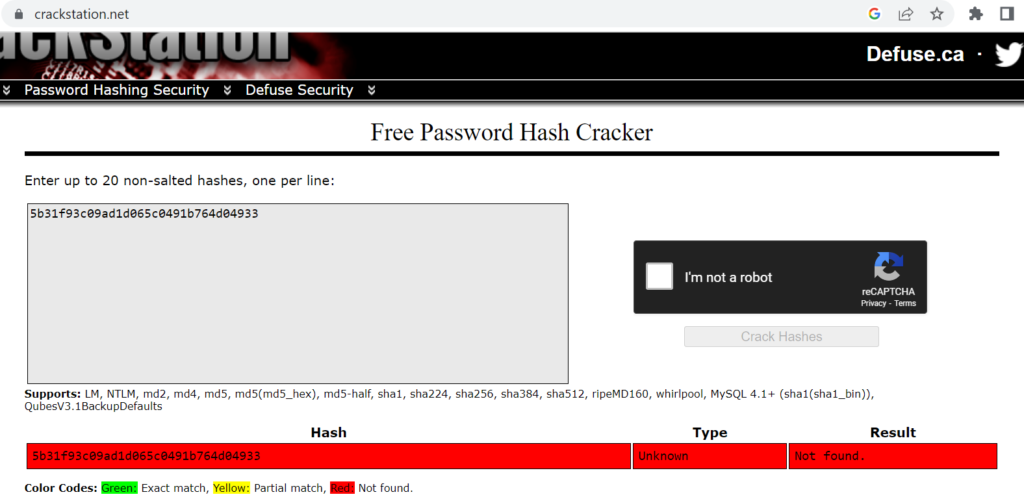
Crack the hash “5b31f93c09ad1d065c0491b764d04933” using online tools
The description provided by TryHackMe mentions crackstation; however I actually found that crackstation was unable to crack it:
However, hashes.com cracked it very quickly and provided me with the algorithm type (md5):
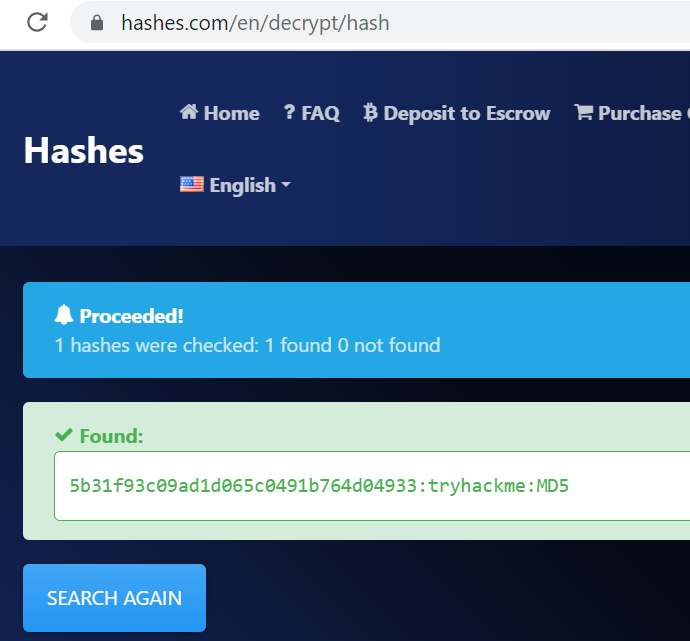
Answer (Highlight Below):
tryhackme
Question 3
Should you encrypt passwords? Yea/Nay
Answer (Highlight Below):
Nay
Task 4 – Recognising password hashes
Question 1
How many rounds does sha512crypt ($6$) use by default?
Answer (Highlight Below):
5000
Question 2
What’s the hashcat example hash (from the website) for Citrix Netscaler hashes?
Answer (Highlight Below):
1765058016a22f1b4e076dccd1c3df4e8e5c0839ccded98ea
Question 3
How long is a Windows NTLM hash, in characters?
Answer (Highlight Below):
32
Task 5 – Password Cracking
Question 1
Crack this hash: $2a$06$7yoU3Ng8dHTXphAg913cyO6Bjs3K5lBnwq5FJyA6d01pMSrddr1ZG
I used hashes.com to crack the hash, which uses bcrypt.
