Day 9 – Where is All This Data Going?
Day 9 is all about WireShark, a popular packet analysis tool that comes installed on Kali Linux (i.e. the AttackBox).
Start the AttackBox and open Wireshark via the top menu: Applications -> Internet -> Wireshark:
Once in Wireshark, open the /root/Rooms/AoC3/Day9/AoC3.pcap file. Alternately, you can do this via the command line using:
sudo wireshark /root/Rooms/AoC3/Day9/AoC3.pcap
Question 1
In the HTTP #1 – GET requests section, which directory is found on the web server?
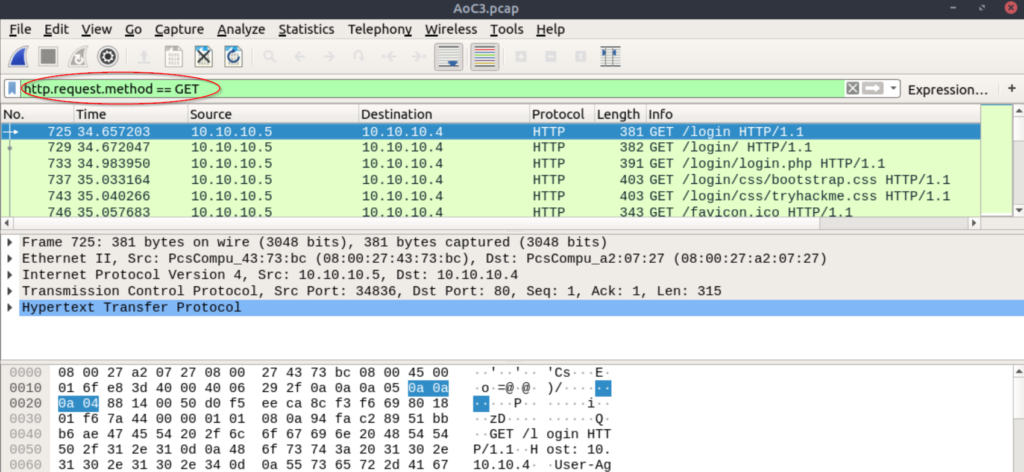
There are many packets, so we want to apply filters so that we have less information to sort through.
Enter ‘http.request.method == GET’ to apply a filter that shows only http requests that use the GET method:
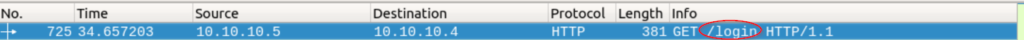
If we look at the ‘Info’, we can see a directory that this GET request is trying to access:
Answer:
(Highlight below to see answer):
login
Question 2
What is the username and password used in the login page in the HTTP #2 – POST section?
Apply a filter that selects for POST requests:
‘http.request.method == POST’
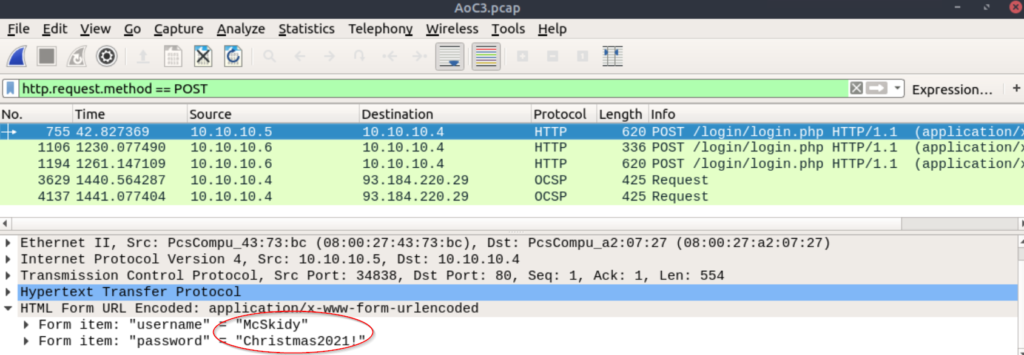
Select the first request and open the ‘HTML Form URL Encoded’ section. You should see the credentials:
Answer:
(Highlight below to see answer):
McSkidy:Christmas2021!
Question 3
What is the User-Agent’s name that has been sent in HTTP #2 – POST section?
