Day 19 – Something Phishy is Going On
You’re probably familiar with Phishing attacks because they are so common that most companies train their employees to recognize them. Phishing attacks use email to send potential victims malicious attachments or links.
Basically, you should severely limit your interaction with email based on your perception of how trustworthy it is and never click a link or download an attachment without being 100% sure it is safe.
Deploy the virtual machine for Day 19 using the green ‘Start Machine’ button.
Open Thunderbird mail:
Question 1
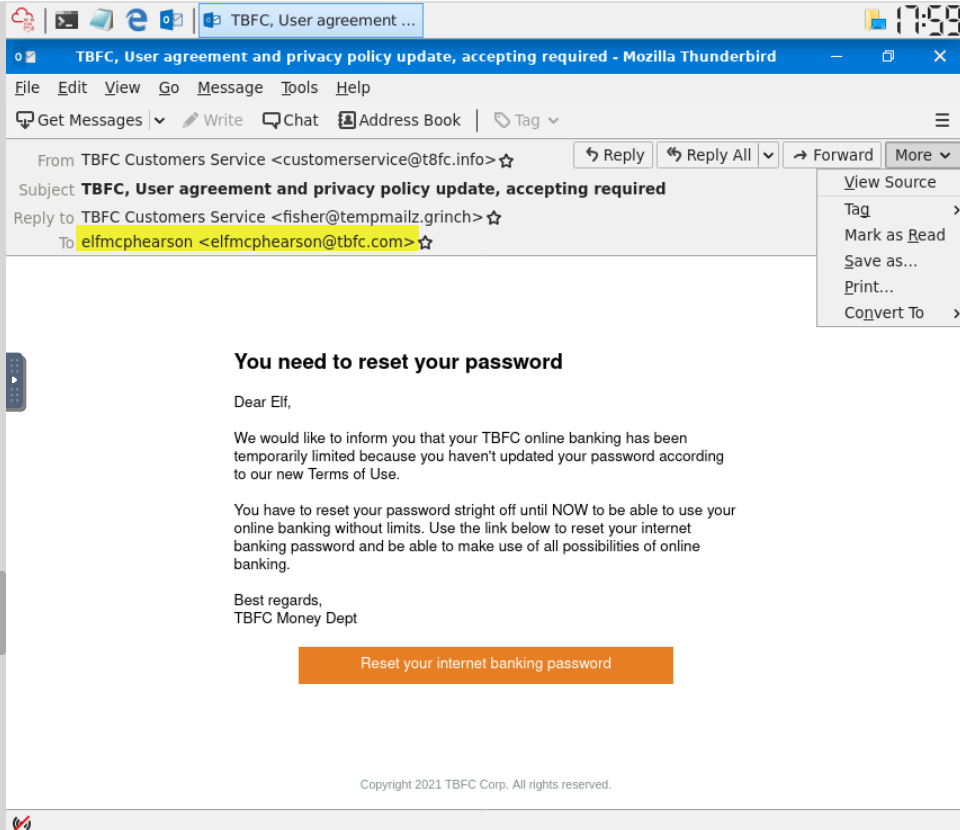
Who was the email sent to? (Answer is the email address)
As soon as we open Thunderbird mail, we are greeted with an email claiming to be our bank and inviting us to change our password using a linked URL. We can see who the email was sent to at the top, under ‘To’:
