TryHackMe – Advent of Cyber 3 – Day 1 – Walkthrough
Introduction to IDOR vulnerabilities
This Task (Day 1) is about IDOR vulnerabilities. IDOR stands for Insecure Direct Object Reference, and is a vulnerability that allows unauthorized access to information.
The first important thing to learn is what a query component is.
You’ve probably seen URLs that contain query components before, such as in this example:
https://example.com/products/product?num=42
In this example, the query component is ‘num=42′ and we can see that the product number is ’42’. The query component has two parts: a parameter and a value. In this example, ‘num’ is the parameter and ’42’ is its’ value.
If we use our browser to change the number, we might be able to navigate to a different product without using links on a website. We might even be able to access the product page for something that we aren’t authorized to see.
This type of vulnerability is an IDOR (Insecure Direct Object Reference) because we are able to directly reference an object. In this case, the object is the web page for a product we aren’t supposed to be able to access.
In the Day 1 challenge, we are basically asked to do two things:
- Find a page with a potential IDOR vulnerability by looking at the URLs for each page.
- Exploit the IDOR by manipulating the query component.
If this sounds confusing, have no fear! It’s way easier than it sounds.
Day 1 Walkthrough
Start by clicking the green ‘View Site’ button on the top right side of the task.
This will open a mock website on the right side of your screen.
Look at the menu at the top of the page. There are links to four web pages: ‘Completed Orders’, ‘Builds’, ‘Inventory’, and ‘Your Activity’.
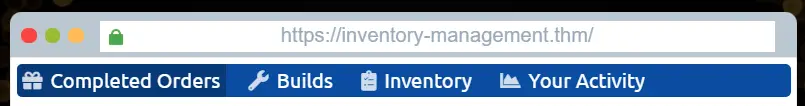
Navigate to each page and observe the URL. You’ll notice that the ‘Your Activity’ page has a URL of:
https://inventory-management.thm/activity?user_id=11
We can see that the URL contains a query component of ‘user_id=11‘.
How can we hack this?
Let’s start by changing the value of the parameter ‘user_id’. Start by changing the value to ‘1’:
https://inventory-management.thm/activity/user_id=1
Question 1
After finding Santa’s account, what is their position in the company?
It turns out that the user with an ID of ‘1’ is Santa himself!
In addition the ID number, we are also given the name corresponding the ID number (Santa), their position in the company, and any recent activity.
Answer: (highlight the box below)
The Boss!
Question 2
After finding McStocker’s account, what is their position in the company?
Continue trying different values for the ‘user_id’ parameter in the URL, incrementing (increasing) the value by ‘1’ each time.
We quickly find that ‘user_id’ number ‘3’ corresponds to McStocker’s account. We can see their position and also find that they have had no recent activity.
Answer: (highlight the box below)
Build Manager
Question 3
After finding the account responsible for tampering, what is their position in the company?
We want to see if we can find the user who has been tampering with our inventory.
Continue to increment the value of ‘user_id’ by 1 until you find the culprit!
After a few moments, you should have found that the ‘user_id’ of ‘9’ is the Grinch’s account!
We can see the Grinch’s name, position, and the changes made by the rascal.
Answer: (highlight the box below)
Mischief Manager
Question 4
What is the received flag when McSkidy fixes the Inventory Management System?
Below the Grinch’s profile information, we can see the recent changes that he’s made. It looks like he’s made changes to a number of SKUs in the inventory.
Revert the changes by clicking the ‘Revert’ button to the right of each change.
Once we revert all of the changes, we should see a popup giving us the flag to answer the question.
Answer: (highlight the box below)
THM{AOC_IDOR_2B34BHI3}