Day 4 – Santa’s Running Behind
Today is all about using a program called Burp Suite to crack our way into Santa’s schedule.
Burp Suite is an incredibly useful, common, and (relatively) easy to use tool. It can be used to modify things like HTTP requests as well as cookies. For example, you can use it to automate the manual cookie manipulation process we covered in Day 3.
The write-up for this task covers basic instructions for using Burp Suite, as well as the topics of authentication, authorization, and fuzzing. Briefly:
Authentication is the process of validating a user’s identity. This is commonly done with a username, and password, with many sensitive applications using additional security measures such as multi-factor authentication.
Authorization is setting permissions for users. Different users will have different resources that they are authorized to access. For example, a guest will be authorized access only to a bare minimum number of resources, a registered user might have more access (depending on the application), and an administrator would have authorization to access all system resources.
Fuzzing is the act of using automation to test a web application’s security. Today, we’ll be fuzzing a web app by using Burp Suite to determine Santa’s password and gain access to his schedule.
Question 1
Access the login form at http://<IP ADDRESS>
Launch the AttackBox and deployable machine (target machine). As a reminder, the AttackBox is launched using the blue button at the top of the web page, and the target machine is launched using the green button at the top of the Day 4 writeup.
Using the AttackBox, launch Firefox and navigate to the IP address of the target machine. For example, if your target machine’s IP address is 10.10.10.10, you would navigate to:
http://10.10.10.10
You should see a login form:
Answer:
No answer needed
Question 2
Configure Burp Suite & Firefox, submit some dummy credentials and intercept the request. Use intruder to attack the login form.
Configuring Burp Suite: Open up Burp Suite. You’ll have to go through two pop-up messages; click ‘Next’ and ‘Start Burp’ to access the main dashboard. Your proxy intercept should already be on but you can confirm this by navigating to the ‘Proxy’ tab.
Configuring Firefox: Go back to Firefox; look for the FoxyProxy icon to the right of the browser navigation bar. Click the icon and select ‘Burp’ as shown in the image below:
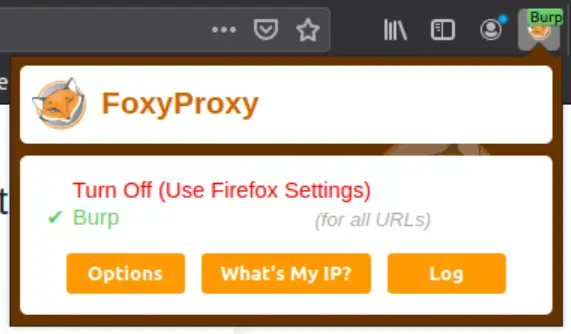
What this does is send your HTTP requests directly to Burp Suite instead of the target machine. By having Burp Suite’s intercept turned ‘on’, Burp will capture your HTTP requests. If turned off, Burp will forward your HTTP requests to the target machine. It enables us to allow normal traffic to flow without closing the Burp Suite application.
The write-up tells us that the username we are trying to access is ‘santa’, so enter this into the login form. Enter a dummy password (I used ‘santaspassword’) and click ‘Login’:
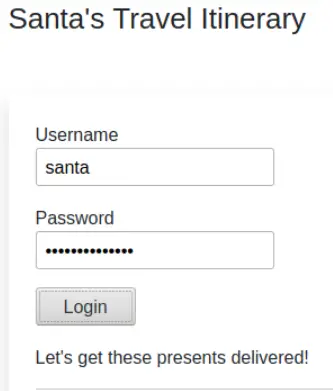
You’ll notice that the app doesn’t try to log us in like it normally would- instead the browser gets hung up. That’s because our POST request is waiting in Burp Suite for us.
Go back to Burp Suite and navigate to the ‘Proxy’ tab if you aren’t already there. You should see the POST request. Right-click anywhere on the request and select ‘Send to Intruder’. Navigate to the ‘Intruder’ tab.