Answer:
(Highlight below to see answer):
Question 2
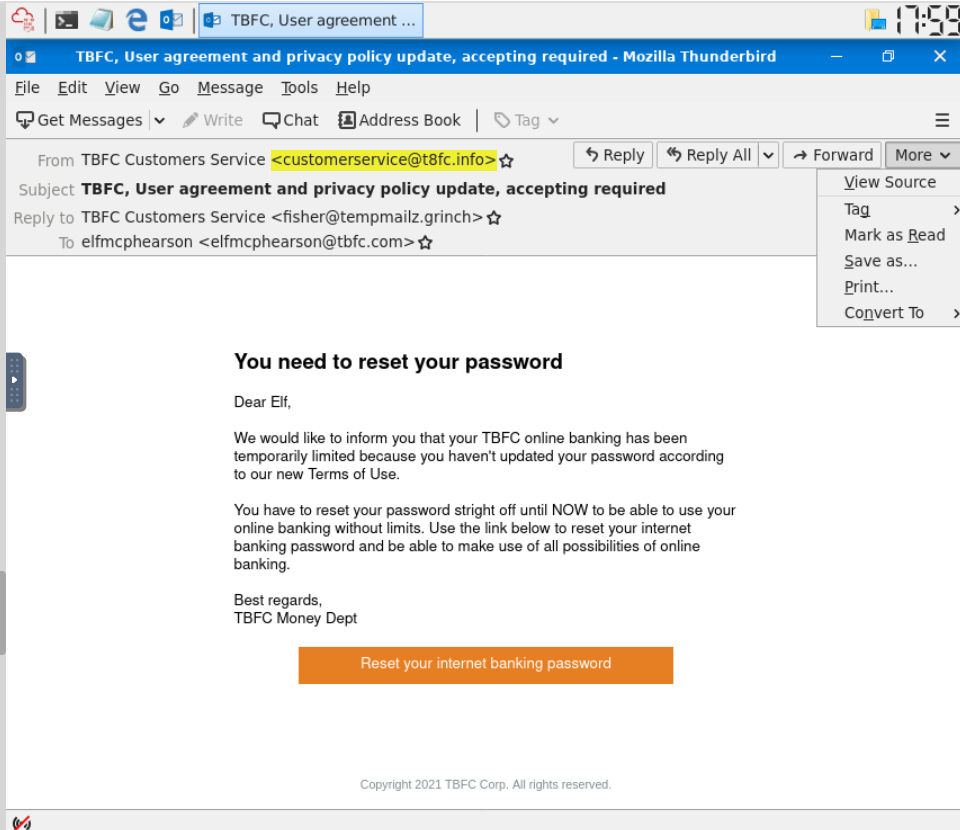
Phishing emails use similar domains of their targets to increase the likelihood the recipient will be tricked into interacting with the email. Who does it say the email was from? (Answer is the email address)
Let’s look at the from email address, ‘[email protected]’, looks legitimate at first glance because it is so similar to TBFC, the acronym for the bank.
Answer:
(Highlight below to see answer):
Question 3
Sometimes phishing emails have a different reply-to email address. If this email was replied to, what email address will receive the email response?
This can also be found at the top of the page, under ‘Reply To’:
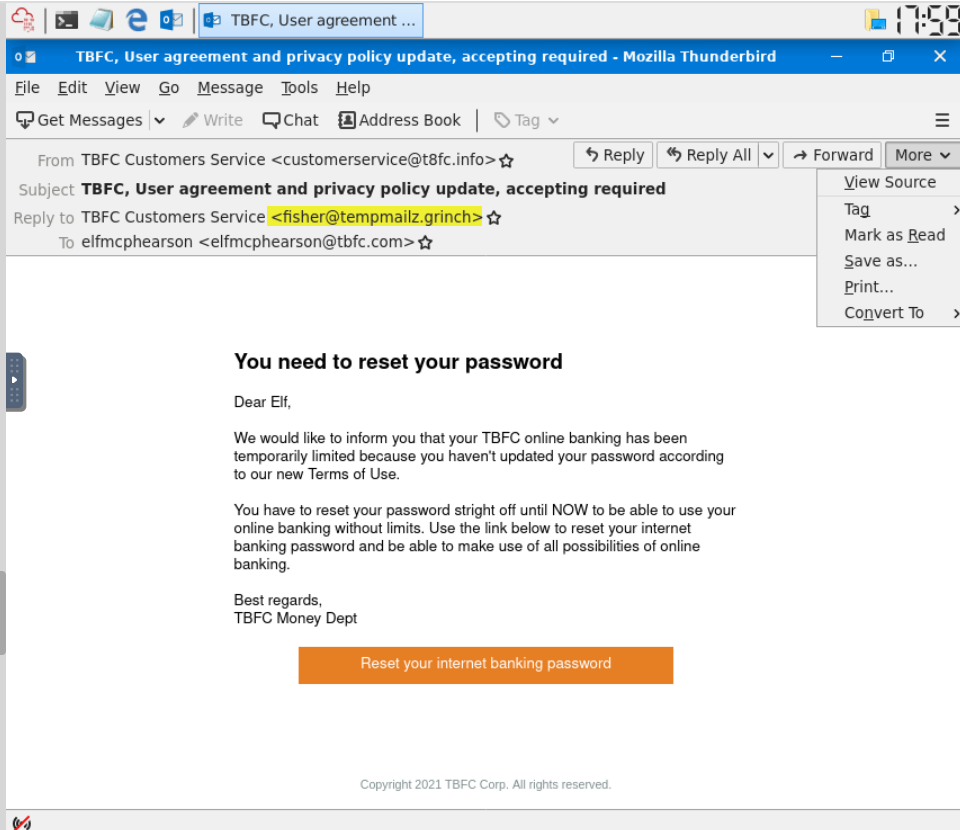
This one doesn’t sound very legitimate.