Within the same packet, expand the section called ‘Hypertext Transfer Protocol’. The name/flag that we need to answer this question is towards the top:
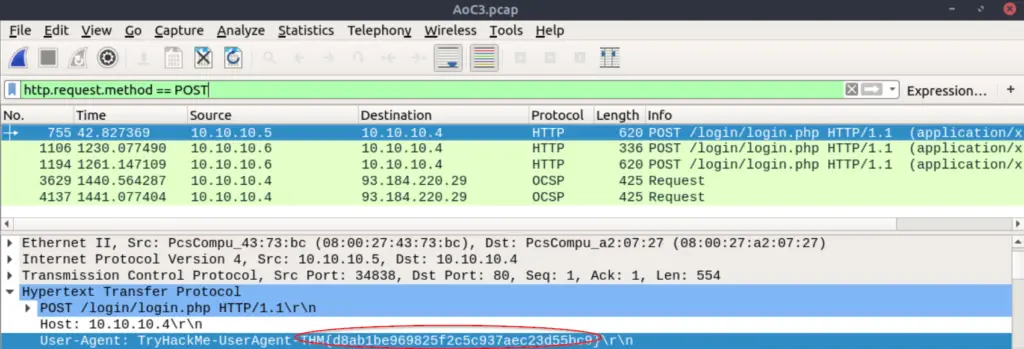
Instead of copying this down manually, you can right click on it and select ‘Follow -> HTTP Stream’:
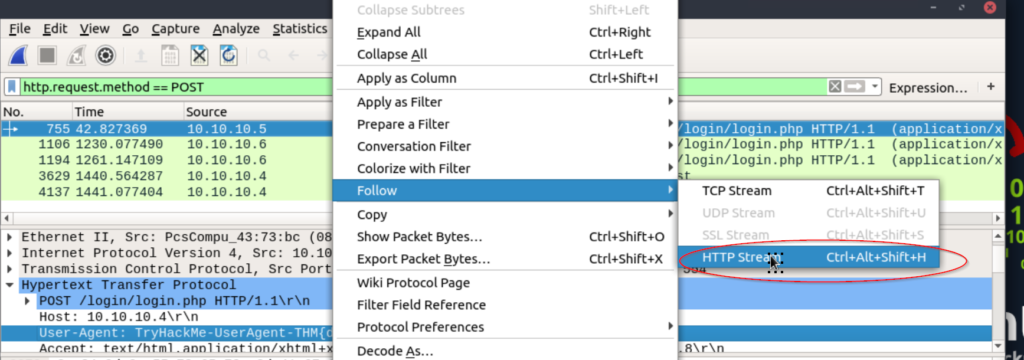
This will open a new window where the User-Agent can be copied.
Answer:
(Highlight below to see answer):
TryHackMe-UserAgent-THM{d8ab1be969825f2c5c937aec23d55bc9}
Question 4
In the DNS section, there is a TXT DNS query. What is the flag in the message of that DNS query?
Enter the filter ‘dns.txt’ to pull up the only packet that references a .txt file:
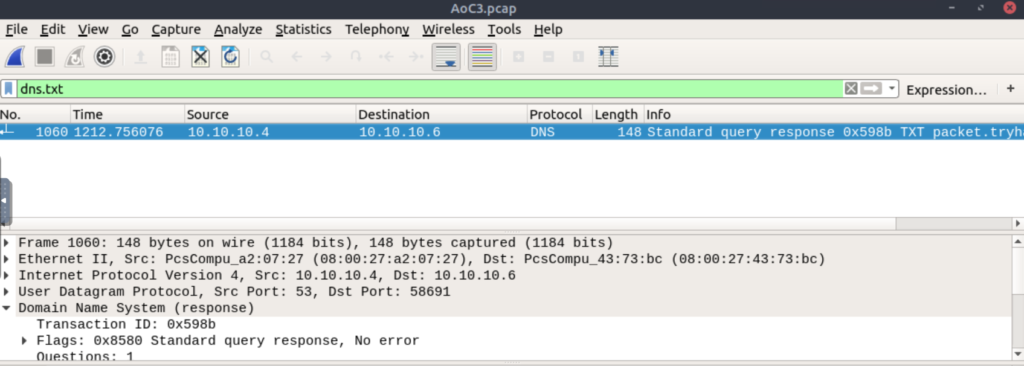
You’ll notice that although there is a ‘flags’ section under ‘Domain Name System (response)’, the contents of the .txt file don’t seem to be accessible. This is because FTP uses two connections. The first, called the control connection, is used to execute FTP commands. Then when we want to transfer a file, a second connection is opened to perform the actual file transfer. This means that the control connection won’t get bogged down by ongoing file transfers.