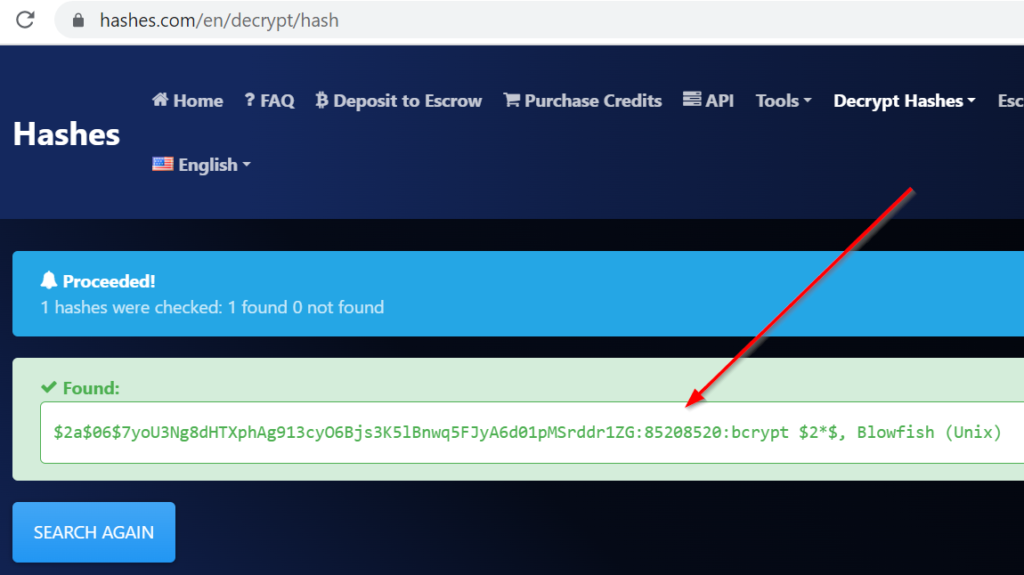
Answer (Highlight Below):
85208520
Question 2
Crack this hash: 9eb7ee7f551d2f0ac684981bd1f1e2fa4a37590199636753efe614d4db30e8e1
Using hashes.com again:
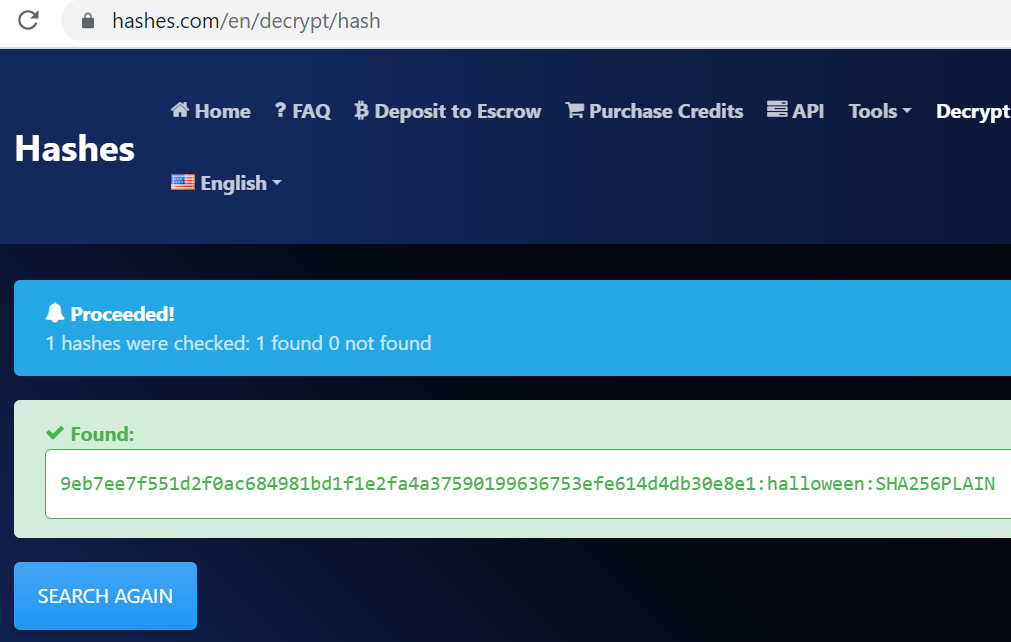
Answer (Highlight Below):
halloween
Question 3
Crack this hash:
$6$GQXVvW4EuM$ehD6jWiMsfNorxy5SINsgdlxmAEl3.yif0/c3NqzGLa0P.S7KRDYjycw5bnYkF5ZtB8wQy8KnskuWQS3Yr1wQ0
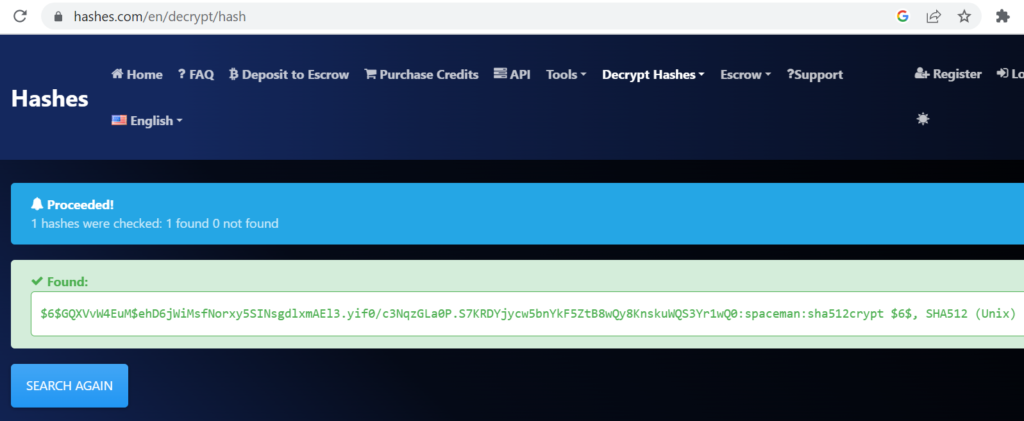
Answer (Highlight Below):
spaceman
Question 4
Bored of this yet? Crack this hash:
b6b0d451bbf6fed658659a9e7e5598fe
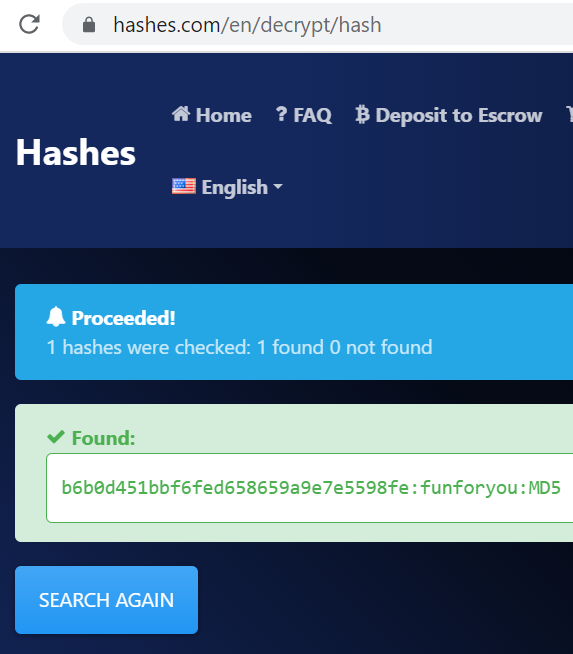
Answer (Highlight Below):
funforyou
Task 6 – Hashing for integrity checking
Question 1
What’s the SHA1 sum for the amd64 Kali 2019.4 ISO? http://old.kali.org/kali-images/kali-2019.4/