Answer:
(Highlight below to see answer):
Question 4
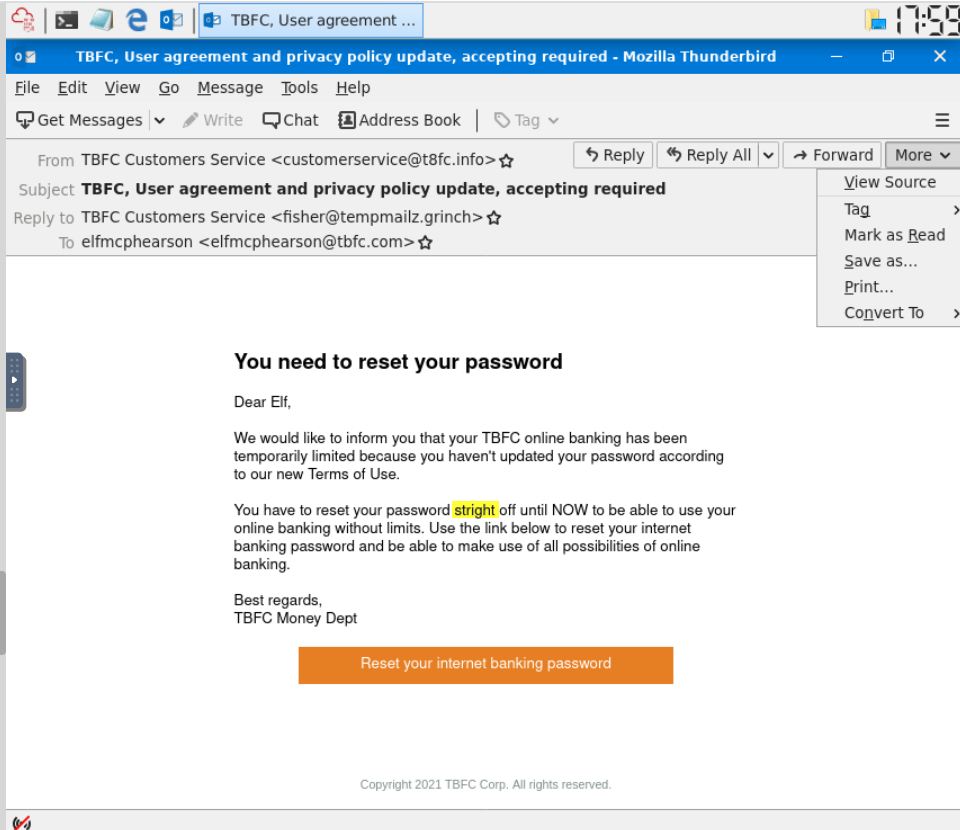
Less sophisticated phishing emails will have typos. What is the misspelled word?
While reading the email I noticed a typo (highlighted in the image above) and some questionable grammar.
Answer:
(Highlight below to see answer):
stright
Question 5
The email contains a link that will redirect the recipient to a fraudulent website in an effort to collect credentials. What is the link to the credential harvesting website?
