Day 21 – Needles in Computer Stacks
Today’s tasks cover YARA, which is a pattern matching tool.
The context provided is that Yara is often used to identify malware using pattern recognition.
There are a couple of things going on when using Yara. First, we need a file containing a Yara rule. Second, we reference the rule and a file that we want the rule to work on using the Yara command:
yara [options] rule_file [target]
To complete the activities, we’ll start by starting the virtual machine by clicking the green ‘Start Machine’ button at the top of the Day 21 description. Wait for it boot.
Open the SciTE text editor using the search feature (click the TryHackMe logo at the top left corner of the GUI).
Then paste in the code for the Yara rule that we are given in the TryHackMe writeup:
rule eicaryara {
meta:
author="tryhackme"
description="eicar string"
strings:
$a="X5O"
$b="EICAR"
$c="ANTIVIRUS"
$d="TEST"
condition:
$a and $b and $c and $d
}This rule contains three elements: meta, strings, and conditions.
Meta contains metadata for the rule. Strings contains four different character strings that we want Yara to look for. Condition tells Yara more specifically what to look for regarding these strings, using Boolean conditions like ‘and’, ‘or’, ‘not’.
Ultimately what this rule is saying is “look for the strings ‘X5O’, and ‘EICAR’, and ‘ANTIVIRUS’, and ‘TEST'”. If all four strings are found, Yara will return a ‘hit’; otherwise, it will return a ‘miss’.
Save this file to the Desktop as ‘eicaryara’.
Open a terminal and navigate to the Desktop folder; run yara using eicaryara against ‘testfile’ on the desktop:
yara eicaryara testfile
If the rule is a ‘hit’, then it will return the following:

If the rule is a ‘miss’, then it wouldn’t return anything.
Why does the rule work? Again, it is looking for the strings Ultimately what this rule is saying is “look for the strings ‘X5O’, ‘EICAR’, ‘ANTIVIRUS’, ‘TEST'”. It must be finding all four strings in testfile. Since testfile is short, we can quickly see this using the cat command:

Note that all four strings can be seen in testfile.
Question 1
We changed the text in the string $a as shown in the eicaryara rule we wrote, from X5O to X50, that is, we replaced the letter O with the number 0. The condition for the Yara rule is $a and $b and $c and $d. If we are to only make a change to the first boolean operator in this condition, what boolean operator shall we replace the ‘and’ with, in order for the rule to still hit the file?
Let’s change our code so that we are now looking for ‘X50’ (with a zero) instead of ‘X5O’ (with the letter ‘O’):
rule eicaryara {
meta:
author="tryhackme"
description="eicar string"
strings:
$a="X50"
$b="EICAR"
$c="ANTIVIRUS"
$d="TEST"
condition:
$a and $b and $c and $d
}If we save the file and run yara again, this time we will get a miss!

Note the lack of output, signifying a ‘miss’. Why did it miss? Because there is no ‘X50’ (with a zero) in testfile, and it is required based on the boolean ‘and’ condition. If we change this to an ‘or’ condition, the rule will no longer require the first string to be found!
Answer:
(Highlight below to see answer):
or
Question 2
What option is used in the Yara command in order to list down the metadata of the rules that are a hit to a file?
This option is covered in the writeup on TryHackMe, but we can also use the ‘yara –help’ command to pull up a list of options:
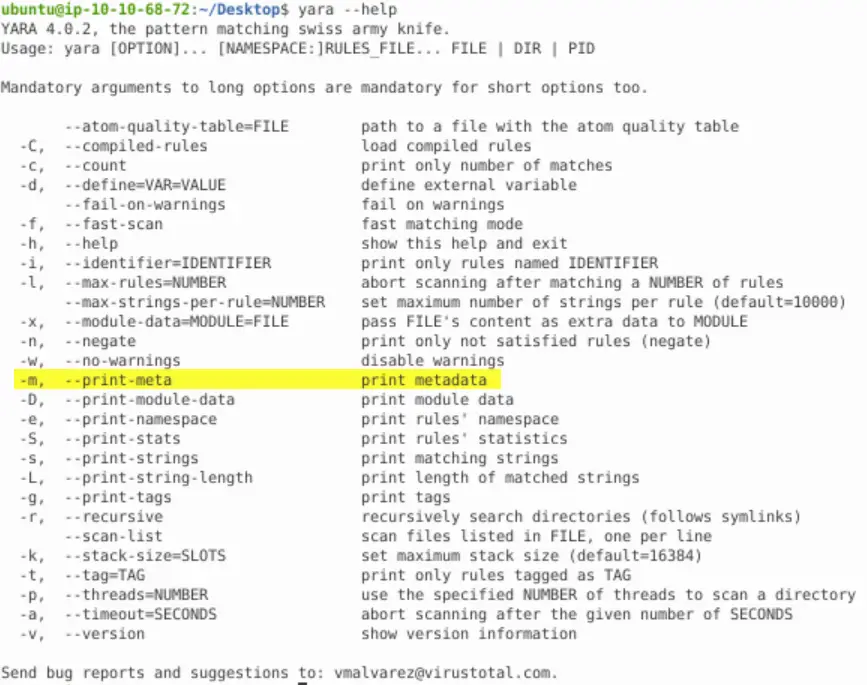
Alternately we can also do something like ‘yara –help | grep meta’, which will pull out only the line with the meta option.
Answer:
(Highlight below to see answer):
-m
Question 3
What section contains information about the author of the Yara rule?
Run the meta command using the ‘-m’ option from the last question. This tells yara to print the metadata for the rule, but note that it will only work if the rule produces a ‘hit’.