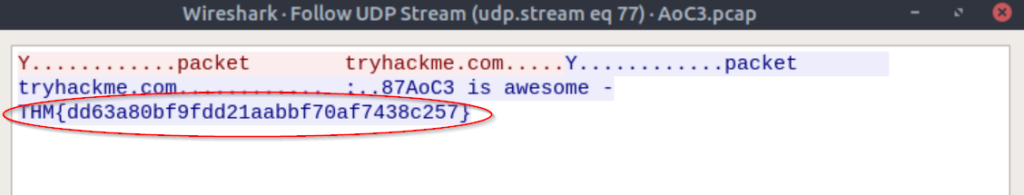
Right click and select ‘Follow -> UDP Stream’:
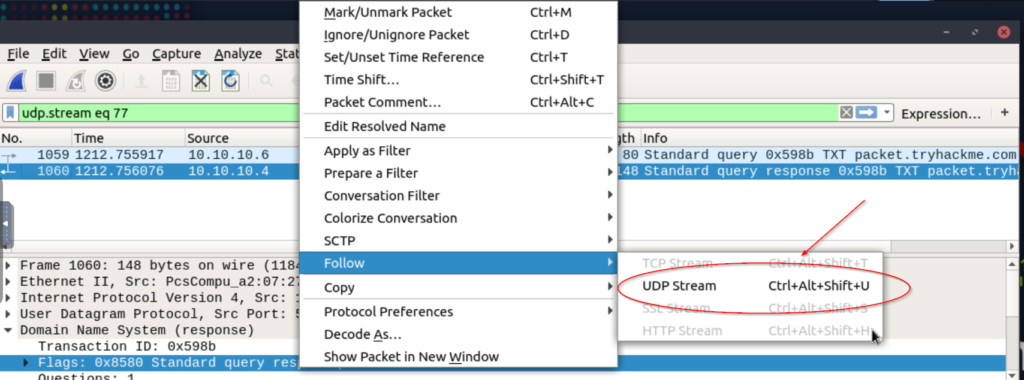
A new window should open that contains the contents of the file, including the flag:
Answer:
(Highlight below to see answer):
THM{dd63a80bf9fdd21aabbf70af7438c257}
Question 5
In the FTP section, what is the FTP login password?
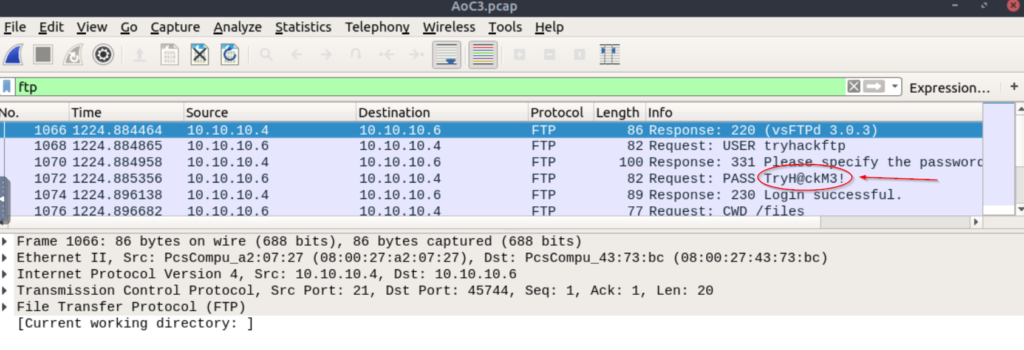
Use the filter ‘FTP’. The following packets should be in the results, and we can see the FTP credentials without going any further:
Answer:
(Highlight below to see answer):
TryH@ckM3!
Question 6
In the FTP section, what is the FTP command used to upload the secret.txt file?
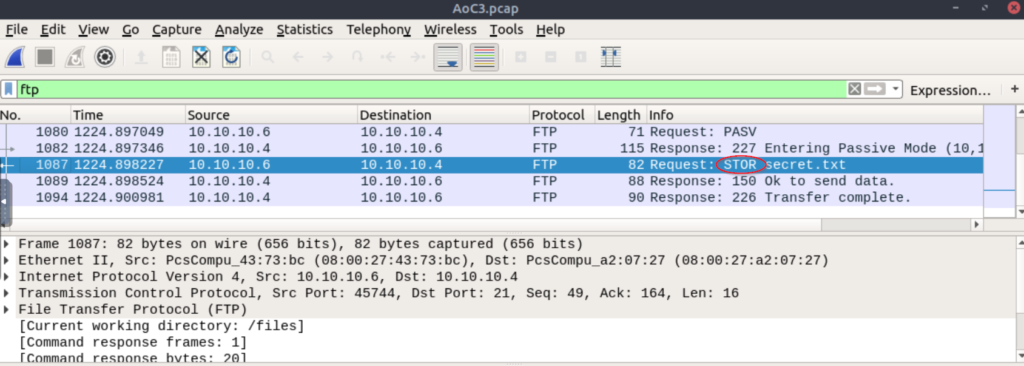
Stay in the same view but scroll down through the packets until you see the secret.txt file.
The command is shown in the ‘Info’ column just before ‘secret.txt’:
Answer:
(Highlight below to see answer):
STOR
Question 7
In the FTP section, what is the content of the secret.txt file?
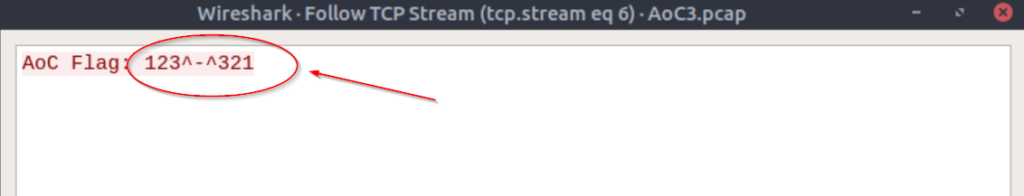
Apply the filter ‘ftp-data’. With this filter applied, we should see only one result.
Right click and select ‘Follow -> TCP Stream’ to obtain the flag:
Answer:
(Highlight below to see answer):
123^-^321