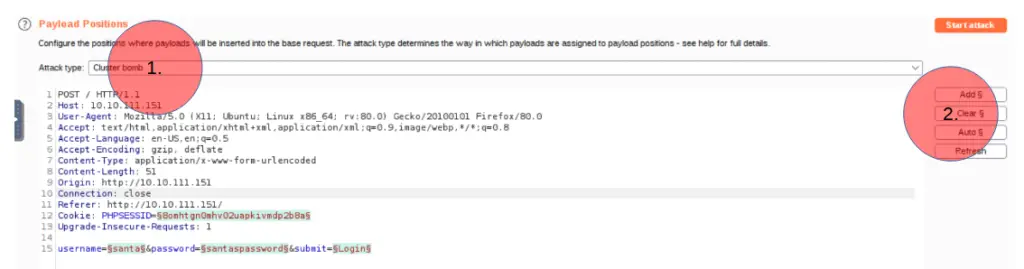
When you open the ‘Intruder’ tab, you will be in the ‘Target’ subtab; navigate to the ‘Positions’ subtab. The ‘Positions’ tab is where we can choose the positions where our payloads (trial passwords) will be tried:
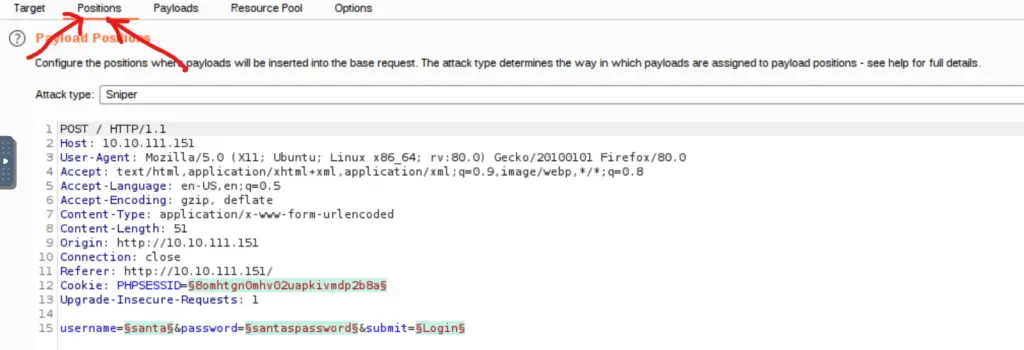
You’ll want to do the following steps (use the image below as a reference):
First, select the ‘Cluster Bomb’ attack type from the dropdown menu at the top.
Next, clear the existing selected positions by pressing the ‘Clear’ button.
Now we’ll need to set the positions that we want Burp Suite to fuzz:
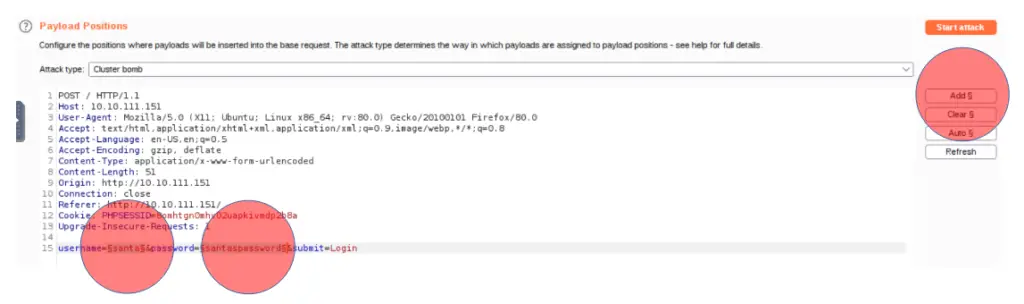
At the bottom of the request, you should see a line that contains the original username and password that we entered earlier into the form. Highlight the username ‘santa’, and click on the ‘Add’ button on the right side. Do the same for the password. Both should now be highlighted and surrounded by brackets as shown above.
Next, navigate to the ‘Payloads’ subtab. The first payload set will correspond to the username, and the second will correspond to the password.