We can obtain the link simply by hovering over it and looking for the URL at the bottom of the page:
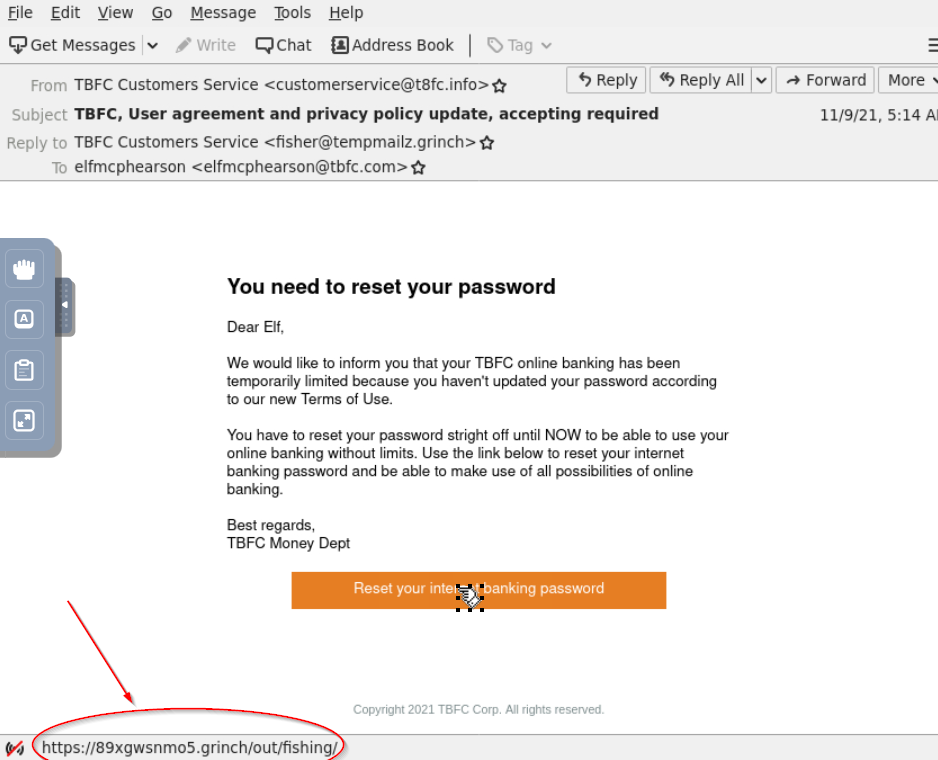
Or you can right-click on the button, select ‘Copy Link Location’, and then paste anywhere to obtain the link.
Answer:
(Highlight below to see answer):
https://89xgwsnmo5.grinch/out/fishing/
Question 6
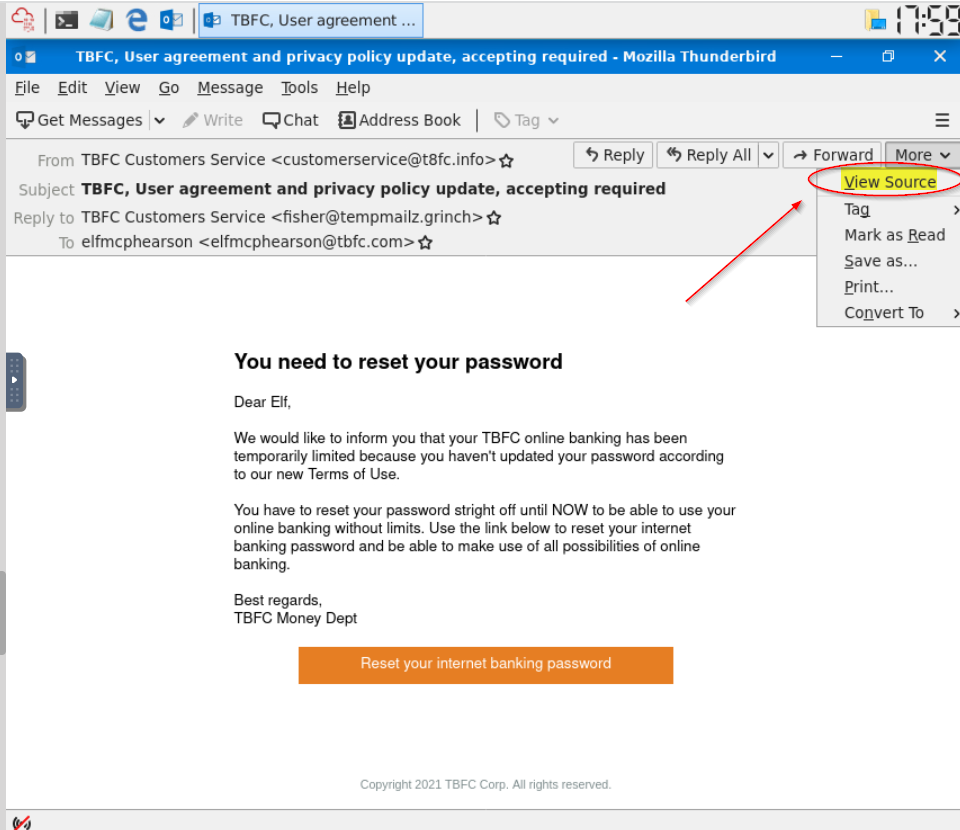
View the email source code. There is an unusual email header. What is the header and its value?