This gives us two pieces of information; author and description. This is in accordance with the ‘meta’ section from the rule (the code we saw earlier).
Answer:
(Highlight below to see answer):
metadata
Question 4
What option is used to print only rules that did not hit?
Our first instinct when trying to figure out an option for a command like yara, should be the –help or man page.
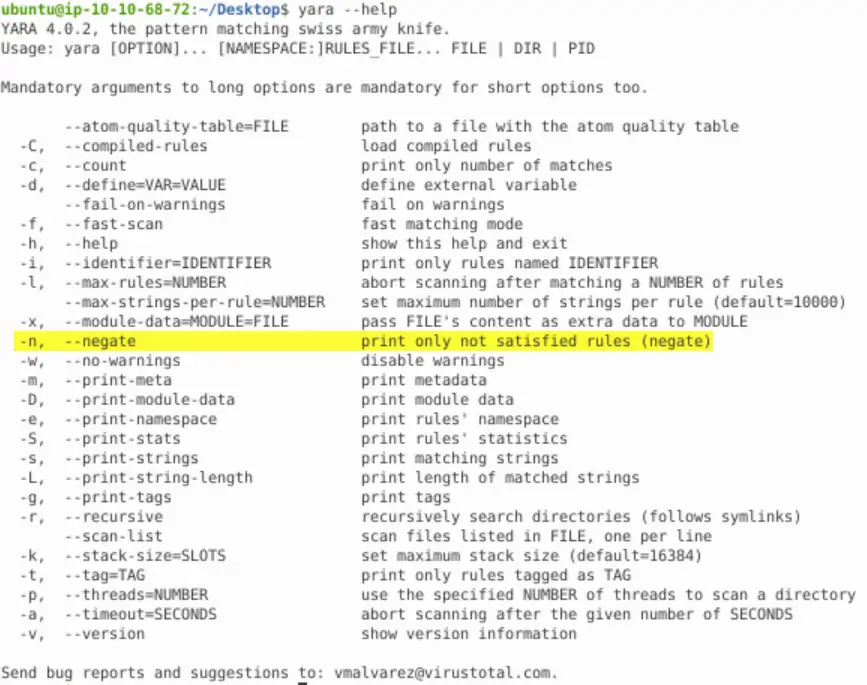
We can read it directly or search through it by piping it into grep. In this case, I used grep to look for the string ‘not’:

Answer:
(Highlight below to see answer):
-n
Question 5
Change the Yara rule value for the $a string to X50. Rerun the command, but this time with the -c option. What is the result?
Return to the eicaryara file, and change the string $a from ‘X5O’ (with the letter ‘O’) to ‘X50’ (with a zer) as we saw in the first question:
rule eicaryara {
meta:
author="tryhackme"
description="eicar string"
strings:
$a="X50"
$b="EICAR"
$c="ANTIVIRUS"
$d="TEST"
condition:
$a and $b and $c and $d
}Note that under ‘condition’, all four boolean expressions are ‘and’, so that all four strings are required. This returns a miss. Run the command with the -c option as given in the question:

It returns a ‘0’ (zero), which means ‘false’ or ‘miss’. A ‘hit’ would result in a ‘1’, or ‘true’.
Answer:
(Highlight below to see answer):
0