Since we know the username is ‘santa’, we can just enter it:
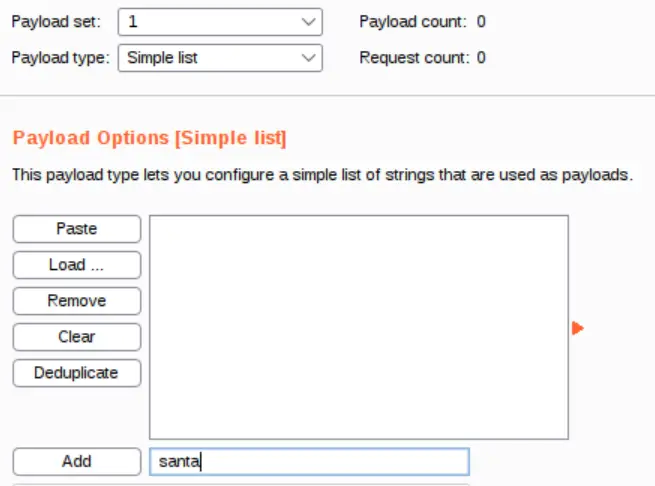
Click the add button and the list will now contain Santa:
Select the second payload set as shown:
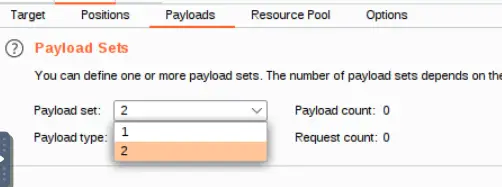
Now, load the password list at /root/Rooms/AoC3/Day4/passwords.txt:
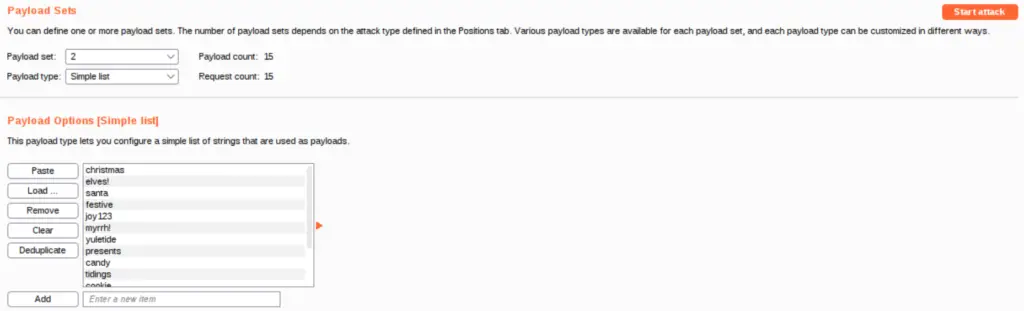
Make sure you’re loading the list into Payload set 2, or the attack won’t work.
Click the orange ‘Start Attack’ button. Burp Suite will start trying combinations of username (only Santa, in this case) and password (the list that we loaded). You should see a new window pop up with details of the attack:
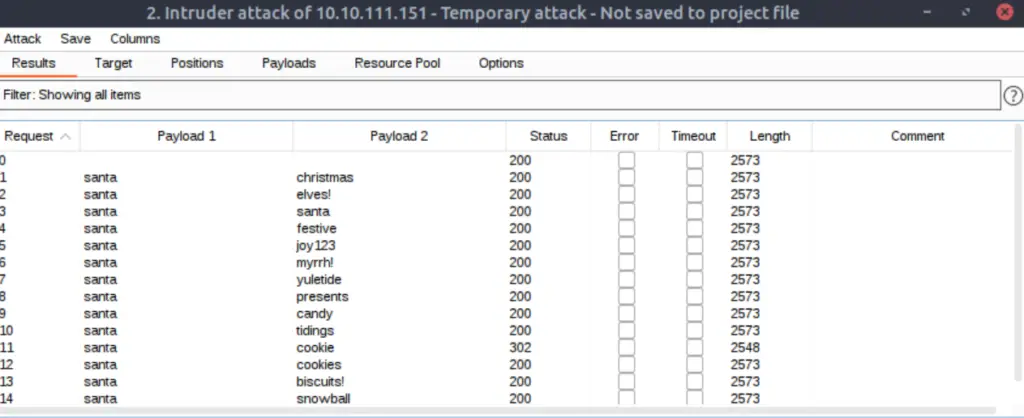
Click on the word ‘Length’ in order to sort by the length of the response. This will help us identify the right password, as the response will be different than for all of the incorrect passwords (i.e. the length will be special). Note that it will also have a different status (302 instead of 200).
Answer:
No answer needed
Question 3
What valid password can you use to access the “santa” account?
If you followed the instructions above, the correct password will be the text in the ‘Payload 2’ column that corresponds to the response with a shorter length and 302 status.
Answer:
(Highlight below to see answer):
cookie
Question 4
What is the flag in Santa’s itinerary?
Go back to Firefox and the login page. Turn the proxy off using Foxy Proxy, and enter the username ‘santa’ and password that we just found.
You should see the flag at the top of the page.
Answer:
(Highlight below to see answer):
THM{SANTA_DELIVERS}