After navigating to the linked page, click on SHA1SUMS:
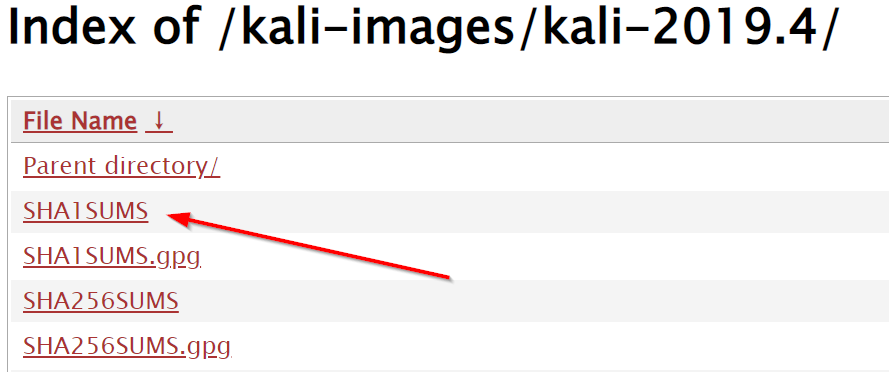
Download this and look at the contents in a text editor of your choosing. Find the entry that corresponds with amd64 Kali 2019.4:
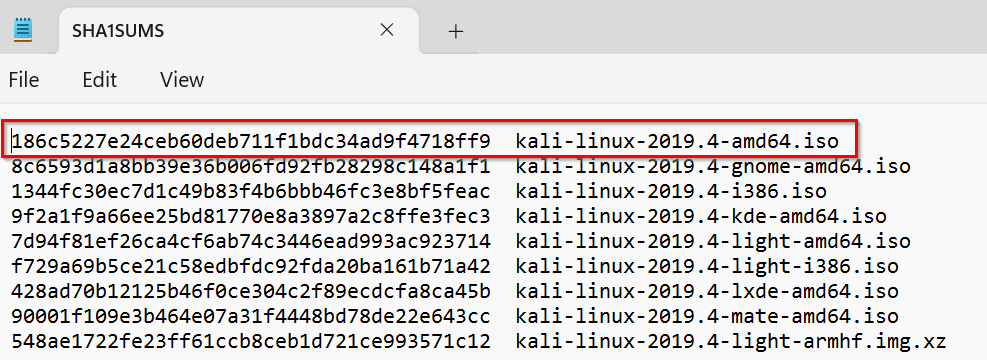
Answer (Highlight Below):
186c5227e24ceb60deb711f1bdc34ad9f4718ff9
Question 2
What’s the hashcat mode number for HMAC-SHA512 (key = $pass)?
Go to https://hashcat.net/wiki/doku.php?id=example_hashes
Find the entry for HMAC-SHA512:

Answer (Highlight Below):
1750
Conclusion
I enjoyed Hashing – Crypto 101 and thought that it did a nice job of introducing basic concepts related to the topic of hashing. A hearty thanks to tryhackme and NinjaJc01 for this one!