You can view the source via the ‘More’ menu on the top-right:
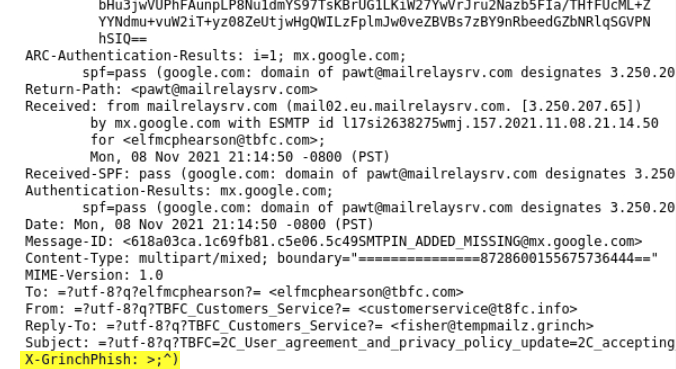
Scan through the code and see if you can find something…THAT looks interesting…
Answer:
(Highlight below to see answer):
X-GrinchPhish: >;^)
Question 7
You received other reports of phishing attempts from other colleagues. Some of the other emails contained attachments. Open attachment.txt. What is the name of the attachment?
Let’s move over to the command line to complete the next few tasks. Open the terminal emulator shortcut at the top of the screen:
We can see that we are signed in as ‘ubuntu’ and the working directory is ubuntu’s home directory, /home/ubuntu.
We need to navigate to the directory containing the email files, so first we change directories to the Desktop and then into the directory ‘Email Artifacts’.
Now we can use the ‘cat’ or ‘less’ command to read attachment.txt:
less attachment.txt
Look for the PDF file referenced as ‘name’:
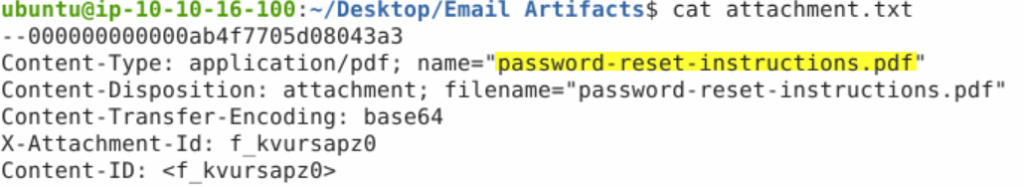
Answer:
(Highlight below to see answer):
password-reset-instructions.pdf
Question 8
What is the flag in the PDF file?
There are probably a few ways to complete this. If you follow the hints provided by THM, it is pretty clear that we need to decode attachment-base-64-only.txt. But how would we know that?
Well, if we load the attachment-bast-64.txt file into CyberChef, we can use the ‘From Base 64’ option to determine that it should decode into a pdf. Then we can use the command given in the TryHackMe writeup:
cat attachment-base64-only.txt | base64 -d > file.pdf
This will decode the file into ‘file.pdf’ in the same directory (/home/ubuntu/Desktop/Email Artifacts). Navigate to the file on the GUI and open it:
You should see the following document, and have found the flag!
Answer:
(Highlight below to see answer):
THM{A0C_Thr33_Ph1sh1ng_An4lys!s}